What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-04-23 16:10:10 | Abusing MySQL LOCAL INFILE to read client files (lien direct) | Recently, I was playing the VolgaCTF 2018 CTF with my teammates from TheGoonies and we came across an interesting Web challenge that we didn't manage to solve during the competition. The following day, I read the write-up and learned a cool technique to attack the MySQL client directly via the LOAD DATA INFILE statement.The "Corp Monitoring" task consisted of a Corporate Monitoring API that would test the healthcheck of a given server by connecting and verifying if the FTP, Web and MySQL servers were up. The MySQL user for the connection was restricted and the healthcheck validation was based on a few queries including the "SHOW DATABASE" command.The key to solve the challenge was to identify the "Can Use LOAD DATA LOCAL" client capability and point the API to a Rogue MySQL server that would read arbitrary files from the client via LOAD DATA INFILE statements.After reading about the technique, I decided to check how several libraries, clients and Web Frameworks could be exploited. I also ended up writing a a Bettercap module to abuse this feature in combination with MITM attacks. Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". |
Hack Tool Vulnerability | ★★★★ | ||
| 2016-12-01 18:15:55 | LuaBot: Malware targeting cable modems (lien direct) | During mid-2015 I disclosed some vulnerabilities affecting multiple ARRIS cable modems. I wrote a blogpost about ARRIS' nested backdoor and detailed some of my cable modem research during the 2015 edition from NullByte Security Conference.CERT/CC released the Vulnerability Note VU#419568 and it got lots of media coverage. I did not provide any POC's during that time because I was pretty sure that those vulnerabilities were easily wormable... And guess what? Someone is actively exploiting those devices since May/2016.The malware targets Puma 5 (ARM/Big Endian) cable modems, including the ARRIS TG862 family. The infection happens in multiple stages and the dropper is very similar to many common worm that targets embedded devices from multiple architectures. The final stage is an ARMEB version from the LuaBot Malware.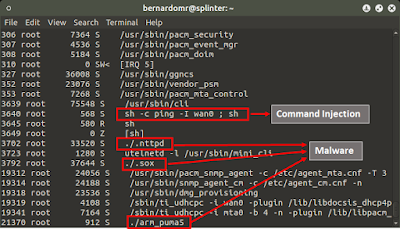 The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. |
Malware Tool Vulnerability | ★★★★ | ||
| 2015-12-09 01:03:30 | Hack.lu 2015 CTF Write Up: Dr. Bob (Forensic 150) (lien direct) | Hack.lu 2015 CTF was organised by fluxfingers during October 20-22. It's one of the coolest CTFs around, the only drawback is that it runs during week days (hey guys patch this for the next years). My team TheGoonies ranked #59th, which is not bad considering we only played part-time.The task Dr. Bob was the one I found most interesting as it included disk forensics, memory forensics and basic crypto tasks.Task: Dr. Bob (Forensic 150)There are elections at the moment for the representative of the students and the winner will be announced tomorrow by the head of elections Dr. Bob. The local schoolyard gang is gambling on the winner and you could really use that extra cash. Luckily, you are able to hack into the mainframe of the school and get a copy of the virtual machine that is used by Dr. Bob to store the results. The desired information is in the file /home/bob/flag.txt, easy as that.Download: dr_bob_e22538fa166acecc68fa17ac148dcbe2.tar.gzThe file provided is a VirtualBox image in a saved state. According to the challenge instructions, we have to retrieve the flag from the user home folder. The VM starts on a login terminal of what seems to be a Linux distro.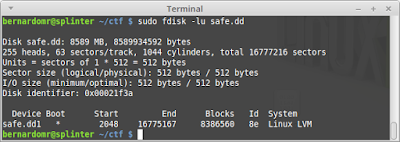 sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan sudo losetup -o 1048576 /dev/loop0 safe.ddsudo lvmdiskscan There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! There are two interesting devices: /dev/vg/root and /dev/vg/home, let's 1 - mount the home folder, 2 - grab the flag and 3 - PROFIT!!! |
Hack Tool | ★★★★ | ||
| 2015-05-04 23:57:38 | Firmware Forensics: Diffs, Timelines, ELFs and Backdoors (lien direct) | This post covers some common techniques that I use to analyze and reverse firmware images. These techniques are particularly useful to dissect malicious firmwares, spot backdoors and detect unwanted modifications.Backdooring and re-flashing firmware images is becoming mainstream: malicious guys are infecting embedded devices and inserting trojans in order to achieve persistence. Recent articles covered the increasing number of trojanized android firmwares and routers that are being permanently modified.Attackers with a privileged network position may MITM your requests and forge fake updates containing malicious firmwares. Writing Evilgrade modules for this is really simple, as most vendors keep failing to deliver updates securely, right ASUS? Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f Valid signature -> nvram_set("rsasign_check", "1")NoConName 2014 CTF Finals: VodkaI'll keep my tradition of writing posts based on CTF challenges because everybody upvotes CTF posts on reddit it's cool.The challenge "Vodka", from NoConName 2014 CTF Finals was created by @MarioVilas, who kindly provided the files here (thanks dude!).I did not participate on the CTF finals, but I found the challenge really interesting because there were many different ways to solve it, summarizing the actions needed to audit a compromised f |
Malware Hack Tool | ★★★★ | ||
| 2015-02-27 00:56:54 | Extracting RAW pictures from memory dumps (lien direct) | IntroductionEarlier today, while reading my Twitter timeline, I saw some Infosec folks discussing about scripts/tools to identify RAW pictures in memory dumps. I decided, then, to write this blog post and share a small hack that I use to visualize data (including memory dumps). Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: Memory DumpsThe first thing you will want to do is to narrow the analysis to the process containing interesting images/pictures. I'm going to use three different memory dumps here:Remote Desktop Client - Windows 7 x64 (mstsc.exe)Let's use the Windows built-in RDP client to connect to an external server and dump the processmemory using procdump: |
Hack Tool | ★★★★ | ||
| 2014-08-22 01:56:46 | Scan the Internet & Screenshot All the Things (lien direct) | During Defcon 22, @ErrataRob, @paulm and @Viss (mass)scanned the Internet and presented some Tips, Tricks and Results. Lots of people confronted @Viss after he posted some VNC screenshots on his Twitter timeline. He posted a follow-up article on his blog and Kashmir Hill, from Forbes, wrote an article about the exposed VNC services.Internet scanning isn't new anymore and people are still surprised with these results. For this post, I'll share some techniques I commonly use to map and screenshot several Internet services during pentest engagements. All this could easily be adapted for other protocols and services, so let's start to Screenshot All the Things. VNCThe easiest way to snapshot these services is to use preexisting tools and script/mod them according to your needs. In order to take screenshots from VNC, I generally use noVNC (an HTML5 VNC client) and a command line utility to capture the WebKit's rendering of a web page.The process is pretty straightforward:1 - Clone the noVNC project from github:git clone git://github.com/kanaka/noVNC2 - Start the mini-webserver and specify the location of the VNC server you want to screenshot:./noVNC/utils/launch.sh --vnc 192.168.1.142:5900 VNCThe easiest way to snapshot these services is to use preexisting tools and script/mod them according to your needs. In order to take screenshots from VNC, I generally use noVNC (an HTML5 VNC client) and a command line utility to capture the WebKit's rendering of a web page.The process is pretty straightforward:1 - Clone the noVNC project from github:git clone git://github.com/kanaka/noVNC2 - Start the mini-webserver and specify the location of the VNC server you want to screenshot:./noVNC/utils/launch.sh --vnc 192.168.1.142:5900 3 - Take a webpage screenshot from command line using CutyCapt, for example:cutycapt --url="http://127.0.0.1:6080/vnc_auto.html" --javascript=on --out=vnc.png --delay=3000 3 - Take a webpage screenshot from command line using CutyCapt, for example:cutycapt --url="http://127.0.0.1:6080/vnc_auto.html" --javascript=on --out=vnc.png --delay=3000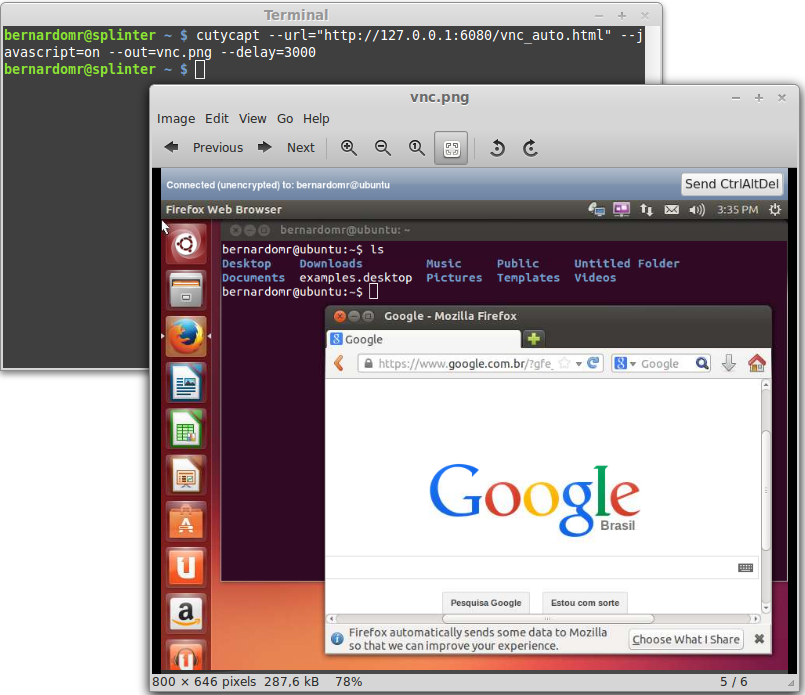 4 - Profit!!!Now all you have to do is masscan the target for ports 5900-5910 (used by VNC), save the results on a text file and create a simple script to take the screenshots. You can also try vncsnapshot, used by @paulm during his Toorcon 2013 talk.RDPMy tool of choice for taking snapshots of RDP ser 4 - Profit!!!Now all you have to do is masscan the target for ports 5900-5910 (used by VNC), save the results on a text file and create a simple script to take the screenshots. You can also try vncsnapshot, used by @paulm during his Toorcon 2013 talk.RDPMy tool of choice for taking snapshots of RDP ser |
Tool | ★★★★ | ||
| 2014-07-21 11:49:10 | Hacking Asus RT-AC66U and Preparing for SOHOpelesslyBroken CTF (lien direct) | So it's finally July, time to pack for DEFCON, follow @defconparties on Twitter and decide which villages to visit and which talks to attend.There's a new hacking competition this year called SOHOpelesslyBroken, presented by ISE and EFF. The objective on Track 0 is to demonstrate previously unidentified vulnerabilities in off-the-shelf consumer wireless routers. Track 1 will hold a live CTF for the duration of DEFCON. CTFs are always fun and this contest involves hacking real embedded devices, what makes it even more fun. Yes, that's my workstation =PI'm particularly interested on the EFF Open Wireless Router, but they didn't disclose details about the device yet. According to the event rules, the ASUS RT-AC66U (HW Ver. A2) [Version 3.0.0.4.266] is one of the possible targets. As I had a spare RT-AC66U at home, I decided to write a quick guide for everyone interested in participating in this competition CTF.reconThe first thing to do is to find the firmware and its source code. Hopefully, Asus RT-AC66U is GPL'ed and we can easily find its source online. The version used for the contest is an old one, from 2012. In order to perform a better analysis, we are going to grab the sources and the firmware from v3.0.0.4.266 and v3.0.0.4.376.1123 (the most recent one as of this writing).Asus RT-AC66u v3.0.0.4.266 - FirmwareAsus RT-AC66u v3.0.0.4.266 - Source CodeAsus RT-AC66u v3.0.0.4.376.1123 - FirmwareAsus RT-AC66u v3.0.0.4.376.1123 - Source CodeMany firmware versions were published between these two releases, we can review the changelogs to find security issues:http://www.asus.com/Networking/RTAC66U/HelpDesk_Download Yes, that's my workstation =PI'm particularly interested on the EFF Open Wireless Router, but they didn't disclose details about the device yet. According to the event rules, the ASUS RT-AC66U (HW Ver. A2) [Version 3.0.0.4.266] is one of the possible targets. As I had a spare RT-AC66U at home, I decided to write a quick guide for everyone interested in participating in this competition CTF.reconThe first thing to do is to find the firmware and its source code. Hopefully, Asus RT-AC66U is GPL'ed and we can easily find its source online. The version used for the contest is an old one, from 2012. In order to perform a better analysis, we are going to grab the sources and the firmware from v3.0.0.4.266 and v3.0.0.4.376.1123 (the most recent one as of this writing).Asus RT-AC66u v3.0.0.4.266 - FirmwareAsus RT-AC66u v3.0.0.4.266 - Source CodeAsus RT-AC66u v3.0.0.4.376.1123 - FirmwareAsus RT-AC66u v3.0.0.4.376.1123 - Source CodeMany firmware versions were published between these two releases, we can review the changelogs to find security issues:http://www.asus.com/Networking/RTAC66U/HelpDesk_Download According to the rules, we have to identify and exploit a 0-day vulnerability. We can combine different flaws with known issues in order to score points. If the vendor had silently patched an issue and you create an exploit for it, that should be scored as a valid 0-day (I'm not going to start discussing terminologies here).Now that we have the source code, it's time to extract and audi According to the rules, we have to identify and exploit a 0-day vulnerability. We can combine different flaws with known issues in order to score points. If the vendor had silently patched an issue and you create an exploit for it, that should be scored as a valid 0-day (I'm not going to start discussing terminologies here).Now that we have the source code, it's time to extract and audi |
Tool | ★★★★ | ||
| 2014-01-08 23:57:00 | Unpacking Firmware Images from Cable Modems (lien direct) | Hacking Cable modems used to be very popular during the early 2000's. People like DerEngel and Isabella from TCNiSO carried lots of research on the topic and talks from bitemytaco (R.I.P) and BlakeSelf during DEFCON 16 and DEFCON 18 covered lots of information on the subject.Securing cable modems is more difficult than other embedded devices because, on most cases, you can't choose your own device/firmware and software updates are almost entirely controlled by your ISP. Most cable modems offer a limited administrative interface and management commands are sent using SNMP.Cable Modem FirmwareThere are basically three types of firmware images for cable modems:- Signed and compresed (PKCS#7 & binary)- Compressed binary images- RAM dump images (uncompressed & raw)You can dump your own firmware image using JTAG or sniffing the connection during upgrades, for example. I'm a big fan of binwalk and I always wondered why it doesn't unpack firmwares from popular Broadcom based cable modems so I decided to research on this.Unpacking the FirmwareFor this analysis I'll use Cisco DPC3925, which is a very common DOCSIS 3.0 modem here in Brazil. Cisco DPC3925 has a BCM3380 chipset, 16MB Flash x 64MB DRAM memory configuration.  The compressed firmware image has around 4MB. Using strings against the file didn't help much and binwalk v1.2.1 (without any additional parameters) did not recognize it. The compressed firmware image has around 4MB. Using strings against the file didn't help much and binwalk v1.2.1 (without any additional parameters) did not recognize it. We can gather lots of useful information from the vendor's page: user guides, datasheets, licensing information and open source disclaimer for the product. There are no sources available on Cisco's home, but the Copyright Notices section states that the product uses LZMA SDK 4.21. We can gather lots of useful information from the vendor's page: user guides, datasheets, licensing information and open source disclaimer for the product. There are no sources available on Cisco's home, but the Copyright Notices section states that the product uses LZMA SDK 4.21.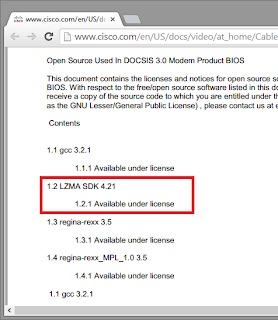 So we know that the firmware is probably packed using LZMA but we still need to figure out how to unpack it. Binwalk - So we know that the firmware is probably packed using LZMA but we still need to figure out how to unpack it. Binwalk - |
Tool | ★★★★ | ||
| 2013-12-10 17:36:29 | Binwally: Directory tree diff tool using Fuzzy Hashing (lien direct) | For this post, I'll discuss about the concept of directory tree and binary diffing and how it could be used to find potential vulnerabilities and security issues that were (silently) patched on firmware images.Silent patching is a big deal as we don't have many security researchers like Spender around. This is a common practice among companies that create software and firmwares for embedded devices. Changelogs from new firmwares often contains few information about security issues, outlining the changes as "bugfixes" or "enhancements": we get no CVE's and we don't know how critical the flaws are.In addition to that, you may occasionally find some reference for the string 'Ac1db1tch3z' on your code (which means that you got a free vulnerability assessment) or your employee Joel might forget to remove a backdoor from the firmware. Diffing the content from previous firmwares may be useful to find out when these backdoors were first installed, modified and/or removed.I introduce you to Binwally: a simple script to perform directory tree diffing using the concept of Fuzzy Hashing (ssdeep) to define a matching score between binaries. Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed |
Tool Vulnerability Patching | ★★★★ |
1
We have: 9 articles.
We have: 9 articles.
To see everything:
Our RSS (filtrered)
