What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2018-04-23 16:10:10 | Abusing MySQL LOCAL INFILE to read client files (lien direct) | Recently, I was playing the VolgaCTF 2018 CTF with my teammates from TheGoonies and we came across an interesting Web challenge that we didn't manage to solve during the competition. The following day, I read the write-up and learned a cool technique to attack the MySQL client directly via the LOAD DATA INFILE statement.The "Corp Monitoring" task consisted of a Corporate Monitoring API that would test the healthcheck of a given server by connecting and verifying if the FTP, Web and MySQL servers were up. The MySQL user for the connection was restricted and the healthcheck validation was based on a few queries including the "SHOW DATABASE" command.The key to solve the challenge was to identify the "Can Use LOAD DATA LOCAL" client capability and point the API to a Rogue MySQL server that would read arbitrary files from the client via LOAD DATA INFILE statements.After reading about the technique, I decided to check how several libraries, clients and Web Frameworks could be exploited. I also ended up writing a a Bettercap module to abuse this feature in combination with MITM attacks. Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". Previous Research Before I start I would like to point that this technique is not new: it's a known and documented feature from the MySQL clients. I gathered prior posts, tools and presentations and they're all written by Russians - it looks like these techniques are not very widespread outside there.- Database Honeypot by design - Presentation from Yuri Goltsev (August 2013)- Rogue-MySql-Server Tool: MySQL fake server to read files of connected clients (September 2013)- MySQL connect file read - Post from the Russian Security (April 2016)Revisiting MySQL LOAD DATA INFILEAccording to the MySQL documentation, the handshake connection phase performs the following tasks:- Exchange the capabilities of client and server- Setup SSL communication channel if requested- Authenticate the client against the serverAfter the successful authentication, the client sends the query and waits for the server response before actually doing something. The "Client Capabilities" packet includes an entry called "Can Use LOAD DATA LOCAL". |
Hack Tool Vulnerability | ★★★★ | ||
| 2016-12-01 18:15:55 | LuaBot: Malware targeting cable modems (lien direct) | During mid-2015 I disclosed some vulnerabilities affecting multiple ARRIS cable modems. I wrote a blogpost about ARRIS' nested backdoor and detailed some of my cable modem research during the 2015 edition from NullByte Security Conference.CERT/CC released the Vulnerability Note VU#419568 and it got lots of media coverage. I did not provide any POC's during that time because I was pretty sure that those vulnerabilities were easily wormable... And guess what? Someone is actively exploiting those devices since May/2016.The malware targets Puma 5 (ARM/Big Endian) cable modems, including the ARRIS TG862 family. The infection happens in multiple stages and the dropper is very similar to many common worm that targets embedded devices from multiple architectures. The final stage is an ARMEB version from the LuaBot Malware.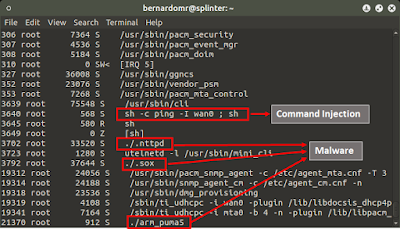 The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. The ARMEL version from the LuaBot Malware was dissected on a blogpost from Malware Must Die, but this specific ARMEB was still unknown/undetected for the time being. The malware was initially sent to VirusTotal on 2016-05-26 and it still has a 0/0 detection rate. |
Malware Tool Vulnerability | ★★★★ | ||
| 2014-07-16 23:41:20 | Foxit PDF Reader Stored XSS (lien direct) | A friend of mine was performing an external pentest recently and he started to complain that his traditional Java exploits were not being effective. He was able to map a few applications and defenses in place protecting the client's network but he still needed an initial access to start pivoting.Basic protections like AV, application white-listing as well as more advanced ones like EMET are used to make the life of criminals (and pentesters) harder, but they're often bypassed. While discussing alternatives with my friend, he told me that the company replaced Adobe Reader after seeing lots of Security Advisories for the product. And what was the replacement? Foxit Reader: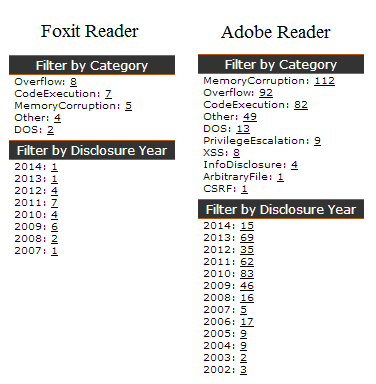 Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: Advisories for Adobe Reader and Foxit Reader listed on OSVDB (May/2014)Less advisories means that the product is more secure, right? Marc Ruef's talk about VDB management summarizes this point: |
Malware Vulnerability Patching Guideline | ★★★★ | ||
| 2014-07-16 23:40:46 | Wildcard DNS, Content Poisoning, XSS and Certificate Pinning (lien direct) | Hi everyone, this time I'm going o talk about an interesting vulnerability that I reported to Google and Facebook a couple of months ago. I had some spare time last October and I started testing for vulnerabilities on a few companies with established bug bounty programs. Google awarded me with $5000,00 and Facebook payed me $500,00 for reporting the bugs.I know you may be more interested on highly sophisticated exploits that allow arbitrary file upload to the Internet, with custom payloads that may lead to unexpected behavior like closing Security Lists. Hopefully this class of bugs is already patched by Fyodor and Attrition is offering an efficient exploit mitigation technique.The title may be a little confusing, but I'm going to show that it's possible to combine all these techniques to exploit vulnerable systems.Content Poisoning and Wildcard DNSHost header poisoning occurs when the application doesn't validate full URL's generated from the HTTP Host header, including the domain name. Recently, the Django Framework fixed a few vulnerabilities related to that and James Kettle made an interesting post discussing lots of attack scenarios using host header attacks.While testing this issue, I found a different kind of Host header attack that abuses the possibility to browse wildcard domains. Let's have a quick look at the Wikipedia entry on Hostnames:"The Internet standards (Request for Comments) for protocols mandate that component hostname labels may contain only the ASCII letters 'a' through 'z' (in a case-insensitive manner), the digits '0' through '9', and the hyphen ('-'). The original specification of hostnames in RFC 952, mandated that labels could not start with a digit or with a hyphen, and must not end with a hyphen. However, a subsequent specification (RFC 1123) permitted hostname labels to start with digits. No other symbols, punctuation characters, or white space are permitted."The fun part here is that the network stack from Windows, Linux and Mac OS X consider domains like -www.plus.google.com, www-.plus.google.com and www.-.plus.google.com valid. It's interesting to note that Android won't resolve these domains for some reason. | Vulnerability Guideline | ★★★★ | ||
| 2014-02-18 09:43:31 | Analyzing Malware for Embedded Devices: TheMoon Worm (lien direct) | All the media outlets are reporting that Embedded Malware is becoming mainstream. This is something totally new and we never heard of this before, right? The high number of Linux SOHO routers with Internet-facing administrative interfaces, the lack of firmware updates and the ease to craft exploits make them a perfect target for online criminals. The Internet of Threats is wildly insecure, but definitely not unpatchable.To all infosec people out there, it's important to understand these threats and report it properly to the media. Some top-notch researchers recently uncovered "Massive Botnets" infecting refrigerators, microwaves, gaming consoles, soda machines and tamagotchis. The problem is that they never provided any sort of evidence, no malware samples, no IOC's and did not write a Hakin9 article describing it. Refrigerator Botnet? Revd. Pastor Laphroaig says Show the PoC || GTFOThe aim for this post is to provide more information to identify/execute embedded binaries, describing how to set your own virtual lab. In case you missed it, head to the first post from the "Analyzing and Running binaries from Firmware Images" series.TheMoon WormJohannes from SANS provided me a sample from "TheMoon" malware and posted some interesting information on their handler's diary. Their honeypots captured the scanning activity and linked the exploit to a vulnerable CGI script running on specific firmwares from the following Linksys routers: E4200, E3200, E3000, E2500, E2100L, E2000, E1550, E1500, E1200, E1000,E900.SANS handlers classified TheMoon as a Worm because of the self-replicating nature of the malware. The worm searches for a "HNAP1" URL to fingerprint and identify potentially vulnerable routers. If you check your FW and Server logs you may find lot's of different IP's probing this URL.The worm was named like this because it contains images from the movie "The Moon". It's possible to carve a few PNG's inside the ELF binary: Refrigerator Botnet? Revd. Pastor Laphroaig says Show the PoC || GTFOThe aim for this post is to provide more information to identify/execute embedded binaries, describing how to set your own virtual lab. In case you missed it, head to the first post from the "Analyzing and Running binaries from Firmware Images" series.TheMoon WormJohannes from SANS provided me a sample from "TheMoon" malware and posted some interesting information on their handler's diary. Their honeypots captured the scanning activity and linked the exploit to a vulnerable CGI script running on specific firmwares from the following Linksys routers: E4200, E3200, E3000, E2500, E2100L, E2000, E1550, E1500, E1200, E1000,E900.SANS handlers classified TheMoon as a Worm because of the self-replicating nature of the malware. The worm searches for a "HNAP1" URL to fingerprint and identify potentially vulnerable routers. If you check your FW and Server logs you may find lot's of different IP's probing this URL.The worm was named like this because it contains images from the movie "The Moon". It's possible to carve a few PNG's inside the ELF binary: |
Malware Vulnerability Patching | ★★★★ | ||
| 2013-12-10 17:36:29 | Binwally: Directory tree diff tool using Fuzzy Hashing (lien direct) | For this post, I'll discuss about the concept of directory tree and binary diffing and how it could be used to find potential vulnerabilities and security issues that were (silently) patched on firmware images.Silent patching is a big deal as we don't have many security researchers like Spender around. This is a common practice among companies that create software and firmwares for embedded devices. Changelogs from new firmwares often contains few information about security issues, outlining the changes as "bugfixes" or "enhancements": we get no CVE's and we don't know how critical the flaws are.In addition to that, you may occasionally find some reference for the string 'Ac1db1tch3z' on your code (which means that you got a free vulnerability assessment) or your employee Joel might forget to remove a backdoor from the firmware. Diffing the content from previous firmwares may be useful to find out when these backdoors were first installed, modified and/or removed.I introduce you to Binwally: a simple script to perform directory tree diffing using the concept of Fuzzy Hashing (ssdeep) to define a matching score between binaries. Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed Binwally says "no" to Silent PatchingFuzzy HashingFuzzy Hashing, also know as context triggered piecewise hashes (CTPH), can match inputs that have homologies. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The concept was introduced by Andrew Tridgell and the most well-known tool is ssdeep, created by Jesse Kornblum.The usage example outlined on ssdeep's homepage summarizes it well:$ ls -l foo.txt-rw-r--r-- 1 jessekor jessekor 240 Oct 25 08:01 foo.txt$ cp foo.txt bar.txt$ echo 1 >> bar.txtA cryptographic hashing algorithm like MD5 can't be used to match these files; they have wildly different hashes.$ md5deep foo.txt bar.txt7b3e9e08ecc391f2da684dd784c5af7c /Users/jessekornblum/foo.txt32436c952f0f4c53bea1dc955a081de4 /Users/jessekornblum/bar.txtBut fuzzy hashing can! We compute the fuzzy hash of one file and use the matching mode to match the other one.$ ssdeep -b foo.txt > hashes.txt$ ssdeep -bm hashes.txt bar.txtbar.txt matches foo.txt (64)The number at the end of the line is a match score, or a weighted measure of how similar these files are. The higher the number, the more similar the files.BinwallyBinwally is a simple Python script that uses this concept to diff directory trees in order to find different, unique and matching files, displaying an overall score of the results. It was based on diffall.py from the book Programming Python (4th Ed |
Tool Vulnerability Patching | ★★★★ |
1
We have: 6 articles.
We have: 6 articles.
To see everything:
Our RSS (filtrered)
