What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2016-10-28 03:32:09 | Configuring Raspberry Pi as a router (lien direct) | I'm setting up a little test network for IoT devices, one isolated a bit from my home network. This is a perfect job for a computer like the Raspberry Pi (or similar computers, such as the Odroid-C2, which is what I'm actually using here). I thought I'd blog the setup details in case anybody else wanted to setup their own isolated home network.Choice of hardwareThe Raspberry Pi B v3 is a fine choice, but there are many alternatives. I'm using the Odroid C2 instead. It's nearly the same, but the chief difference for my purposes is that the Ethernet adapter is native. On the RPi, the Ethernet adapter is actually connected via USB. Network utilities don't like USB Ethernet as much.The choice of hardware dictates the operating system. Download the latest version of Ubuntu for the Odroid C2. They keep moving around where to get it, but you can google "odroid c2 downloads" to find it. My version is Ubuntu MATE 16.04 LTS.Your home networkYour home network likely uses the addresses 192.168.1.xxx. This is also the range that most of the devices I'm testing will use as their initial defaults. Therefore, I've changed my network to something strange that won't share the address range, like 10.20.30.x.sudo bashOn the Internet, help text always prefixes sudo in front of every line. This is tedious. I just open up a root bash prompt instead. All the examples below assume that.Reconfigure the hostnameThe first step for me is always reconfiguring the hostname. I've got a bunch of small systems and VMs, and if I don't remember to reset the hostname, I go crazy. You do this by editing the files /etc/hostname and the file /ets/hosts.vi /etc/hostnamevi /etc/hostsI'm naming this device odroidrouter.Reconfigure networkingAll these small computers seem to be using some form of Debian, which usually uses the ifupdown method of configuring the network. It's in flux and always changing, but my current configuration looks like the following.vi /etc/network/interfacesauto usbnet0allow-hotplug usbnet0iface usbnet0 inet static address 10.20.30.45 netmask 255.255.255.0 gateway 10.20.30.1 dns-nameservers 8.8.8.8 8.8.4.4iface usbnet0 inet6 auto | ★★ | |||
| 2016-10-24 23:58:00 | Lamers: the problem with bounties (lien direct) | In my last two posts, I pointed out that the anti-spam technique known as "DKIM" cryptographically verifies emails. This can be used to verify that some of the newsworthy emails are, indeed, correct and haven't been doctored. I offer a 1 btc (one bitcoin, around ~$600 at current exchange rates) bounty if anybody can challenge this assertion.Unfortunately, bounties attract lamers who think they deserve the bounty. This faked email show _undetectable_ addition of cc: field (& other fields) and whitespace in email body; no tricks #PayUpRob @ErrataRob https://t.co/X8oUplx2UL- ((( Matt Beebe ))) (@VoteBeebe) October 25, 2016This guy insists he wins the bounty because he can add spaces to the email, and add fields like "Cc:" that DKIM doesn't check. Since DKIM ignores extra spaces and only checks important fields, these changes pass. The guy claims it's "doctored" because technically, he has changed things, even though he hasn't actually changed any of the important things (From, Date, Subject, and body content).No. This doesn't qualify for the bounty. It doesn't call into question whether the Wikileaks emails say what they appear to say. It's so obvious that people have already contacted me and passed on it, knowing it wouldn't win the bounty. If I'd pay out this bounty for this lameness, one of the 10 people who came up with the idea before this lamer would get this bounty, not him. It'd probably go to this guy:@ErrataRob super lame i know, but this does pass DKIM sig check in thunderbird. base64 here https://t.co/14EyaBKfNL pic.twitter.com/dG94f5lH8o- Philip (@_miw) October 22, 2016Let me get ahead of the lamers and point to more sophisticated stuff that also doesn't count. The following DKIM verified email appears to say that Hillary admitting she eats kittens. This would be newsworthy if true, and a winner of this bounty if indeed it could trick people.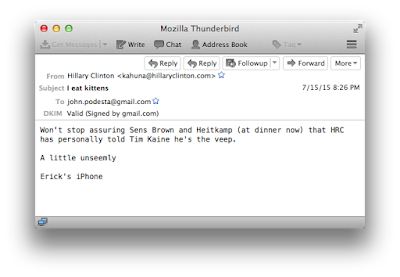 This is in fact also very lame. I mean, it's damn convincing, but only to lamers. You can see my trick by looking at the email on pastebin (http://pastebin.com/wRsnz0Y6) and comparing it to the original (https://wikileaks.org/podesta-emails/emailid/2986).The trick is that I've added extra From/Subject fields before the DKIM header, so DKIM doesn't see them. DKIM only sees the fields after. It tricks other validation tools, such as this online validator. However, email readers (Thunderbi This is in fact also very lame. I mean, it's damn convincing, but only to lamers. You can see my trick by looking at the email on pastebin (http://pastebin.com/wRsnz0Y6) and comparing it to the original (https://wikileaks.org/podesta-emails/emailid/2986).The trick is that I've added extra From/Subject fields before the DKIM header, so DKIM doesn't see them. DKIM only sees the fields after. It tricks other validation tools, such as this online validator. However, email readers (Thunderbi |
||||
| 2016-10-23 21:01:38 | Politifact: Yes we can fact check Kaine\'s email (lien direct) | This Politifact post muddles over whether the Wikileaks leaked emails have been doctored, specifically the one about Tim Kaine being picked a year ago. The post is wrong -- we can verify this email and most of the rest.In order to bloc spam, emails nowadays contain a form of digital signatures that verify their authenticity. This is automatic, it happens on most modern email systems, without users being aware of it.This means we can indeed validate most of the Wikileaks leaked DNC/Clinton/Podesta emails. There are many ways to do this, but the easiest is to install the popular Thunderbird email app along with the DKIM Verifier addon. Then go to the Wikileaks site and download the raw source of the email https://wikileaks.org/podesta-emails/emailid/2986.As you see in the screenshot below, the DKIM signature verifies as true. If somebody doctored the email, such as changing the date, then the signature would not verify. I try this in the email below, changing the date from 2015 to 2016. This causes the signature to fail. If somebody doctored the email, such as changing the date, then the signature would not verify. I try this in the email below, changing the date from 2015 to 2016. This causes the signature to fail. There are some reasons DKIM might fail, specifically if the sender uses short keys. This doesn't apply to GMail, which uses strong 2048 bit keys, as demonstrated in the following screenshot. (No, the average person isn't supposed to understand this screen shot, but experts can). There are some reasons DKIM might fail, specifically if the sender uses short keys. This doesn't apply to GMail, which uses strong 2048 bit keys, as demonstrated in the following screenshot. (No, the average person isn't supposed to understand this screen shot, but experts can). What this means is that the only way this email could've been doctored is if there has been an enormous, nation-state level hack of Google to steal their signing key. It's possible, of course, but extraordinarily improbable.Yes, it's possible that not emails in the Wikileaks dump are legitimate. The ones without DKIM or which use weak keys can be forged. But it's improbable to believe this specific email was forged -- it would need a national-state level hack of Google. That's possible, of course, but it's conspiracy-theory level thinking.Since DKIM verifies this email and most of the others, we conclude that Kaine is "pants on fire" lying about this specific email, and "mostly untrue" in his claim that the Wikileaks emails have been doctored. What this means is that the only way this email could've been doctored is if there has been an enormous, nation-state level hack of Google to steal their signing key. It's possible, of course, but extraordinarily improbable.Yes, it's possible that not emails in the Wikileaks dump are legitimate. The ones without DKIM or which use weak keys can be forged. But it's improbable to believe this specific email was forged -- it would need a national-state level hack of Google. That's possible, of course, but it's conspiracy-theory level thinking.Since DKIM verifies this email and most of the others, we conclude that Kaine is "pants on fire" lying about this specific email, and "mostly untrue" in his claim that the Wikileaks emails have been doctored.As a side note, I offer a 1-BTC (one bit coin, ~600 at today's exchange rate) bounty to anybody who can prove me wrong. If you can doctor the above email, then you win the bounty. Some rules apply (i.e. it needs to be a real doctored email, not a trick). I offer this |
★★ | |||
| 2016-10-21 21:51:27 | Yes, we can validate the Wikileaks emails (lien direct) | Recently, WikiLeaks has released emails from Democrats. Many have repeatedly claimed that some of these emails are fake or have been modified, that there's no way to validate each and every one of them as being true. Actually, there is, using a mechanism called DKIM.DKIM is a system designed to stop spam. It works by verifying the sender of the email. Moreover, as a side effect, it verifies that the email has not been altered.Hillary's team uses "hillaryclinton.com", which as DKIM enabled. Thus, we can verify whether some of these emails are true.Recently, in response to a leaked email suggesting Donna Brazile gave Hillary's team early access to debate questions, she defended herself by suggesting the email had been "doctored" or "falsified". That's not true. We can use DKIM to verify it.You can see the email in question at the WikiLeaks site: https://wikileaks.org/podesta-emails/emailid/5205. The title suggests they have early access to debate questions, and includes one specifically on the death penalty, with the text:since 1973, 156 people have been on death row and later set free. Since 1976, 1,414 people have been executed in the U.SIndeed, during the debate the next day, they asked the question:Secretary Clinton, since 1976, we have executed 1,414 people in this country. Since 1973, 156 who were convicted have been exonerated from the death row.It's not a smoking gun, but at the same time, it both claims they got questions in advance while having a question in advance. Trump gets hung on similar chains of evidence, so it's not something we can easily ignore.Anyway, this post isn't about the controversy, but the fact that we can validate the email. When an email server sends a message, it'll include an invisible "header". They aren't especially hidden, most email programs allow you to view them, it's just that they are boring, so hidden by default. The DKIM header in this email looks like:DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=hillaryclinton.com; s=google; h=from:mime-version:references:in-reply-to:date:message-id:subject:to :cc; bh=EHIyNFKU1g6KhzxpAJQtxaW82g5+cTT3qlzIbUpGoRY=; b=JgW85tkuhlDcythkyCrUMjPIAjHbUVPtgyqu+KpUR/kqQjE8+W23zacIh0DtVTqUGD mzaviTrNmI8Ds2aUlzEFjxhJHtgKT4zbRiqDZS7fgba8ifMKCyDgApGNfenmQz+81+hN 2O | ||||
| 2016-10-21 20:01:27 | Some notes on today\'s DNS DDoS (lien direct) | Some notes on today's DNS outages due to DDoS.We lack details. As a techy, I want to know the composition of the traffic. Is it blindly overflowing incoming links with junk traffic? Or is it cleverly sending valid DNS requests, overloading the ability of servers to respond, and overflowing outgoing link (as responses are five times or more as big as requests). Such techy details and more make a big difference. Was Dyn the only target? Why were non-Dyn customers effected?Nothing to do with the IANA handover. So this post blames Obama for handing control of DNS to the Russians, or some such. It's silly, and not a shred of truth to it. For the record, I'm (or was) a Republican and opposed handing over the IANA. But the handover was a symbolic transition of a minor clerical function to a body that isn't anything like the U.N. The handover has nothing to do with either Obama or today's DDoS. There's no reason to blame this on Obama, other than the general reason that he's to blame for everything bad that happened in the last 8 years.It's not a practice attack. A Bruce Schneier post created the idea of hacking doing "practice" DDoS. That's not how things work. Using a botnot for DDoS always degrades it, as owners of machines find the infections and remove them. The people getting the most practice are the defenders, who learn more from the incident than the attackers do.It's not practice for Nov. 8. I tweeted a possible connection to the election because I thought it'd be self-evidently a troll, but a lot of good, intelligent, well-meaning people took it seriously. A functioning Internet is not involved in counting the votes anywhere, so it's hard to see how any Internet attack can "rig" the election. DDoSing news sources like CNN might be fun -- a blackout of news might make some people go crazy and riot in the streets. Imagine if Twitter went down while people were voting. With this said, we may see DDoS anyway -- lots of kids control large botnets, so it may happen on election day because they can, not because it changes anything.Dyn stupidly uses BIND. According to "version.bind" queries, Dyn (the big DNS provider that is a major target) uses BIND. This is the most popular DNS server software, but it's wrong. It 10x to 100x slower than alternatives, meaning that they need 100x more server hardware in order to deal with DDoS attacks. BIND is also 10x more complex -- it strives to be the reference implementation that contains all DNS features, rather than a simple bit of software that just handles this one case. BIND should never be used for Internet-facing DNS, packages like KnotDNS and NSD should be used instead.Fixing IoT. The persistent rumor is that an IoT botnet is being used. So everything is calling for regulations to secure IoT devices. This is extraordinarily bad. First of all, most of the devices are made in China and shipped to countries not in the United States, so there's little effect our regulations can have. Except they would essentially kill the Kickstarter community coming up with innovative IoT devices. Only very large corporations can afford the regulatory burden involved. Moreover, it's unclear what "security" means. There no real bug/vulnerability being exploited here other than default passwords -- something even the US government has at times refused to recognize as a security "vulnerability".Fixing IoT #2. People have come up with many ways default passwords might be solved, such as having a sticker on the device with a randomly generated password. Getting the firmware to match a printed sticker during manufacturing is a hard, costly problem. I mean, they do it all the time for other reasons, but it starts to become a burden for cheaper device. But in any event, the correct solution is connecting via Bluetooth. That seems to be the most p | ||||
| 2016-10-18 20:19:56 | Trump on cybersecurity: vacuous and populist (lien direct) | Trump has published his policy on cybersecurity. It demonstrates that he and his people do not understand the first thing about cybersecurity.Specifically, he wants “the best defense technologies†and “cyber awareness training for all government employeesâ€. These are well known bad policies in the cybersecurity industry. They are the sort of thing the intern with a degree from Trump University would come up with.Awareness training is the knee-jerk response to any problem. Employees already spend a lot of their time doing mandatory training for everything from environmental friendly behavior, to sexual harassment, to Sarbannes-Oxley financial compliance, to cyber-security. None of it has proven effective, but organizations continue to force it, either because they are required to, or they are covering their asses. No amount of training employees to not click on email attachments helps. Instead, the network must be secure enough that reckless clicking on attachments pose no danger.Belief in a technological Magic Pill that will stop hackers is common among those who know nothing about cybersecurity. Such pills don't exist. The least secure networks already have “the best defense technologiesâ€. Things like anti-virus, firewalls, and intrusion prevention systems do not stop hackers by themselves – but area instead tools that knowledgeable teams use in order to make their jobs easier. It's like how a chisel doesn't make a sculpture by itself, but is instead just a tool used by the artist. The government already has all the technology it needs. It's problems instead derive from the fact that they try to solve their problems the way Trump does – by assigning the task to some Trump University intern.Lastly, Trump suggests that on the offensive side, we need to improve our offensive abilities, in order to create a cyber deterrence. We already do that. The United States is by far the #1 nation in offensive capabilities. In 2015, Obama forced China to the table, to sign an agreement promising they'd stop hacking us. Since then, China has kept the agreement, and has dropped out of the news as being the source of cyber attacks. Privately, many people in government tell me its because we did some major cyber attack in China that successfully deterred them.[if gte mso 9]> [if gte mso 9]> Normal 0 false false false EN-US JA X-NONE | Guideline | |||
| 2016-10-12 15:21:46 | WTF Yahoo/FISA search in kernel? (lien direct) | A surprising detail in the Yahoo/FISA email search scandal is that they do it with a kernel module. I thought I'd write up some (rambling) notes.What the government was searching forAs described in the previoius blog post, we'll assume the government is searching for the following string, and possibly other strings like it within emails:### Begin ASRAR El Mojahedeen v2.0 Encrypted Message ###I point this out because it's simple search identifying things. It's not natural language processing. It's not searching for phrases like “bomb presidentâ€.Also, it's not AV/spam/childporn processing. Those look at different things. For example, filtering message containing childporn involves calculating a SHA2 hash of email attachments and looking up the hashes in a table of known bad content. This is quite different from searching.The Kernel vs. User SpaceOperating systems have two parts, the kernel and user space. The kernel is the operating system proper (e.g. the “Linux kernelâ€). The software we run is in user space, such as browsers, word processors, games, web servers, databases, GNU utilities [sic], and so on.The kernel has raw access to the machine, memory, network devices, graphics cards, and so on. User space has virtual access to these things. The user space is the original “virtual machinesâ€, before kernels got so bloated that we needed a third layer to virtualize them too.This separation between kernel and user has two main benefits. The first is security, controlling which bit of software has access to what. It means, for example, that one user on the machine can't access another's files. The second benefit is stability: if one program crashes, the others continue to run unaffected.Downside of a Kernel ModuleWriting a search program as a kernel module (instead of a user space module) defeats the benefits of user space programs, making the machine less stable and less secure.Moreover, the sort of thing this module does (parsing emails) has a history of big gapping security flaws. Parsing stuff in the kernel makes cybersecurity experts run away screaming in terror.On the other hand, people have been doing security stuff (SSL implementations and anti-virus scanning) in the kernel in other situations, so it's not unprecedented. I mean, it's still wrong, but it's been done before.Upside of a Kernel ModuleIf doing this is as a kernel module (instead of in user space) is so bad, then why does Yahoo do it? It's probably due to the widely held, but false, belief that putting stuff in the kernel makes it faster.Everybody knows that kernels are faster, for two reasons. First is that as a program runs, making a system call switches context, from running in user space to running in kernel space. This step is expensive/slow. Kernel modules don't incur this expense, because code just jumps from one location in the kernel to another. The second performance issue is virtual memory, where reading memory requires an extra step in user space, to translate the virtual memory address to a physical one. Kernel modules access physical memory directly, without this extra step.But everyone is wrong. Using features like hugepages gets rid of the cost of virtual memory translation cost. There are ways to mitigate the cost of user/kernel transitions, such as moving data in bulk instead of a little bit at a time. Also, CPUs have improved in recent years, dramatically reducing the cost of a kernel/user transition.The problem we face, though, is inertia. Everyone knows moving modules into the kernel makes things faster. It's hard getting them to un-learn what they've been taught.Also, following this logic, Yahoo may already hav | Yahoo | |||
| 2016-10-06 02:47:52 | What the Yahoo NSA might\'ve looked for (lien direct) | The vague story about Yahoo searching emails for the NSA was cleared up today with various stories from other outlets [1]. It seems clear a FISA court order was used to compel Yahoo to search all their customer's email for a pattern (or patterns). But there's an important detail still missing: what specifically were they searching for? In this post, I give an example.The NYTimes article explains the search thusly:Investigators had learned that agents of the foreign terrorist organization were communicating using Yahoo's email service and with a method that involved a “highly unique†identifier or signature, but the investigators did not know which specific email accounts those agents were using, the officials said.What they are likely referring it is software like "Mujahideen Secrets", which terrorists have been using for about a decade to encrypt messages. It includes a unique fingerprint/signature that can easily be searched for, as shown below.In the screenshot below, I use this software to type in a secret message: I then hit the "encrypt" button, and get the following, a chunk of random looking text: I then hit the "encrypt" button, and get the following, a chunk of random looking text: This software encrypts, but does not send/receive messages. You have to do that manually yourself. It's intended that terrorists will copy/paste this text into emails. They may also paste the messages into forum posts. Encryption is so good that nobody, not even the NSA, can crack properly encrypted messages, so it's okay to post them to public forums, and still maintain secrecy.In my case, I copy/pasted this encrypted message into an email message from one of my accounts and sent to to one of my Yahoo! email accounts. I received the message shown below: This software encrypts, but does not send/receive messages. You have to do that manually yourself. It's intended that terrorists will copy/paste this text into emails. They may also paste the messages into forum posts. Encryption is so good that nobody, not even the NSA, can crack properly encrypted messages, so it's okay to post them to public forums, and still maintain secrecy.In my case, I copy/pasted this encrypted message into an email message from one of my accounts and sent to to one of my Yahoo! email accounts. I received the message shown below: The obvious "highly unique signature" the FBI should be looking for, to catch this software, is the string:### Begin ASRAR El Mojahedeen v2.0 Encrypted Message ###Indeed, if this is the program the NSA/FBI was looking for, they've now caught this message in their dragnet of incoming Yahoo! mail. This is a bit creepy, which is why I added a plea to the message, in unencrypted form, asking them not to rendition or drone strike me. Since the NSA can use such signatures to search traffic from websites, as well as email traffic, there's a good change you've been added to their "list" simply for reading this blog post. For fun, send this blogpost to family or friends you don't particularly like, in order to get them on the watch list as well. The obvious "highly unique signature" the FBI should be looking for, to catch this software, is the string:### Begin ASRAR El Mojahedeen v2.0 Encrypted Message ###Indeed, if this is the program the NSA/FBI was looking for, they've now caught this message in their dragnet of incoming Yahoo! mail. This is a bit creepy, which is why I added a plea to the message, in unencrypted form, asking them not to rendition or drone strike me. Since the NSA can use such signatures to search traffic from websites, as well as email traffic, there's a good change you've been added to their "list" simply for reading this blog post. For fun, send this blogpost to family or friends you don't particularly like, in order to get them on the watch list as well. |
Yahoo | |||
| 2016-10-04 19:58:59 | The Yahoo-email-search story is garbage (lien direct) | Joseph Menn (Reuters) is reporting that Yahoo! searched emails for the NSA. The details of the story are so mangled that it's impossible to say what's actually going on.The first paragraph says this:Yahoo Inc last year secretly built a custom software program to search all of its customers' incoming emailsThe second paragraph says this:The company complied with a classified U.S. government demand, scanning hundreds of millions of Yahoo Mail accountsWell? Which is it? Did they "search incoming emails" or did they "scan mail accounts"? Whether we are dealing with emails in transmit, or stored on the servers, is a BFD (Big Fucking Detail) that you can't gloss over and confuse in a story like this. Whether searches are done indiscriminately across all emails, or only for specific accounts, is another BFD.The third paragraph seems to resolve this, but it doesn't:Some surveillance experts said this represents the first case to surface of a U.S. Internet company agreeing to an intelligence agency's request by searching all arriving messages, as opposed to examining stored messages or scanning a small number of accounts in real time.Who are these "some surveillance experts"? Why is the story keeping their identities secret? Are they some whistleblowers afraid for their jobs? If so, then that should be mentioned. In reality, they are unlikely to be real surveillance experts, but just some random person that knows slightly more about the subject than Joseph Menn, and their identities are being kept secret in order to prevent us from challenging these experts -- which is a violation of journalistic ethics.And, are they analyzing the raw information the author sent them? Or are they opining on the garbled version of events that we see in the first two paragraphs.It is not known what information intelligence officials were looking for, only that they wanted Yahoo to search for a set of characters. That could mean a phrase in an email or an attachment, said the sources, who did not want to be identified.What the fuck is a "set of characters"??? Is this an exact quote for somewhere? Or something the author of the story made up? The clarification of what this "could mean" doesn't clear this up, because if that's what it "actually means", then why not say this to begin with?What outsiders know about the NSA/FBI's ability to ask for strong selectors (email addresses). What what we don't know about is their ability to search all emails, regardless of account, for arbitrary keywords/phases. If that's what's going on, then this would be a huge story. But the story doesn't make it clear that this is actually what's going on -- just strongly implies it.There are many other ways to interpret this story. For example, the government may simply be demanding that when Yahoo satisfies demands for emails (based on email addresses), that it does so from the raw incoming stream, before it hits spam/malware filters. Or, they may be demanding that Yahoo satisfies their demands with more secrecy, so that the entire company doesn't learn of the email addresses that a FISA order demands. Or, the government may be demanding that the normal collection happen in real time, in the seconds that emails arrive, instead of minutes later.Or maybe this isn't an NSA/FISA story at all. Maybe the DHS has a cybersecurity information sharing program that distributes IoCs (indicators of compromise) to companies under NDA. Because it's a separate program under NDA, Yahoo would need to setup a email malware scanning system separate from their existing malware system in order to use those IoCs.My point is this: the story is full of mangled details that really tell us nothing. I can come up with multiple, unrelated s | Yahoo | |||
| 2016-10-01 23:01:15 | No, Trump\'s losses doesn\'t allow tax avoidance (lien direct) | The New York Times is reporting that Tump lost nearly a billion dollars in 1995, and this would enable tax avoidance for 18 years. No, it doesn't allow "avoidance". This is not how taxes work.Let's do a little story problem:You invest in a broad basket of stocks for $100,000You later sell them for $110,000Capital gains rate on this is 20%How much taxes do you owe?Obviously, since you gained $10,000 net, and tax rate is 20%, you then owe $2,000 in taxes.But this is only because losses offset gains. All the stocks in your basket didn't go up 10%. Some went up more, some actually lost money. It's not unusual that the losing stocks might go down $50,000, while the gainers go up $60,000, thus giving you the 10% net return, if you are investing in high-risk/high-reward stocks.What if instead we change the tax code to only count the winners, ignoring the losing stocks. Now, instead of owing taxes on $10,000, you owe taxes on $60,000. At 20% tax rate, this comes out to $12,000 in taxes -- which is actually more than you earned on your investments.Taxing only investments that win, while ignoring losers, is bad tax policy. It would mean, essentially, taxing investments at greater than 100% rate. This would mean people would stop investing, because it would only lose money. It's a stupid tax policy, which is why no country does it. All countries tax the net gain on investments, gains minus losses.In the above story problem, we bought and sold the stock all at once. In the real world, people buy and sell a little bit at time over the years. It doesn't change the basic math. For that reason, losses in one year can be carried forward to offset gains in later years. You can't do the reverse, offset previous years, because you've already paid the taxes. You don't want the government giving Trump a $200-million tax refund check when he loses $1-billion.Thus, there's nothing wrong with offsetting $1 billion gains in later years with $1 billion in losses. He's not avoiding taxes on the gains for 18 years -- it instead means that he has no gains over that 18 year period. That he might have been earning any money, net, for 20 years is the big story -- not that he's taking advantage of some loophole in the tax law.Offsetting future gains with past losses is not a loophole. Everybody who invests, and hence sometimes has losses, does it. Every country's tax code, like France, Sweden, or any socialist paradise you care to name, works the same way.That's why Trump is going to win this election. The press knows how taxes work, but they intentionally twist the story to make Trump look bad. The real story with these returns is that Trump is, in fact, a shitty investor, not that he's a tax cheat. By the way, I am a tax cheat. I had losses in the 2009 crash. Instead of immediately using those losses to offset gains in 2010 and 2011, I waited until Obamacare came into effect, which raised my tax rates. Only then did I claim the losses against gains, saving an extra few percent on my tax bill, and screwing the government out of a few thousand dollars (in a totally legal way).There's a few bad tax loopholes in the system, like the ones hedge fund managers use, but overall, you really can't avoid paying taxes. You can shift things around a bit to change which taxes you pay, such as the above example, but that the rich use tax loopholes to avoid taxes is a myth. Indeed, in terms of taxes payments received by the government, most of them come from the rich -- at a higher rate than they come from the poor -- minus the odd hedge fund manager. |
||||
| 2016-09-28 19:01:08 | Some technical notes on the PlayPen case (lien direct) | In March of 2015, the FBI took control of a Tor onion childporn website ("PlayPen"), then used an 0day exploit to upload malware to visitors's computers, to identify them. There is some controversy over the warrant they used, and government mass hacking in general. However, much of the discussion misses some technical details, which I thought I'd discuss here.IP addressIn a post on the case, Orin Kerr claims:retrieving IP addresses is clearly a searchHe is wrong. Uploading malware to gather other things (hostname, username, MAC address) is clearly a search. But discovering the IP address is a different thing.Today's homes contain many devices behind a single router. The home has only one public IP address, that of the router. All the other devices have local IP addresses. The router then does network address translation (NAT) in order to convert outgoing traffic to all use the public IP address.The FBI sought the public IP address of the NAT/router, not the local IP address of the perp's computer. The malware ("NIT") didn't search the computer for the IP address. Instead the NIT generated network traffic, destined to the FBI's computers. The FBI discovered the suspect's public IP address by looking at their own computers.Historically, there have been similar ways of getting this IP address (from a Tor hidden user) without "hacking". In the past, Tor used to leak DNS lookups, which would often lead to the user's ISP, or to the user's IP address itself. Another technique would be to provide rich content files (like PDF) or video files that the user would have to be downloaded to view, and which then would contact the Internet (contacting the FBI's computers) themselves bypassing Tor.Since the Fourth Amendment is about where the search happens, and not what is discovered, it's not a search to find the IP address in packets arriving at FBI servers. How the FBI discovered the IP address may be a search (running malware on the suspect's computer), but the public IP address itself doesn't necessarily mean a search happened.In any event, if not for the IP address, then PlayPen searches still happened for the hostname, username, and MAC address. Imagine the FBI gets a search warrant, shows up at the suspect's house, and finds no child porn. They then look at the WiFi router, and find that suspected MAC address is indeed connected. They then use other tools to find that the device with that MAC address is located in the neighbor's house -- who has been piggybacking off the WiFi.It's a pre-crime warrant (#MinorityReport)The warrant allows the exploit/malware/search to be used whenever somebody logs in with a username and password.The key thing here is that the warrant includes people who have not yet created an account on the server at the time the warrant is written. They will connect, create an account, log in, then start accessing the site.In other words, the warrant includes people who have never committed a crime when the warrant was issued, but who first commit the crime after the warrant. It's a pre-crime warrant. Sure, it's possible in any warrant to catch pre-crime. For example, a warrant for a drug dealer may also catch a teenager making their first purchase of drugs. But this seems quantitatively different. It's not targeting the known/suspected criminal -- it's targeting future criminals.This could ea | Guideline | ★★★★★ | ||
| 2016-09-28 09:25:13 | Beware: Attribution & Politics (lien direct) | tl;dr - Digital location data can be inherently wrong and it can be spoofed. Blindly assuming that it is accurate can make an ass out of you on twitter and when regulating drones. Guest contributor and friend of Errata Security Elizabeth Wharton is an attorney and host of the technology-focused weekly radio show "Buzz Off with Lawyer Liz" on America's Web Radio. This post is merely her musings and not legal advice.Filtering through various campaign and debate analysis on social media, a tweet caught my eye. The message itself was not the concern and the underlying image has since been determined to be fake. Rather, I was stopped by the140 character tweet's absolute certainty that internet user location data is infallible. The author presented a data map as proof without question, caveat, or other investigation. Boom, mic drop - attribution!According to the tweeting pundit, "Russian trollbots" are behind the #TrumpWon hashtag trending on Twitter.  The proof? The twitter post claims that the Trendsmap showed the initial hashtag tweets as originating from accounts located in Russia. Within the first hour the tweet and accompanying map graphic was "liked" 1,400 times and retweeted 1,495 times. A gotcha moment because a pew-pew map showed that the #TrumpWon hashtag originated from Twitter accounts located in Russia. Boom, mic drop - attribution!Except, not so fast. First, Trendsmap has since clarified that the map and data in the tweet above are not theirs (the Washington Post details the faked data/map ). Moreover, location data is tricky. According to the Trendsmap FAQ page they use the location provided in a user's profile and GeoIP provided by Google. Google's GeoIP is crafted using a proprietary system and other databases such as MaxMind. IP mapping is not an exact art. Kashmir Hill, editor of Fusion's Real Future, and David Maynor, delved into the issues and inaccuracies of IP mapping earlier this year. Kashmir wrote extensively on their findings and how phantom IP addresses and MaxMind's use of randomly selected default locations created digital hells for individuals all over the country - Internet Mapping Glitch Turned Random Farm into Digital Hell.Reliance on such mapping and location information as an absolute has tripped up law enforcement and is poised to trip up the drone industry. Certain lawmakers like to point to geofencing and other location applications as security and safety cure-all solutions. Sen. Schumer (D-N.Y.) previously included geofencing as a key element of his 2015 drone safety bill. Geofencing as a safety measure was mentioned during Tuesday's U.S. House Small Business Committee hearing on Commercial Drone Operations. With geofencing, the drone is programmed to prohibit operations above a certain height or to keep out of certain locations. Attempt to fly in a prohibited area and the aircraft will automatically shut down. Geofencing relies on location data, including geospatial data collected from a variety of sources. As seen with GeoIP, data can be wrong. Additionally, the data must be interpreted and analyzed by the aircraft's software systems. Aircraft systems are not bui The proof? The twitter post claims that the Trendsmap showed the initial hashtag tweets as originating from accounts located in Russia. Within the first hour the tweet and accompanying map graphic was "liked" 1,400 times and retweeted 1,495 times. A gotcha moment because a pew-pew map showed that the #TrumpWon hashtag originated from Twitter accounts located in Russia. Boom, mic drop - attribution!Except, not so fast. First, Trendsmap has since clarified that the map and data in the tweet above are not theirs (the Washington Post details the faked data/map ). Moreover, location data is tricky. According to the Trendsmap FAQ page they use the location provided in a user's profile and GeoIP provided by Google. Google's GeoIP is crafted using a proprietary system and other databases such as MaxMind. IP mapping is not an exact art. Kashmir Hill, editor of Fusion's Real Future, and David Maynor, delved into the issues and inaccuracies of IP mapping earlier this year. Kashmir wrote extensively on their findings and how phantom IP addresses and MaxMind's use of randomly selected default locations created digital hells for individuals all over the country - Internet Mapping Glitch Turned Random Farm into Digital Hell.Reliance on such mapping and location information as an absolute has tripped up law enforcement and is poised to trip up the drone industry. Certain lawmakers like to point to geofencing and other location applications as security and safety cure-all solutions. Sen. Schumer (D-N.Y.) previously included geofencing as a key element of his 2015 drone safety bill. Geofencing as a safety measure was mentioned during Tuesday's U.S. House Small Business Committee hearing on Commercial Drone Operations. With geofencing, the drone is programmed to prohibit operations above a certain height or to keep out of certain locations. Attempt to fly in a prohibited area and the aircraft will automatically shut down. Geofencing relies on location data, including geospatial data collected from a variety of sources. As seen with GeoIP, data can be wrong. Additionally, the data must be interpreted and analyzed by the aircraft's software systems. Aircraft systems are not bui |
Guideline | ★★ | ||
| 2016-09-18 21:46:34 | Why Snowden won\'t be pardoned (lien direct) | Edward Snowden (NSA leakerblower) won't be pardoned. I'm not arguing that he shouldn't be pardoned, but that he won't be pardoned. The chances are near zero, and the pro-pardon crowd doesn't seem to be doing anything to cange this. This post lists a bunch of reasons why. If your goal is to get him pardoned, these are the sorts of things you'll have to overcome.The tl;dr list is this:Obama hates whistleblowersObama loves the NSAA pardon would be betrayalSnowden leaked because he was disgruntled, not because he was a man of conscience (***)Snowden hasn't yet been convictedSnowden leaked too muchSnowden helped Russian intelligenceNothing was found to be illegal or unconstitutionalObama hates whistleblowersObama campaigned promising to be the most transparent president in history. Among his campaign promises are:Protect Whistleblowers: Often the best source of information about waste, fraud, and abuse in government is an existing government employee committed to public integrity and willing to speak out. Such acts of courage and patriotism, which can sometimes save lives and often save taxpayer dollars, should be encouraged rather than stifled as they have been during the Bush administration. We need to empower federal employees as watchdogs of wrongdoing and partners in performance. Barack Obama will strengthen whistleblower laws to protect federal workers who expose waste, fraud, and abuse of authority in government. Obama will ensure that federal agencies expedite the process for reviewing whistleblower claims and whistleblowers have full access to courts and due process.That sounds like it was tailor made for Snowden, right? But Obama actual actions as president have been the opposite, at least where national security is concerned. Obama has prosecuted more whistleblowers under the espionage act than any other president – indeed, more than all previous presidents combined [**]. Moreover, Obama's prosecutions [**] have clearly politically motivated. Others, like Patreus and Clinton, have not been prosecuted with the same fervor for mishandling classified information. Obviously, Obama's actions here have not been based on any principle.If Obama was willing to prosecute those for minor leaks, he's certainly motivated to prosecute Snowden for his huge leak. That politicians are never punished for their failures to follow through on campaign promises means that Obama doesn't care. Obama hasn't closed down Gitmo after 8 years, despite promising that'd be his first task in office.In order for the pro-pardon campaign to succeed, they are going to have to repeatedly hold Obama's feet to the fire. They need to keep pointing out Obama's many transparency promises. They'll have to point out how Obama's campaign promises inspired Snowden, and that it was Obama's failure to uphold his campaign promises that led Snowden to his actions. Blame Obama.Obama loves the NSAI think it was William Gates in his book who noted that Presidents, even the left-wing ones, quickly get subverted by the military. The military is apolitical, and takes the concept of “Commander in Chief†seriously. When the President says “jumpâ€, they say “how highâ€. In contrast, the President struggles with civilian departments under his nominal control, who passively resist his orders.The NSA is a military organization (as opposed to the CIA, which is civilian). Therefore, the President loves the NSA. It's one of the few organization that does what he wants.Possibly more important is the fact that Obama wi | ||||
| 2016-09-17 01:14:36 | Review: "Snowden" (2016) (lien direct) | tldr:If you are partisan toward Snowden, you'll like the movie.If you know little about Snowden, it's probably too long/slow -- you'll be missing the subtext.If you are anti-Snowden, you'll hate it of course.The movie wasn't bad. I was expecting some sort of over-dramatization, a sort of Bourne-style movie doing parkour through Hong Kong ghettos. Or, I expected a The Fifth Estate sort of movie that was based on the quirky character of Assange. But instead, the movie was just a slight dramatization of the events you (as a Snowden partisan) already know. Indeed, Snowden is a boring protagonist in the movie -- which makes the movie good. All the other characters in the movie are more interesting than the main character. Even the plot isn't all that interesting -- it's just a simple dramatization of what happens -- it's that slow build-up of tension toward the final reveal that keeps your attention.In other words, it's clear that if you like Snowden, understand the subtext, you'll enjoy riding along on this slow buildup of tension.Those opposed to Snowden, however, will of course gag on the one-side nature of the story. There's always two sides to every story. While the film didn't go overboard hyping Snowden's side, it was still partisan, mostly ignoring the opposing side. I can imagine all my friends who work for government walking out in anger, not being able to tolerate this one-sided view of the events. I point this out because with the release of this movie, there's also been a surge in the "Pardon Snowden" movement. No, the chances of that are nil. Even though such a thing seems obvious to you, it's only because you haven't seen the other side.So if you don't like Snowden, at best you'll be bored, at worst you'll be driven out of the theater in anger.I don't think the movie stands alone, without all this subtext we already know. So if you haven't been following along with the whole story, I don't think you'll enjoy it.Finally, there's watching everyone else in the audience. They seemed to like it, and they seemed to "get" the key points the director was trying to make. It was a rather slow Friday night for all the movies being shown, so the theater wasn't empty, but neither was it very full. I'd guess everyone there already had some interest in Snowden. Obviously, from the sign out front, they don't expect as much interest in this film as they do in Bridget Jones' Baby and Blair Witch 2. |
||||
| 2016-09-11 23:56:29 | What\'s the testimonial of passwords? (lien direct) | In this case described by Orin Kerr, the judge asks if entering a password has any testimonial other than "I know the password". Well, rather a lot. A password is content. While it's a foregone conclusion that this encrypted drive here in this case belongs to the suspect, the password may unlock other things that currently cannot be tied to the suspect. Maybe the courts have an answer to this problem, but in case they haven't, I thought I'd address this from a computer-science point of view.Firstly, we have to address the phrasing of entering a password, rather than disclosing the password. Clearly, the court is interested in only the content of the disk drive the password decrypts, and uninterested in the password itself. Yet, entering a password is the same as disclosing it. Technically, there's no way to enter a password in such a way that it can't be recorded. I don't know the law here, and whether courts would protect this disclosure, but for the purposes of this blog post, "entering" is treated the same as "disclosing".Passwords have content. This paper focuses on one real, concrete example, but let's consider some hypothetical cases first.As is well-known, people often choose the birth dates of their children as the basis for passwords. Imagine a man has a password "emily97513" -- and that he has an illegitimate child named "Emily" who was born on May 13, 1997. Such a password would be strong evidence in a paternity suite.As is well-known, people base passwords on sports teams. Imagine a password is "GoBears2017", strong evidence the person is a fan of the Chicago Bears, despite testimony in some case that he's never been to Chicago.Lastly, consider a password "JimmyHoffaDieDieDie" in a court case where somebody is suspected of having killed Jimmy Hoffa.But these are hypotheticals; now let's consider a real situation with passwords. Namely, good passwords are unique. By unique we mean that good passwords are chosen such that they are they so strange that nobody else would ever have chosen that password.For example, Wikileaks published many "insurance" files -- encrypted files containing leaks that nobody could decrypt. This allowed many people to mirror leak data without actually knowing the contents of the leaks. In a book on Wikileaks, the Guardian inadvertently disclosed that the password to the Manning leaks was ACollectionOfDiplomaticHistorySince_1966_ToThe_PresentDay#. It was then a simple matter of attempting to decrypt the many Wikileaks insurance files until the right one was found.In other words, the content of the password was used to discover the files it applied to.Another example is password leaks. Major sites like LinkedIn regularly get hacked and get account details dumped on the Internet. Sites like HaveIBennPwned.com track such leaks. Given a password, it's possible to search these dumps for corresponding email addresses. Thus, hypothetically, once law enforcement knows a person's password, they can then search for email accounts the user might hold that they might not previously have know about.Statistically, passwords are even more unique (sic) than fingerprints, DNA testing, and other things police regularly relying upon (though often erroneously) as being "unique". Consider the password kaJVD7VqcR. While it's only 10 character long, it's completely unique. I just googled it to make sure -- and got zero hits. The chances of another random 10 character password matching this one is one in 1018 chances. In other words, if a billion people each chose a billion random passwords, only then would you have a chance that somebody would pick this same random password.Thus | ★★★★ | |||
| 2016-08-31 11:57:20 | A quick lesson in Political Correctness (lien direct) | It's hard to see Political Correctness in action when it's supporting your own political beliefs. It's easier seen from the other side. You can see in in the recent case of football player Colin Kaepernick, who has refused to stand for the national anthem. Many are condemning him, on the grounds that his speech is not politically correct.For example, ex-teammate Alex Boone criticizes him for disrespecting the flag, because his brother has friends who died in the wars in Iraq. Others in the NFL like Burgess Owen and coach Ron Rivera have made similar statements.If you think Kaepernick is wrong, then argue that he's wrong. Don't argue that he shouldn't speak on the grounds that he's not Politically Correct, offending veterans, or is a bad citizen.We live in a country of freedom, where anyone is free to not stand and salute the flag or sing the anthem. So many have grievances of some sort or another that you'd think more would be availing themselves of this freedom. The problem here is not that Kaepernick does it, but that so few others do it as well. The problem here is Political Correctness. | ★★★★★ | |||
| 2016-08-26 23:01:43 | Notes on that StJude/MuddyWatters/MedSec thing (lien direct) | I thought I'd write up some notes on the StJude/MedSec/MuddyWaters affair. Some references: [1] [2] [3] [4].The story so fartl;dr: hackers drop 0day on medical device company hoping to profit by shorting their stockSt Jude Medical (STJ) is one of the largest providers of pacemakers (aka. cardiac devices) in the country, around ~$2.5 billion in revenue, which accounts for about half their business. They provide "smart" pacemakers with an on-board computer that talks via radio-waves to a nearby monitor that records the functioning of the device (and health data). That monitor, "Merlin@Home", then talks back up to St Jude (via phone lines, 3G cell phone, or wifi). Pretty much all pacemakers work that way (my father's does, although his is from a different vendor).MedSec is a bunch of cybersecurity researchers (white-hat hackers) who have been investigating medical devices. In theory, their primary business is to sell their services to medical device companies, to help companies secure their devices. Their CEO is Justine Bone, a long-time white-hat hacker.Muddy Waters is an investment company known for investigating companies, finding problems like accounting fraud, and profiting by shorting the stock of misbehaving companies.Apparently, MedSec did a survey of many pacemaker manufacturers, chose the one with the most cybersecurity problems, and went to Muddy Waters with their findings, asking for a share of the profits Muddy Waters got from shorting the stock.Muddy Waters published their findings in [1] above. St Jude published their response in [2] above. They are both highly dishonest. I point that out because people want to discuss the ethics of using 0day to short stock when we should talk about the ethics of lying."Why you should sell the stock" [finance issues]In this section, I try to briefly summarize Muddy Water's argument why St Jude's stock will drop. I'm not an expert in this area (though I do a bunch of investment), but they do seem flimsy to me.Muddy Water's argument is that these pacemakers are half of St Jude's business, and that fixing them will first require recalling them all, then take another 2 year to fix, during which time they can't be selling pacemakers. Much of the Muddy Waters paper is taken up explaining this, citing similar medical cases, and so on.If at all true, and if the cybersecurity claims hold up, then yes, this would be good reason to short the stock. However, I suspect they aren't true -- and they are simply trying to scare people about long-term consequences allowing Muddy Waters to profit in the short term.@selenakyle on Twitter suggests this interest document [4] about market-solutions to vuln-disclosure, if you are interested in this angle of things.The 0day being droppedWell, they didn't actually drop 0day as such, just claims that 0day exists -- that it's been "demonstrated". Reading through their document a few times, I've created a list of the 0day they found, to the granularity that | Guideline | Deloitte | ||
| 2016-08-25 18:16:46 | Notes on the Apple/NSO Trident 0days (lien direct) | I thought I'd write up some comments on today's news of the NSO malware using 0days to infect human rights activist phones. For full reference, you want to read the Citizen's Lab report and the Lookout report.Press: it's news to you, it's not news to usI'm seeing breathless news articles appear. I dread the next time that I talk to my mom that she's going to ask about it (including "were you involved"). I suppose it is new to those outside the cybersec community, but for those of us insiders, it's not particularly newsworthy. It's just more government malware going after activists. It's just one more set of 0days.I point this out in case press wants to contact for some awesome sounding quote about how exciting/important this is. I'll have the opposite quote.Don't panic: all patches fix 0daysWe should pay attention to context: all patches (for iPhone, Windows, etc.) fix 0days that hackers can use to break into devices. Normally these 0days are discovered by the company itself or by outside researchers intending to fix (and not exploit) the problem. What's different here is that where most 0days are just a theoretical danger, these 0days are an actual danger -- currently being exploited by the NSO Group's products. Thus, there's maybe a bit more urgency in this patch compared to other patches.Don't panic: NSA/Chinese/Russians using secret 0days anywayIt's almost certain the NSA, the Chinese, and the Russian have similar 0days. That means applying this patch makes you safe from the NSO Group (for a while, until they find new 0days), but it's unlikely this patch makes you safe from the others.Of course it's multiple 0daysSome people are marveling how the attack includes three 0days. That's been the norm for browser exploits for a decade now. There's sandboxes and ASLR protections to get through. There's privilege escalation to get into the kernel. And then there's persistence. How far you get in solving one or more of these problems with a single 0day depends upon luck.It's actually four 0daysWhile it wasn't given a CVE number, there was a fourth 0day: the persistence using the JavaScriptCore binary to run a JavaScript text file. The JavaScriptCore program appears to be only a tool for developers and not needed the functioning of the phone. It appears that the iOS 9.3.5 patch disables. While technically, it's not a coding "bug", it's still a design bug. 0days solving the persistence problem (where the malware/implant runs when phone is rebooted) are worth over a hundred thousand dollars all on their own.That about wraps it up for VEPVEP is Vulnerability Equities Process that's supposed to, but doesn't, manage how the government uses 0days it acquires.Agitators like the EFF have been fighting against the NSA's acquisition and use of 0days, as if this makes us all less secure. What today's incident shows is that acquisition/use of 0days will be widespread around the world, regardless what the NSA does. It's be nice to get more transparency about what they NSA is doing through the VEP process, but the reality is the EFF is never going to get anything close to what it's agitating for.That about wraps is up for WassenaarWassenaar is an internal arms control "treaty". Left-wing agitators convinced the Wassenaar folks to add 0days and malware to the treaty -- with horrific results. There is essentially no difference between bad code and good code, only how it's used, so the the Wassenaar extensions have essentially outlawed all good code and security research | ★★★ | |||
| 2016-08-25 00:08:49 | Another lesson in confirmation bias (lien direct) | The biggest problem with hacker attribution is the confirmation bias problem. Once you develop a theory, your mind shifts to distorting evidence trying to prove the theory. After a while, only your theory seems possible as one that can fit all your carefully selected evidence.You can watch this happen in two recent blogposts [1] [2] by Krypt3ia attributing bitcoin payments to the Shadow Broker hackers as coming from the government (FBI, NSA, TAO). These posts are absolutely wrong. Nonetheless, the press has picked up on the story and run with it [*]. [Note: click on the pictures in this post to blow them up so you can see them better].The Shadow Brokers published their bitcoin address (19BY2XCgbDe6WtTVbTyzM9eR3LYr6VitWK) asking for donations to release the rest of their tools. They've received 66 transactions so far, totally 1.78 bitcoin, or roughly $1000 at today's exchange rate.Bitcoin is not anonymous by pseudonymous. Bitcoin is a public ledger with all transaction visible by everyone. Sometimes we can't tie addresses back to people, but sometimes we can. There are a lot of researchers who spent a lot of time on "taint anlysis" trying to track down the real identity of evildoers. Thus, it seems plausible that we might be able to discover the identities of those people making contributions to Shadow Brokers.The first of Krypt3ia's errant blogposts tries to use the Bitcoin taint analysis plugin within Maltego in order to do some analysis on the Shadow Broker address. What he found was links to the Silk Road address -- the address controlled by the FBI since they took down that darknet marketplace several years ago. Therefore, he created the theory that the government (FBI? NSA? TAO?) was up to some evil tricks, such as trying to fill the account with money so that they could then track where the money went in the public blockchain.But he misinterpreted the links. (He was wrong.) There were no payments from the Silk Road accounts to the Shadow Broker account. Instead, there were people making payments to both accounts. As a prank.To demonstrate how this prank wors, I made my own transaction, where I pay money to the Shadow Brokers (19BY2...), to Silk Road (1F1A...), and to a few other well-known accounts controlled by the government. The point here is that anybody can do these shenanigans. That government controlled addresses are involved means nothing. They are public, and anybody can send coin to them.That blogpost points to yet more shenanigans, such as somebody "rick rolling", to confirm that TAO hackers were involved. What you see in the picture below is a series of transactions using bitcoin addresses containing the phrase "never gonna give you up", the title of Rich Astley's song (I underlined the words in red). The point here is that anybody can do these shenanigans. That government controlled addresses are involved means nothing. They are public, and anybody can send coin to them.That blogpost points to yet more shenanigans, such as somebody "rick rolling", to confirm that TAO hackers were involved. What you see in the picture below is a series of transactions using bitcoin addresses containing the phrase "never gonna give you up", the title of Rich Astley's song (I underlined the words in red). |
Guideline | |||
| 2016-08-21 19:26:06 | A lesson in social engineering: president debates (lien direct) | In theory, we hackers are supposed to be experts in social engineering. In practice, we get suckered into it like everyone else. I point this out because of the upcoming presidential debates between Hillary and Trump (and hopefully Johnson). There is no debate, there is only social engineering.Some think Trump will pull out of the debates, because he's been complaining a lot lately that they are rigged. No. That's just because Trump is a populist demagogue. A politician can only champion the cause of the "people" if there is something "powerful" to fight against. He has to set things up ahead of time (debates, elections, etc.) so that any failure on his part can be attributed to the powerful corrupting the system. His constant whining about the debates doesn't mean he'll pull out any more than whining about the election means he'll pull out of that.Moreover, he's down in the polls (What polls? What's the question??). He therefore needs the debates to pull himself back up. And it'll likely work -- because social-engineering.Here's how the social engineering works, and how Trump will win the debates.The moderators, the ones running the debate, will do their best to ask Trump the toughest questions they think of. At this point, I think their first question will be about the Kahn family, and Trump's crappy treatment of their hero son. This is one of Trump's biggest weaknesses, but especially so among military-obsessed Republicans.And Trump's response to this will be awesome. I don't know what it will be, but I do know that he's employing some of the world's top speech writers and debate specialists to work on the answer. He'll be practicing this question diligently working on a scripted answer, from many ways it can be asked, from now until the election. And then, when that question comes up, it'll look like he's just responding off-the-cuff, without any special thought, and it'll impress the heck out of all the viewers that don't already hate him.The same will apply too all Trump's weak points. You think the debates are an opportunity for the press to lock him down, to make him reveal his weak points once and for all in front of a national audience, but the reverse is true. What the audience will instead see is somebody given tough, nearly impossible questions, and who nonetheless has a competent answer to everything. This will impress everyone with how "presidential" Trump has become.Also, waivering voters will see that the Trump gets much tougher questions than Hillary. This will feed into Trump's claim the media is biased against him. Of course, the reality is that Trump is a walking disaster area with so many more weaknesses to hit, but there's some truth to the fact that media has a strong left-wing bias. Regardless of Trump's performance, the media will be on trial during the debate, and they'll lose.The danger to Trump is that he goes off script, that his advisors haven't beaten it into his head hard enough that he's social engineering and not talking. That's been his greatest flaw so far. But, and this is a big "but", it's also been his biggest strength. By owning his gaffes, he's seen as a more authentic man of the people and not a slick politician. I point this out because we are all still working according to the rules of past elections, and Trump appears to have rewritten the rules for this election.Anyway, this post is about social-engineering, not politics. You should watch the debate, not for content, but for how well each candidates does social engineering. Watch how they field every question, then "bridge" to a prepared statement they've been practicing for months. Watch how the moderators try to take them "off message", and how the candidates put things back "on message". Watch how Clinton, while be | ||||
| 2016-08-20 17:50:17 | Bugs don\'t come from the Zero-Day Faerie (lien direct) | This WIRED "article" (aka. thinly veiled yellow journalism) demonstrates the essential thing wrong with the 0day debate. Those arguing for NSA disclosure of 0days believe the Zero-Day Faerie brings them, that sometimes when the NSA wakes up in the morning, it finds a new 0day under its pillow.The article starts with the sentences:WHEN THE NSA discovers a new method of hacking into a piece of software or hardware, it faces a dilemma. Report the security flaw it exploits to the product's manufacturer so it gets fixed, or keep that vulnerability secret-what's known in the security industry as a “zero dayâ€-and use it to hack its targets, gathering valuable intelligence.But the NSA doesn't accidentally "discover" 0days -- it hunts for them, for the purpose of hacking. The NSA first decides it needs a Cisco 0day to hack terrorists, then spends hundreds of thousands of dollars either researching or buying the 0day. The WIRED article imagines that at this point, late in the decision cycle, that suddenly this dilemma emerges. It doesn't.The "dilemma" starts earlier in the decision chain. Is it worth it for the government to spend $100,000 to find and disclose a Cisco 0day? Or is it worth $100,000 for the government to find a Cisco 0day and use it to hack terrorists.The answers are obviously "no" and "yes". There is little value of the national interest in spending $100,000 to find a Cisco 0day. There are so many more undiscovered vulnerabilities that this will make little dent in the total number of bugs. Sure, in the long run, "vuln disclosure" makes computers more secure, but a large government investment in vuln disclosure (and bug bounties) will only be a small increase on the total vuln disclosure that happens without government involvement.Conversely, if it allows the NSA to hack into a terrorist network, a $100,000 is cheap, and an obvious benefit.My point is this. There are legitimate policy questions about government hacking and use of 0days. At the bare minimum, there should be more transparency. But the premises of activists like Andy Greenburg are insane. NSA 0days aren't accidentally "discovered", they don't come a magic Zero-Day Faerie. The NSA instead hunts for them, after they've come up with a clearly articulated need that exceeds mere disclosure. Credit: @dinodaizovi, among others, has recently tweeted that "discover" is a flawed term that derails the 0day debate, as those like Greenberg assume it means as he describes it in his opening paragraph, that the NSA comes across them accidentally. Dino suggested the word "hunt" instead. |
★★ | |||
| 2016-08-18 17:11:10 | EQGRP tools are post-exploitation (lien direct) | A recent leak exposed hackings tools from the "Equation Group", a group likely related to the NSA TAO (the NSA/DoD hacking group). I thought I'd write up some comments.Despite the existence of 0days, these tools seem to be overwhelmingly post-exploitation. They aren't the sorts of tools you use to break into a network -- but the sorts of tools you use afterwards.The focus of the tools appear to be about hacking into network equipment, installing implants, achievement permanence, and using the equipment to sniff network traffic.Different pentesters have different ways of doing things once they've gotten inside a network, and this is reflected in their toolkits. Some focus on Windows and getting domain admin control, and have tools like mimikatz. Other's focus on webapps, and how to install hostile PHP scripts. In this case, these tools reflect a methodology that goes after network equipment.It's a good strategy. Finding equipment is easy, and undetectable, just do a traceroute. As long as network equipment isn't causing problems, sysadmins ignore it, so your implants are unlikely to be detected. Internal network equipment is rarely patched, so old exploits are still likely to work. Some tools appear to target bugs in equipment that are likely older than Equation Group itself.In particular, because network equipment is at the network center instead of the edges, you can reach out and sniff packets through the equipment. Half the time it's a feature of the network equipment, so no special implant is needed. Conversely, when on the edge of the network, switches often prevent you from sniffing packets, and even if you exploit the switch (e.g. ARP flood), all you get are nearby machines. Getting critical machines from across the network requires remotely hacking network devices.So you see a group of pentest-type people (TAO hackers) with a consistent methodology, and toolmakers who develop and refine tools for them. Tool development is a rare thing amount pentesters -- they use tools, they don't develop them. Having programmers on staff dramatically changes the nature of pentesting.Consider the program xml2pcap. I don't know what it does, but it looks like similar tools I've written in my own pentests. Various network devices will allow you to sniff packets, but produce output in custom formats. Therefore, you need to write a quick-and-dirty tool that converts from that weird format back into the standard pcap format for use with tools like Wireshark. More than once I've had to convert HTML/XML output to pcap. Setting port filters for 21 (FTP) and Telnet (23) produces low-bandwidth traffic with high return (admin passwords) within networks -- all you need is a script that can convert the packets into standard format to exploit this.Also consider the tftpd tool in the dump. Many network devices support that protocol for updating firmware and configuration. That's pretty much all it's used for. This points to a defensive security strategy for your organization: log all TFTP traffic.Same applies to SNMP. By the way, SNMP vulnerabilities in network equipment is still low hanging fruit. SNMP stores thousands of configuration parameters and statistics in a big tree, meaning that it has an enormous attack surface. Anything value that's a settable, variable-length value (OCTECT STRING, OBJECT IDENTIFIER) is something you can play with for buffer-overflows and format string bugs. The Cisco 0day in the toolkit was one example.Some have pointed out that the code in the tools is crappy, and they make obvious crypto errors (such as using the same initialization vectors). This is nonsense. It's largely pentesters, not software developers, creating these tools. And they have limited threat models -- encryption is to avoid easy detection that they are exfiltrating data, not to prevent somebody from looking at the data. | ★★★ | |||
| 2016-08-17 14:18:01 | Hey lawyers, I\'m not your client (lien direct) | We can't talk casually with lawyers, at parties or infosec conferences. For one thing, it's an ethical problem for them, as they put a couple minute's thought into a question that can have lifelong consequences for a you. For another thing, it puts them legal jeopardy if you (falsely) think there is an attorney-client relationship. This makes lawyers boring people at parties, because all they can discuss is nonsense like sports scores.In an attempt to remedy this situation, so we can talk casually about the law, I'm writing the following open-letter:Dear Lawyers:Unless there is a written agreement signed by you and me, I'm not your client. I understand that I should not interpret any comment as actual legal advice. I know that we are talking about hypothetical situations, and that I should not try to apply that information to my own situation. I know that we are often making jokes, and taking such things seriously as "legal advice" would be against my interests. I'm the one at fault, deliberately instigating you into discussing hypotheticals and making such jokes, for the lulz.Sincerely,Robert GrahamOf course, I don't know if this letter will actually help lawyers chillax and talk more openly about the law. For that, I guess I'd need legal advice. | ★★ | |||
| 2016-08-15 17:36:52 | National interest is exploitation, not disclosure (lien direct) | Most of us agree that more accountability/transparency is needed in how the government/NSA/FBI exploits 0days. However, the EFF's positions on the topic are often absurd, which prevent our voices from being heard.One of the EFF's long time planks is that the government should be disclosing/fixing 0days rather than exploiting them (through the NSA or FBI). As they phrase it in a recent blog post:as described by White House Cybersecurity Coordinator, Michael Daniel: “[I]n the majority of cases, responsibly disclosing a newly discovered vulnerability is clearly in the national interest.†Other knowledgeable insiders-from former National Security Council Cybersecurity Directors Ari Schwartz and Rob Knake to President Obama's hand-picked Review Group on Intelligence and Communications Technologies-have also endorsed clear, public rules favoring disclosure.The EFF isn't even paying attention to what the government said. The majority of vulnerabilities are useless to the NSA/FBI. Even powerful bugs like Heartbleed or Shellshock are useless, because they can't easily be weaponized. They can't easily be put into a point-and-shoot tool and given to cyberwarriors.Thus, it's a tautology saying "majority of cases vulns should be disclosed". It has no bearing on the minority of bugs the NSA is interested in -- the cases where we want more transparency and accountability.These minority of bugs are not discovered accidentally. Accidental bugs have value to the NSA, so the NSA spends considerable amount of money hunting down different bugs that would be of use, and in many cases, buying useful vulns from 0day sellers. The EFF pretends the political issue is about 0days the NSA happens to come across accidentally -- the real political issue is about the ones the NSA spent a lot of money on.For these bugs, the minority of bugs the NSA sees, we need to ask whether it's in the national interest to exploit them, or to disclose/fix them. And the answer to this question is clearly in favor of exploitation, not fixing. It's basic math.An end-to-end Apple iOS 0day (with sandbox escape and persistance) is worth around $1 million, according to recent bounties from Zerodium and Exodus Intel.There are two competing national interests with such a bug. The first is whether such a bug should be purchased and used against terrorist iPhones in order to disrupt ISIS. The second is whether such a bug should be purchased and disclosed/fixed, to protect American citizens using iPhones.Well, for one thing, the threat is asymmetric. As Snowden showed, the NSA has widespread control over network infrastructure, and can therefore insert exploits as part of a man-in-the-middle attack. That makes any browser-bugs, such as the iOS bug above, much more valuable to the NSA. No other intelligence organization, no hacker group, has that level of control over networks, especially within the United States. Non-NSA actors have to instead rely upon the much less reliable "watering hole" and "phishing" methods to hack targets. Thus, this makes the bug of extreme value for exploitation by the NSA, but of little value in fixing to protect Americans.The NSA buys one bug per version of iOS. It only needs one to hack into terrorist phones. But there are many more bugs. If it were in the national internet to buy iOS 0days, buying just one will have little impact, since many more bugs still lurk waiting to be found. The government would have to buy many bugs to make a significant dent in the risk.And why is the government helping Apple at the expense of competitors anyway? Why is it securing iOS with its bug-bounty program and not Android? And not Windows? And not Adobe PDF? And not the million other products people use?The point is that no sane person can arg | ||||
| 2016-08-08 13:43:01 | I gamergate Meredith Mciver (lien direct) | One of the basic skills of hackers is "doxxing". It's actually not a skill. All you need to do is a quick search of public records databases through sites like Spokeo, Intelius, and Ancestry.com and you can quickly dox anybody.During the Republican convention, Trump's wife plagiarized Obama's wife in a speech. A person in the Trump organization named "Meredith Mciver" took the blame for it. Trump haters immediately leapt to the conclusion that this person was fake, pointing out her Twitter and Facebook accounts were created after the controversy started.So I'm going to go all gamergate on her and see what I can find.According to New York public records, somebody named "Meredith Mciver" has been working for a company called the "The Trump Organization" as "Staff Writer" for many years. Her parents are Phyllis and James Mciver. Her older sister is Karen Mciver. She has an apartment at 588 W End Avenue in Manhattan (though I won't tell you which apartment -- find out for yourself). Through Ancestry.com, you can track down more information, such as her yearbook photo from 1962.Now, all these public records could be fake, of course, but that would require a conspiracy larger than the one hiding the truth about Obama's birth certificate.I point this out because we have enough reasons to hate Trump (his populist demagoguery, his bankrupt character, his racism) and don't need to search for more reasons. Yet, conspiracy theorists, "mciverers", want to exploit this non-issue as much as they can. |
★★★ | |||
| 2016-07-22 22:24:07 | My Raspeberry Pi cluster (lien direct) | So I accidentally ordered too many Raspberry Pi's. Therefore, I built a small cluster out of them. I thought I'd write up a parts list for others wanting to build a cluster.To start with is some pics of the cluster What you see is a stack of 7 RPis. At the bottom of the stack is a USB multiport charger and also an Ethernet hub. You see USB cables coming out of the charger to power the RPis, and out the other side you see Ethernet cables connecting the RPis to a network. I've including the mouse and keyboard in the picture to give you a sense of perspective. Here is the same stack turn around, seeing it from the other side. Out the bottom left you see three external cables, one Ethernet to my main network and power cables for the USB charger and Ethernet hub. You can see that the USB hub is nicely tied down to the frame, but that the Ethernet hub is just sort jammed in there somehow. Here is the same stack turn around, seeing it from the other side. Out the bottom left you see three external cables, one Ethernet to my main network and power cables for the USB charger and Ethernet hub. You can see that the USB hub is nicely tied down to the frame, but that the Ethernet hub is just sort jammed in there somehow. |
Guideline | ★★ | ||
| 2016-06-23 04:41:55 | Use the freakin\' debugger (lien direct) | This post is by a guy who does "not use a debugger". That's stupid. Using a friendly source-level debugger (Visual Studio, XCode, Eclipse) to step line-by-line through working code is what separates the 10x programmers from the wannabes. Yes, it's a bit of a learning hurdle, and creating "project" files for small projects is a bit of a burden, but do it. It'll vastly improve your coding skill.That post quotes people like Rob Pike saying that stepping line-by-line is a crutch, that instead you should be able to reason about code. And that's true, if you understand what you are doing completely.But in the real world, you never do. Programmers are constantly forced to stretch and use unfamiliar languages. Worse yet, they are forced to use unfamiliar libraries. Documentation sucks, there's no possible way to understand APIs than to step through code -- either watching the returned values, or compiling their source and stepping into it.As an experienced programmer, it's true I often don't step through every line. The lines I understand completely, the ones I can fully reason about, I don't bother. But the programmer spends only a small percentage of their time on things they understand -- most of the time spent coding is noodling on the things they don't understand, and that's where the debugger comes in.And this doesn't even take into account that in the real world, where programmers spend a lot of time working on other people's code. Sometimes the only way to figure it out is to set a breakpoint and run the unit test until it reaches that point.Programmers fetishize editors. Real programmers, those who produce a lot of code, fetishize debuggers, both the one built into the IDE for debugging working code, and also the specialized tools for diagnosing problems in buggy code.Seriously, if you are learning to program, learn to use the debugger in the integrated IDE. Step line-by-line through every line of code, until you grok it.. Microsoft's Visual Code is a good system for debugging JavaScript (which is a good starting language to learn). You'll thank me later when you are pulling down seven figures as a 10x programmer.I take the contrary position -- aggressive use of a debugger gives you insight you won't get by mere inspection. https://t.co/U81C80tR88- John Carmack (@ID_AA_Carmack) June 22, 2016 | ★★ | |||
| 2016-06-22 00:27:52 | Reverse Turing testing tech support (lien direct) | So I have to get a new Windows license for a new PC. Should I get Windows 10 Home or Windows 10 Professional? What's the difference?So I google the question, which gives me this website: Ooh, a button that says "Download Table". That's exactly what I want -- a technical list without all the fluff. I scroll down to the parts that concern me, like encryption. Ooh, a button that says "Download Table". That's exactly what I want -- a technical list without all the fluff. I scroll down to the parts that concern me, like encryption. Wait, what? What's the difference between "Device Encryption" and "BitLocker"? I though BitLocker was Device Encryption?? Well, the purchase screen for Windows 10 has this friendly little pop out offering to help. Of course, as a techy, I know that such things are worse than useless, but I haven't tried one in a while, so I thought if I'd see if anything changed.So up pops a chat window and we start chatting: Wait, what? What's the difference between "Device Encryption" and "BitLocker"? I though BitLocker was Device Encryption?? Well, the purchase screen for Windows 10 has this friendly little pop out offering to help. Of course, as a techy, I know that such things are worse than useless, but I haven't tried one in a while, so I thought if I'd see if anything changed.So up pops a chat window and we start chatting: So at first he says they are the same. When I press him on the difference, he then admits they are different. He can't read the document I'm reading, because it's on a non-Microsoft "third party" site. While it's true it's on "windows.net", that's still a Microsoft site, but apparently he's not allowed to access it. I appears Microsoft firewalls their access to the Internet so jerks like me can't social engineer them.So he goes on to find other differences: So at first he says they are the same. When I press him on the difference, he then admits they are different. He can't read the document I'm reading, because it's on a non-Microsoft "third party" site. While it's true it's on "windows.net", that's still a Microsoft site, but apparently he's not allowed to access it. I appears Microsoft firewalls their access to the Internet so jerks like me can't social engineer them.So he goes on to find other differences: At this point, he's acting as a Markov bot, searching Microsoft's internal site with the terms I give him, then selecting random phrases to spew back at me, with no understanding. Support for TPM has nothing to do with the difference.Finally, he admits he can't answer the question, and offers to send me to more technical people: At this point, he's acting as a Markov bot, searching Microsoft's internal site with the terms I give him, then selecting random phrases to spew back at me, with no understanding. Support for TPM has nothing to do with the difference.Finally, he admits he can't answer the question, and offers to send me to more technical people: |
★★★★★ | |||
| 2016-06-18 23:17:27 | Tesla review: What you need to know about charging (lien direct) | Before you buy an electric car, you need to understand charging. It's a huge deal. You think it works almost like filling the gas tank. It doesn't. Before going on long trips, you first need to do math and a bit of planning.The MathLike BMW model numbers indicate engine size, Tesla model numbers indicate the size of the battery, so my "Tesla S P90D" has a 90kwh (killowatt-hour) battery, with a 286mile range. Their lowest end model is the “Tesla S 60â€, which has a 60kwh hour battery, or a 208mile advertised range.In the United States, a typical plug is a 120volt circuit with a maximum of 15amps. Doing the math, this is how long it'll take for me to recharge the battery: That's right, 1.4 days (or 2.1 days for a 90kwh car). This is the absolute worse case scenario, mind you, but it demonstrates that you have to pay attention to charging. You can't simply drive up to a station, fill up the tank in a couple minutes, and drive away.Let's say you live in Austin, Texas, and you have a meeting in Dallas. You think that you can drive up to Dallas in your new Tesla S 60, let the car charge while you are in the meeting, and then drive home. Or, maybe you have dinner there, letting the car charge longer. Or maybe you even stay overnight.Nope, even 24 hours later, you still might not have enough charge left to get home. At 195 miles, it's at the range of the 60kwh battery, which would take more than a day to recharge using a normal electric circuit. That's right, 1.4 days (or 2.1 days for a 90kwh car). This is the absolute worse case scenario, mind you, but it demonstrates that you have to pay attention to charging. You can't simply drive up to a station, fill up the tank in a couple minutes, and drive away.Let's say you live in Austin, Texas, and you have a meeting in Dallas. You think that you can drive up to Dallas in your new Tesla S 60, let the car charge while you are in the meeting, and then drive home. Or, maybe you have dinner there, letting the car charge longer. Or maybe you even stay overnight.Nope, even 24 hours later, you still might not have enough charge left to get home. At 195 miles, it's at the range of the 60kwh battery, which would take more than a day to recharge using a normal electric circuit. Faster ChargingThat was a worst case scenario. Luckily, you probably won't be charging using a normal 120volt/15amp circuit. That's just the emergency backup if all else fails.In your home, for high-watt devices like ovens, air conditioners, and clothes dryers, you have higher wattage circuits. The typical max in your home will be a 240volt/50amp circuit. It has a different power connector than a normal circuit, thicker wires, and so forth. Doing the math on this sucker, you get: Faster ChargingThat was a worst case scenario. Luckily, you probably won't be charging using a normal 120volt/15amp circuit. That's just the emergency backup if all else fails.In your home, for high-watt devices like ovens, air conditioners, and clothes dryers, you have higher wattage circuits. The typical max in your home will be a 240volt/50amp circuit. It has a different power connector than a normal circuit, thicker wires, and so forth. Doing the math on this sucker, you get: For our 190 mile drive, then, you can except to drive to Dallas, charge during the meeting and dinner for 5 hours, then you'll have enough juice to get back home.When you buy a Tesla, the first thing you'll do is hire and electrician, and for $1000 to $5000, pay them to install this high-end circuit in your garage or car port. Since you garage is usually where the circuit breaker is located anyway, it's usually the low-end of this range. You have to choose either the NEMA 14-50 plug, which can be used to power any electric car, or the Tesla HPWC (“High Power Wall Chargerâ€) that just bundles the cord and everything together, making it easier t For our 190 mile drive, then, you can except to drive to Dallas, charge during the meeting and dinner for 5 hours, then you'll have enough juice to get back home.When you buy a Tesla, the first thing you'll do is hire and electrician, and for $1000 to $5000, pay them to install this high-end circuit in your garage or car port. Since you garage is usually where the circuit breaker is located anyway, it's usually the low-end of this range. You have to choose either the NEMA 14-50 plug, which can be used to power any electric car, or the Tesla HPWC (“High Power Wall Chargerâ€) that just bundles the cord and everything together, making it easier t |
Tesla | ★★★★★ | ||
| 2016-06-18 16:37:56 | Ethereum/TheDAO hack simplified (lien direct) | The news in the Bitcoin world is the Ethereum/DAO hack. I thought I'd write up a simplified explanation.What is Bitcoin?I'm sure you know, or have an idea what Bitcoin is, but I'll explain it again in terms that are important here.Bitcoin is just a public ledger (the "blockchain"), of all transaction there ever was. This ledger is huge (80-gigabytes) and growing, but Moore's Law says computers grow even faster, so that shouldn't be a problem.Each entry in the ledger says to move the coins received in these previous entries, and give them to this recipient. In other words:move these coins I received there, to this guy hereIn the future when that guy spends the coin in a new transaction, he'll refer back to this transaction here. That's why it's called a "chain" -- every transaction refers to a previous one, back to the original creation of the coins.Actually, these transactions aren't fixed as simply moving money around. Instead, a script is used, written in a bitcoin-specific programming language that can do things like add, multiply, and compare numbers. However, it's not a full programming language. It can't call functions or execute loops. It's complex enough to do allow some creativity, such as allowing transactions to be escrowed by a third party, but it can't do much more than that.What are alt-coins?After Bitcoin took off, other people started to create their own variations.Most of these variations have offered no meaningful improvement over Bitcoin. They instead are just popular among speculators who pump and dump, hoping to buy in at a low price and sell to some fool at a higher price.There are only two alt-coins that have actually made an improvement: ZeroCoin and Ethereum. ZeroCoin works by making transactions anonymous. Ethereum is the alt-coin that is being discussed here.What is Ethereum?Ethereum is a variation of Bitcoin that uses a full programming language instead of a simple scripting language. The reason for this is that Ethereum supports smart contracts.Let's say that we want to organize a small conference. We need 100 people to sign up and pay/deposit money, so we can rent a hotel and such. But if not enough people sign up by a certain date, then the deposits need to be refunded. With Ethereum, we can write in a JavaScript-like language to code up this contract. It'll guarantee that everyone will get a ticket to the conference, or everyone will get their money refunded, depending on how many sign up.That's a simple example. The possibilities are endless, which has got a lot of people really excited. Which, of course, makes the believers insufferable among non-believers in the system.What is The DAO?DAO stands for decentralized autonomous organization. It's notionally like the example above for getting funds for a small conference, except that it includes much more. Members buy shares in the DAO, and according to the number of shares they have, can vote on things. The dreamers have the idea they'll replace Democracy and run entire countries this way.There are many types of DAOs on the Ethereum blockchain, but one in particular is TheDAO, which is some sort of DAO-based mutual-fund/investment-fund. You buy in, vote on which investments the fund should make, then reap the returns. It looks like a big organization, but it actually just runs as bits of code and data within the Etherium blockchain.This investment scheme has gobbled up 10% of Ethereum coins, or $100 million worth out of Ethereum's $1 billion ecosystem.When you want to leave the fund, you sp | ★★★★★ | |||
| 2016-06-14 15:51:14 | Scanning for ClamAV 0day (lien direct) | Last week an 0day was released for ClamAV. Well, not really an 0day so much as somebody noticed idiotic features in ClamAV. So I scanned the Internet for the problem.The feature is that the daemon listens for commands that tell it to do things like scan files. Normally, it listens only locally for such commands, but can be reconfigured to listen remotely on TCP port 3310. Some packages that include ClamAV sometimes default to this.It's a simple protocol that consists of sending a command in clear text, like "PING", "VERSION", "SHUTDOWN", or "SCAN So I ran masscan with the following command:masscan 0.0.0.0/0 -p3310 --banners --hello-string[3310] VkVSU0lPTg==Normally when you scan an address range (/0) and port (3310), you'd just see which ports are open/closed. That's not useful in this case, because it finds 2.7 million machines. Instead, you want to establish a full TCP connection. That's what the --banners option does, giving us only 38 thousand machines that successfully establish a connection. The remaining machines are large ranges on the Internet where firewalls are configured to respond with SYN-ACK, with the express purpose of frustrating port scanners.But of those 38k machines, most are actually things like web servers running on odd ports. 51 machines running VNC, 641 machines running SSH, and so on.To find specifically ClamAV, I send a command using the --hello-string feature. I send the text "VERSION", which must be encoded with base64 on the command-line for masscan (in case you need to also send binary).This finds 5950 machines (i.e. 6k) that respond back with a ClamAV signature. typical examples of this response are: At first I thought the date was when they last updated the software, maybe as a page. Roughly half had dates of either this morning or the day before. But no, it's actually the dates when they last updated their signatures.From this we can conclude that roughly half of ClamAV installations are configured to auto-update their signatures.Roughly 2400 machines (nearly half) had the version 0.97.5. This was released in June 2012 (four years old). I'm thinking some appliance maker like Barracuda bundled the software -- appliances are notorious for not getting updated software. That hints at why this non-default configuration is so common -- it's not users who made this decision, but the software that bundles ClamAV with other things. Scanning other ports gives me no clues -- they appear all over the map, with different versions of SSH, different services running, different SSL versions, and so on. I thought maybe "mail server" (since that'd be a common task for ClamAV), but there were only a few servers, and they ran different mail server software. So it's a mystery why this specific version is so popular.I manually tested various machines with "SCAN foo". They all replied "file not found", which hints that all the units I found are vulnerable to this 0day.As for other things, I came across a bunch of systems claiming to be ChinaDDoS systems: At first I thought the date was when they last updated the software, maybe as a page. Roughly half had dates of either this morning or the day before. But no, it's actually the dates when they last updated their signatures.From this we can conclude that roughly half of ClamAV installations are configured to auto-update their signatures.Roughly 2400 machines (nearly half) had the version 0.97.5. This was released in June 2012 (four years old). I'm thinking some appliance maker like Barracuda bundled the software -- appliances are notorious for not getting updated software. That hints at why this non-default configuration is so common -- it's not users who made this decision, but the software that bundles ClamAV with other things. Scanning other ports gives me no clues -- they appear all over the map, with different versions of SSH, different services running, different SSL versions, and so on. I thought maybe "mail server" (since that'd be a common task for ClamAV), but there were only a few servers, and they ran different mail server software. So it's a mystery why this specific version is so popular.I manually tested various machines with "SCAN foo". They all replied "file not found", which hints that all the units I found are vulnerable to this 0day.As for other things, I came across a bunch of systems claiming to be ChinaDDoS systems: |
★★★ | |||
| 2016-06-08 00:13:36 | No, Musky, Feudalism is best for Mars (lien direct) | Recently, the press fawned all over Elon Musk's comments at a conference. Among them was Musk's claim that "direct democracy" would be the best system, where citizen's vote directly for laws, rather than voting for (corrupt) representatives/congressmen. This is nonsense. The best political system would be feudalism.There is no such thing as "direct democracy". Our representatives in congress are only the first layer on top of a bureaucracy. Most rules that restrict us are not "laws" voted by congress but "regulations" decided by some bureaucrat.Consider the BP Gulf Oil spill, as an example. It happened because oil companies got cozy with their regulators, the minerals Management Service (MMS), part of the Department of the Interior. The bureaucrats had a dual mandate: to protect the environment, and to promote economic activity. Oil companies lobbied them to risk the environment in favor of profits.Consider Obamcare's controversial mandate that health insurers must pay for abortions. This was not part of the law pass by congress, but a decision by the bureaucrats in charge of all the little details in carrying out the law.Consider the Federal Communication Commission (FCC) regulation of the Internet. It bases its power to regulate the Internet on laws that essentially predate the Internet as we know it.No matter how ideal this "direct Democracy" of Musk's, you are still going to leave most decision making in the hands of a bureaucracy. This is especially true on space flight to Mars. If something's wrong with the air system, you want a technician making quick decisions to fix it. Otherwise, people would suffocate long before they had a chance to vote on the issue. Technicians must be trusted with important decisions, like jettisoning that one pod killing 10 people in order to save the remaining 100.No matter the political system, you are going to have the bureaucracy making tactical, day-to-day decisions. You are also going to have an upper tier, making long term strategic decisions. It's how all political systems work, from monarchies to "direct democracy". They largely just change the names of the bureaucrats, rather than being substantively different.The corruption in Democracies doesn't necessarily come from those in power, but from the voters themselves. Voters are idiots and vote like idiots. That's why you have candidates like those of the U.S's current election season -- populist demagogues preying on people's ignorance proposing solutions that educated people believe to be unworkable. The majority of voters have never taken an economics class, do not understand foreign policy, or have any other qualification to make the decisions they make.Instead of education, voters overwhelming decide what's best for themselves, not dispassionately what's best for society as a whole. College students vote for free college. Old people vote for social security and health care. Mothers vote for child leave and child care. Racists vote to keep unwanted types out of their community. And so on. That's corruption at it's core.As de Tocqueville is famous for noting, democracy only lasts up to the point that 51% of the population realizes they can vote to just take everything away from the other 49%. You call it corruption, but our current system allows a member of the 49% to lobby congress so that they don't get screwed by the 51%. Indeed, that's what most lobbyists do -- they aren't asking for special favors from the government so much as trying to alleviate special punishments. It's a sort of corruption defending themselves from the voter's corruption.As the famous quote goes, "Democracy is the worst form of government -- except for all the others". It's a horrible system, it's just we h | Uber | |||
| 2016-06-06 08:39:09 | Instrumenting masscan for AFL network fuzzing (lien direct) | This blog post is about work in progress. You probably don't want to read it. So I saw this tweet today:Fuzzing masscan by @ErrataRob with AFL by @lcamtuf. Forgot to remove the crash-handler so crashes logged as hangs. pic.twitter.com/Yh5ElNyvOm- Dr David D. Davidson (@dailydavedavids) June 5, 2016As it turns it, he's just fuzzing input files. This is good, he's apparently already found some bugs, but it's not a huge threat.Instead, what really needs to be fuzzed is network input. This is chronic problem with AFL, which is designed for inserting files, not network traffic, into programs.But making this work is actually pretty trivial. I just need to make a tiny change to masscan so that instead of opening a libpcap adapter, it instead opens a libpcap formatted file.This change was trivial, successfully running it is tough. You have to configure the command-line so all IP addresses match up with the libpcap file content, which is a pain. I created a sample lipcap file and checked it into the project, along with a help document explaining it. Just git clone the project, run make, then run this command line to see it run for yourself:bin/masscan --nobacktrace --adapter file:data/afl-http.pcap --source-ip 10.20.30.200 --source-port 6000 --source-mac 00-11-22-33-44-55 --router-mac c0-c1-c0-a0-9b-9d --seed 0 --banners -p80 74.125.196.147 --nostatusIf you run on the command-line, it appears to return immediately. I say "appears" because there's actually a 10 millisecond wait. That limits fuzzing speed to a 100 attempts per second, rather than thousands per second. That's a tougher change, so I'll have to get around to fixing that, but in the meanwhile, you can just run a bunch of AFLs in parallel to get around this.But when I try to run AFL, it's not working at the moment. In instead get this error: 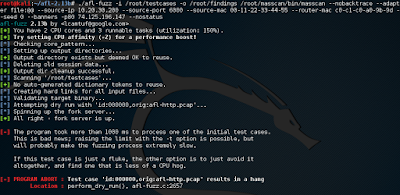 As you can see, the command that returns in 10ms is now hanging when run under AFL, which says that it doesn't return in 1000ms. Using the '-t' option to increase the timeout doesn't help. Running masscan in some other way, such as parsing configuration files, works just fine. As you can see, the command that returns in 10ms is now hanging when run under AFL, which says that it doesn't return in 1000ms. Using the '-t' option to increase the timeout doesn't help. Running masscan in some other way, such as parsing configuration files, works just fine.UpdateSo I changed to where I "join" threads cleanly, so that the entire thing can run cleanly without every having to stop and wait. However, this creates a second problem not AFL refused to run because it's crashing instead of hanging. AFL suggests that it might be an out-of-memory i |
||||
| 2016-06-02 20:32:52 | My fellow Republicans: don\'t support Trump (lien direct) | Scott Adams, the creator of the Dilbert comic strip, has a post claiming a Trump presidency wouldn't be as bad as people fear. It's a good post. But it's wrong.Trump is certainly not as bad as his haters claim. Trump not only disables the critical-thinking ability of his supporters, but also of his enemies. In most conversations, I end up defending Trump -- not because I support him as a candidate, but because I support critical-thinking. He's only racist sometimes, most of the time I love his political incorrectness.But with all that said, he would indeed be a horrible president. As a long-term Republican, I'd prefer a Hillary Clinton presidency, and I hate Hillary to the depths of my soul. She's corrupt, and worst of all, she's a leftist.But there's a thing worse than being a leftist (or right-winger) and that's being a "populist demagogue". Populist demagogues tell you that all your problems are caused by them (you know, those people), and present unrealistic solutions to problems. They appeal to base emotion and ignorance.When nations fail because of politics, it's almost always due to populist demagogues. Virtually all dictators are a "man of the people", protecting the people's interests against the powerful (somehow, the dictators themselves are never part of the "powerful", since by definition, they are "of the people"). We see that in Venezuela right now, whose economy has crashed with oil prices (50% of their GDP was oil exports). The leader is making everything worse by running the playbook of bad populist policies. For example he's printing money, which first year economics textbooks tell you causes inflation, then blaming the resulting inflation on the United States and the CIA manipulating prices. That's the essence of populism: they pursue horrible policies, but blame the consequences on them.In a Trump presidency, bad results that educated people know is caused by the government policy will instead be blamed on Mexico, China, and so on. The worst things get, the more crowd will cheer on Trump's and congress's bad policies, the more they punish Mexico and China, and the more they make bad policies worse.Consider the $15 minimum wage promoted by Bernie Sanders, a hateful populist demagogue who is, if anything, worse than Trump. Hillary wanted $12.Why not $18? Why not $25? Why not $100/hour minimum wage? Presumably, there are some negative thingies that happen the more you hike minimum wage. Presumably, there are some educated people out there who have studied this problem and can measure these things. And there are. An example is this non-partisan, Congressional Office of Management and Budget (OMB) analysis of raising minimum wage to $10.10. It describes numerous positive and negative effects, none of which fits in a demagogic sound bite.Raising the minimum wage has broad popular support, even among Republicans, because few are educated enough to appreciate the downsides. But yet, it doesn't get raised. The only explanation by populists like Bernie, or Trump, is that there must be some conspiracy (such as by Wall Street billionaires) that prevents the minimum wage from being raised. The truth is that our political leaders are basing their decision on things like the OMB report. They are basing their votes on an educated analysis of the policy, not on corruption and bribes from Wall Street. Note that there is no right or wrong answer to raising the minimum wage. There are reasonable people on both sides. It's just that this true debate based on education is far different than the public debate, which is based on emotion and ignorance.Trade, which both Bernie and Trump oppose, is the same way. Educated people are fo | Guideline | |||
| 2016-06-02 04:43:42 | Drumpf: this is not how German works (lien direct) | In our willingness to believe any evil of Trump, some have claimed his original name was "Drumpf". This isn't true, this isn't how the German language works. Trump has the power to short-circuit critical thinking in both his supporters and his enemies. The "Drumpf" meme is just one example.There was no official pronunciation or spelling of German words/names until after Trump's grandfather was born. As this The Guardian article describes, in the city ("Kallstadt") where Trump's grandfather was born, you'll see many different spellings of the family name in the church's records. like "Drumb, Tromb, Tromp, Trum, Trumpff, Dromb" and Trump. A person might spell their name different ways on different documents, and the names of children might be spelled different than their parent's. It makes German genealogy tough sometimes.During that time, different areas of German had different dialects that were as far apart as Dutch and German are today. Indeed, these dialects persist. Germans who grow up outside of cities often learn their own local dialect and standard German as two different languages. Everyone understands standard German, but many villagers cannot speak it. They often live their entire lives within a hundred kilometers of where they grew up because if they go too far away, people can no longer understand them.The various German dialects, sub-dialects, and accents often had consistent language shifts, where the same sound is pronounced differently across many words. For example, words that in English have a 'p' will in German have 'pf" instead, like the word penny becoming Pfennig, or pepper becoming Pfeffer.Kallstadt is located in the Pfalz region of Germany, or as they pronounce it in the local dialect, Palz. You see what I'm getting at, what is 'pf' in German is 'p' (like English) in the local dialect. Thus, you'd say "Trump" if you were speak Pfalz dialect, or "Trumpf" if you were speaking standard German.It's like the word for stocking, which in standard German is Strumpf. In documents written around that time in the Pfalz region, you'd find spellings like Strump, Strumpf, Strumpff, Strimp, and Stromp. Both the vowels and the last consonant would change (according to a Pfalz dictionary I found online).Friederich Trump was born in 1869, in a time when Germany was split into numerous smaller countries. The German Empire that unified Germany was created in 1871. The counsel to standardize the language and spellings was 1876. Friederich emigrated to America in 1885. In other words, his birth predates the era in which they would've standardized the spelling of names.From the records we have, "Trump" was on his baptism record, and "Trump" is how he spelled his name in America, but "Trumpf", with an 'f' was on his immigration form. That's perfectly reasonable. The immigration officer was probably a German speaker, who asked his name, and spelled it according to his version of German, with an 'f'.This idea of an official spelling/pronunciation of a name is a modern invention, with the invention of the modern "state" and "government officials". It didn't exist back when Friederich was born. His only birth record is actually his baptismal record at the local church.Thus, Trump's name is spelled "Trump". It was never officially spelled any other way in the past. It was never "changed". Sure, you'll see church documents and stuff with different spellings, but just how all words and names were handled back then. Insisting that he's "Drumpf" is ignorant -- it's not now the German language works. Update: Somebody named Gwenda Blair wrote book on Trump's family, which claims t |
||||
| 2016-05-31 19:27:00 | From scratch: why these mass scans are important (lien direct) | The way the Internet works is that "packets" are sent to an "address". It's the same principle how we send envelopes through the mail. Just put an address on it, hand it to the nearest "router", and the packet will get forwarded hop-to-hop through the Internet in the direction of the destination.What you see as the address at the top of your web browser, like "www.google.com" or "facebook.com" is not the actual address. Instead, the real address is a number. In much the same way a phonebook (or contact list) translates a person's name to their phone number, there is a similar system that translates Internet names to Internet addresses.There are only 4 billion Internet addresses. It's a number between between 0 and 4,294,967,296. In binary, it's 32-bits in size, which comes out to that roughly 4 billion combinations.For no good reason, early Internet pioneers split up that 32-bit number into four 8-bit numbers, which each has 256 combinations (256 × 256 × 256 × 256 = 4294967296). Thus, why write Internet address like "192.168.38.28" or "10.0.0.1". Yes, as you astutely point out, there are many more than 4 billion devices on the Internet (the number is closer to around 10 billion). What happens is that we can use address sharing (also called "network address translation"), so that many devices can share a single Internet adress. All the devices in your home (laptop, iPad, Nest thermistat, WiFi enabled Barbie, etc.) has a unique address that only works in the home. When the packets go through your home router to the Internet, they get changed so that they all come from the same Internet address.This sharing only works when the device is what's called a "client", which consumes stuff on the Internet (like watching video, reading webpages), but which doesn't provide anything to the Internet. Your iPad reaches out to the Internet, but in general nothing on the Internet is trying to reach your iPad. Sure, I can make a Facetime video call to your iPad, but that's because both of us are clients of Apple's corporate computers.The opposite of a client is a "server". These are the computers that provide things to the Internet. These are the things you are trying to reach. There are web server, email servers, chat servers, and so. When you hear about Apple or Facebook building a huge "data center" somewhere, it's just a big building full of servers.A single computer can provide many services. They are distinguished by a number between 0 and 65,535 (a 16-bit number). Different services tend to run on "well known" ports. The well known port for encrypted web servers is 443 (no, there's no good reason that number out of 65535 combinations was chosen, it's not otherwise meaningful). Non-encrypted web-servers are at port 80, by the way, but all servers by now should be encrypted.Web links like "https://www.google.com:443" must contain the port number. However, if you are using the default, then you can omit it, so "https://www.google.com" is just fine. However, any other port must be specified, such as "https://www.robertgraham.com:3774/some/secret.pdf". When you visit such links within your browser, it'll translate the name into an Internet address, then send packets to the combination address:port.Normally, when you look for things on the web, you use a search engine like Google to find things. Google works by "spidering" the Internet, reading pages, then following links to other pages. After I post this blog post, Google is going to add "https://www.robertgraham.com:3774/some/secret.pdf" to it's index and try to read that webpage. It doesn't | ★★★★★ | |||
| 2016-05-30 01:48:24 | Doing a \'full scan\' of the Internet right now (lien direct) | So I'm doing a "full" scan of the Internet, all TCP ports 0-65535 on all addresses. This explains the odd stuff you see from 209.126.230.7x.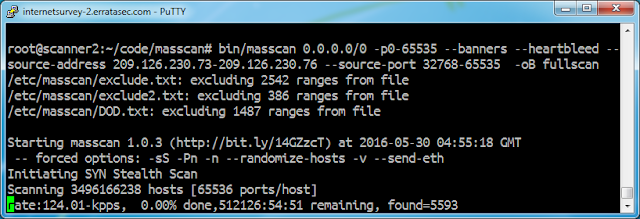 I'm scanning at only 125kpps from 4 source IP addresses, or roughly 30kpps from each source address. This is so that I'll get below many thresholds for IDSs, which trigger when they see fast scans from a single address. The issue isn't to avoid detection, but to avoid generating work for people who get unnecessarily paranoid about the noise they see in their IDS logs.This scan won't finish at this speed, of course, it won't get even close. Technically, it'd take 50 years to complete at this rate.The point isn't create a comprehensive scan, but to do sampling scan. I'll let it run a week like this, which will get 0.1% of the Internet, and then stop the scan.What am I looking for? I don't know. I'm just doing something weird in order to see what happens. With that said, I am testing any port I connect to with Heartbleed. This should give us an estimation of how many Internet-of-Things devices are still vulnerable to that bug. I'm also interested to see how many things allow connections to port 0.I'm also interested in see those devices/firewalls that respond with a SYN-ACK to any SYN. That's why, in the above picture, the "found" count is so high. I haven't actually found many real things, but it looks like it because these devices send SYN-ACKs without actually establishing TCP connections.Anyway, send me a tweet @erratarob with information on how you perceive this incoming scan. Is your firewall and IDS handling it well? or do you have messed up configuration/policies where this causes more noise/concern than is warranted? I'm scanning at only 125kpps from 4 source IP addresses, or roughly 30kpps from each source address. This is so that I'll get below many thresholds for IDSs, which trigger when they see fast scans from a single address. The issue isn't to avoid detection, but to avoid generating work for people who get unnecessarily paranoid about the noise they see in their IDS logs.This scan won't finish at this speed, of course, it won't get even close. Technically, it'd take 50 years to complete at this rate.The point isn't create a comprehensive scan, but to do sampling scan. I'll let it run a week like this, which will get 0.1% of the Internet, and then stop the scan.What am I looking for? I don't know. I'm just doing something weird in order to see what happens. With that said, I am testing any port I connect to with Heartbleed. This should give us an estimation of how many Internet-of-Things devices are still vulnerable to that bug. I'm also interested to see how many things allow connections to port 0.I'm also interested in see those devices/firewalls that respond with a SYN-ACK to any SYN. That's why, in the above picture, the "found" count is so high. I haven't actually found many real things, but it looks like it because these devices send SYN-ACKs without actually establishing TCP connections.Anyway, send me a tweet @erratarob with information on how you perceive this incoming scan. Is your firewall and IDS handling it well? or do you have messed up configuration/policies where this causes more noise/concern than is warranted?Update: This is the sort of thing I find doing this random scan, an OpenVPN accelerator that still hasn't been patched for Heartbleed: 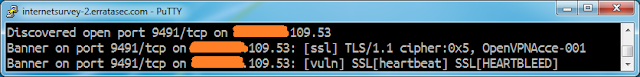 Again, the point isn't find these devices specficially, but to estimate how many of this sort of thing is out there. Again, the point isn't find these devices specficially, but to estimate how many of this sort of thing is out there.Update: At this early point, it looks like VNC is found much more often on random ports than it is on the official port of 5900. 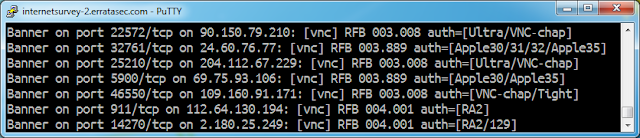 |
★★ | |||
| 2016-05-27 22:23:11 | Hiroshima is a complex memorial (lien direct) | In the news is Obama's visit to the Hiroshima atomic bomb memorial. The memorial is more complex than you think. It's not a simple condemnation of the bomb. Instead, it's a much more subtle presentation of the complexity of what happened.I mention this because of articles like this one at Foreign Policy magazine, in which the author starts by claiming he frequently re-visits Hiroshima. He claims that the memorial has a clear meaning, a message, that he takes back from the site. It doesn't.The museum puts the bombing into context. It shows how Japan had been in a constant state of war since the 1890s, with militaristic roots going back further in to Samurai culture. It showed how Japan would probably have continued their militaristic ways had the United States not demanded complete surrender, a near abdication of the emperor, and imposed a pacifist constitution on the country.In other words, Japan accepts partial responsibility for having been bombed.It doesn't shy away from the horror of the bomb. It makes it clear that such bombs should never again be used on humans. But even that has complexity. More people were killed in the Tokyo firebombing than Hiroshima and Nagasaki combined. Had Hiroshima not been nuked, it would've instead been flattened with conventional bombs, causing more devastation and killing nearly as many people. The Japanese were likely more afraid of the Russian invasion than American nukes when they surrendered unconditionally.When I left the memorial, I was left with the profound sense that I just didn't know the answers.The truth is that few have "real" opinions about the Hiroshima atomic blast. Their opinions just proxies for how they feel about American's military might today. The Foreign Policy article above, which claims to have gotten the "message" from the memorial, is a lie. Nobody gets clarity and focus on the issue coming from the memorial, just a new appreciation of the problem. https://traveljapan.co.nz/tours-view/hiroshima-miyajima-1-day-tour-3236 https://traveljapan.co.nz/tours-view/hiroshima-miyajima-1-day-tour-3236 |
★★★★ | |||
| 2016-05-27 20:19:53 | The EFF is Orwellian as fuck (lien direct) | As this blog has documented many times * * * *, the Electronic Frontier Foundation (EFF) is exactly the populist demagogues that Orwell targets in his books 1984 and Animal Farm. Today, the EFF performed yet another amusingly Orwellian stunt. Urging the FCC to regulate cyberspace, it cites the exact law that it had previously repudiated.Specifically, the EFF frequently champions the document Declaration of Independence of Cyberspace, written by one of its founders, John Perry Barlow. This document says:"Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather."Specifically, Barlow is talking about a then recent act of Congress:In the United States, you have today created a law, the Telecommunications Reform Act, which repudiates your own Constitution and insults the dreams of Jefferson, Washington, Mill, Madison, DeToqueville, and Brandeis. These dreams must now be born anew in us.That 1996 Act adds sections to the telcom laws, such as this portion:Title II is amended by inserting after section 221 (47 U.S.C. 221) the following new section: `SEC. 222. PRIVACY OF CUSTOMER INFORMATION.Today, though, the EFF cites this section as to why the FCC should regulation Internet privacy:The Commission has the Statutory Authority Under Both Section 222 and Section 705 to Protect Consumer Privacy.So which is it? Does the EFF repudiate the law, and want government to avoid regulating cyberspace? Or does the EFF use that law to encourage government to regulate cyberspace? Both have their pros and cons, but you really can have only one.Of course, EFF supporters claim both. It's fascinating watching their doublethink follow the precise lines described by Orwell. They have no problems believing both ideas simultaneously. This shows that the real danger of totalitarianism isn't the evil dictators who impose it from above, but the willing populace (like EFF supporters) who champion it from below.In any case, it's JPBarlow's document that was correct. The world is rapidly moving to SSL by default, defeating broadband provider's ability to invade their customer's privacy. That broadband providers are invading customer privacy is mostly just a strawman argument by the EFF, fearmongering in an attempt to pass unneeded regulation. | ★★★★ | |||
| 2016-05-06 16:44:43 | Freaking out over the DBIR (lien direct) | Many in the community are upset over the recent "Verizon DBIR" because it claims widespread exploitation of the "FREAK" vulnerability. They know this is impossible, because of the vulnerability details. But really, the problem lies in misconceptions about how "intrusion detection" (IDS) works. As a sort of expert in intrusion detection (by which, I mean the expert), I thought I'd describe what really went wrong.First let's talk FREAK. It's a man-in-the-middle attack. In other words, you can't attack a web server remotely by sending bad data at it. Instead, you have to break into a network somewhere and install a man-in-the-middle computer. This fact alone means it cannot be the most widely exploited attack.Second, let's talk FREAK. It works by downgrading RSA to 512-bit keys, which can be cracked by supercomputers. This fact alone means it cannot be the most widely exploited attack -- even the NSA does not have sufficient compute power to crack as many keys as the Verizon DBIR claim were cracked.Now let's talk about how Verizon calculates when a vulnerability is responsible for an attack. They use this methodology:look at a compromised system (identified by AV scanning, IoCs, etc.)look at which unpatched vulnerabilities the system has (vuln scans)see if the system was attacked via those vulnerabilities (IDS)In other words, if you are vulnerable to FREAK, and the IDS tells you people attacked you with FREAK, and indeed you were compromised, then it seems only logical that they compromised you through FREAK.This sounds like a really good methodology -- but only to stupids. (Sorry for being harsh, I've been pointing out this methodology sucks for 15 years, and am getting frustrated people still believe in it.)Here's the problem with all data breach investigations. Systems get hacked, and we don't know why. Yet, there is enormous pressure to figure out why. Therefore, we seize on any plausible explanation. We then go through the gauntlet of logical fallacies, such as "confirmation bias", to support our conclusion. They torture the data until it produces the right results.In the majority of breach reports I've seen, the identified source of the compromise is bogus. That's why I never believed North Korea was behind the Sony attack -- I've read too many data breach reports fingering the wrong cause. Political pressure to come up with a cause, any cause, is immense.This specific logic, "vulnerable to X and attacked with X == breached with X" has been around with us for a long time. 15 years ago, IDS vendors integrated with vulnerability scanners to produce exactly these sorts of events. It's nonsense that never produced actionable data.In other words, in the Verizon report, things went this direction. FIRST, they investigated a system and found IoCs (indicators that the system had been compromised). SECOND, they did the correlation between vuln/IDS. They didn't do it the other way around, because such a system produces too much false data. False data is false data. If you aren't starting with this vuln/IDS correlation, then looking for IoCs, then there is no reason to believe such correlations will be robust afterwards.On of the reasons the data isn't robust is that IDS events do not mean what you think they mean. Most people in our industry treat them as "magic", that if an IDS triggers on a "FREAK" attack, then that's what happen.But that's not what happened. First of all, there is the issue of false-positives, whereby the system claims a "FREAK" attack happened, when nothing related to the issue happened. Looking at various IDSs, this should be rare for FREAK, but happens for other kinds of attacks.Then there is the issue of | ★★ | |||
| 2016-05-05 18:03:14 | Satoshi: how Craig Wright\'s deception worked (lien direct) | My previous post shows how anybody can verify Satoshi using a GUI. In this post, I'll do the same, with command-line tools (openssl). It's just a simple application of crypto (hashes, public-keys) to the problem.I go through this step-by-step discussion in order to demonstrate Craig Wright's scam. Dan Kaminsky's post and the redditors comes to the same point through a different sequence, but I think my way is clearer.Step #1: the Bitcoin addressWe know certain Bitcoin addresses correspond to Satoshi Nakamoto him/her self. For the sake of discussion, we'll use the address 15fszyyM95UANiEeVa4H5L6va7Z7UFZCYP. It's actually my address, but we'll pretend it's Satoshi's. In this post, I'm going to prove that this address belongs to me.The address isn't the public-key, as you'd expect, but the hash of the public-key. Hashes are a lot shorter, and easier to pass around. We only pull out the public-key when we need to do a transaction. The hashing algorithm is explained on this website [http://gobittest.appspot.com/Address]. It's basically base58(ripemd(sha256(public-key)).Step #2: You get the public-keyHashes are one-way, so given a Bitcoin address, we can't immediately convert it into a public-key. Instead, we have to look it up in the blockchain, the vast public ledger that is at the heart of Bitcoin. The blockchain records every transaction, and is approaching 70-gigabytes in size.To find an address's match public-key, we have to search for a transaction where the bitcoin is spent. If an address has only received Bitcoins, then its matching public-key won't appear in the Blockchain. In that case, a person trying to prove their identity will have to tell you the public-key, which is fine, of course, since the keys are designed to be public.Luckily, there are lots of websites that store the blockchain in a database and make it easy for us to browse. I use Blockchain.info. The URL to my address is:https://blockchain.info/address/15fszyyM95UANiEeVa4H5L6va7Z7UFZCYPThere is a list of transactions here where I spend coin. Let's pick the top one, at this URL:https://blockchain.info/tx/8c4263d864d4f36e4eb4065a877e3e9a68cbe1de63a7b1fda70096e1e209cbbbToward the bottom are the "scripts". Bitcoin has a small scripting language, allowing complex transactions to be created, but most transactions are simple. There are two common formats for these scripts, and old format and a new format. In the old format, you'll find the public-key in the Output Script. In the new format, you'll find the public-key in the Input Scripts. It'll be a long long number starting with "04".In this case, my public-key is:04b19ffb77b602e4ad3294f770130c7677374b84a7a164fe6a80c81f13833a673dbcdb15c29857ce1a23fca1c808b9c29404b84b986924e6ff08fb3517f38bc099You can verify this hashes to my Bitcoin address by the website I mention above.Step #3: You format the key according to OpenSSLOpenSSL wants the public-key in it's own format (wrapped in ASN.1 DER, then encoded in BASE64). I should just insert the JavaScript form to do it directly in this post, but | ★★★★★ | |||
| 2016-05-04 05:17:20 | Vulns are sparse, code is dense (lien direct) | The question posed by Bruce Schneier is whether vulnerabilities are "sparse" or "dense". If they are sparse, then finding and fixing them will improve things. If they are "dense", then all this work put into finding/disclosing/fixing them is really doing nothing to improve things.I propose a third option: vulns are sparse, but code is dense.In other words, we can secure specific things, like OpenSSL and Chrome, by researching the heck out of them, finding vulns, and patching them. The vulns in those projects are sparse.But, the amount of code out there is enormous, considering all software in the world. And it changes fast -- adding new vulns faster than our feeble efforts at disclosing/fixing them.So measured across all software, no, the secure community hasn't found any significant amount of bugs. But when looking at critical software, like OpenSSL and Chrome, I think we've made great strides forward.More importantly, let's ignore the actual benefits/costs of fixing bugs for the moment. What all this effort has done is teach us about the nature of vulns. Critical software is written to day in a vastly more secure manner than it was in the 1980s, 1990s, or even the 2000s. Windows, for example, is vastly more secure. Sure, others are still lagging (car makers, medical device makers), but they are quickly learning the lessons and catching up. Finding a vuln in an iPhone is hard -- so hard that hackers will earn $1 million doing it from the NSA rather than stealing your credit card info. 15 years ago, the opposite was true. The NSA didn't pay for Windows vulns because they fell out of trees, and hackers made more money from hacking your computer.My point is this: the "are vulns sparse/dense?" puts a straight-jacket around the debate. I see it form an orthogonal point of view. | ★★★★★ | |||
| 2016-05-02 20:23:20 | Satoshi: That\'s not how any of this works (lien direct) | In this WIRED article, Gaven Andresen says why he believes Craig Wright's claim to be Satoshi Nakamoto:“It's certainly possible I was bamboozled,†Andresen says. “I could spin stories of how they hacked the hotel Wi-fi so that the insecure connection gave us a bad version of the software. But that just seems incredibly unlikely. It seems the simpler explanation is that this person is Satoshi.â€That's not how this works. That's not how any of this works.The entire point of Bitcoin is that it's decentralized. We don't need to take Andresen's word for it. We don't need to take anybody's word for it. Nobody needs to fly to London and check it out on a private computer. Instead, you can just send somebody the signature, and they can verify it themselves. That the story was embargoed means nothing -- either way, Andresen was constrained by an NDA. Since they didn't do it the correct way, and were doing it the roundabout way, the simpler explanation is that he was being bamboozled.Below is an example of this, using the Electrum Bitcoin wallet software: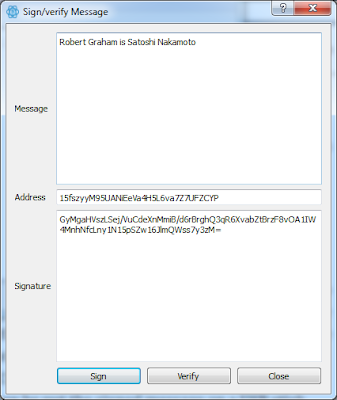 This proves that the owner of the Bitcoin Address has signed the Message, producing the Signature. I typed the first two fields, hit the "Sign" button. The wallet looked up the address in my wallet (which can have many addresses), found the matching private key that only I posess, then signed the message by filling in the bottom window.If you had reason to believe that this address belonged to Satoshi Nakamoto, such as if it had been the first blocks, then I would have just proven to you that I am indeed Satoshi. You wouldn't need to take anybody's word for it. You'd simply type in the fields (or copy/paste), hit "verify", and verify for yourself.So you can verify me, here are the strings you can copy/paste:Robert Graham is Satoshi Nakamoto15fszyyM95UANiEeVa4H5L6va7Z7UFZCYP GyMgaHVszLSej/VuCdeXnMmiB/d6rBrghQ3qR6XvabZtBrzF8vOA1IW4MnhNfcLny1N15pSZw16JlmQWss7y3zM=You should get either a "Signature verified" or "Wrong signature" message when you click the "Verify" button. This proves that the owner of the Bitcoin Address has signed the Message, producing the Signature. I typed the first two fields, hit the "Sign" button. The wallet looked up the address in my wallet (which can have many addresses), found the matching private key that only I posess, then signed the message by filling in the bottom window.If you had reason to believe that this address belonged to Satoshi Nakamoto, such as if it had been the first blocks, then I would have just proven to you that I am indeed Satoshi. You wouldn't need to take anybody's word for it. You'd simply type in the fields (or copy/paste), hit "verify", and verify for yourself.So you can verify me, here are the strings you can copy/paste:Robert Graham is Satoshi Nakamoto15fszyyM95UANiEeVa4H5L6va7Z7UFZCYP GyMgaHVszLSej/VuCdeXnMmiB/d6rBrghQ3qR6XvabZtBrzF8vOA1IW4MnhNfcLny1N15pSZw16JlmQWss7y3zM=You should get either a "Signature verified" or "Wrong signature" message when you click the "Verify" button.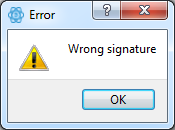  There may be a little strangeness since my original message is ASCII, but if you copy out of this webpage, it'll go in as Unicode, but it appears that this formatting information is ignored in the verification process, so it'll still work.SummaryOccam's Razor i There may be a little strangeness since my original message is ASCII, but if you copy out of this webpage, it'll go in as Unicode, but it appears that this formatting information is ignored in the verification process, so it'll still work.SummaryOccam's Razor i |
||||
| 2016-05-01 20:23:23 | Touch Wipe: a question for you lawyers (lien direct) | Whether the police can force you to unlock your iPhone depends upon technicalities. They can't ask you for your passcode, because that would violate the 5th Amendment right against "self incrimination". On the other hand, they can force you to press your finger on the TouchID button, or (as it has been demonstrated) unlock the phone themselves using only your fingerprint.So I propose adding a new technicality into the mix: "Touch Wipe". In addition to recording fingerprints to unlock the phone, Apple/Android should add the feature where users record fingerprints to wipe (erase) the phone. For example, I may choose my thumb to unlock, and my forefinger to wipe.Indeed, I may record only one digit to unlock, and all nine remaining digits to wipe. Or even, I may decide to record all 10 digits on both hands to wipe, and not use Touch ID at all to unlock (relying solely on the passcode).This now presents the problem for the police. They can't force me to unlock the phone. They can't get around that by using my fingerprints, because they might inadvertently destroy evidence.The legal system is resilient against legal trickery such as this. If think you've figured out a way to beat the system, then it's usually because you just don't understand the system well enough. But I think I've figured out how to beat this system, so I write this up so that lawyers can explain why I'm wrong. | ||||
| 2016-04-27 13:48:07 | None (lien direct) | Who's your lawyer. Insights & Wisdom via HBO's Silicon Valley (S.3, E. 1)[if gte mso 9]> [if gte mso 9]> Normal 0 false false false EN-US X-NONE X-NONE [if gte mso 9]> | ||||
| 2016-04-26 20:14:09 | My next scan (lien direct) | So starting next week, running for a week, I plan on scanning for ports 0-65535 (TCP). Each probe will be completely random selection of IP+port. The purpose is to answer the question about the most common open ports.This would take a couple years to scan for all ports, so I'm not going to do that. But, scanning for a week should give me a good statistical sampling of 1% of the total possible combinations.Specifically, the scan will open a connection and wait a few seconds for a banner. Protocols like FTP, SSH, and VNC reply first with data, before you send requests. Doing this should find such things lurking at odd ports. We know that port 22 is the most common for SSH, but what is the second most common?Then, if I get no banner in response, I'll send an SSL "Hello" message. We know that port 443 is the most common SSL port, but what is the second most common?In other words, by waiting for SSH, then sending SSL, I'll find SSH even it's on the (wrong) port of 443, and I'll find SSL even if it's on port 22. And all other ports, too.Anyway, I point this out because people will start to see a lot of strange things in their logs. Also, I'm hoping that people will have suggestions before I start the scan for additional things to do during the scan.Update: I'll be scanning from addresses between 209.126.230.70 and 209.126.230.78. BTW, yes '0' is a valid port.BTW, numbers larger than 65535 or smaller than 0 (negative numbers) aren't valid -- but they'll work in most applications because they simply use the lower 16-bits of any numbers that are given. Thus, port number -1 is just 65535, and port number 65536 is the same as 0. |
||||
| 2016-04-14 03:50:25 | Defining "Gray Hat" (lien direct) | WIRED has written an article defining “White Hatâ€, “Black Hatâ€, and “Grey Hatâ€. It's incomplete and partisan.Black Hats are the bad guys: cybercriminals (like Russian cybercrime gangs), cyberspies (like the Chinese state-sponsored hackers that broke into OPM), or cyberterrorists (ISIS hackers who want to crash the power grid). They may or may not include cybervandals (like some Anonymous activity) that simply defaces websites. Black Hats are those who want to cause damage or profit at the expense of others.White Hats do the same thing as Black Hats, but are the good guys. The break into networks (as pentesters), but only with permission, when a company/organization hires them to break into their own network. They research the security art, such vulnerabilities, exploits, and viruses. When they find vulnerabilities, they typically work to fix/patch them. (That you frequently have to apply security updates to your computers/devices is primarily due to White Hats). They develop products and tools for use by good guys (even though they sometimes can be used by the bad guys). The movie “Sneakers†refers to a team of White Hat hackers.Grey Hat is anything that doesn't fit nicely within these two categories. There are many objective meanings. It can sometimes refer to those who break the law, but who don't have criminal intent. It can sometimes include the cybervandals, whose activities are more of a prank rather than a serious enterprise. It can refer to “Search Engine Optimizers†who use unsavory methods to trick search engines like Google to rank certain pages higher in search results, to generate advertising profits.But, it's also used subjectively, to simply refer to activities the speaker disagrees with. Our community has many debates over proper behavior. Those on one side of a debate frequently use Gray Hat to refer to those on the other side of the debate.The biggest recent debate is “0day sales to the NSAâ€, which blew up after Stuxnet, and in particular, after Snowden. This is when experts look for bugs/vulnerabilities, but instead of reporting them to the vendor to be fixed (as White Hats typically do), they sell the bugs to the NSA, so the vulnerabilities (call “0days†in this context) can be used to hack computers in intelligence and military operations. Partisans who don't like the NSA use “Grey Hat†to refer to those who sell 0days to the NSA.WIRED's definition is this partisan definition. Kim Zetter has done more to report on Stuxnet than any other journalist, which is why her definition is so narrow.But Google is your friend. If you search for “Gray Hat†on Google and set the time range to pre-Stuxnet, then you'll find no use of the term that corresponds to Kim's definition, despite the term being in widespread use for more than a decade by that point. Instead, you'll find things like this EFF “Gray Hat Guideâ€. You'll also find how L0pht used the term to describe themselves when selling their password cracking tool called “L0phtcrackâ€, from back in 1998.Fast forward to today, activists from the EFF and ACLU call 0day sellers “merchants of deathâ€. But those on the other side of the debate point out how the 0days in Stuxnet saved thousands of lives. The US government had decided to stop Iran's nuclear program, and 0days gave them a way to do that without bombs, assassinations, or a shooting war. Those who engage in 0day sales do so with the highest professional ethics. If that WaPo article |
To see everything:
Our RSS (filtrered)
