What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-11-22 07:45:40 | Lazarus APT uses an Android app to target Samsung users in the South Korea (lien direct) | >The North Korea linked group Lazarus APT has been using a new strain of Android malware to target smartphone users in South Korea. The hacking campaign was spotted by McAfee and Palo Alto Networks, both security firms attributed the attacks to the Hidden Cobra APT. The activity of the Lazarus APT Group surged in 2014 and 2015, its […] | Medical | APT 38 | ||
| 2017-11-15 17:21:07 | US Government Warns of Hidden Cobra North Korea Cyber Threat (lien direct) | A Department of Homeland Security (DHS) Alert released on Tuesday warns the public about a campaign of hacking by the government of North Korea it has code-named “Hidden Cobra.” DHS joined the FBI for a joint Technical Alert about the campaign and its use of a piece of malicious software dubbed FallChill, a remote access trojan (RAT)...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/493009316/0/thesecurityledger -->» | Medical | APT 38 | ||
| 2017-11-15 11:14:56 | US Government issues alert about North Korean "Hidden Cobra" cyber attacks (lien direct) |  The FBI and US Department of Homeland Security have issued an alert that hackers have targeted the aerospace industry, financial services and critical infrastructure with a remote access trojan (RAT) to further exploit vulnerable networks. The FBI and US Department of Homeland Security have issued an alert that hackers have targeted the aerospace industry, financial services and critical infrastructure with a remote access trojan (RAT) to further exploit vulnerable networks.
|
Medical | APT 38 | ||
| 2017-11-15 08:52:11 | US DHS and FBI share reports on FALLCHILL and Volgmer malware used by North Korean Hidden Cobra APT (lien direct) | >US DHS published the details of the malware FALLCHILL and Volgmer used by the APT group Hidden Cobra that is linked to the North Korean government. The US Department of Homeland Security (DHS) published the details of the hacking tool FALLCHILL used one of the APT group linked to the North Korean government tracked as Hidden Cobra (aka Lazarus Group). […] | Medical | APT 38 | ||
| 2017-10-17 07:50:25 | North Korean Hackers Used Hermes Ransomware to Hide Recent Bank Heist (lien direct) | Evidence suggests the infamous Lazarus Group, a hacking crew believed to be operating out of North Korea, is behind the recent hack on the Far Eastern International Bank (FEIB) in Taiwan. [...] | Medical | APT 38 | ||
| 2017-10-16 22:32:36 | Taiwan Heist: Lazarus Tools and Ransomware (lien direct) | Written by Sergei Shevchenko, Hirman Muhammad bin Abu Bakar, and James WongBACKGROUNDReports emerged just over a week ago of a new cyber-enabled bank heist in Asia. Attackers targeting Far Eastern International Bank (FEIB), a commercial firm in Taiwan, moved funds from its accounts to multiple overseas beneficiaries. In a story which reminds us of the Bangladesh Bank case – the culprits had compromised the bank's system connected to the SWIFT network and used this to perform the transfers. In recent days, various malware samples have been uploaded to malware repositories which appear to originate from the intrusion. These include both known Lazarus group tools, as well as a rare ransomware variant called 'Hermes' which may have been used as a distraction or cover-up for the security team whilst the heist was occurring. The timeline below provides an overview of the key events: 01 October 2017  Malware compiled containing admin credentials for the FEIB network. 03 October 2017 Malware compiled containing admin credentials for the FEIB network. 03 October 2017  Transfers using MT103 messages were sent from FEIB to Cambodia, the US and Sri Lanka. Messages to cover the funds for the payments were incorrectly created and sent. 03 October 2017 Transfers using MT103 messages were sent from FEIB to Cambodia, the US and Sri Lanka. Messages to cover the funds for the payments were incorrectly created and sent. 03 October 2017  Breach discovered and ransomware uploaded to online malware repository site. 04 October 2017 Breach discovered and ransomware uploaded to online malware repository site. 04 October 2017  Individual in Sri Lanka cashes out a reported Rs30m (~$195,000). 06 October 2017 Individual in Sri Lanka cashes out a reported Rs30m (~$195,000). 06 October 2017  |
Medical | Wannacry APT 38 | ||
| 2017-08-16 16:55:51 | North Korean Cyberspies Target US Defense Contractors Following Nuclear Threats (lien direct) | The North Korean cyber-espionage group known as the Lazarus Group has been busy hacking US defense contractors, according to a report published on Monday by security research firm Palo Alto Networks. [...] | Medical | APT 38 | ||
| 2017-06-21 11:47:47 | WannaCryptor attack \'may have come from Lazarus group\' (lien direct) | Experts in the UK and the US have reportedly claimed that the recent global WannaCryptor ransomware attack was initiated by the North Korean Lazarus Group. | Medical | Wannacry APT 38 | ||
| 2017-06-19 08:15:46 | Hidden Cobra And DeltaCharlie: An Explainer (lien direct) | The ISBuzz Post: This Post Hidden Cobra And DeltaCharlie: An Explainer | Medical | APT 38 | ||
| 2017-06-16 16:00:31 | Threatpost News Wrap, June 16, 2017 (lien direct) | Mike Mimoso and Chris Brook discuss the news of the week, including Microsoft's XP patches, Hidden Cobra, a Nigerian BEC campaign, MacRansom, and more. | Medical | APT 38 | ||
| 2017-06-14 17:55:58 | US Blames North Korean \'Hidden Cobra\' Group For Cyber Attacks Since 2009 (lien direct) | The ISBuzz Post: This Post US Blames North Korean ‘Hidden Cobra’ Group For Cyber Attacks Since 2009 | Medical | APT 38 | ||
| 2017-06-14 17:17:21 | DHS, FBI Warn of North Korea \'Hidden Cobra\' Strikes Against US Assets (lien direct) | DHS and the FBI warned that North Korean attackers are targeting U.S. businesses with malware- and botnet-related attacks that are part of concerted effort dubbed "Hidden Cobra." | Medical | APT 38 | ||
| 2017-06-14 14:22:31 | US indicts North Korea for host of cyberattacks, expects more to come (lien direct) | A North Korean entity called Hidden Cobra was behind a series of cyberattacks in the US using sophisticated tools and targeting a diverse group of entities. | Medical | APT 38 | ||
| 2017-06-14 10:44:45 | U.S. Warns of North Korea\'s \'Hidden Cobra\' Attacks (lien direct) | The United States Computer Emergency Readiness Team (US-CERT) released a technical alert on Tuesday on behalf of the DHS and the FBI to warn organizations of North Korea's “Hidden Cobra†activities, particularly distributed denial-of-service (DDoS) attacks. | Medical | APT 38 | ||
| 2017-06-14 05:23:04 | US Warns of \'DeltaCharlie\' – A North Korean DDoS Botnet Malware (lien direct) | The United States government has released a rare alert about an ongoing, eight-year-long North Korean state-sponsored hacking operation.
The joint report from the FBI and U.S. Department of Homeland Security (DHS) provided details on "DeltaCharlie," a malware variant used by "Hidden Cobra" hacking group to infect hundreds of thousands of computers globally as part of its DDoS botnet network.
|
Medical | APT 38 | ||
| 2017-06-14 04:00:00 | Video: North Korean hacking group has been hitting the US since 2009 (lien direct) | Hidden Cobra, a North Korean-backed hacking group, may also be responsible for WannaCry and the Sony Pictures hack. | Medical | Wannacry APT 38 | ★★★★ | |
| 2017-05-31 07:33:02 | Analysis of Competing Hypotheses, WCry and Lazarus (ACH part 2), (Wed, May 31st) (lien direct) | Introduction In my previous diary, I did a very brief introduction on what the ACH method is [1], so that now all readers, also those who had never seen it before, can have a common basic understanding of it. One more thing I have not mentioned yet is how the scores are calculated. There are three different algorithms: an Inconsistency Counting algorithm, a Weighted Inconsistency Counting algorithm, and a Normalized algorithm [2]. The Weighted Inconsistency Counting algorithm, the one used in todays examples, builds on the Inconsistency algorithm, but also factors in weights of credibility and relevance values. For each item of evidence, a consistency entry of I width:300px" /> Today, I will apply ACH to a recent quite known case: WCry attribution. There has been lots of analyses and speculations around it, lately several sources in the InfoSec community tied WCry strongly to Lazarus Group [3][4][5][6], while some others provided motivation for being skeptical about such attribution [7]. Therefore, it is a perfect case to show the use of ACH: several different hypotheses, facts, evidences and assumptions. Digital Shadows WCry ACH analysis About two weeks ago, Digital Shadows published a very well done post on ACH applied to WCry attribution [8]. Regarding possible attribution to Lazarus though, as stated on their post, At the time of writing, however, we assessed there to be insufficient evidence to corroborate this claim of attribution to this group, and alternative hypotheses should be considered. Therefore among the hypotheses considered is missing one specifically for Lazarus in place of a more generic nation state or state affiliate actor. The following are the four different hypotheses considered by Digital Shadows: A sophisticated financially-motivated cybercriminal actor - H1 An unsophisticated financially-motivated cybercriminal actor - H2 A nation state or state-affiliated actor conducting a disruptive operation - H3 A nation state or state-affiliated actor aiming to discredit the National Security Agency (NSA) width:600px" /> Given the final scores computed, they have assessed that though by no means definitive, a WannaCry campaign launched by an unsophisticated cybercriminal actor was the most plausible scenario based on the information that is currently available. Just one note on my side, from my calculation seems they have made a mistake, and H2 score should be -2.121 rather than -1.414. This does not change the final result, but brings H2 and H3 way closer. My WCry ACH Analysis Although the Digital Shadows analysis was a very good one, I felt something was missing, both on the hypotheses as well as on the evidences side. Particularly, in my opinion, I would add three more hypotheses. When thinking about NSA being the final target of this, other than A nation state or state-affiliated actor aiming to discredit the NSA, I think that it should be considered also a (generic/unattributed) TA aiming at unveiling/exposing the extent of possible NSA network of compromised machines (H5). This is something one would expect from a hacktivist maybe, although it seems to be way more sophisticated than what hacktivist have got us used to. One difference with the H4 could be on the lack of supporting media narrative. While if one wants to discredit NSA would be ready to have a supporting media narrative, if the goal was simply to unveil and show to everyone the potential extent of NSA infected machines, the infection as it was would have been sufficient, given also the abundant media coverage it got. Although this may still be seen as too close to H4 to be a different hypothesis, I still do see a case for it. | Medical | Wannacry APT 38 | ||
| 2017-05-30 14:00:19 | New Evidence Cements Theory That North Korea is Behind Lazarus Group (lien direct) | A 53-page report released today by Group-IB, a Russian cyber-security vendor, contains new evidence that cements the theory that the North Korean government is behind the Lazarus Group, a cyber-espionage outfit. [...] | Medical | APT 38 | ||
| 2017-05-29 11:10:00 | Linguistic Analysis Suggests WannaCry Hackers Could be From Southern China (lien direct) | It's been almost four weeks since the outcry of WannaCry ransomware, but the hackers behind the self-spread ransomware threat have not been identified yet.
However, two weeks ago researchers at Google, Kaspersky Lab, Intezer and Symantec linked WannaCry to 'Lazarus Group,' a state-sponsored hacking group believed to work for the North Korean government.
Now, new research from dark web
|
Medical | Wannacry APT 38 | ||
| 2017-05-19 13:00:19 | Threatpost News Wrap, May 19, 2017 (lien direct) | Mike Mimoso and Chris Brook discuss WannaCry, Microsoft's response, the killswitches, a potential link with Lazarus Group, and what the future holds for the ShadowBrokers. | Medical | Wannacry APT 38 | ||
| 2017-05-17 06:50:12 | 3 Security Firms Say WannaCry Ransomware Shares Code with North Korean Malware (lien direct) | While initially, we thought this would be a silly and unsubstantiated discovery, the number of security firms claiming they've identified and confirmed connections between the WannaCry ransomware and malware used by the Lazarus Group has now gone up to three. [...] | Medical | Wannacry APT 38 | ||
| 2017-05-17 03:33:55 | WanaCrypt0r Ransomworm (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDSince the release of the ETERNALBLUE exploit by 'The Shadow Brokers' last month security researchers have been watching for a mass attack on global networks. This came on Friday 12th May when it was bundled with ransomware called WanaCrypt0r and let loose. Initial reports of attacks were highlighted by Telefonica in Spain but the malware quickly spread to networks in the UK where the National Health Service (NHS) was impacted, followed by many other networks across the world.The infographic below illustrates the key components of the WanaCrypt0r ransomware. This is described in further detail in subsequent sections of this report along with initial clues on attribution.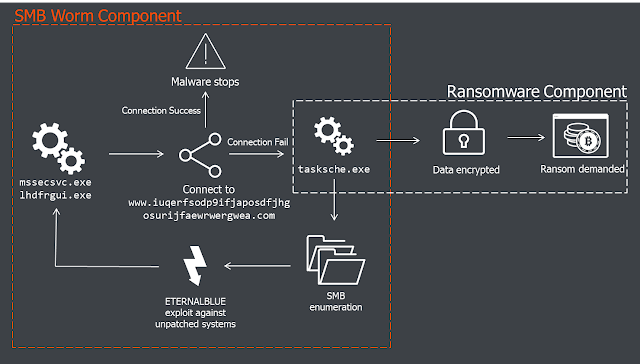 ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs |
Guideline Medical | Wannacry APT 38 | ||
| 2017-05-16 10:39:48 | WannaCry ransomware cyber-attack \'may have N Korea link\' (lien direct) | You may not have heard of the Lazarus Group, but you may be aware of its work. The devastating hack on Sony Pictures in 2014, and another on a Bangladeshi bank in 2016, have both been attributed to the highly sophisticated group. It is widely believed that the Lazarus Group worked out of China, but on behalf ... | Medical | Wannacry APT 38 | ||
| 2017-04-04 08:22:00 | Kaspersky Lab reveals \'direct link\' between banking heist hackers and North Korea (lien direct) | Kaspersky Lab found a “direct link†between the Lazarus group banking heist hackers and North Korea.While Lazarus is a notorious cyber-espionage and sabotage group, a subgroup of Lazarus, called Bluenoroff by Kaspersky researchers, focuses only on financial attacks with the goal of “invisible theft without leaving a trace.â€The group has four main types of targets: financial institutions, casinos, companies involved in the development of financial trade software and crypto-currency businesses.To read this article in full or to leave a comment, please click here | Medical | APT 38 | ||
| 2017-04-03 20:38:44 | Lazarus APT Spinoff Linked to Banking Hacks (lien direct) | The Lazarus Group has splintered off a group whose mission is to attack banks and steal money in order to fund its operations. | Medical | APT 38 | ||
| 2017-04-03 16:33:01 | Banking hackers left a clue that may link them to North Korea (lien direct) | The notorious hackers behind a string of banking heists have left behind a clue that supports a long-suspected link to North Korea, according to security researchers.The so-called Lazarus Group has been eyed as a possible culprit behind the heists, which included last February's $81 million theft from Bangladesh's central bank through the SWIFT transaction software.However, hackers working for the group recently made a mistake: They failed to wipe the logs from a server the group had hacked in Europe, security firm Kaspersky Lab said on Monday.To read this article in full or to leave a comment, please click here | Medical | APT 38 | ||
| 2017-03-06 12:13:22 | Lazarus & Watering-hole attacks (lien direct) | On 3rd February 2017, researchers at badcyber.com released an article that detailed a series of attacks directed at Polish financial institutions. The article is brief, but states that "This is – by far – the most serious information security incident we have seen in Poland" followed by a claim that over 20 commercial banks had been confirmed as victims.This report provides an outline of the attacks based on what was shared in the article, and our own additional findings. ANALYSISAs stated in the blog, the attacks are suspected of originating from the website of the Polish Financial Supervision Authority (knf.gov[.]pl), shown below: From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen From at least 2016-10-07 to late January the website code had been modified to cause visitors to download malicious JavaScript files from the following locations: hxxp://sap.misapor[.]ch/vishop/view.jsp?pagenum=1hxxps://www.eye-watch[.]in/design/fancybox/Pnf.action Both of these appear to be compromised domains given they are also hosting legitimate content and have done for some time. The malicious JavaScript leads to the download of malware to the victim's device. Some hashes of the backdoor have been provided in BadCyber's technical analysis: 85d316590edfb4212049c4490db08c4bc1364bbf63b3617b25b58209e4529d8c1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae The C&Cs given in the BadCyber analysis were the following IP addresses: 125.214.195.17196.29.166.218 LAZARUS MALWAREOnly one of the samples referenced by BadCyber is available in public malware repositories. At the moment we cannot verify that it originated from the watering-hole on the KNF website – but we have no reason to doubt this either. MD5 hash Filename File Info First seen |
Guideline Medical | APT 38 | ||
| 2017-03-06 12:13:03 | Lazarus\' False Flag Malware (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDWe continue to investigate the recent wave of attacks on banks using watering-holes on at least two financial regulator websites as well as others. Our initial analysis of malware disclosed in the BadCyber blog hinted at the involvement of the 'Lazarus' threat actor. Since the release of our report, more samples have come to light, most notably those described in the Polish language niebezpiecznik.pl blog on 7 February 2017. MD5 hash Filename Compile Time File Info Submitted 9216b29114fb6713ef228370cbfe4045 srservice.chm N/A N/A N/A 8e32fccd70cec634d13795bcb1da85ff srservice.hlp N/A N/A N/A e29fe3c181ac9ddb | Guideline Medical | APT 38 | ||
| 2017-02-13 20:39:54 | Lazarus mob possibly behind malware attacks against Polish banks (lien direct) |  A hacking gang known as the Lazarus Group might be responsible for malware attacks that have targeted Polish banks and other financial organizations.
David Bisson reports. A hacking gang known as the Lazarus Group might be responsible for malware attacks that have targeted Polish banks and other financial organizations.
David Bisson reports.
|
Medical | APT 38 | ||
| 2017-01-03 14:00:00 | Top 12 AlienVault Blogs of 2016 (lien direct) | Wow, 2016 was quite a year, which provided the AlienVault team and our guest bloggers with plenty of topics to blog on from InfoSec best practices to OceanLotus to Reverse Engineering to building a home malware lab! We are looking forward to providing more educational and useful blogs in 2017. As in 2016, we welcome and support guest bloggers who have contributions to make to the Infosec community. If you are interested in being a guest blogger, please contact me at kbrew@alienvault.com. Lastly, please subscribe to our blog to ensure you get all the new goodies either daily or a weekly summary in your inbox. With our further ado, following are the top 12 AlienVault blogs of 2016: Building a Home Lab to Become a Malware Hunter - A Beginner’s Guide - The top blog of 2016 was written by @sudosev and explains how he set up his own home malware lab. How Penetration Testers Use Google Hacking - Jayme Hancock describes how to do Google hacking / dorking cleverly as a pen tester. It even includes a helpful "cheat sheet". Security Issues of WiFi - How it Works - Everyone loves WiFi, but Joe Gray explains how WiFi works and describes the many security issues and nuances associated with WiFi. Reverse Engineering Malware - In this blog, I interview some members of our AlienVault Labs team to learn how they reverse engineer malware when they're doing security research. The team describes several approaches and tools to use in analyzing malware samples. The Mirai Botnet, Tip of the IoT Iceberg - Javvad Malik talks about IoT security challenges in general, and focuses on the Mirai botnet which focused on XiongMai Technologies IoT equipment in a recent attack. Web Application Security: Methods and Best Practices - The OWASP top 10 and web application security testing are covered in this educational blog by Garrett Gross. Common Types of Malware, 2016 Update - Lauren Barraco outlines the different categories of malware and highlights What's New in 2016. PowerWare or PoshCoder? Comparison and Decryption - Peter Ewane of the Labs team talks about his research into PowerShell vulnerabilities and exploits. He focuses on PowerWare, whick seems to be heavily based on PoshCoder. Can You Explain Encryption to Me? - In this blog by Javvad Malik, he describes encryption to his boss in a hilarious exchange of notes. Javvad then outlines the basics of encryption in a very understandable way. OceanLotus for OS X – an Application Bundl | Medical | APT 38 APT 32 | ||
| 2016-08-09 13:00:00 | OnionDog – An Example of a Regional, Targeted Attack (lien direct) | BackgroundBad actors are getting more sophisticated with the techniques they employ, including their ability to target specific industries and geographical regions. OnionDog is a good example of an attack that exploits a vulnerability in an application that is both popular in the target region, and is commonly deployed in the organizations the attackers wish to compromise.The Helios team at 360 SkyEye Labs published a detailed analysis of the OnionDog APT earlier this year, and during the dog-days of Summer (see what I did there?) it seems appropriate to revisit this malware. OnionDog has been around for several years and exploits a vulnerability in Hangul office software, which is a popular Korean-language productivity suite. Hangul software is also widely deployed in South Korean Government agencies and facilities.The group behind OnionDog is the Lazarus Group, exposed by AlienVault and other threat intelligence teams as part of Operation Blockbuster for its targeting of Sony Pictures and a range of other targets.How it WorksOnionDog used various techniques to entice victims to open the malicious attachment. The attachments targeted a range of government agencies and utilities, such as power, water, ports, transit, and rail to lure its victims (see the screenshot of the ‘Investigation Report of the Korean Railway Accident” below). Source: 360 SkyEye LabsThe malware installs a back door to the compromised system, collects and forwards information about the compromised systems to the C&C server, as well as infecting any device attached to the USB drive.Impact on youThe regional nature of OnionDog will likely limit your exposure to this particular version of the threat if you’re not located in South Korea. However, if there is a user of Hangul software on your network, or if someone in your office may have visited an office that uses Hangul software and plugged a device into a compromised system, you may be at risk of data loss. However, although this version of the malware is localized to South Korea, the Lazarus Group could easily choose another popular application to target specific organizations in other countries.How AlienVault HelpsThe AlienVaultâ Unified Security Management (USM)™ platform delivers the essential security capabilities that organizations of all sizes need to detect, prioritize, and respond to threats like OnionDog. The AlienVault Labs team regularly updates the rulesets that drive the threat detection and response capabilities of the AlienVault USM platform, to keep you up to date with new and evolving threats such as OnionDog. The Labs team performs the threat research that most IT teams simply don’t have the expertise, time, budget, or tools to do themselves on the latest threats, and how to detect and respond to them.The Labs team recently updated the USM platform’s ability to detect this new threat by adding IDS signatures to detect the malicious traffic and a correlation directive to link events from across a network that indicate a system compromised by OnionDog. Learn more about the Source: 360 SkyEye LabsThe malware installs a back door to the compromised system, collects and forwards information about the compromised systems to the C&C server, as well as infecting any device attached to the USB drive.Impact on youThe regional nature of OnionDog will likely limit your exposure to this particular version of the threat if you’re not located in South Korea. However, if there is a user of Hangul software on your network, or if someone in your office may have visited an office that uses Hangul software and plugged a device into a compromised system, you may be at risk of data loss. However, although this version of the malware is localized to South Korea, the Lazarus Group could easily choose another popular application to target specific organizations in other countries.How AlienVault HelpsThe AlienVaultâ Unified Security Management (USM)™ platform delivers the essential security capabilities that organizations of all sizes need to detect, prioritize, and respond to threats like OnionDog. The AlienVault Labs team regularly updates the rulesets that drive the threat detection and response capabilities of the AlienVault USM platform, to keep you up to date with new and evolving threats such as OnionDog. The Labs team performs the threat research that most IT teams simply don’t have the expertise, time, budget, or tools to do themselves on the latest threats, and how to detect and respond to them.The Labs team recently updated the USM platform’s ability to detect this new threat by adding IDS signatures to detect the malicious traffic and a correlation directive to link events from across a network that indicate a system compromised by OnionDog. Learn more about the |
Medical | APT 38 | ||
| 2016-02-24 14:00:00 | Operation BlockBuster unveils the actors behind the Sony attacks (lien direct) | Today, a coordinated coalition involving AlienVault and several other security companies led by Novetta is announcing Operation BlockBuster. This industry initiative was created to share information and potentially disrupt the infrastructure and tools from an actor named the Lazarus Group. The Lazarus Group has been responsible for several operations since at least 2009, including the attack that affected Sony Pictures Entertainment in 2014.Part of our research on this actor was presented at the Kaspersky Security Analyst Summit (SAS) in Tenerife, Spain on February 9th, 2016 as a joint talk between AlienVault and Kaspersky’s Global Research and Analysis Team.In the research that AlienVault and Kaspersky collaborated on, we attributed several campaigns to this actor. Armed with some of the indicators that US-CERT made public after the Sony attack, we continued to analyze different campaigns in 2015 that we suspected were being launched by the same actor. Eventually we were also able to attribute previous activity to the same attackers including:Sony Pictures Entertainment - 2014Operation DarkSeoul - 2013Operation Troy - 2013Wild Positron / Duuzer - 2015Besides several campaigns were the Lazarus group has utilized wipers to perform destructive attacks, they have also been busy using the same tools to perform data theft and cyber espionage operations.Today, as part of the Operation BlockBuster release, we want to share some of our findings and TTP’s from the Lazarus Group that allowed us to link and attribute all the campaigns and tools into the same cluster of activity. We highly recommend that you read the comprehensive report Novetta published today that includes details on the project’s scope and the more than 45 malware families identified, and includes signatures and guidance to help organizations detect and stop the group’s actions.Encryption/Shared keysOne of the key findings that gave us the opportunity to link several families to the same actors was finding a dropper that the attackers use. This dropper contains a compressed resource (ZIP) with the name “MYRES” that is protected by a password. The attackers have reused the same password in different occasions and we were able to find droppers containing different families used by the group. This actor also reuses the code libraries they utilize to perform RSA encryption. We were also able to find the exact same public key in multiple variants.Batch scriptsThis actor often uses BAT files that share the same skeleton in order to delete the initial files after infection. This actor also reuses the code libraries they utilize to perform RSA encryption. We were also able to find the exact same public key in multiple variants.Batch scriptsThis actor often uses BAT files that share the same skeleton in order to delete the initial files after infection. We have seem them reuse this technique across multiple droppers and payloads.Obfuscation functionsThe Lazarus Group uses a few different methods to obfuscate API functions and dynamically load them. One of them consist on using a simple XOR schema. We have seem them reuse this technique across multiple droppers and payloads.Obfuscation functionsThe Lazarus Group uses a few different methods to obfuscate API functions and dynamically load them. One of them consist on using a simple XOR schema. |
Medical | Yahoo APT 38 |
To see everything:
Our RSS (filtrered)
