What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-06-03 11:12:04 | How to track that annoying pop-up (lien direct) | In a recent update to their Office suite on Windows, Microsoft made a mistake where every hour, for a fraction of a second, a black window pops up on the screen. This leads many to fear their system has been infected by a virus. I thought I'd document how to track this down.The short answer is to use Mark Russinovich's "sysinternals.com" tools. He's Windows internals guru at Microsoft and has been maintaining a suite of tools that are critical for Windows system maintenance and security. Copy all the tools from "https://live.sysinternals.com". Also, you can copy with Microsoft Windows Networking (SMB). Of these tools, what we want is something that looks at "processes". There are several tools that do this, but focus on processes that are currently running. What we want is something that monitors process creation.The tool for that is "sysmon.exe". It can monitor not only process creation, but a large number of other system events that a techy can use to see what the system has been doing, and if you are infected with a virus.Sysmon has a fairly complicated configuration file, and if you enabled everything, you'd soon be overwhelmed with events. @SwiftOnSecurity has published a configuration file they use in the real world in real environment that cuts down on the noise, and focuses on events that are really important. It enables monitoring of "process creation", but filters out know good processes that might fill up your logs. You grab the file here. Save it to the same directory to where you saved Sysmon:https://raw.githubusercontent.com/SwiftOnSecurity/sysmon-config/master/sysmonconfig-export.xmlOnce you've done it, run the following command to activate the Sysmon monitoring service using this configuration file by running the following command as Administrator. (Right click on the Command Prompt icon and select More/Run as Administrator).sysmon.exe -accepteula -i sysmonconfig-export.xml Of these tools, what we want is something that looks at "processes". There are several tools that do this, but focus on processes that are currently running. What we want is something that monitors process creation.The tool for that is "sysmon.exe". It can monitor not only process creation, but a large number of other system events that a techy can use to see what the system has been doing, and if you are infected with a virus.Sysmon has a fairly complicated configuration file, and if you enabled everything, you'd soon be overwhelmed with events. @SwiftOnSecurity has published a configuration file they use in the real world in real environment that cuts down on the noise, and focuses on events that are really important. It enables monitoring of "process creation", but filters out know good processes that might fill up your logs. You grab the file here. Save it to the same directory to where you saved Sysmon:https://raw.githubusercontent.com/SwiftOnSecurity/sysmon-config/master/sysmonconfig-export.xmlOnce you've done it, run the following command to activate the Sysmon monitoring service using this configuration file by running the following command as Administrator. (Right click on the Command Prompt icon and select More/Run as Administrator).sysmon.exe -accepteula -i sysmonconfig-export.xml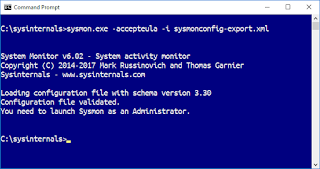 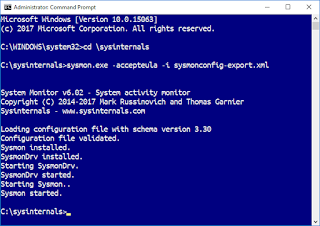 Now sit back and relax until that popup happens again. Right after it does, go into the "Event Viewer" application (click on Windows menu and type "Event Viewer", or run 'eventvwr.exe'. Now y Now sit back and relax until that popup happens again. Right after it does, go into the "Event Viewer" application (click on Windows menu and type "Event Viewer", or run 'eventvwr.exe'. Now y |
Guideline | |||
| 2017-05-30 08:25:36 | I want to talk for a moment about tolerance (lien direct) | This post is in response to this Twitter thread. I was going to do a series of tweets in response, but as the number grew, I thought it'd better be done in a blog.I want to talk for a moment about free speech advocacy. This'll be a thread, 1/many.- Jillian (@jilliancyork) May 30, 2017She thinks we are fighting for the rights of Nazis. We aren't -- indeed, the fact that she thinks we are is exactly the problem. They aren't Nazis.The issue is not about a slippery slope that first Nazi's lose free speech, then other groups start losing their speech as well. The issue is that it's a slippery slope that more and more people get labeled a Nazi. And we are already far down that slope.The "alt-right" is a diverse group. Like any group. Vilifying the entire alt-right by calling them Nazi's is like lumping all Muslims in with ISIS or Al Qaeda. We really don't have Nazi's in America. Even White Nationalists don't fit the bill. Nazism was about totalitarianism, real desire to exterminate Jews, lebensraum, and Aryan superiority. Sure, some of these people exist, but they are a fringe, even among the alt-right.It's at this point we need to discuss words like "tolerance". I don't think it means what you think it means.The idea of tolerance is that reasonable people can disagree. You still believe you are right, and the other person is wrong, but you accept that they are nonetheless a reasonable person with good intentions, and that they don't need to be punished for holding the wrong opinion.Gay rights is a good example. I agree with you that there is only one right answer to this. Having spent nights holding my crying gay college roommate, because his father hated gays, has filled me with enormous hatred and contempt for people like his father. I've done my fair share shouting at people for anti-gay slurs.Yet on the other hand, progressive icons like Barack Obama and Hillary Clinton have had evolving positions on gay rights issues, such as having opposed gay marriage at one time.Tolerance means accepting that a person is reasonable, intelligent, and well-meaning -- even if they oppose gay marriage. It means accepting that Hillary and Obama were reasonable people, even when they were vocally opposing gay marriage.I'm libertarian. Like most libertarians, I support wide open borders, letting any immigrant across the border for any reason. To me, Hillary's and Obama's immigration policies are almost as racist as Trump's. I have to either believe all you people supporting Hillary/Obama are irredeemably racist -- or that well-meaning, good people can disagree about immigration.I could go through a long list of issues that separate the progressive left and alt-right, and my point would always be the same. While people disagree on issues, and I have my own opinions about which side is right, there are reasonable people on both sides. If there are issues that divide our country down the middle, then by definition, both sides are equally reasonable. The problem with the progressive left is that they do not tolerate this. They see the world as being between one half who hold the correct opinions, and the other half who are unreasonable.What defines the "alt-right" is not Nazism or White Nationalism, but the reaction of many on the right to intolerance of many on the left. Every time somebody is punished and vilified for uttering what is in fact a reasonable difference of opinion, they join the "alt-right".The issue at stake here, the issue that the ACLU is defending, is after that violent attack on the Portland train by an extremist, the city is denying all "alt-right" protesters the right to march. It's blaming all those of the "alt-right" for the actions of one of their member. It's si | ||||
| 2017-05-22 21:46:37 | Houston we have a problem! (lien direct) |  Of the many undesirable results of the Space Program is the fetishization of the "mission control center", with it's rows of workstations facing a common central screen. Ever since, anybody with any sort of mission now has a similar control center.It's a pain for us in the cybersecurity community because every organization wants a "security operations center" laid out the same way. The point of he room isn't to create something that's efficient for working, but one that will impress visitors. The things done to impress customers can often make an already difficult job even more difficult. Of the many undesirable results of the Space Program is the fetishization of the "mission control center", with it's rows of workstations facing a common central screen. Ever since, anybody with any sort of mission now has a similar control center.It's a pain for us in the cybersecurity community because every organization wants a "security operations center" laid out the same way. The point of he room isn't to create something that's efficient for working, but one that will impress visitors. The things done to impress customers can often make an already difficult job even more difficult. I point this out because of the "glowing globe" picture from President Trump's visit to Saudi Arabia. It's supposed to celebrate the opening of the "Global Center for Combating Extremist Ideology" (http://etidal.org). Zoom the camera out a bit, and you can see it's the mission control center from hell. I point this out because of the "glowing globe" picture from President Trump's visit to Saudi Arabia. It's supposed to celebrate the opening of the "Global Center for Combating Extremist Ideology" (http://etidal.org). Zoom the camera out a bit, and you can see it's the mission control center from hell.  Manually counting, I see three sides, each with slightly more than 100 workstations/employees, or more than 300 in total. I don't know if they intend all three sections to focus on the same sets of problems, or if they are split into three different tasks (e.g. broadcast TV vs. Internet content). Their brochure is unclear. I suspect in the long it'll be full of third country nations from a broad swath of Muslim nations who can speak the local languages and dialects, working in a sweat-shop manner.In any case, it's clear that the desire for show/spectacle has far outstripped any practical use.The more I read about this, the more Orwellian it seems. Rather than opposing ISIS's violence, it seems more intent on promoting a Saudi ideology. The whole spectacle seems intent on tricking the Trump administration into supporting something it really should be opposing. Manually counting, I see three sides, each with slightly more than 100 workstations/employees, or more than 300 in total. I don't know if they intend all three sections to focus on the same sets of problems, or if they are split into three different tasks (e.g. broadcast TV vs. Internet content). Their brochure is unclear. I suspect in the long it'll be full of third country nations from a broad swath of Muslim nations who can speak the local languages and dialects, working in a sweat-shop manner.In any case, it's clear that the desire for show/spectacle has far outstripped any practical use.The more I read about this, the more Orwellian it seems. Rather than opposing ISIS's violence, it seems more intent on promoting a Saudi ideology. The whole spectacle seems intent on tricking the Trump administration into supporting something it really should be opposing. |
||||
| 2017-05-12 02:51:43 | Some notes on Trump\'s cybersecurity Executive Order (lien direct) | President Trump has finally signed an executive order on "cybersecurity". The first draft during his first weeks in power were hilariously ignorant. The current draft, though, is pretty reasonable as such things go. I'm just reading the plain language of the draft as a cybersecurity expert, picking out the bits that interest me. In reality, there's probably all sorts of politics in the background that I'm missing, so I may be wildly off-base.Holding managers accountableThis is a great idea in theory. But government heads are rarely accountable for anything, so it's hard to see if they'll have the nerve to implement this in practice. When the next breech happens, we'll see if anybody gets fired."antiquated and difficult to defend Information Technology"The government uses laughably old computers sometimes. Forces in government wants to upgrade them. This won't work. Instead of replacing old computers, the budget will simply be used to add new computers. The old computers will still stick around."Legacy" is a problem that money can't solve. Programmers know how to build small things, but not big things. Everything starts out small, then becomes big gradually over time through constant small additions. What you have now is big legacy systems. Attempts to replace a big system with a built-from-scratch big system will fail, because engineers don't know how to build big systems. This will suck down any amount of budget you have with failed multi-million dollar projects.It's not the antiquated systems that are usually the problem, but more modern systems. Antiquated systems can usually be protected by simply sticking a firewall or proxy in front of them."address immediate unmet budgetary needs necessary to manage risk"Nobody cares about cybersecurity. Instead, it's a thing people exploit in order to increase their budget. Instead of doing the best security with the budget they have, they insist they can't secure the network without more money.An alternate way to address gaps in cybersecurity is instead to do less. Reduce exposure to the web, provide fewer services, reduce functionality of desktop computers, and so on. Insisting that more money is the only way to address unmet needs is the strategy of the incompetent.Use the NIST frameworkProbably the biggest thing in the EO is that it forces everyone to use the NIST cybersecurity framework.The NIST Framework simply documents all the things that organizations commonly do to secure themselves, such run intrusion-detection systems or impose rules for good passwords.There are two problems with the NIST Framework. The first is that no organization does all the things listed. The second is that many organizations don't do the things well.Password rules are a good example. Organizations typically had bad rules, such as frequent changes and complexity standards. So the NIST Framework documented them. But cybersecurity experts have long opposed those complex rules, so have been fighting NIST on them.Another good example is intrusion-detection. These days, I scan the entire Internet, setting off everyone's intrusion-detection systems. I can see first hand that they are doing intrusion-detection wrong. But the NIST Framework recommends they do it, because many organizations do it, but the NIST Framework doesn't demand they do it well.When this EO forces everyone to follow the NIST Framework, then, it's likely just going to i | Guideline | Yahoo Tesla | ||
| 2017-05-10 01:52:09 | John Oliver is wrong about Net Neutrality (lien direct) | People keep linking to John Oliver bits. We should stop doing this. This is comedy, but people are confused into thinking Oliver is engaging in rational political debate:Tune in now to catch @lastweetonight with @iamjohnoliver on why we need net neutrality and Title II. https://t.co/muSGrItCp9- EFF (@EFF) May 8, 2017Enlightened people know that reasonable people disagree, that there's two sides to any debate. John Oliver's bit erodes that belief, making one side (your side) sound smart, and the other side sound unreasonable.The #1 thing you should know about Net Neutrality is that reasonable people disagree. It doesn't mean they are right, only that they are reasonable. They aren't stupid. They aren't shills for the telcom lobby, or confused by the telcom lobby. Indeed, those opposed to Net Neutrality are the tech experts who know how packets are routed, whereas the supporters tend only to be lawyers, academics, and activists. If you think that the anti-NetNeutrality crowd is unreasonable, then you are in a dangerous filter bubble.Most everything in John Oliver's piece is incorrect.For example, he says that without Net Neutrality, Comcast can prefer original shows it produces, and slow down competing original shows by Netflix. This is silly: Comcast already does that, even with NetNeutrality rules.Comcast owns NBC, which produces a lot of original shows. During prime time (8pm to 11pm), Comcast delivers those shows at 6-mbps to its customers, while Netflix is throttled to around 3-mbps. Because of this, Comcast original shows are seen at higher quality than Netflix shows.Comcast can do this, even with NetNeutrality rules, because it separates its cables into "channels". One channel carries public Internet traffic, like Netflix. The other channels carry private Internet traffic, for broadcast TV shows and pay-per-view.All NetNeutrality means is that if Comcast wants to give preference to its own contents/services, it has to do so using separate channels on the wire, rather than pushing everything over the same channel. This is a detail nobody tells you because NetNeutrality proponents aren't techies. They are lawyers and academics. They maximize moral outrage, while ignoring technical details.Another example in Oliver's show is whether search engines like Google or the (hypothetical) Bing can pay to get faster access to customers. They already do that. The average distance a packet travels on the web is less than 100-miles. That's because the biggest companies (Google, Facebook, Netflix, etc.) pay to put servers in your city close to you. Smaller companies, such as search engine DuckDuckGo.com, also pay third-party companies like Akamai or Amazon Web Services to get closer to you. The smallest companies, however, get poor performance, being a thousand miles away.You can test this out for yourself. Run a packet-sniffer on your home network for a week, then for each address, use mapping tools like ping and traceroute to figure out how far away things are.The Oliver bit mentioned how Verizon banned Google Wallet. Again, technical details are important here. It had nothing to do with Net Neutrality issues blocking network packets, but only had to do with Verizon-branded phones blocking access to the encrypted enclave. You could use Google Wallet on unlocked phones you bought separately. Moreover, market forces won in the end, with Google Wallet (aka. Android Wall | ||||
| 2017-05-07 20:46:01 | Hacker dumps, magnet links, and you (lien direct) | In an excellent post pointing out Wikileaks deserves none of the credit given them in the #MacronLeaks, the author erroneously stated that after Archive.org took down the files, that Wikileaks provided links to a second archive. This is not true. Instead, Wikileaks simply pointed to what's known as "magnet links" of the first archive. Understanding magnet links is critical to understanding all these links and dumps, so I thought I'd describe them.The tl;dr version is this: anything published via BitTorrent has a matching "magnet link" address, and the contents can still be reached via magnet links when the original publisher goes away.In this case, the leaker uploaded to "archive.org", a popular Internet archiving resource. This website allows you to either download files directly, which is slow, or via peer-to-peer using BitTorrent, which is fast. As you know, BitTorrent works by all the downloaders exchanging pieces with each other, rather getting them from the server. I give you a piece you don't have, in exchange for a piece I don't have.BitTorrent, though still requires a "torrent" (a ~30k file that lists all the pieces) and a "tracker" (http://bt1.archive.org:6969/announce) that keeps a list of all the peers so they can find each other. The tracker also makes sure that every piece is available from at least one peer.When "archive.org" realized what was happening, they deleted the leaked files, the torrent, and the tracking.However, BitTorrent has another feature called "magnet links". This is simply the "hash" of the "torrent" file contents, which looks something like "06724742e86176c0ec82e294d299fba4aa28901a". (This isn't a hash of the entire file, but just the important parts, such as the filenames and sizes).Along with downloading files, BitTorrent software on your computer also participates in a "distributed hash" network. When using a torrent file to download, your BitTorrent software still tell other random BitTorrent clients about the hash. Knowledge of this hash thus spreads throughout the BitTorrent world. It's only 16 bytes in size, so the average BitTorrent client can keep track of millions of such hashes while consuming very little memory or bandwidth.If somebody decides they want to download the BitTorrent with that hash, they broadcast that request throughout this "distributed hash" network until they find one or more people with the full torrent. They then get the torrent description file from them, and also a list of peers in the "swarm" who are downloading the file.Thus, when the original torrent description file, the tracker, and original copy goes away, you can still locate the swarm of downloaders through this hash. As long as all the individual pieces exist in the swarm, you can still successfully download the original file.In this case, one of the leaked documents was a 2.3 gigabyte file called "langannerch.rar". The torrent description file called "langanerch_archive.torrent" is 26 kilobytes in size. The hash (magnet link) is 16 bytes in size, written "magnet:?xt=urn:btih:06724742e86176c0ec82e294d299fba4aa28901a". If you've got BitTorrent software installed and click on the link, you'll join the swarm and start downloading the file, even though the original torrent/tracker/files have gone away.According to my BitTorrent client, there are currently 108 people in the swarm downloading this file world-wide. I'm currently connected to 11 of them. Most of them appear to be located in France. | ★★★★ | |||
| 2017-05-06 04:15:35 | Some notes on #MacronLeak (lien direct) |  Tonight (Friday May 5 2017) hackers dumped emails (and docs) related to French presidential candidate Emmanuel Macron. He's the anti-Putin candidate running against the pro-Putin Marin Le Pen. I thought I'd write up some notes.Are they Macron's emails?No. They are e-mails from members of his staff/supporters, namely Alain Tourret, Pierre Person, Cedric O??, Anne-Christine Lang, and Quentin Lafay.There are some documents labeled "Macron" which may have been taken from his computer, cloud drive -- his own, or an assistant.Who done it?Obviously, everyone assumes that Russian hackers did it, but there's nothing (so far) that points to anybody in particular.It appears to be the most basic of phishing attacks, which means anyone could've done it, including your neighbor's pimply faced teenager.Update: Several people [*] have pointed out Trend Micro reporting that Russian/APT28 hackers were targeting Macron back on April 24. Coincidentally, this is also the latest that emails appear in the dump.What's the hacker's evil plan?Everyone is proposing theories about the hacker's plan, but the most likely answer is they don't have one. Hacking is opportunistic. They likely targeted everyone in the campaign, and these were the only victims they could hack. It's probably not the outcome they were hoping for.But since they've gone through all the work, it'd be a shame to waste it. Thus, they are likely releasing the dump not because they believe it will do any good, but because it'll do them no harm. It's a shame to waste all the work they put into it.If there's any plan, it's probably a long range one, serving notice that any political candidate that goes against Putin will have to deal with Russian hackers dumping email.Why now? Why not leak bits over time like with Clinton?France has a campaign blackout starting tonight at midnight until the election on Sunday. Thus, it's the perfect time to leak the files. Anything salacious, or even rumors of something bad, will spread viraly through Facebook and Twitter, without the candidate or the media having a good chance to rebut the allegations.The last emails in the logs appear to be from April 24, the day after the first round vote (Sunday's vote is the second, runoff, round). Thus, the hackers could've leaked this dump any time in the last couple weeks. They chose now to do it.Are the emails verified?Yes and no.Yes, we have DKIM signatures between people's accounts, so we know for certain that hackers successfully breached these accounts. DKIM is an anti-spam method that cryptographically signs emails by the sending domain (e.g. @gmail.com), and thus, can also verify the email hasn't been altered or forged.But no, when a salacious email or document is found in the dump Tonight (Friday May 5 2017) hackers dumped emails (and docs) related to French presidential candidate Emmanuel Macron. He's the anti-Putin candidate running against the pro-Putin Marin Le Pen. I thought I'd write up some notes.Are they Macron's emails?No. They are e-mails from members of his staff/supporters, namely Alain Tourret, Pierre Person, Cedric O??, Anne-Christine Lang, and Quentin Lafay.There are some documents labeled "Macron" which may have been taken from his computer, cloud drive -- his own, or an assistant.Who done it?Obviously, everyone assumes that Russian hackers did it, but there's nothing (so far) that points to anybody in particular.It appears to be the most basic of phishing attacks, which means anyone could've done it, including your neighbor's pimply faced teenager.Update: Several people [*] have pointed out Trend Micro reporting that Russian/APT28 hackers were targeting Macron back on April 24. Coincidentally, this is also the latest that emails appear in the dump.What's the hacker's evil plan?Everyone is proposing theories about the hacker's plan, but the most likely answer is they don't have one. Hacking is opportunistic. They likely targeted everyone in the campaign, and these were the only victims they could hack. It's probably not the outcome they were hoping for.But since they've gone through all the work, it'd be a shame to waste it. Thus, they are likely releasing the dump not because they believe it will do any good, but because it'll do them no harm. It's a shame to waste all the work they put into it.If there's any plan, it's probably a long range one, serving notice that any political candidate that goes against Putin will have to deal with Russian hackers dumping email.Why now? Why not leak bits over time like with Clinton?France has a campaign blackout starting tonight at midnight until the election on Sunday. Thus, it's the perfect time to leak the files. Anything salacious, or even rumors of something bad, will spread viraly through Facebook and Twitter, without the candidate or the media having a good chance to rebut the allegations.The last emails in the logs appear to be from April 24, the day after the first round vote (Sunday's vote is the second, runoff, round). Thus, the hackers could've leaked this dump any time in the last couple weeks. They chose now to do it.Are the emails verified?Yes and no.Yes, we have DKIM signatures between people's accounts, so we know for certain that hackers successfully breached these accounts. DKIM is an anti-spam method that cryptographically signs emails by the sending domain (e.g. @gmail.com), and thus, can also verify the email hasn't been altered or forged.But no, when a salacious email or document is found in the dump |
Uber APT 28 | |||
| 2017-05-03 15:00:26 | FBI\'s Comey dangerous definition of "valid" journalism (lien direct) | The First Amendment, the "freedom of speech" one, does not mention journalists. When it says "freedom of the press" it means the physical printing press. Yes, that does include newspapers, but it also includes anybody else publishing things, such as the famous agitprop pamphlets published by James Otis, John Dickinson, and Thomas Paine. There was no journalistic value to Thomas Paine's Common Sense. The pamphlet argued for abolishing the monarchy and for American independence.Today in testimony before congress, FBI directory James Comey came out in support of journalism, pointing out that they would not prosecute journalists doing their jobs. But he then modified his statement, describing "valid" journalists as those who in possession of leaks would first check with the government, to avoid publishing anything that would damage national security. It's a power the government has abused in the past to delay or censor leaks. It's specifically why Edward Snowden contacted Glenn Greenwald and Laura Poitras -- he wanted journalists who would not kowtow the government on publishing the leaks.Comey's testimony today was in regards to prosecuting Assange and Wikileaks. Under the FBI's official "journalist" classification scheme, Wikileaks are not real journalists, but instead publish "intelligence porn" and are hostile to America's interests.To be fair, there may be good reasons to prosecute Assange. Publishing leaks is one thing, but the suspicion with Wikileaks is that they do more, that they actively help getting the leaks in the first place. The original leaks that started Wikileaks may have come from hacks by Assange himself. Assange may have helped Manning grab the diplomatic cables. Wikileaks may have been involved in hacking the DNC and Podesta emails, more than simply receiving and publishing the information.If that's the case, then the US government would have good reason to prosecute Wikileaks.But that's not what Comey said today. Instead, Comey referred only to Wikileaks constitutionally protected publishing activities, and how since they didn't fit his definition of "journalism", they were open to prosecution. This is fundamentally wrong, and a violation of the both the spirit and the letter of the First Amendment. The FBI should not have a definition of "journalism" it thinks is valid. Yes, Assange is an anti-American douchebag. Being an apologist for Putin's Russia disproves his claim of being a neutral journalist targeting the corrupt and powerful. But these activities are specifically protected by the Constitution.If this were 1776, Comey would of course be going after Thomas Paine, for publishing "revolution porn", and not being a real journalist. | ||||
| 2017-04-26 00:40:17 | "Fast and Furious 8: Fate of the Furious" (lien direct) | So "Fast and Furious 8" opened this weekend to world-wide box office totals of $500,000,000. I thought I'd write up some notes on the "hacking" in it. The tl;dr version is this: yes, while the hacking is a bit far fetched, it's actually more realistic than the car chase scenes, such as winning a race with the engine on fire while in reverse.[SPOILERS]Car hacking |
Tesla | |||
| 2017-04-18 14:49:30 | Mirai, Bitcoin, and numeracy (lien direct) | Newsweek (the magazine famous for outing the real Satoshi Nakamoto) has a story about how a variant of the Mirai botnet is mining bitcoin. They fail to run the numbers.The story repeats a claim by Mcafee that 2.5 million devices were infected with Mirai at some point in 2016. If they were all mining bitcoin, how much money would the hackers be earning?I bought security cameras and infected them with Mirai. A typical example of the CPU running on an IoT device is an ARM926EJ-S processor. As this website reports, such a processor running at 1.2 GHz can mine at a rate of 0.187-megahashes/second. That's a bit fast for an IoT device, most are slower, some are faster, we'll just use this as the average. As this website reports, such a processor running at 1.2 GHz can mine at a rate of 0.187-megahashes/second. That's a bit fast for an IoT device, most are slower, some are faster, we'll just use this as the average. According to this website, the current hash-rate of all minters is around 4-million terahashes/second. According to this website, the current hash-rate of all minters is around 4-million terahashes/second. Bitcoin blocks are mined every 10 minutes, with the current (April 2017) reward set at 12.5 bitcoins per block, giving roughly 1800 bitcoins/day in reward.The current price of bitcoin is $1191. Bitcoin blocks are mined every 10 minutes, with the current (April 2017) reward set at 12.5 bitcoins per block, giving roughly 1800 bitcoins/day in reward.The current price of bitcoin is $1191. Okay, let's plug all these numbers in: total Mirai hash-rate = 2.5 million bots times 0.185 megahash/sec = 0.468 terahashes/second daily Bitcoin earnings = $1191 times 1800 = $2.1 million/day daily Mirai earnings = (0.468 divided by 4-million) times $2.1 million = $0.25In other words, if the entire Mirai botnet of 2.5 million IoT devices was furiously mining bitcoin, it's total earnings would be $0.25 (25 cents) per day.ConclusionIf 2.5 million IoT devices mine Bitcoin, they'd earn in total 25 pennies per day. It's inconceivable that anybody would add bitcoin mining to the Mirai botnet other than as a joke. Okay, let's plug all these numbers in: total Mirai hash-rate = 2.5 million bots times 0.185 megahash/sec = 0.468 terahashes/second daily Bitcoin earnings = $1191 times 1800 = $2.1 million/day daily Mirai earnings = (0.468 divided by 4-million) times $2.1 million = $0.25In other words, if the entire Mirai botnet of 2.5 million IoT devices was furiously mining bitcoin, it's total earnings would be $0.25 (25 cents) per day.ConclusionIf 2.5 million IoT devices mine Bitcoin, they'd earn in total 25 pennies per day. It's inconceivable that anybody would add bitcoin mining to the Mirai botnet other than as a joke.Bonus: A single 5 kilogram |
||||
| 2017-03-19 02:45:37 | Pranksters gonna prank (lien direct) | So Alfa Bank (the bank whose DNS traffic link it to trump-email.com) is back in the news with this press release about how in the last month, hackers have spoofed traffic trying to make it look like there's a tie with Trump. In other words, Alfa claims these packets are trying to frame them for a tie with Trump now, and thus (by extension) it must've been a frame last October.There is no conspiracy here: it's just merry pranksters doing pranks (as this CNN article quotes me).Indeed, among the people pranking has been me (not the pranks mentioned by Alfa, but different pranks). I ran a scan sending packets from IP address to almost everyone one the Internet, and set the reverse lookup to "mail1.trumpemail.com". Sadly, my ISP doesn't allow me to put hyphens in the name, so it's not "trump-email.com" as it should be in order to prank well.Geeks gonna geek and pranksters gonna prank. I can imagine all sorts of other fun pranks somebody might do in order to stir the pot. Since the original news reports of the AlfaBank/trump-email.com connection last year, we have to assume any further data is tainted by goofballs like me goofing off.By the way, in my particular case, there's a good lesson to be had here about the arbitrariness of IP addresses and names. There is no server located at my IP address of 209.216.230.75. No such machine exists. Instead, I run my scans from a nearby machine on the same network, and "spoof" that address with masscan:$ masscan 0.0.0.0/0 -p80 --banners --spoof-ip 209.216.230.75This sends a web request to every machine on the Internet from that IP address, despite no machine anywhere being configured with that IP address.I point this out because people are confused by the meaning of an "IP address", or a "server", "domain", and "domain name". I can imagine the FBI looking into this and getting a FISA warrant for the server located at my IP address, and my ISP coming back and telling them that no such server exists, nor has a server existed at that IP address for many years.In the case of last years story, there's little reason to believe IP spoofing was happening, but the conspiracy theory still breaks down for the same reason: the association between these concepts is not what you think it is. Listrak, the owner of the server at the center of the conspiracy, still reverse resolves the IP address 66.216.133.29 as "mail1.trump-email.com", either because they are lazy, or because they enjoy the lulz. Sadly, my ISP doesn't allow me to put hyphens in the name, so it's not "trump-email.com" as it should be in order to prank well.Geeks gonna geek and pranksters gonna prank. I can imagine all sorts of other fun pranks somebody might do in order to stir the pot. Since the original news reports of the AlfaBank/trump-email.com connection last year, we have to assume any further data is tainted by goofballs like me goofing off.By the way, in my particular case, there's a good lesson to be had here about the arbitrariness of IP addresses and names. There is no server located at my IP address of 209.216.230.75. No such machine exists. Instead, I run my scans from a nearby machine on the same network, and "spoof" that address with masscan:$ masscan 0.0.0.0/0 -p80 --banners --spoof-ip 209.216.230.75This sends a web request to every machine on the Internet from that IP address, despite no machine anywhere being configured with that IP address.I point this out because people are confused by the meaning of an "IP address", or a "server", "domain", and "domain name". I can imagine the FBI looking into this and getting a FISA warrant for the server located at my IP address, and my ISP coming back and telling them that no such server exists, nor has a server existed at that IP address for many years.In the case of last years story, there's little reason to believe IP spoofing was happening, but the conspiracy theory still breaks down for the same reason: the association between these concepts is not what you think it is. Listrak, the owner of the server at the center of the conspiracy, still reverse resolves the IP address 66.216.133.29 as "mail1.trump-email.com", either because they are lazy, or because they enjoy the lulz. It's absurd thinking anything sent by the server is related to the Trump Orgainzation today, and it's equally plausible that nothing the server sent was related to Trump last year as well, especially since (as CNN reports), Trump had severed their ties with Cendyn (the mar It's absurd thinking anything sent by the server is related to the Trump Orgainzation today, and it's equally plausible that nothing the server sent was related to Trump last year as well, especially since (as CNN reports), Trump had severed their ties with Cendyn (the mar |
||||
| 2017-03-15 13:39:32 | Assert() in the hands of bad coders (lien direct) | Using assert() creates better code, as programmers double-check assumptions. But only if used correctly. Unfortunately, bad programmers tend to use them badly, making code worse than if no asserts were used at all. They are a nuanced concept that most programmers don't really understand.We saw this recently with the crash of "Bitcoin Unlimited", a version of Bitcoin that allows more transactions. They used an assert() to check the validity of input, and when they received bad input, most of the nodes in the network crashed.The Bitcoin code is full of bad uses of assert. The following examples are all from the file main.cpp.Example #1: this line of code: if (nPos >= coins->vout.size() || coins->vout[nPos].IsNull()) assert(false); This use of assert is silly. The code should look like this: assert | Guideline | |||
| 2017-03-11 17:03:54 | Some confusing language in the 0day debate (lien direct) | As revealed in last week's CIA #Vault7 leaks, the CIA has some 0days. This has ignited the debate about whether organizations like the CIA should be disclosing these 0days so that vendors can fix them, rather than "stockpiling" them. There seems to be some confusion about language.StockpileThe word "stockpile" has multiple connotations, as shown below: This distorts the debate. Using the word "stockpile" strongly implies "reserve for use" at some time in the future. This prejudices the debate. If the the 0day is sitting on a shelf somewhere not being used, then it apparently has little value for offense, and thus, should be disclosed/patched for defense.The truth is that that government does not buy 0days to sit on the shelf. With few exceptions, it buys 0days because it plans to use them in an offensive operation. This was described in that recent RAND report: This distorts the debate. Using the word "stockpile" strongly implies "reserve for use" at some time in the future. This prejudices the debate. If the the 0day is sitting on a shelf somewhere not being used, then it apparently has little value for offense, and thus, should be disclosed/patched for defense.The truth is that that government does not buy 0days to sit on the shelf. With few exceptions, it buys 0days because it plans to use them in an offensive operation. This was described in that recent RAND report: It's the sellers who might keep 0days on the shelf, because the buyers have no immediate need. It's not the government buyers who are stockpiling.Words like "stockpiling", "amassing", or "hoarding" also bring the connotation that the number is too big. Words like "hoarding" bring the connotation that the government is doing something to keep the 0days away from others, preventing them from finding them, too.Neutral terms would be more accurate, such as "acquiring" 0days, or having a "collection" 0days.Find 0daysPeople keep describing the government as "finding" 0days. The word has two different meanings: It's the sellers who might keep 0days on the shelf, because the buyers have no immediate need. It's not the government buyers who are stockpiling.Words like "stockpiling", "amassing", or "hoarding" also bring the connotation that the number is too big. Words like "hoarding" bring the connotation that the government is doing something to keep the 0days away from others, preventing them from finding them, too.Neutral terms would be more accurate, such as "acquiring" 0days, or having a "collection" 0days.Find 0daysPeople keep describing the government as "finding" 0days. The word has two different meanings: We are talking about two different policies here, one where the government finds 0day by chance, and one where they obtain 0days by effort.Numerous articles quote Michael Daniel, former cyberczar under Obama, as claiming their default policy was to disclose 0days they find. What he meant was those found by chance. That doesn't apply to vulnerabilities researched/bought by the CIA/NSA. Obviously, if you've got a target (like described above), and you buy an 0day to attack that target, you are going to use it. You aren't going to immediately disclose it, thereby making it useless for the purpose for which you bought it.Michael Daniels is typical government speak: while their official policy was to disclose, their practice was to not disclose.Using the word "find" prejudices the conversation, like "stockpiling", making it look like the government has no particular interest in an 0day, and is just hoarding it out of spite. What the government actually does is "buy" 0days from outsiders, or "researches" 0days themselves. Either way, they put a lot of We are talking about two different policies here, one where the government finds 0day by chance, and one where they obtain 0days by effort.Numerous articles quote Michael Daniel, former cyberczar under Obama, as claiming their default policy was to disclose 0days they find. What he meant was those found by chance. That doesn't apply to vulnerabilities researched/bought by the CIA/NSA. Obviously, if you've got a target (like described above), and you buy an 0day to attack that target, you are going to use it. You aren't going to immediately disclose it, thereby making it useless for the purpose for which you bought it.Michael Daniels is typical government speak: while their official policy was to disclose, their practice was to not disclose.Using the word "find" prejudices the conversation, like "stockpiling", making it look like the government has no particular interest in an 0day, and is just hoarding it out of spite. What the government actually does is "buy" 0days from outsiders, or "researches" 0days themselves. Either way, they put a lot of |
||||
| 2017-03-09 19:30:33 | FBI: what to look for in the Trump/AlfaBank connection (lien direct) | As CNN reports, the FBI seems to be looking into that connection between Trump and Alfa Bank. Here are some things to look for.First, get your own copy of the logs from root name servers. I don't trust the source of the original logs. I suspect they've been edited in order to show a relationship with Alfa Bank. You've got lots of sources both inside government and in private industry that can provide a copy of these logs without a warrant. (Which sucks, you should need a warrant, but that's the current state of affairs).Second, look at the server in question. It's probably located at 140 Akron Road, Ephrata, PA. What you are looking for are the logs of anything sent from the server during that time, specifically any e-mails.Third, talk to Cendyn, and ask them what that server was used for during that time. Their current statement is that it was used by the Metron meeting software. In other words, they say that after they stopped using it to send marketing emails, they started using it for their meeting product. They seem a little confused, so it'd be nice to pin them down. Specifically, get logfiles indicating precisely what happened, and figure out how Metron works, what sorts of messages it will generate.Fourth, talk to Cendyn, and ask them about customers of their Metron meeting software, namely who used it to arrange meetings with Alfa Bank or the Trump organization. My guess is that this is where you'll really get the juicy information, getting a list of what meetings happened when and who was invited.Fifth, talk to Cendyn and get logfiles form their DNS servers to figure out who was resolving that domain name (mail1.trump-email.com) during that time period.Sixth, ask Alfa Bank for logfiles from their DNS resolvers that would tell you which machines internally were generating those requests.My guess is that all of this will come up empty. There's a coincidence here, but a small one. Much of the technical details have been overhyped and mean little. | ★★★★ | |||
| 2017-03-09 03:46:36 | Some notes on the RAND 0day report (lien direct) | The RAND Corporation has a research report on the 0day market [*]. It's pretty good. They've got the pricing about right ($1 million for full chain iPhone exploit, but closer to $100k for others). They've got the stats about right (5% chance somebody else will discover an exploit). Yet, they've got some problems, namely phrasing the debate as activists want, rather than a neutral view of the debate.The report frequently uses the word "stockpile". This is a biased term used by activists. According to the dictionary, it means:a large accumulated stock of goods or materials, especially one held in reserve for use at a time of shortage or other emergency.Activists paint the picture that the government (NSA, CIA, DoD, FBI) buys 0day to hold in reserve in case they later need them. If that's the case, then it seems reasonable that it's better to disclose/patch the vuln then let it grow moldy in a cyberwarehouse somewhere.But that's not how things work. The government buys vulns it has immediate use for (primarily). Almost all vulns it buys are used within 6 months. Most vulns in its "stockpile" have been used in the previous year. These cyberweapons are not in a warehouse, but in active use on the front lines.This is top secret, of course, so people assume it's not happening. They hear about no cyber operations (except Stuxnet), so they assume such operations aren't occurring. Thus, they build up the stockpiling assumption rather than the active use assumption.If the RAND wanted to create an even more useful survey, they should figure out how many thousands of times per day our government (NSA, CIA, DoD, FBI) exploits 0days. They should characterize who they target (e.g. terrorists, child pornographers), success rate, and how many people they've killed based on 0days. It's this data, not patching, that is at the root of the policy debate.That 0days are actively used determines pricing. If the government doesn't have immediate need for a vuln, it won't pay much for it, if anything at all. Conversely, if the government has urgent need for a vuln, it'll pay a lot.Let's say you have a remote vuln for Samsung TVs. You go to the NSA and offer it to them. They tell you they aren't interested, because they see no near term need for it. Then a year later, spies reveal ISIS has stolen a truckload of Samsung TVs, put them in all the meeting rooms, and hooked them to Internet for video conferencing. The NSA then comes back to you and offers $500k for the vuln.Likewise, the number of sellers affects the price. If you know they desperately need the Samsung TV 0day, but they are only offering $100k, then it likely means that there's another seller also offering such a vuln.That's why iPhone vulns are worth $1 million for a full chain exploit, from browser to persistence. They use it a lot, it's a major part of ongoing cyber operations. Each time Apple upgrades iOS, the change breaks part of the existing chain, and the government is keen on getting a new exploit to fix it. They'll pay a lot to the first vuln seller who can give them a new exploit.Thus, there are three prices the government is willing to pay for an 0day (the value it provides to the government):the price for an 0day they will actively use right now (high)the price for an 0day they'll stockpile for possible use in the future (low)the price for an 0day they'll disclose to the vendor to patch (very low)That these are different prices is important to the policy debate. When activists claim the government should disclose the 0day they acquire, they are ignoring the price the 0day was acquired for. Since the government actively uses the 0day, they are acquired for a high-price, with their "use" value far higher than their "patch" value. It\ | ||||
| 2017-03-08 19:22:03 | A note about "false flag" operations (lien direct) | There's nothing in the CIA #Vault7 leaks that calls into question strong attribution, like Russia being responsible for the DNC hacks. On the other hand, it does call into question weak attribution, like North Korea being responsible for the Sony hacks.There are really two types of attribution. Strong attribution is a preponderance of evidence that would convince an unbiased, skeptical expert. Weak attribution is flimsy evidence that confirms what people are predisposed to believe.The DNC hacks have strong evidence pointing to Russia. Not only does all the malware check out, but also other, harder to "false flag" bits, like active command-and-control servers. A serious operator could still false-flag this in theory, if only by bribing people in Russia, but nothing in the CIA dump hints at this.The Sony hacks have weak evidence pointing to North Korea. One of the items was the use of the RawDisk driver, used both in malware attributed to North Korea and the Sony attacks. This was described as "flimsy" at the time [*]. The CIA dump [*] demonstrates that indeed it's flimsy -- as apparently CIA malware also uses the RawDisk code.In the coming days, biased partisans are going to seize on the CIA leaks as proof of "false flag" operations, calling into question Russian hacks. No, this isn't valid. We experts in the industry criticized "malware techniques" as flimsy attribution, long before the Sony attack, and long before the DNC hacks. All the CIA leaks do is prove we were right. On the other hand, the DNC hack attribution is based on more than just this, so nothing in the CIA leaks calls into question that attribution. | ||||
| 2017-03-07 22:53:37 | Only lobbyist and politicians matter, not techies (lien direct) | The NSA/CIA will only buy an 0day if they can use it. They can't use it if they disclose the bug.I point this out, yet again, because of this WaPo article [*] built on the premise that the NSA/CIA spend millions of dollars on 0day they don't use, while unilaterally disarming tiself. Since that premise is false, the entire article is false. It's the sort of article you get when all you interview are Washington D.C. lobbyists and Washington D.C. politicians -- and no outside experts.It quotes former cyberczar (under Obama) Michael Daniel explaining that the "default assumption" is to disclose 0days that the NSA/CIA get. This is a Sean Spicer style lie. He's paid to say this, but it's not true. The NSA/CIA only buy 0day if they can use it. They won't buy 0day if the default assumption is that they will disclose it. QED: the default assumption of such 0day is they won't disclose them.The story quotes Ben Wizner of the ACLU saying that we should patch 0days instead of using them. Patching isn't an option. If we aren't using them, then we aren't buying them, and hence, there are no 0days to patch. The two options are to not buy 0days at all (and not patch) or buy to use them (and not patch). Either way, patching doesn't happen.Wizner didn't actually say "use them". He said "stockpiling" them, a word that means "hold in reserve for use in the future". That's not what the NSA/CIA does. They buy 0days to use, now. They've got budgets and efficiency ratings. They don't buy 0days which they can't use in the near future. In other words, Wizner paints the choice between an 0day that has no particular value to the government, and one would have value being patched.The opposite picture is true. Almost all the 0days possessed by the NSA/CIA have value, being actively used against our adversaries right now. Conversely, patching an 0day provides little value for defense. Nobody else knew about the 0day anyway (that's what 0day means), so nobody was in danger, so nobody was made safer by patching it.Wizner and Snowden are quoted in the article that somehow the NSA/CIA is "maintaining vulnerabilities" and "keeping the holes open". This phrasing is deliberately misleading. The NSA/CIA didn't create the holes. They aren't working to keep them open. If somebody else finds the same 0day hole and tells the vendor (like Apple), then the NSA/CIA will do nothing to stop them. They just won't work to close the holes.Activists like Wizner and Snowden deliberate mislead on the issue because they can't possibly win a rational debate. The government is not going to continue to spend millions of dollars on buying 0days just to close them, because everyone agrees the value proposition is crap, that the value of fixing yet another iPhone hole is not worth the $1 million it'll cost, and do little to stop Russians from finding an unrelated hole. Likewise, while the peacenicks (rightfully, in many respects) hate the militarization of cyberspace, they aren't going to win the argument that the NSA/CIA should unilaterally disarm themselves. So instead they've tried to morph the debate into some crazy argument that makes no sense.This is the problem with Washington D.C. journalism. It presumes the only people who matter are those in Washington, either the lobbyists of one position, or government defenders of another position. At no point did they go out and talk to technical experts, such as somebody who has discovered, weaponized, used an 0day exploit. So they write articles premised on the fact that the NSA/CIA, out of their offensive weapons budget, will continue to buy 0days that are immediately patched and fixed without ever being useful. | Guideline | ★★ | ||
| 2017-03-07 20:40:20 | Some comments on the Wikileaks CIA/#vault7 leak (lien direct) | I thought I'd write up some notes about the Wikileaks CIA "#vault7" leak. This post will be updated frequently over the next 24 hours.The CIA didn't remotely hack a TV. The docs are clear that they can update the software running on the TV using a USB drive. There's no evidence of them doing so remotely over the Internet. If you aren't afraid of the CIA breaking in an installing a listening device, then you should't be afraid of the CIA installing listening software.The CIA didn't defeat Signal/WhattsApp encryption. The CIA has some exploits for Android/iPhone. If they can get on your phone, then of course they can record audio and screenshots. Technically, this bypasses/defeats encryption -- but such phrases used by Wikileaks arehighly misleading, since nothing related to Signal/WhatsApp is happening. What's happening is the CIA is bypassing/defeating the phone. Sometimes. If they've got an exploit for it, or can trick you into installing their software.There's no overlap or turf war with the NSA. The NSA does "signals intelligence", so they hack radios and remotely across the Internet. The CIA does "humans intelligence", so they hack locally, with a human. The sort of thing they do is bribe, blackmail, or bedazzle some human "asset" (like a technician in a nuclear plant) to stick a USB drive into a slot. All the various military, law enforcement, and intelligence agencies have hacking groups to help them do their own missions.The CIA isn't more advanced than the NSA. Most of this dump is child's play, simply malware/trojans cobbled together from bits found on the Internet. Sometimes they buy more advanced stuff from contractors, or get stuff shared from the NSA. Technologically, they are far behind the NSA in sophistication and technical expertise.The CIA isn't hoarding 0days. For one thing, few 0days were mentioned at all. The CIA's techniques rely upon straightforward hacking, not super secret 0day hacking Second of all, they aren't keeping 0days back in a vault somewhere -- if they have 0days, they are using them.The VEP process is nonsense. Activists keep mentioning the "vulnerability equities process", in which all those interested in 0days within the government has a say in what happens to them, with the eventual goal that they be disclosed to vendors. The VEP is nonsense. The activist argument is nonsense. As far as I can tell, the VEP is designed as busy work to keep people away from those who really use 0days, such as the NSA and the CIA. If they spend millions of dollars buying 0days because it has that value in intelligence operations, they aren't going to destroy that value by disclosing to a vendor. If VEP forces disclosure, disclosure still won't happen, the NSA will simply stop buying vulns.There's no false flags. In several places, the CIA talks about making sure that what they do isn't so unique, so it can't be attributed to them. However, Wikileaks's press release hints that the "UMBRAGE" program is deliberately stealing techniques from Russia to use as a false-flag operation. This is nonsense. For example, the DNC hack attribution was live command-and-control servers simultaneously used against different Russian targets -- not a few snippets of code.This hurts the CIA a lot. Already, one AV researcher has told me that a virus they once suspected came from the Russians or Chinese can now be attributed to the CIA, as it matches the description perfectly to something in the leak. We can develop anti-virus and intrusion-detection signatures based on this information that will defeat much of what we read in these documents. This would put a multi-year delay in the CIA's development efforts. Plus, it'll now go on a witch-hunt looking for the leaker, which will erode morale. Update: Three extremely smart and knowledgeable people who I respect disagree, claiming | Guideline | |||
| 2017-03-06 06:50:36 | Journalists: How hacking details matter (lien direct) | When I write my definitive guide for journalists covering hacking, I'm going to point out how easy it is for journalists to misunderstand the details of a story -- especially when they change the details to fit the story they want to tell.For example, there is the notorious "CIA hacked Senate computers" scandal. In fact, the computers in question were owned by the CIA, located in a CIA facility, and managed/operated by CIA employees. You can't "hack" computers you own. Yes, the CIA overstepped the bounds of an informal agreement with the Senate committee overseeing them, but in no way did anything remotely like "hacking" occur.This detail matter. If the CIA had truly hacked the Senate committee, that would be a constitutional crisis. A small misstep breaking an informal agreement is not.A more recent example is this story, which mentions that AlfaBank-Trump connection, claiming the server was in Trump Tower [*]:What about the computer server at Trump Tower?Several news media outlets have reported that investigators last year were puzzled by data transmissions between a computer server at Trump Tower and a computer server associated with a Russian bank. Although Mr. Trump on Twitter talked about his “phones,†in theory a judge might determine that the computer address of the server in the tower was a facility being used by a foreign power, Russia, to communicate, and authorize surveillance of it.No, the server was not located in Trump Tower. It was located outside Philadelphia. It's owned and operated by a company called Listrak. There's no evidence anybody in the Trump Organization even knew about the server. It was some other company named Cendyn who decided to associate Trump's name with the server. There's no evidence of communication between the server and Alfa -- only evidence of communication about the server from Alfa.The details are important to the story, because it's trying to show how a judge "might determine that the computer ... in the tower was a facility being used by a foreign power". If it's not anywhere near or related to the Trump Tower, no such determination could be made.Then there was that disastrous story from the Washington Post about Russia hacking into a Vermont power plant [*], which still hasn't been retracted despite widespread condemnation. No such hacking occurred. Instead, the details of what happened is that an employee checked Yahoo mail from his laptop. The night before, the DHS had incorrectly configured its "Einstein" intrusion detection system to trigger on innocent traffic with Yahoo as an indicator of compromise from Russian hackers.You can see how journalists make these mistakes. If CIA is spying on computers used by Senate staffers, then the natural assumption is that the CIA hacked those computers. If there was a server associated with the Trump Organization, however tenuous, it's easy to assume a more concrete relationship, such as the server being located in Trump's offices. You can see how once the DHS claims there was a hack, and you've filled your stories with quotes from senators pontificating about the meaning of such hacks, it's very difficult to retract the story when the details emerge there was nothing remotely resembling a hack.I'm not trying to claim that journalists need to be smarter about hacking. I'm instead claiming that journalists need to be smarter about journalism. The flaws here all go one way -- toward the sensational. Instead of paying attention to the details and questioning whether such sensational | Yahoo | |||
| 2017-02-28 05:24:59 | Some moon math (lien direct) | So "Brianna Wu" (famous for gamergate) is trending, and because I love punishment, I clicked on it to see why. Apparently she tweeted that Elon Musk's plan to go to the moon is bad, because once there he can drop rocks on the Earth with the power of 100s of nuclear bombs. People are mocking her for the stupidity of this.But the math checks out.First of all, she probably got the idea from Heinlein's book The Moon is a Harsh Mistress where the rebel moon colonists do just that. I doubt she did her own math, and relied upon Heinlein to do it for her. But let's do the math ourselves.Let's say that we want to stand at the height of the moon and drop a rock. How big a rock do we need to equal the energy of an atomic bomb. To make things simple, let's assume the size of bombs we want is that of the one dropped on Hiroshima.As we know from high school physics, the energy of a dropped object (ignoring air) is:energy = mass * gravity * heightSolving for mass, the equation is:mass = energy/(gravity * height)So our equation is:mass of rock = (energy of Hiroshima bomb) / (Earth gravity) * (height of moon))Luckily, these day we have Wolfram Alfa where we can type that in as an equation [*]: So the answer is 1.8 billion grams, or 1.8 million kilograms, or 1.8 thousand metric tons.Well, that's a fine number and all, but what does that equal? Is that the size of Rhode Island? or just a big truck?The answer is: about the same mass as the Space Shuttle during launch (2.03 million kilograms [*]).That's big rock, but not so big that it's impractical, especially since things weigh 1/6th as on Earth. In Heinlein's books, instead of shooting rocks via rockets, it shot them into space using a railgun, magnetic rings. Since the moon doesn't have an atmosphere, you don't need to shoot things straight up. Instead, you can accelerate them horizontally across the moon's surface, to an escape velocity of 5,000 mph. As the moon's surface curves away, they'll head out into space (or toward Earth)Thus, Elon Musk would need to:go the moonsetup a colony, undergroundmine orebuild a magnetic launch gunbuild fields full of solar panels for energymine some rockcover it in iron (for magnet gun to hold onto)bomb earthAt that point, he could drop hundreds of "nukes" on top of us. I, for one, would welcome our Lunar overlords. Free Luna! So the answer is 1.8 billion grams, or 1.8 million kilograms, or 1.8 thousand metric tons.Well, that's a fine number and all, but what does that equal? Is that the size of Rhode Island? or just a big truck?The answer is: about the same mass as the Space Shuttle during launch (2.03 million kilograms [*]).That's big rock, but not so big that it's impractical, especially since things weigh 1/6th as on Earth. In Heinlein's books, instead of shooting rocks via rockets, it shot them into space using a railgun, magnetic rings. Since the moon doesn't have an atmosphere, you don't need to shoot things straight up. Instead, you can accelerate them horizontally across the moon's surface, to an escape velocity of 5,000 mph. As the moon's surface curves away, they'll head out into space (or toward Earth)Thus, Elon Musk would need to:go the moonsetup a colony, undergroundmine orebuild a magnetic launch gunbuild fields full of solar panels for energymine some rockcover it in iron (for magnet gun to hold onto)bomb earthAt that point, he could drop hundreds of "nukes" on top of us. I, for one, would welcome our Lunar overlords. Free Luna!Update: I've made a number of short cuts, but I don't think they'll affect the math much. For example, Earth's gravity, at the height of the moon, is 9 m/s2, whereas at the Earth's surface, it's 9.8 m/s2. It's a small enough different that I can ignore it for back-of-the-napkin calculations.Also, we don't need escape velocity for the moon as a whole, just enough to reach the point where Earth's gravity takes over. On the other hand, we need to kill the speed of the Moons's orbit (2,000 miles per hour) in order to get down to Earth, or we just end up orbiting the Earth. I just assume the two roughly cancel |
||||
| 2017-02-24 17:29:00 | A quick note about iconoclasm (lien direct) |  I'm an iconoclast [*]. Whenever things become holy, whereby any disagreement is treated as heresy, then I disagree. There are two reasonable sides to every argument. When you vilify one of the sides in the argument, then I step into defend them -- not that they are right, but that they are reasonable.This makes many upset, because once a cause has become Holy, anybody disagreeing with orthodoxy (like me) is then, by definition, a horrible person. I get things like the image to the right.(Please don't harass/contact this person -- she believes what many do, and singling her out would be mean).For the record, I'm rabidly feminist, anti-racist, pro-LGBT, pro-civil-rights. It's just that while I care a lot, I'm not Orthodox. I likely disagree with you about the details. When you vilify those who disagree with you, I will defend them....which is the best troll, ever. Admitting somebody is wrong, but defending them as reasonable, seems to upset people more than just arguing the other side is right. I'm an iconoclast [*]. Whenever things become holy, whereby any disagreement is treated as heresy, then I disagree. There are two reasonable sides to every argument. When you vilify one of the sides in the argument, then I step into defend them -- not that they are right, but that they are reasonable.This makes many upset, because once a cause has become Holy, anybody disagreeing with orthodoxy (like me) is then, by definition, a horrible person. I get things like the image to the right.(Please don't harass/contact this person -- she believes what many do, and singling her out would be mean).For the record, I'm rabidly feminist, anti-racist, pro-LGBT, pro-civil-rights. It's just that while I care a lot, I'm not Orthodox. I likely disagree with you about the details. When you vilify those who disagree with you, I will defend them....which is the best troll, ever. Admitting somebody is wrong, but defending them as reasonable, seems to upset people more than just arguing the other side is right. |
||||
| 2017-02-21 21:21:13 | Border Digital Safety for Journalists (lien direct) | The CPJ, the "Committee to Protect Journalists", offers some horrible advice [*] on Digital Security, especially when crossing the border.The most important piece of advice I can give you is this: if somebody's life depends upon it, then no simple piece of advice, no infographic, is going to help you. You have to learn about cybersecurity enough to make intelligent decisions for yourself. You have to make difficult tradeoffs yourself. Anybody giving you simple advice or infographics is a charlatan.So I thought I'd discuss what's wrong with the following infographic: I. Passwords, managers, and two-factorThe biggest issue is don't reuse passwords across different accounts. If you do, when hackers breach one of your accounts, they breach all of them. I use a simple password for all the accounts I don't care about, then complex unique passwords for all my important accounts. I have to write them down on a piece of paper I've got hidden at home, because sometimes I forget them.Password managers certainly help you have multiple strong passwords across many accounts. On the other hand, it puts all your eggs in one basket, and the police can grab them from the company.Two-fact can help, but hackers have shown they can intercept SMS messages to your phone number.One problem you have to deal with is that going through border control, they'll ask for all your social media passwords. If you are using two-factor authentication (SMS to a phone) then it won't do them much good having the passwords. Not having your phone with you while your cross the border isn't hard. You can use a separate Google Voice phone number (free) which you disconnect form your phone before traveling across the border, and reconnect when you get back home. You can also use a cheap $3/month account (like one of the M2M/IoT SIMs) on a second phone.II. Encrypt laptop and screen lockBorder control, law enforcement, and smart criminals can bypass the "screen lock". This is practically true for MacBooks (with their Thunderbolt ports), they've got the tools to do this with ease. This is theoretically true for Windows, though without Thunderbolt or Firewire, I don't know how to easily break out the screen lock on most of them.The upshot is that before going through border security, power off your laptop completely.Encrypting your laptop is excellent advice, but you are still likely to fail at this. In all likelihood, you are going to choose a weak password that can be "brute-forced" (guessed) by the police. Or, you are going to setup a "password recovery" feature where the police can get your password by subpoenaing Apple or Microsoft. Describing how to do this well requires multiple pages of text.III. Use Signal or WhatsAppUsing Signal is good. However, they still get the metadata who you are talking to. Also, using Signal in a foreign country makes you stand out, because only people with something to hide from the police use Signal. Using WhatsApp is better, because lots of people use WhatsApp for normal day-to-day chat. These are the sorts of subtle issues you have to think through.IV. Secure BrowserOn the phone, use Brave. It's like having Chrome with HTTPS-Anywhere and uBlock origin built in, getting rid of privacy tracking cookies and ads. Indeed, one of the engineers of HTTPS-Anywhere is one of the principle enginee I. Passwords, managers, and two-factorThe biggest issue is don't reuse passwords across different accounts. If you do, when hackers breach one of your accounts, they breach all of them. I use a simple password for all the accounts I don't care about, then complex unique passwords for all my important accounts. I have to write them down on a piece of paper I've got hidden at home, because sometimes I forget them.Password managers certainly help you have multiple strong passwords across many accounts. On the other hand, it puts all your eggs in one basket, and the police can grab them from the company.Two-fact can help, but hackers have shown they can intercept SMS messages to your phone number.One problem you have to deal with is that going through border control, they'll ask for all your social media passwords. If you are using two-factor authentication (SMS to a phone) then it won't do them much good having the passwords. Not having your phone with you while your cross the border isn't hard. You can use a separate Google Voice phone number (free) which you disconnect form your phone before traveling across the border, and reconnect when you get back home. You can also use a cheap $3/month account (like one of the M2M/IoT SIMs) on a second phone.II. Encrypt laptop and screen lockBorder control, law enforcement, and smart criminals can bypass the "screen lock". This is practically true for MacBooks (with their Thunderbolt ports), they've got the tools to do this with ease. This is theoretically true for Windows, though without Thunderbolt or Firewire, I don't know how to easily break out the screen lock on most of them.The upshot is that before going through border security, power off your laptop completely.Encrypting your laptop is excellent advice, but you are still likely to fail at this. In all likelihood, you are going to choose a weak password that can be "brute-forced" (guessed) by the police. Or, you are going to setup a "password recovery" feature where the police can get your password by subpoenaing Apple or Microsoft. Describing how to do this well requires multiple pages of text.III. Use Signal or WhatsAppUsing Signal is good. However, they still get the metadata who you are talking to. Also, using Signal in a foreign country makes you stand out, because only people with something to hide from the police use Signal. Using WhatsApp is better, because lots of people use WhatsApp for normal day-to-day chat. These are the sorts of subtle issues you have to think through.IV. Secure BrowserOn the phone, use Brave. It's like having Chrome with HTTPS-Anywhere and uBlock origin built in, getting rid of privacy tracking cookies and ads. Indeed, one of the engineers of HTTPS-Anywhere is one of the principle enginee |
||||
| 2017-02-20 21:20:33 | Skillz: editing a web page (lien direct) | So one of the skillz you ought to have in cybersec is messing with web-pages client-side using Chrome's Developer Tools. Web-servers give you a bunch of HTML and JavaScript code which, once it reaches your browser, is yours to change and play with. You can do a lot with web-sites that they don't intend by changing that code.Let me give you an example. It's only an example -- touching briefly on steps to give you an impression what's going on. It's not a ground up explanation of everything, which you may find off-putting. Click on the images to expand them so you can see fully what's going on.Today is the American holiday called "Presidents Day". It's actually not a federal holiday, but a holiday in all 50 states. Originally it was just Washington's birthday (February 22), but some states choose to honor other presidents as well, hence "Presidents Day".Thus of us who donated to Donald Trump's campaign (note: I donated to all candidates campaigns back in 2015) received an email today suggesting that to honor Presidents Day, we should "sign a card" for Trump. It's a gross dis-honoring of the Presidents the day is supposed to commemorate, but whatever, it's the 21st century.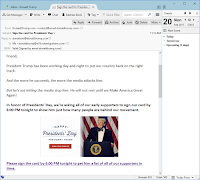 Okay, let's say we want to honor the current President with a bunch of 🖕🖕🖕🖕 in order to point out his crassness of exploiting this holiday, and clicked on the URL [*], and filled it in as such (with multiple skin tones for the middle finger, just so he knows its from all of us): Okay, let's say we want to honor the current President with a bunch of 🖕🖕🖕🖕 in order to point out his crassness of exploiting this holiday, and clicked on the URL [*], and filled it in as such (with multiple skin tones for the middle finger, just so he knows its from all of us):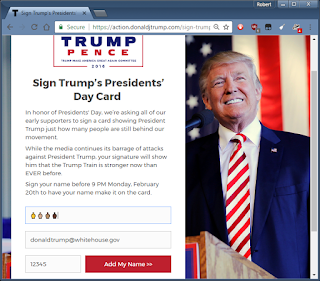 Okay, now we hit the submit button "Add My Name" in order to send this to his campaign. The only problem is, the web page rejects us, telling us "Please enter a valid name" (note, I'm changing font sizes in these screen shots so you can see the message): Okay, now we hit the submit button "Add My Name" in order to send this to his campaign. The only problem is, the web page rejects us, telling us "Please enter a valid name" (note, I'm changing font sizes in these screen shots so you can see the message):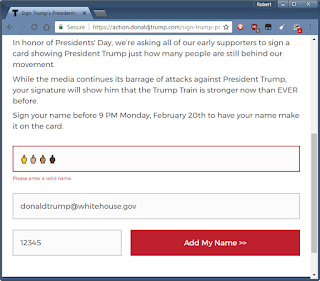 This is obviously client side validation of the field. It's at this point that we go into Developer Tools in order to turn it off. One way is to [right-click] on that button, and from the popup menu, select "Inspect", which gets you this screen (yes, the original page is squashed to the left-hand side): This is obviously client side validation of the field. It's at this point that we go into Developer Tools in order to turn it off. One way is to [right-click] on that button, and from the popup menu, select "Inspect", which gets you this screen (yes, the original page is squashed to the left-hand side): |
||||
| 2017-02-18 22:30:56 | You don\'t need printer security (lien direct) | So there's this tweet:The guy at the HP printer security booth seriously told a customer that he needs print security "because stuxnet exploits the print spooler" pic.twitter.com/WRyfEGj9hR- Jake Williams (@MalwareJake) February 15, 2017What it's probably refering to is this: This is an obviously bad idea.Well, not so "obvious", so some people have ask me to clarify the situation. After all, without "security", couldn't a printer just be added to a botnet of IoT devices?The answer is this:Fixing insecurity is almost always better than adding a layer of security.Adding security is notoriously problematic, for three reasonsHackers are active attackers. When presented with a barrier in front of an insecurity, they'll often find ways around that barrier. It's a common problem with "web application firewalls", for example.The security software itself can become a source of vulnerabilities hackers can attack, which has happened frequently in anti-virus and intrusion prevention systems.Security features are usually snake-oil, sounding great on paper, with with no details, and no independent evaluation, provided to the public.It's the last one that's most important. HP markets features, but there's no guarantee they work. In particular, similar features in other products have proven not to work in the past.HP describes its three special features in a brief whitepaper [*]. They aren't bad, but at the same time, they aren't particularly good. Windows already offers all these features. Indeed, as far as I know, they are just using Windows as their firmware operating system, and are just slapping an "HP" marketing name onto existing Windows functionality.HP Sure Start: This refers to the standard feature in almost all devices these days of having a secure boot process. Windows supports this in UEFI boot. Apple's iPhones work this way, which is why the FBI needed Apple's help to break into a captured terrorist's phone. It's a feature built into most IoT hardware, though most don't enable it in software.Whitelisting: Their description sounds like "signed firmware updates", but if that was they case, they'd call it that. Traditionally, "whitelisting" referred to a different feature, containing a list of hashes for programs that can run on the device. Either way, it's a pretty common functionality.Run-time intrusion detection: They have numerous, conflicting descriptions on their website. It may mean scanning memory for signatures of known viruses. It may mean stack cookies. It may mean double-checking kernel modules. Windows does all these things, and it has a tiny benefit on stopping security threats.As for traditional threats for attacks against printers, none of these really are important. What you need to secure a printer is the ability to disable services you aren't using (close ports), enable passwords and other access control, and delete files of old print jobs so hackers can't grab them from the printer. HP has features to address these security problems, This is an obviously bad idea.Well, not so "obvious", so some people have ask me to clarify the situation. After all, without "security", couldn't a printer just be added to a botnet of IoT devices?The answer is this:Fixing insecurity is almost always better than adding a layer of security.Adding security is notoriously problematic, for three reasonsHackers are active attackers. When presented with a barrier in front of an insecurity, they'll often find ways around that barrier. It's a common problem with "web application firewalls", for example.The security software itself can become a source of vulnerabilities hackers can attack, which has happened frequently in anti-virus and intrusion prevention systems.Security features are usually snake-oil, sounding great on paper, with with no details, and no independent evaluation, provided to the public.It's the last one that's most important. HP markets features, but there's no guarantee they work. In particular, similar features in other products have proven not to work in the past.HP describes its three special features in a brief whitepaper [*]. They aren't bad, but at the same time, they aren't particularly good. Windows already offers all these features. Indeed, as far as I know, they are just using Windows as their firmware operating system, and are just slapping an "HP" marketing name onto existing Windows functionality.HP Sure Start: This refers to the standard feature in almost all devices these days of having a secure boot process. Windows supports this in UEFI boot. Apple's iPhones work this way, which is why the FBI needed Apple's help to break into a captured terrorist's phone. It's a feature built into most IoT hardware, though most don't enable it in software.Whitelisting: Their description sounds like "signed firmware updates", but if that was they case, they'd call it that. Traditionally, "whitelisting" referred to a different feature, containing a list of hashes for programs that can run on the device. Either way, it's a pretty common functionality.Run-time intrusion detection: They have numerous, conflicting descriptions on their website. It may mean scanning memory for signatures of known viruses. It may mean stack cookies. It may mean double-checking kernel modules. Windows does all these things, and it has a tiny benefit on stopping security threats.As for traditional threats for attacks against printers, none of these really are important. What you need to secure a printer is the ability to disable services you aren't using (close ports), enable passwords and other access control, and delete files of old print jobs so hackers can't grab them from the printer. HP has features to address these security problems, |
||||
| 2017-02-01 15:56:16 | 1984 is the new Bible in the age of Trump (lien direct) | In the age of Trump, Orwell's book 1984 is becoming the new Bible: a religious text which few read, but which many claim supports their beliefs. A good demonstration is this CNN op-ed, in which the author describes Trump as being Orwellian, but mostly just because Trump is a Republican.Trump's populist attacks against our (classically) liberal world order is indeed cause for concern. His assault on the truth is indeed a bit Orwellian. But it's op-eds like this one at CNN that are part of the problem.While the author of the op-ed spends much time talking about his dogs ("Winston", "Julia"), and how much he hates Trump, he spends little time on the core thesis "Orwellianism". When he does, it's mostly about old political disagreements. For example, the op-ed calls Trump's cabinet appointees Orwellian simply because they are Republicans:He has provided us with Betsy DeVos, a secretary of education nominee who is widely believed to oppose public education, and who promotes the truly Orwellian-sounding concept of "school choice," a plan that seems well-intentioned but which critics complain actually siphons much-needed funds from public to private education institutions.Calling school-choice "Orwellian" is absurd. Republicans want to privatize more, and the Democrats want the state to run more of the economy. It's the same disagreement that divides the two parties on almost any policy issue. When you call every little political disagreement "Orwellian" then you devalue the idea. I'm Republican, so of course I'd argue that the it's the state-run education system giving parents zero choice that is the thing that's Orwellian here. And now we bicker, both convinced that Orwell is on our side in this debate. #WhatWouldOrwellDoIf something is "Orwellian", then you need to do a better job demonstrating this, making the analogy clear. For example, last year I showed how in response to a political disagreement, that Wikipedia and old newspaper articles were edited in order to conform to the new political reality. This is a clear example of Winston Smith's job of changing the past in order to match the present.But even such clear documentation is probably powerless to change anybody's mind. Whether "changing the text of old newspaper articles to fit modern politics" is Orwellian depends entirely on your politics, whether the changes agree with your views. Go follow the link [*] and see for yourself and see if you agree with the change (replacing the word "refugee" in old articles with "asylee" instead).It's this that Orwell was describing. Doublethink wasn't something forced onto us by a totalitarian government so much as something we willingly adopted ourselves. The target of Orwell's criticism wasn't them, the totalitarian government, but us, the people who willingly went along with it. Doublethink is what people in both parties (Democrats and Republicans) do equally, regardless of the who resides in the White House.Trump is an alt-Putin. He certainly wants to become a totalitarian. But at this point, his lies are juvenile and transparent, which even his supporters find difficult believing [*]. The most Orwellian thing about him is what he inherits from Obama [*]: the two Party system, perpetual war, omnipresent surveillance, the propaganda system, and our nascent cyber-police-state [*]. | ||||
| 2017-01-30 01:08:47 | Uber was right to disable surge pricing at JFK (lien direct) | Yesterday, the NYC taxi union had a one-hour strike protesting Trump's "Muslim Ban", refusing to pick up passengers at the JFK airport. Uber responded by disabling surge pricing at the airport. This has widely been interpreted as a bad thing, so the hashtag "#DeleteUber" has been trending, encouraging people to delete their Uber accounts/app.These people are wrong, obviously so.Surge PricingUber's "Surge Pricing" isn't price gouging, as many assume. Instead, the additional money goes directly to the drivers, to encourage them come to the area surging and pick up riders. Uber isn't a taxi company. It can't direct drivers to go anywhere. All it can do is provide incentives. "Surge Pricing" for customers means "Surge Income" for the drivers, giving them an incentive. Drivers have a map showing which areas of the city are surging, so they can drive there.Another way of thinking about it is "Demand Pricing". It's simply the economic Law of Supply and Demand. If demand increases, then prices increase, and then supply increases chasing the higher profits. It's why famously you can't get a taxi cab on New Years Eve, but you can get an Uber driver. Taxi drivers can't charge more when demand is surging, so there's no more taxis available on that date than on any other. But Uber drivers can/do charge more, so there's more Uber drivers.Supply and Demand is every much a law as Gravity. If the supply of taxi drivers is less than the demand, then not everyone is going to get a ride. That's basic math. If there's only 20 drivers right now, and 100 people wanting a ride, then 80 riders are going to be disappointed. The only solution is more drivers. Paying drivers more money gets more drivers. The part time drivers, the drivers planning on partying instead of working, will decide to work New Years chasing the surge wages.Uber's announcementUber made the following announcement:Surge pricing has been turned off at #JFK Airport. This may result in longer wait times. Please be patient.- Uber NYC (@Uber_NYC) January 29, 2017Without turning off Surge Pricing, Uber's computers would notice the spike in demand, as would-be taxi customers switch to Uber. The computers would then institute surge pricing around JFK automatically. This would notify the drivers in the area, who would then flock to JFK, chasing the higher income. This would be bad for the strike.By turning off surge pricing, there would be no increase in supply. It would mean the only drivers going to JFK are those dropping off passengers. It would mean that Uber wouldn't be servicing any more riders than on a normal day, making no difference to the taxi strike, one way or the other.Why wouldn't Uber stop pickups at JFK altogether, joining the strike? Because it'd be a tough decision for them. They have a different relationship with their drivers. Both taxis and Uber are required to take passengers to the airport if asked, but taxis are much better at weaseling out of it [*]. That means screwing drivers, forcing them to go way out to JFK with no return fare. In contrast, taxis were warned enough ahead of time to avoid the trip.The timingThe above section assumes a carefully considered Uber policy. In reality, they didn't have the time.The taxi union didn't announce their decision until 5pm, with the strike set for only one hour, between 6pm and 7pm.BREAKING: NYTWA dr | Uber | |||
| 2017-01-27 00:40:02 | Is \'aqenbpuu\' a bad password? (lien direct) | Press secretary Sean Spicer has twice tweeted a random string, leading people to suspect he's accidentally tweeted his Twitter password. One of these was 'aqenbpuu', which some have described as a "shitty password". Is is actually bad?No. It's adequate. Not the best, perhaps, but not "shitty".It depends upon your threat model. The common threats are password reuse and phishing, where the strength doesn't matter. When the strength does matter is when Twitter gets hacked and the password hashes stolen.Twitter uses the bcrypt password hashing technique, which is designed to be slow. A typical desktop with a GPU can only crack bcrypt passwords at a rate of around 321 hashes-per-second. Doing the math (26 to the power of 8, divided by 321, divided by one day) it will take 20 years for this desktop to crack the password.That's not a good password. A botnet with thousands of desktops, or a somebody willing to invest thousands of dollars on a supercomputer or cluster like Amazon's, can crack that password in a few days.But, it's not a bad password, either. A hack of a Twitter account like this would be a minor event. It's not worth somebody spending that much resources hacking. Security is a tradeoff -- you protect a ton of gold with Ft. Knox like protections, but you wouldn't invest the same amount protecting a ton of wood. The same is true with passwords -- as long as you don't reuse your passwords, or fall victim to phishing, eight lower case characters is adequate.This is especially true if using two-factor authentication, in which case, such a password is more than adequate.I point this out because the Trump administration is bad, and Sean Spicer is a liar. Our criticism needs to be limited to things we can support, such as the DC metro ridership numbers (which Spicer has still not corrected). Every time we weakly criticize the administration on things we cannot support, like "shitty passwords", we lessen our credibility. We look more like people who will hate the administration no matter what they do, rather than people who are standing up for principles like "honesty". The numbers above aren't approximations. I actually generated a bcrypt hash and attempted to crack it in order to benchmark how long this would take. I'll describe the process here.First of all, I installed the "PHP command-line". While older versions of PHP used MD5 for hashing, the newer versions use Bcrypt.# apt-get install php5-cliI then created a PHP program that will hash the password: 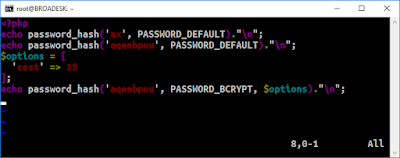 I actually use it three ways. The first way is to hash a small password "ax", one short enough that the password cracker will actually succeed in hashing. The second is to hash the password with PHP defaults, which is what I assume Twitter is using. The third is to increase the difficulty level, in case Twitter has increased the default difficulty level at all in order to protect weak passwords.I then ran the PHP script, producing these hashes:$ php spicer.php$2y$10$1BfTonhKWDN23cGWKpX3YuBSj5Us3eeLzeUsfylemU0PK4JFr4moa I actually use it three ways. The first way is to hash a small password "ax", one short enough that the password cracker will actually succeed in hashing. The second is to hash the password with PHP defaults, which is what I assume Twitter is using. The third is to increase the difficulty level, in case Twitter has increased the default difficulty level at all in order to protect weak passwords.I then ran the PHP script, producing these hashes:$ php spicer.php$2y$10$1BfTonhKWDN23cGWKpX3YuBSj5Us3eeLzeUsfylemU0PK4JFr4moa |
Guideline | |||
| 2017-01-21 18:12:43 | The command-line, for cybersec (lien direct) | On Twitter I made the mistake of asking people about command-line basics for cybersec professionals. A got a lot of useful responses, which I summarize in this long (5k words) post. It's mostly driven by the tools I use, with a bit of input from the tweets I got in response to my query.bashBy command-line this document really means bash.There are many types of command-line shells. Windows has two, 'cmd.exe' and 'PowerShell'. Unix started with the Bourne shell 'sh', and there have been many variations of this over the years, 'csh', 'ksh', 'zsh', 'tcsh', etc. When GNU rewrote Unix user-mode software independently, they called their shell “Bourne Again Shell†or “bash†(queue "JSON Bourne" shell jokes here).Bash is the default shell for Linux and macOS. It's also available on Windows, as part of their special “Windows Subsystem for Linuxâ€. The windows version of 'bash' has become my most used shell.For Linux IoT devices, BusyBox is the most popular shell. It's easy to clear, as it includes feature-reduced versions of popular commands.man'Man' is the command you should not run if you want help for a command.Man pages are designed to drive away newbies. They are only useful if you already mostly an expert with the command you desire help on. Man pages list all possible features of a program, but do not highlight examples of the most common features, or the most common way to use the commands.Take 'sed' as an example. It's used most commonly to do a search-and-replace in files, like so:$ sed 's/rob/dave/' foo.txtThis usage is so common that many non-geeks know of it. Yet, if you type 'man sed' to figure out how to do a search and replace, you'll get nearly incomprehensible gibberish, and no example of this most common usage.I point this out because most guides on using the shell recommend 'man' pages to get help. This is wrong, it'll just endlessly frustrate you. Instead, google the commands you need help on, or better yet, search StackExchange for answers.You might try asking questions, like on Twitter or forum sites, but this requires a strategy. If you ask a basic question, self-important dickholes will respond by telling you to “rtfm†or “read the fucking manualâ€. A better strategy is to exploit their dickhole nature, such as saying “too bad command xxx cannot do yyyâ€. Helpful people will gladly explain why you are wrong, carefully explaining how xxx does yyy.If you must use 'man', use the 'apropos' command to find the right man page. Sometimes multiple things in the system have the same or similar names, leading you to the wrong page.apt-get install yumUsing the command-line means accessing that huge open-source ecosystem. Most of the things in this guide do no already exist on the system. You have to either compile them from source, or install via a package-manager. Linux distros ship with a small footprint, but have a massive database of precompiled software “packages†in the cloud somewhere. Use the "package manager" to install the software from the cloud.On Debian-derived systems (like Ubuntu, Kali, Raspbian), type “apt-get install masscan†to install “masscan†(as an example). Use “apt-cache search scan†to find a bunch of scanners you might want to install.On RedHat systems, use “yum†instead. On BSD, use the “ports†system, which you can also get working for macOS.If no pre-compiled package exists for a program, then you'll have to download the source code and compile it. There's about an 80% chance this will work easy, following the instructions. There is a 20% | Guideline | |||
| 2017-01-13 00:21:53 | About that Giuliani website... (lien direct) | Rumors are that Trump is making Rudy Giuliani some sort of "cyberczar" in the new administration. Therefore, many in the cybersecurity scanned his website "www.giulianisecurity.com" to see if it was actually secure from hackers. The results have been laughable, with out-of-date software, bad encryption, unnecessary services, and so on.But here's the deal: it's not his website. He just contracted with some generic web designer to put up a simple page with just some basic content. It's there only because people expect if you have a business, you also have a website.That website designer in turn contracted some basic VPS hosting service from Verio. It's a service Verio exited around March of 2016, judging by the archived page.The Verio service promised "security-hardened server software" that they "continually update and patch". According to the security scans, this is a lie, as the software is all woefully out-of-date. According OS fingerprint, the FreeBSD image it uses is 10 years old. The security is exactly what you'd expect from a legacy hosting company that's shut down some old business.You can probably break into Giuliani's server. I know this because other FreeBSD servers in the same data center have already been broken into, tagged by hackers, or are now serving viruses.But that doesn't matter. There's nothing on Giuliani's server worth hacking. The drama over his security, while an amazing joke, is actually meaningless. All this tells us is that Verio/NTT.net is a crappy hosting provider, not that Giuliani has done anything wrong. 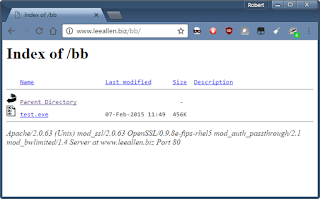  |
||||
| 2017-01-10 00:22:49 | NAT is a firewall (lien direct) | NAT is a firewall. It's the most common firewall. It's the best firewall.I thought I'd point this out because most security experts might disagree, pointing to some "textbook definition". This is wrong.A "firewall" is anything that establishes a barrier between some internal (presumably trusted) network and the outside, public, and dangerous Internet where anybody can connect to you at any time. A NAT creates exactly that sort of barrier.What other firewalls provide (the SPI packet filters) is the ability to block outbound connections, not just incoming connections. That's nice, but that's not a critical feature. Indeed, few organizations use firewalls that way, it just causes complaints when internal users cannot access Internet resources.Another way of using firewalls is to specify connections between a DMZ and an internal network, such as a web server exposed to the Internet that needs a hole in the firewall to access an internal database. While not technically part of the NAT definition, it's a feature of all modern NATs. It's the only way to get some games to work, for example.There's already more than 10-billion devices on the Internet, including homes with many devices, as well as most mobile phones. This means that NAT is the most common firewall. The reason hackers find it difficult hacking into iPhones is partly because they connect to the Internet through carrier-grade NAT. When hackers used "alpine" as the backdoor in Cydia, they still had to exploit it over local WiFi rather than the carrier network.Not only is NAT the most common firewall, it's the best firewall. Simple SPI firewalls that don't translate addresses have an inherent hole in that they are "fail open". It's easy to apply the wrong firewall ruleset, either permanently, or just for moment. You see this on internal IDS, where for no reason there's suddenly a spike of attacks against internal machines because of a bad rule. Every large organization I've worked with can cite examples of this.NAT, on the other hand, fails closed. Common mistakes shutdown access to the Internet rather than open up access from the Internet. The benefit is so compelling that organizations with lots of address space really need to give it up and move to private addressing instead.The definition of firewall is malleable. At one time it included explicit and transparent proxies, for example, which were the most popular type. These days, many people think of only state packet inspection filters as the "true" firewall. I take the more expansive view of things.The upshot is this: NAT is by definition a firewall. It's the most popular firewall. It's the best firewalling technology. Note: Of course, no organization should use firewalls of any type. They break the "end-to-end" principle of the Internet, and thus should be banned by law. |
||||
| 2017-01-09 23:13:24 | No, Yahoo! isn\'t changing its name (lien direct) | Trending on social media is how Yahoo is changing it's name to "Altaba" and CEO Marissa Mayer is stepping down. This is false.What is happening instead is that everything we know of as "Yahoo" (including the brand name) is being sold to Verizon. The bits that are left are a skeleton company that holds stock in Alibaba and a few other companies. Since the brand was sold to Verizon, that investment company could no longer use it, so chose "Altaba". Since 83% of its investment is in Alibabi, "Altaba" makes sense. It's not like this new brand name means anything -- the skeleton investment company will be wound down in the next year, either as a special dividend to investors, sold off to Alibaba, or both.Marissa Mayer is an operations CEO. Verizon didn't want her to run their newly acquired operations, since the entire point of buying them was to take the web operations in a new direction (though apparently she'll still work a bit with them through the transition). And of course she's not an appropriate CEO for an investment company. So she had no job left -- she made her own job disappear.What happened today is an obvious consequence of Alibaba going IPO in September 2014. It meant that Yahoo's stake of 16% in Alibaba was now liquid. All told, the investment arm of Yahoo was worth $36-billion while the web operations (Mail, Fantasy, Tumblr, etc.) was worth only $5-billion.In other words, Yahoo became a Wall Street mutual fund who inexplicably also offered web mail and cat videos.Such a thing cannot exist. If Yahoo didn't act, shareholders would start suing the company to get their money back.That $36-billion in investments doesn't belong to Yahoo, it belongs to its shareholders. Thus, the moment the Alibaba IPO closed, Yahoo started planning on how to separate the investment arm from the web operations.Yahoo had basically three choices.The first choice is simply give the Alibaba (and other investment) shares as a one time dividend to Yahoo shareholders. A second choice is simply split the company in two, one of which has the investments, and the other the web operations. The third choice is to sell off the web operations to some chump like Verizon.Obviously, Marissa Mayer took the third choice. Without a slushfund (the investment arm) to keep it solvent, Yahoo didn't feel it could run its operations profitably without integration with some other company. That meant it either had to buy a large company to integrate with Yahoo, or sell the Yahoo portion to some other large company.Every company, especially Internet ones, have a legacy value. It's the amount of money you'll get from firing everyone, stop investing in the future, and just raking in year after year a stream of declining revenue. It's the fate of early Internet companies like Earthlink and Slashdot. It's like how I documented with Earthlink [*], which continues to offer email to subscribers, but spends only enough to keep the lights on, not even upgrading to the simplest of things like SSL.Presumably, Verizon will try to make something of a few of the properties. Apparently, Yahoo's Fantasy sports stuff is popular, and will probably be rebranded as some new Verizon thing. Tumblr is already it's own brand name, independent of Yahoo, and thus will probably continue to exist as its own business unit.One of the weird things is Yahoo Mail. It permanently bound to the "yahoo.com" domain, so you can't do much with the "Yahoo" brand without bringing Mail along with it. Though at this point, the "Yahoo" brand is pretty tarnished. There's not much new you can put under that brand anyway. I can't see how Verizon would want to invest in that brand at all -- just milk it for what it can over the coming years.The investment company cannot long exist on its own. Investors want their | Yahoo | |||
| 2017-01-06 01:48:02 | Notes about the FTC action against D-Link (lien direct) | Today, the FTC filed a lawsuit against D-Link for security problems, such as backdoor passwords. I thought I'd write up some notes.The suit is not "product liability", but "unfair and deceptive" business practices for promising "security". In addition, they interpret "security" different from the cybersecurity community.This needs to be stressed because right now in our industry, there is a big discussion of product liability, insisting that everything attached to the Internet needs to be secured. People will therefore assume the FTC action is based on "liability".Instead, all six counts are based upon the fact that D-Link offers its products for securing networks, and claims they are secure. Because they have backdoor passwords, clear-text passwords, command-injection bugs, and public private-keys, the FTC feels the claims of security to be untrue.The key point I'm trying to make is that D-Link can resolve the suit (in theory) by simply removing all claims of "security". Sure, it can claim it supports stateful-inspection firewalls and WPA2, but not things like "WPA2 security". (Sure, the FTC may come back with a new lawsuit -- but it would solve the points raised in this one). On the other hand, while "deception" is the law the FTC uses, their obvious real intent is to improve security. They intend for D-Link to remove it's security weakness, not to change its claims. The lawsuit is also intended to scare all IoT makers into securing their products, not to remove claims of security.We see this intent in other posts on the FTC website. They've long been talking about IoT security. Recently, they announced a contest giving out $25,000 to the best solution for patching out-of-date IoT devices [*]. It's a silly contest, but shows what their real intent is.Thus, the language of the lawsuit is very much about improving security, while the actual counts are about unfair/deceptive practices.This is unfair for a number of reasons. Among their claims is that D-Link lied to their customers for saying "you need to change the default password to secure the device", because the device still had a command-injection bug. That's a shocking departure from common sense. We in the cybersecurity community repeatedly advise people to change passwords to make devices more secure, ignoring any other insecurity that might exist. It means I'm just as deceptive as D-Link is.The FTC's action is a clear violation of "due process". They didn't create a standard ahead of time of bugs that it would consider making a product "insecure", but instead arbitrarily punished D-Link for not meeting an unknown standard "secure". They never published a document saying "you can't advertise your product as being 'secure' if it contains this list of problems".More to the point, their idea of "secure" is at odds with the cybersecurity community. We would indeed describe WPA2 as secure, regardless of some other feature of the device that makes it insecure. Most IoT devices are intended to be used behind a firewall anyway, so the only attack surface is the WiFi network. In such cases, the device can have backdoor passwords up the ying-yang, and we in the cybersecurity community will still call is "secure".This is important because no product will ever be perfectly secure. Ten years from now, hackers will still dis On the other hand, while "deception" is the law the FTC uses, their obvious real intent is to improve security. They intend for D-Link to remove it's security weakness, not to change its claims. The lawsuit is also intended to scare all IoT makers into securing their products, not to remove claims of security.We see this intent in other posts on the FTC website. They've long been talking about IoT security. Recently, they announced a contest giving out $25,000 to the best solution for patching out-of-date IoT devices [*]. It's a silly contest, but shows what their real intent is.Thus, the language of the lawsuit is very much about improving security, while the actual counts are about unfair/deceptive practices.This is unfair for a number of reasons. Among their claims is that D-Link lied to their customers for saying "you need to change the default password to secure the device", because the device still had a command-injection bug. That's a shocking departure from common sense. We in the cybersecurity community repeatedly advise people to change passwords to make devices more secure, ignoring any other insecurity that might exist. It means I'm just as deceptive as D-Link is.The FTC's action is a clear violation of "due process". They didn't create a standard ahead of time of bugs that it would consider making a product "insecure", but instead arbitrarily punished D-Link for not meeting an unknown standard "secure". They never published a document saying "you can't advertise your product as being 'secure' if it contains this list of problems".More to the point, their idea of "secure" is at odds with the cybersecurity community. We would indeed describe WPA2 as secure, regardless of some other feature of the device that makes it insecure. Most IoT devices are intended to be used behind a firewall anyway, so the only attack surface is the WiFi network. In such cases, the device can have backdoor passwords up the ying-yang, and we in the cybersecurity community will still call is "secure".This is important because no product will ever be perfectly secure. Ten years from now, hackers will still dis |
||||
| 2017-01-05 22:50:57 | Profs: you should use JavaScript to teach Computer Science (lien direct) | Universities struggle with the canonical programming language they should teach students for Computer Science. Ideally, as they take computer science classes, all the homework assignments and examples will be in the same language. Today, that language is usually Java or Python. It should be JavaScript.The reason for this is simple: whatever language you learn, you will also have to learn JavaScript, because it's the lingua franca of web browsers.Python is a fundamentally broken language. Version 3 is incompatible with version 2, but after a decade, version 2 is still more popular. It's still unforgivably slow: other languages use JITs as a matter of course to get near native speed, while Python is still nearly always interpreted. Python isn't used in the real world, it's far down the list of languages programmers will use professionally. Python is primarily a middlware language, with neither apps nor services written in it.Java is a fine language, but there's a problem with it: it's fundamentally controlled by a single company, Oracle, who is an evil company. Consumer versions of Java come with viruses. They sue those who try to come up with competing versions of Java. It's not an "open" system necessary for universities.JavaScript has none of these problems. It's an open standard with many competing versions, two of which are completely open-source. New versions of the language are backwards compatible, but everyone stays closely up to date with the latest version anyway. It's extremely fast, as browsers vendors compete among themselves for the fastest JavaScript engine. It's used professionally everywhere, from writing phone apps to writing network services. And as mentioned above, everyone has to learn it eventually, because it's the language of web browsers.It's a great "software engineering" language. Most IDEs support it, but especially Microsoft's "Visual Code", which provides the same IDE for Windows, Mac, and Linux for editing and debugging JavaScript. A cross-platform IDE that works the same for all students, regardless of desktop, is an enormous plus. All the other "software engineering" features work well with JavaScript as well, such as professional requirements of version control, bug tracking, and unit/regression testing.It's an adequate "computer science" language. It supports all the major paradigms, like object-oriented and functional programming. It's perfect for teaching algorithms, data structures, complexity, boolean logic, number theory, Like most programming languages, it's got great library support for things like graphics, machine learning, robotics, cryptography, networking, databases, and so on.One weakness is that it's not "multithreaded", but that's pretty much a weakness in every language except maybe Erlang. Even in C, people are taught to do it wrong (mutexes) instead of the right way (scalable).JavaScript certainly has some quirks, but those are a feature for education, not a fault. Educators should go into a deep-dive with JavaScript explaining how it differs from other programming language. Explain how JavaScript pointers differ from C pointers, how object-oriented features differ from Java/C++, how functional features differ from LISP. A deep dive into things like AsmJS and JITs will teach you a lot about all languages.It's not adequate to teach all computer science concepts, of course. If you are teaching scientific computing, then things like MATLAB and R will be better -- but those languages are impractical for other computer science topics.In short, unlike any other language, everyone eventually has to learn JavaScript, in order to work within the browser. Given that, then we might as well use it as a pedagogical language. For most computer science topics, it's as | ||||
| 2017-01-03 21:33:01 | Dear Obama, From Infosec (lien direct) | Dear President Obama:We are more than willing to believe Russia was responsible for the hacked emails/records that influenced our election. We believe Russian hackers were involved. Even if these hackers weren't under the direct command of Putin, we know he could put a stop to such hacking if he chose. It's like harassment of journalists and diplomats. Putin encourages a culture of thuggery that attacks opposition, without his personal direction, but with his tacit approval.Your lame attempts to convince us of what we already agree with has irretrievably damaged your message.Instead of communicating with the America people, you worked through your typical system of propaganda, such as stories in the New York Times quoting unnamed "senior government officials". We don't want "unnamed" officials -- we want named officials (namely you) who we can pin down and question. When you work through this system of official leaks, we believe you have something to hide, that the evidence won't stand on its own.We still don't believe the CIA's conclusions because we don't know, precisely, what those conclusions are. Are they derived purely from companies like FireEye and CloudStrike based on digital forensics? Or do you have spies in Russian hacker communities that give better information? This is such an important issue that it's worth degrading sources of information in order to tell us, the American public, the truth.You had the DHS and US-CERT issue the "GRIZZLY-STEPPE" report "attributing those compromises to Russian malicious cyber activity". It does nothing of the sort. It's full of garbage. It contains signatures of viruses that are publicly available, used by hackers around the world, not just Russia. It contains a long list of IP addresses from perfectly normal services, like Tor, Google, Dropbox, Yahoo, and so forth.Yes, hackers use Yahoo for phishing and malvertising. It doesn't mean every access of Yahoo is an "Indicator of Compromise".For example, I checked my web browser [chrome://net-internals/#dns] and found that last year on November 20th, it accessed two IP addresses that are on the Grizzley-Steppe list: No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati |
Yahoo APT 29 APT 28 | |||
| 2017-01-01 18:02:45 | Your absurd story doesn\'t make me a Snowden apologist (lien direct) | Defending truth in the Snowden Affair doesn't make one an "apologist", for either side. There plenty of ardent supporters on either side that need to be debunked. The latest (anti-Snowden) example is the HPSCI committee report on Snowden [*], and stories like this one in the Wall Street Journal [*]. Pointing out the obvious holes doesn't make us "apologists".Snowden & apologists will brush this off w/ vague denials and counteraccusations. Burden's on them to square his representations w/ reality.- Susan Hennessey (@Susan_Hennessey) December 31, 2016As Edward Epstein documents in the WSJ story, one of the lies Snowden told was telling his employer (Booz-Allen) that he was being treated for epilepsy when in fact he was fleeing to Hong Kong in order to give documents to Greenwald and Poitras.Well, of course he did. If you are going to leak a bunch of documents to the press, you can't do that without deceiving your employer. That's the very definition of this sort of "whistleblowing". Snowden has been quite open to the public about the lies he told his employer, including this one.Rather than evidence that there's something wrong with Snowden, the way Snowden-haters (is that the opposite of "apologist"?) seize on this is evidence that they are a bit unhinged.The next "lie" is the difference between the number of documents Greenwald says he received (10,000) and the number investigators claim were stolen (1.5 million). This is not the discrepancy that it seems. A "document" counted by the NSA is not the same as the number of "files" you might get on a thumb drive, which was shown the various ways of counting the size of the Chelsea/Bradley Manning leaks. Also, the NSA can only see which files Snowden accessed, not which ones were then subsequently copied to a thumb drive.Finally, there is the more practical issue that Snowden cannot review the documents while at work. He'd have to instead download databases and copy whole directories to his thumb drives. Only away from work would he have the chance to winnow down which documents he wanted to take to Hong Kong, deleting the rest. Nothing Snowden has said conflicts with him deleting lots of stuff he never gave journalists, that he never took with him to Hong Kong, or took with him to Moscow.The next "lie" is that Snowden claims the US revoked his passport after he got on the plane from Hong Kong and before he landed in Moscow.This is factually wrong, in so far as the US had revoked his passport (and issued an arrest warrant) and notified Hong Kong of the revocation a day before the plane took off. However, as numerous news reports of the time reported, the US information [in the arrest warrant] was contradictory and incomplete, and thus Hong Kong did nothing to stop Snowden from leaving [*]. The Guardian [*] quotes a Hong Kong official as saying Snowden left "through a lawful and normal channel". Seriously, countries are much less concerned about checking passports of passenger leaving than those arriving.It's the WSJ article that's clearly prevaricating here, quoting a news article where a Hong Kong official admits being notified, but not quoting the officials saying that the information was bad, that they took no action, and that Snowden left in the normal way.The next item | ||||
| 2016-12-29 20:40:33 | Some notes on IoCs (lien direct) | Obama "sanctioned" Russia today for those DNC/election hacks, kicking out 35 diplomats, closing diplomatic compounds, seizing assets of named individuals/groups. They also published "IoCs" of those attacks, fingerprints/signatures that point back to the attackers, like virus patterns, file hashes, and IP addresses.These IoCs are of low quality. They are published as a political tool, to prove they have evidence pointing to Russia. They have limited utility to defenders, or those publicly analyzing attacks.Consider the Yara rule included in US-CERT's "GRIZZLY STEPPE" announcement: What is this? What does this mean? What do I do with this information?It's a YARA rule. YARA is a tool ostensibly for malware researchers, to quickly classify files. It's not really an anti-virus product designed to prevent or detect an intrusion/infection, but to analyze an intrusion/infection afterward -- such as attributing the attack. Signatures like this will identify a well-known file found on infected/hacked systems.What this YARA rule detects is, as the name suggests, the "PAS TOOL WEB KIT", a web shell tool that's popular among Russia/Ukraine hackers. If you google "PAS TOOL PHP WEB KIT", the second result points to the tool in question. You can download a copy here [*], or you can view it on GitHub here [*].Once a hacker gets comfortable with a tool, they tend to keep using it. That implies the YARA rule is useful at tracking the activity of that hacker, to see which other attacks they've been involved in, since it will find the same web shell on all the victims.The problem is that this P.A.S. web shell is popular, used by hundreds if not thousands of hackers, mostly associated with Russia, but also throughout the rest of the world (judging by hacker forum posts). This makes using the YARA signature for attribution problematic: just because you found P.A.S. in two different places doesn't mean it's the same hacker.A web shell, by the way, is one of the most common things hackers use once they've broken into a server. It allows further hacking and exfiltration traffic to appear as normal web requests. It typically consists of a script file (PHP, ASP, PERL, etc.) that forwards commands to the local system. There are hundreds of popular web shells in use.We have little visibility into how the government used these IoCs. IP addresses and YARA rules like this are weak, insufficient for attribution by themselves. On the other hand, if they've got web server logs from multiple victims where commands from those IP addresses went to this specific web shell, then the attribution would be strong that all these attacks are by the same actor.In other words, these rules can be a reflection of the fact the government has excellent information for attribution. Or, it could be a reflection that they've got only weak bits and pieces. It's impossible for us outsiders to tell. IoCs/signatures are fetishized in the cybersecurity community: they love the small rule, but they ignore the complexity and context around the rules, often misunderstanding what's going on. (I've written thousands of the things -- I'm constantly annoyed by the ignorance among those not understanding what they mean).I see on What is this? What does this mean? What do I do with this information?It's a YARA rule. YARA is a tool ostensibly for malware researchers, to quickly classify files. It's not really an anti-virus product designed to prevent or detect an intrusion/infection, but to analyze an intrusion/infection afterward -- such as attributing the attack. Signatures like this will identify a well-known file found on infected/hacked systems.What this YARA rule detects is, as the name suggests, the "PAS TOOL WEB KIT", a web shell tool that's popular among Russia/Ukraine hackers. If you google "PAS TOOL PHP WEB KIT", the second result points to the tool in question. You can download a copy here [*], or you can view it on GitHub here [*].Once a hacker gets comfortable with a tool, they tend to keep using it. That implies the YARA rule is useful at tracking the activity of that hacker, to see which other attacks they've been involved in, since it will find the same web shell on all the victims.The problem is that this P.A.S. web shell is popular, used by hundreds if not thousands of hackers, mostly associated with Russia, but also throughout the rest of the world (judging by hacker forum posts). This makes using the YARA signature for attribution problematic: just because you found P.A.S. in two different places doesn't mean it's the same hacker.A web shell, by the way, is one of the most common things hackers use once they've broken into a server. It allows further hacking and exfiltration traffic to appear as normal web requests. It typically consists of a script file (PHP, ASP, PERL, etc.) that forwards commands to the local system. There are hundreds of popular web shells in use.We have little visibility into how the government used these IoCs. IP addresses and YARA rules like this are weak, insufficient for attribution by themselves. On the other hand, if they've got web server logs from multiple victims where commands from those IP addresses went to this specific web shell, then the attribution would be strong that all these attacks are by the same actor.In other words, these rules can be a reflection of the fact the government has excellent information for attribution. Or, it could be a reflection that they've got only weak bits and pieces. It's impossible for us outsiders to tell. IoCs/signatures are fetishized in the cybersecurity community: they love the small rule, but they ignore the complexity and context around the rules, often misunderstanding what's going on. (I've written thousands of the things -- I'm constantly annoyed by the ignorance among those not understanding what they mean).I see on |
APT 29 APT 28 | |||
| 2016-12-28 23:27:25 | IoT saves lives but infosec wants to change that (lien direct) | The cybersecurity industry mocks/criticizes IoT. That's because they are evil and wrong. IoT saves lives. This was demonstrated a couple weeks ago when a terrorist attempted to drive a truck through a Christmas market in German. The truck has an Internet-connected braking system (firmware updates, configuration, telemetry). When it detected the collision, it deployed the brakes, bringing the truck to a stop. Injuries and deaths were a 10th of the similar Nice truck attack earlier in the year.All the trucks shipped by Scania in the last five years have had mobile phone connectivity to the Internet. Scania pulls back telemetry from trucks, for the purposes of improving drivers, but also to help improve the computerized features of the trucks. They put everything under the microscope, such as how to improve air conditioning to make the trucks more environmentally friendly.Among their features is the "Autonomous Emergency Braking" system. This is the system that saved lives in Germany.You can read up on these features on their website, or in their annual report [*].My point is this: the cybersecurity industry is a bunch of police-state fetishists that want to stop innovation, to solve the "security" problem first before allowing innovation to continue. This will only cost lives. Yes, we desperately need to solve the problem. Almost certainly, the Scania system can trivially be hacked by mediocre hackers. But if Scania had waited first to secure its system before rolling it out in trucks, many more people would now be dead in Germany. Don't listen to cybersecurity professionals who want to stop the IoT revolution -- they just don't care if people die. Update: Many, such the first comment, point out that the emergency brakes operate independently of the Internet connection, thus disproving this post.That's silly. That's the case of all IoT devices. The toaster still toasts without Internet. The surveillance camera still records video without Internet. My car, which also has emergency brakes, still stops. In almost no IoT is the Internet connectivity integral to the day-to-day operation. Instead, Internet connectivity is for things like configuration, telemetry, and downloading firmware updates -- as in the case of Scania.While the brakes don't make their decision based on the current connectivity, connectivity is nonetheless essential to the equation. Scania monitors its fleet of 170,000 trucks and uses that information to make trucks, including braking systems, better.My car is no more or less Internet connected than the Scania truck, yet hackers have released exploits at hacking conferences for it, and it's listed as a classic example of an IoT device. Before you say a Scania truck isn't an IoT device, you first have to get all those other hackers to stop calling my car an IoT device. |
||||
| 2016-12-21 18:44:41 | "From Putin with Love" - a novel by the New York Times (lien direct) | In recent weeks, the New York Times has written many stories on Russia's hacking of the Trump election. This front page piece [*] alone takes up 9,000 words. Combined, the NYTimes coverage on this topic exceeds the length of a novel. Yet, for all this text, the number of verifiable facts also equals that of a novel, namely zero. There's no evidence this was anything other than an undirected, Anonymous-style op based on a phishing campaign.The question that drives usIt's not that Russia isn't involved, it's that the exact nature of their involvement is complicated. Just because the hackers live in Russia doesn't automatically mean their attacks are directed by the government.It's like the recent Islamic terrorist attacks in Europe and America. Despite ISIS claiming credit, and the perpetrators crediting ISIS, we are loathe to actually blame the attacks directly on ISIS. Overwhelmingly, it's individuals who finance and plan their attacks, with no ISIS organizational involvement other than inspiration.The same goes for Russian hacks. The Russian hacker community is complicated. There are lots of actors with various affiliations with the government. They are almost always nationalistic, almost always pro-Putin. There are many individuals and groups who act to the benefit of Putin/Russia with no direct affiliation with the government. Others do have ties with the government, but these are often informal relationships, sustained by patronage and corruption.Evidence tying Russian attacks to the Russian government is thus the most important question of all -- and it's one that the New York Times is failing to answer. The fewer facts they have, the more they fill the void with vast amounts of verbiage.Sustaining the narrativeHere's a trick when reading New York Times articles: when they switch to passive voice, they are covering up a lie. An example is this paragraph from the above story [*]:The Russians were also quicker to turn their attacks to political purposes. A 2007 cyberattack on Estonia, a former Soviet republic that had joined NATO, sent a message that Russia could paralyze the country without invading it. The next year cyberattacks were used during Russia's war with Georgia.Normally, editors would switch this to the active voice, or:The next year, Russia used cyberattacks in their war against Georgia.But that would be factually wrong. Yes, cyberattacks happened during the conflicts with Estonia and Georgia, but the evidence in both cases points to targets and tools going viral on social media and web forums. It was the people who conducted the attacks, not the government. Whether it was the government who encouraged the people is the big question -- to which we have no answer. Since the NYTimes has no evidence pointing to the Russian government, they switch to the passive voice, hoping you'll assume they meant the government was to blame.It's a clear demonstration that the NYTimes is pushing a narrative, rather than reporting just the facts allowing you to decide for yourself.Tropes and clichesThe NYTimes story is dominated by cliches or "tropes".One such trope is how hackers are always "sophisticated", which leads to the conclusion they must be state-sponsored, not simple like the Anonymous collective. Amusingly, the New York Times tries to give two conflicting "sophisticated" narratives at once. Their article [*] has a section titled "Honing Stealthy Tactics", which ends with describing the attacks as "brazen" | Guideline | |||
| 2016-12-20 23:08:58 | No, that House Judiciary committee did not reject backdoors (lien direct) | A House of Representatives committee has produced a report on "encryption". It's tilted in our favor, the "strong crypto" side of the debate, but not enough for us to embrace it. It stops short of explicitly condemning crypto-backdoors, but also supports "compelled disclosure" and "government hacking". It tries to thread the needle, claiming both "security interests" and "individual privacy" can be accommodated. They can't be.I point this out because on many issues, our side has compromised, only to have that used against us. Those like the EFF compromised on the USA FREEDOM act, supporting it at the beginning as a way to reform NSA metadata surveillance, only to have the end product increase such surveillance. Yes, the EFF then retracted their support, but by then, the damage had been done.Our side came up with the euphemism "strong crypto" to position our opposition to "backdoors", that any attempt to backdoor crypto inevitably "weakens" it. This is going to bite us in the end when lawmakers decide to compromise on "strong backdoors".While this committee report explicitly says "Congress should not weaken this vital technology because doing so works against the national interest", and suggests other approaches to gather evidence, nowhere does it explicitly reject "backdoors". The idea of "strong backdoors" is consistent with the report.I'm not saying the report actually supports "strong backdoors". It does a good job arguing our side, such as how there's no way to mandate backdoors in foreign crypto software we might install on our phones. While it doesn't explicitly mention "backdoors", it does so many times euphemistically, driving home the (correct) point that strong encryption is critically important to our economy and modern society.Thus, the removal of the word "backdoor" is obviously an attempt to make the document more palatable to the other side, the law enforcement side. It explicitly avoids taking a "binary" position.The paper then suggests two other controversial policies: compelled disclosure and hacking."Compelled disclosure" is where law enforcement compels somebody to either reveal their password, or decrypt something. This is problematic for a number of reasons. One is the Fifth Amendment provisions against self incrimination. The other is the practical fact that the suspect may not be able to, either because they've forgotten the password to an old backup drive, or because the phone they are being forced to decrypt isn't actually theirs. Most of us oppose "compelled disclosure", though not as strongly as "backdoors". That's mostly because any abuse would immediately be visible, whereas backdoors can be exploited in secret."Hacking" is where the government breaks into your computer. "End-to-end" crypto doesn't protect you when the NSA has hacked one "end", such as by breaking into your phone. Many in the community oppose this, because it can be abused in secret with no public accountability. Recent "Rule 41" changes have been especially contentious. The recent "Playpen" case is also controversial, especially the way the FBI keeps its exploit secret. On the other hand, many vigorous opponents of backdoors are also vigorous supporters of government hacking, wanting neither artificial abilities for, or artificial limitations against, law enforcement [this includes me].In conclusion, the above paper stresses that there is no "binary" debate between pro-encryption and law enforcement. This is wrong. The debate over "backdoors" is indeed binary: law enforcement won't accept any solution without them, and freedom activists will accept no solution with them. Compelled decryption may also be such a sticky, uncompromisable debate. Only "government hac | Guideline | |||
| 2016-12-13 00:50:13 | That anti-Trump Recode article is terrible (lien direct) | Trump's a dangerous populist. However, the left-wing media's anti-Trump fetishism is doing nothing to stop Trump. It's no better than "fake news" -- it gets passed around a lot on social-media, but is intellectually bankrupt, unlikely to change anybody's mind. A good example is this op-ed on Re/Code [*] about Silicon Valley leaders visiting Trump.The most important feature of that Re/code article is that it contains no criticism of Trump other than the fact that he's a Republican. Half the country voted for Trump. Half the country voted Republican. It's not just Trump that this piece imagines as being unreasonable, but half the country. It's a fashionable bigotry among some of Silicon Valley's leftist elite.But CEOs live in a world where half their customers are Republican, where half their share holders are Republican. They cannot lightly take political positions that differ from their investors/customers. The Re/code piece claims CEOs said "we are duty-bound as American citizens to attend". No, what they said was "we are duty-bound as officers of our corporations to attend".The word "officer", as in "Chief Operating Officer", isn't an arbitrary title like "Senior Software Engineer" that has no real meaning. Instead, "officer" means "bound by duty". It includes a lot of legal duties, for which they can go to jail if they don't follow. It includes additional duties to shareholders, for which the board can fire them if they don't follow.Normal employees can have Twitter disclaimers saying "these are my personal opinions only, not that of my employer". Officers of corporations cannot. They are the employer. They cannot champion political causes of their own that would impact their stock price. Sure, they can do minor things, like vote, or contribute quietly to campaigns, as long as they aren't too public. They can also do political things that enhances stock price, such as opposing encryption backdoors. Tim Cook can announce he's gay, because that enhances the brand image among Apple's key demographic of millennials. It's not something he could do if he were the CEO of John Deere Tractors.Among the things the CEO's cannot do is take a stance against Donald Trump. The Boeing thing is a good example. The Boeing's CEO criticized Trump's stance on free trade, and 30 minutes later Trump tweeted criticisms of a $4 billion contract with Boeing, causing an immediate billion drop in Boeing's stock price.This incident shows why the rest of us need to appose Trump. Such vindictive politics is how democracies have failed. We cannot allow this to happen here. But the hands of CEOs are tied -- they are duty bound to avoid such hits to their stock price.On the flip, this is one of the few chances CEOs will be able to lobby Trump. If Trump has proven anything, it's that he has no real positions on things. This would be a great time to change his mind on "encryption backdoors", for example.Trump is a dangerous populist who sews distrust in the institutions that give us a stable, prosperous country. Any institution, from the press, to the military, to the intelligence services, to the election system, is attacked, brought into disrepute, even if it supports him. Trump has a dubious relationship with the truth, such as his repeated insistence he won a landslide rather than by a slim margin. He has deep character flaws, such as his vindictive attacks against those who oppose him (Boeing is just one of many examples). Hamilton electors cite deep, patriotic principles for changing their votes, such as Trump's foreign influences and demagoguery.What I'm demonstrating here is that thinking persons have good reasons to oppose Trump that can be articulated without mentioning political issues that divide Democrats and Republicans. That the Re/code a | Guideline | |||
| 2016-12-11 02:46:15 | Some notes on a Hamilton election (lien direct) | At least one elector for Trump has promised to switch his vote, becoming a "Hamilton Elector". Assuming 36 more electors (about 10% of Trump's total) do likewise, and Trump fails to get the 270 absolute majority, then what happens? Since all of the constitutional law scholars I follow haven't taken a stab at this, I thought I would write up some notes.Foreign powers and populistsIn Federalist #68, Alexander Hamilton laid out the reasons why electors should switch their vote. The founders feared bad candidates unduly influenced by foreign powers, and demagogues. Trump is unabashedly both. He criticizes our own CIA claiming what every American knows, that Russia interfered in our election. Trump is the worst sort of populist demagogue, offering no solution to problems other than he'll be a strong leader.Therefore, electors have good reasons to change their votes. I'm not suggesting they should, only that doing so is consistent with our Constitutional principles and history.So if 10% of Trump's electors defect, how would this actually work?Failure to get 270 vote absolute majority (math)Well, to start with, let's count up the number of electors. Each state gets one elector for every House Representative and each Senator. Since there are 435 members of the House and 100 members of the Senate, that comes out to 535. However, the 23rd Amendment adds three more electors for Washington D.C. (so they can vote in the Presidential election but not Congress). So that means the there are 538 total electors.According to the Constitution, the winner must get an absolute majority, meaning over 50% of the electoral votes cast. Half of 538 is 269, plus one to get more than half to get majority, equals 270. Thus, Trump must get at least 270 electoral votes. If he gets only 269, the election fails.Trump won 306 electors in the election. To get below 270, then 37 electors must switch their votes, which is a little over 10%.Electors are free to change their votesConstitutionally, the electors are free to change their votes. However, for most, it would destroy their political careers. Most are state party people who have spent years building up power and reputation in their respective states. Violating their word would destroy all that -- nobody would trust them again. They would certainly never be chosen as an elector again, of course.Many states have laws against electors changing their votes. It is widely accepted that these laws are unconstitutional and would be struck down the courts, but in the meanwhile, some vote flippers would have to spend considerable time and money defending themselves from the legal punishment.Electors vote December 19We've only got until December 19th [*] for electors to change their minds. That's the date they vote. The votes are collected in their various states, then sent to Washington.Electoral votes counted January 6Ballots are theoretically sealed until January 6, when the votes are unsealed and counted in front of Congress.A 26 state majority of House delegationsIf the elector college fails to get an absolute majority of 270 votes, then the election is thrown into the House of Representatives. But it's not a straight up vote among all 435 members of the House. Instead, there are 50 votes -- one for each state delegation. Again, the winner must get an absolute majority to win, meaning 26 votes.This will be the newly elected House of Representatives, which will have been sworn in on January 3, three days earlier. They are instructed to immediately vote, right after the count | Guideline | |||
| 2016-12-05 23:41:40 | That "Commission on Enhancing Cybersecurity" is absurd (lien direct) | An Obama commission has publish a report on how to "Enhance Cybersecurity". It's promoted as having been written by neutral, bipartisan, technical experts. Instead, it's almost entirely dominated by special interests and the Democrat politics of the outgoing administration.In this post, I'm going through a random list of some of the 53 "action items" proposed by the documents. I show how they are policy issues, not technical issues. Indeed, much of the time the technical details are warped to conform to special interests.IoT passwordsThe recommendations include such things as Action Item 2.1.4:Initial best practices should include requirements to mandate that IoT devices be rendered unusable until users first change default usernames and passwords. This recommendation for changing default passwords is repeated many times. It comes from the way the Mirai worm exploits devices by using hardcoded/default passwords.But this is a misunderstanding of how these devices work. Take, for example, the infamous Xiongmai camera. It has user accounts on the web server to control the camera. If the user forgets the password, the camera can be reset to factory defaults by pressing a button on the outside of the camera.But here's the deal with security cameras. They are placed at remote sites miles away, up on the second story where people can't mess with them. In order to reset them, you need to put a ladder in your truck and drive 30 minutes out to the site, then climb the ladder (an inherently dangerous activity). Therefore, Xiongmai provides a RESET.EXE utility for remotely resetting them. That utility happens to connect via Telnet using a hardcoded password.The above report misunderstands what's going on here. It sees Telnet and a hardcoded password, and makes assumptions. Some people assume that this is the normal user account -- it's not, it's unrelated to the user accounts on the web server portion of the device. Requiring the user to change the password on the web service would have no effect on the Telnet service. Other people assume the Telnet service is accidental, that good security hygiene would remove it. Instead, it's an intended feature of the product, to remotely reset the device. Fixing the "password" issue as described in the above recommendations would simply mean the manufacturer would create a different, custom backdoor that hackers would eventually reverse engineer, creating MiraiV2 botnet. Instead of security guides banning backdoors, they need to come up with standard for remote reset.That characterization of Mirai as an IoT botnet is wrong. Mirai is a botnet of security cameras. Security cameras are fundamentally different from IoT devices like toasters and fridges because they are often exposed to the public Internet. To stream video on your phone from your security camera, you need a port open on the Internet. Non-camera IoT devices, however, are overwhelmingly protected by a firewall, with no exposure to the public Internet. While you can create a botnet of Internet cameras, you cannot create a botnet of Internet toasters.The point I'm trying to demonstrate here is that the above report was written by policy folks with little grasp of the technical details of what's going on. They use Mirai to justify several of their "Action Items", none of which actually apply to the technical details of Mirai. It has little to do with IoT, passwords, or hygiene.Public-private partnershipsAction Item 1.2.1: The President should create, through executive order, the National Cybersecurity Private–Public Program (NCP 3 ) as a forum for addressing cybersecurity issues through a high-level, joint public–private collaboration.We've had public-private partnerships to secure cyberspace for over 20 years, such as the FBI InfraGuard partner | Guideline | |||
| 2016-12-01 14:37:51 | Electoral college should ignore Lessig (lien direct) | Reading this exchange between law profs disappoints me. [1] [2] [3] [4] [5]The decision Bush v Gore cites the same principle as Lessig, that our system is based on "one person one vote". But it uses that argument to explain why votes should not be changed once they are cast:Having once granted the right to vote on equal terms, the State may not, by later arbitrary and disparate treatment, value one person's vote over that of another.Lessig cites the principle of "one person one vote", but in a new and novel way. He applies in an arbitrary way that devalues some of the votes that have already been cast. Specifically, he claims that votes cast for state electors should now be re-valued as direct votes for a candidate.The United States isn't a union of people. It's a union of states. It says so right in the name. Compromises between the power of the states and power of the people have been with us for forever. That's why states get two Senators regardless of size, but Representatives to the House are assigned proportional to population. The Presidential election is expressly a related compromise, assigning the number of electors to a state equal to the number of Senators plus Representatives.The Constitution doesn't even say electors should be chosen using a vote. It's up to the states to decide. All states have chosen election, but they could've demanded a wrestling match or juggling contest instead. The point is that the Constitution, historical papers, and 200 years of history rejects Lessig's idea that the President should be elected with a popular vote.Moreover, this election shows the value of election by states. The tension nowadays is between big urban areas and rural areas. In the city, when workers lose their jobs due to immigration or trade, they can go down the street and get another job. In a rural area, when the factory shuts down, the town is devastated, and there are no other jobs to be had. The benefits of free trade are such that even Trump can't roll them back -- but as a nation we need to address the disproportionate impact changes have on rural communities. That rural communities can defend their interests is exactly why our Constitution is the way it is -- and why the President isn't chosen with a popular vote.Hillary did not win the popular vote. No popular vote was held. Instead, we had state-by-state votes for electors. It's implausible that the per-candidate votes would have been the same had this been a popular vote. Candidates would have spent their time and money campaigning across the entire country instead of just battleground states. Voters would have different motivations on which candidates to choose and on whether they should abstain. There is nothing more clearly "disparate and arbitrary" treatment of votes than claiming a your vote for an elector (or abstention) will now instead be treated as a national vote for the candidate.Hillary got only 48% of the vote, what we call a plurality. Counting abstentions, that's only 26% of the vote. The rules of | ||||
| 2016-11-27 17:28:57 | No, it\'s Matt Novak who is a fucking idiot (lien direct) | I keep seeing this Gizmodo piece entitled “Snowden is a fucking idiotâ€. I understand the appeal of the piece. The hero worship of Edward Snowden is getting old. But the piece itself is garbage.The author, Matt Novak, is of the new wave of hard-core leftists intolerant of those who disagree with them. His position is that everyone is an idiot who doesn't agree with his views: Libertarians, Republicans, moderate voters who chose Trump, and even fellow left-wingers that aren't as hard-core.If you carefully read his piece, you'll see that Novak doesn't actually prove Snowden is wrong. Novak doesn't show how Snowden disagrees with facts, but only how Snowden disagrees with the left-wing view of the world, "libertarian garbage" as Novak puts it. It's only through deduction that we come to the conclusion: those who aren't left-wing are idiots, Snowden is not left-wing, therefore Snowden is an idiot.The question under debate in the piece is:technology is more important than policy as a way to protect our libertiesIn other words, if you don't want the government spying on you, then focus on using encryption (use Signal) rather than trying to change the laws so they can't spy on you.On a factual basis (rather than political), Snowden is right. If you live in Germany and don't want the NSA spying on you there is little policy-wise that you can do about it, short of convincing Germany to go to war against the United States to get the US to stop spying.Likewise, for all those dissenters in countries with repressive regimes, technology precedes policy. You can't effect change until you first can protect yourselves from the state police who throws you in jail for dissenting. Use Signal.In our own country, Snowden is right about “politicsâ€. Snowden's leak showed how the NSA was collecting everyone's phone records to stop terrorism. Privacy organizations like the EFF supported the reform bill, the USA FREEDOM ACT. But rather than stopping the practice, the “reform†opened up the phone records to all law enforcement (FBI, DEA, ATF, IRS, etc.) for normal law enforcement purposes.Imagine the protestors out there opposing the Dakota Access Pipeline. The FBI is shooting down their drones and blasting them with water cannons. Now, because of the efforts of the EFF and other privacy activists, using the USA FREEDOM ACT, the FBI is also grabbing everyone's phone records in the area. Ask yourself who is the fucking idiot here: the guy telling you to use Signal, or the guy telling you to focus on “politics†to stop this surveillance.Novak repeats the hard-left version of the creation of the Internet:The internet has always been monitored by the state. It was created by the fucking US military and has been monitored from day one. Surveillance of the internet wasn't invented after September 11, 2001, no matter how many people would like to believe that to be the case.No, the Internet was not created by the US military. Sure, the military contributed to the Internet, but the majority of contributions came from corporations, universities, and researchers. The left-wing claim that the government/military created the Internet involves highlighting their contributions while ignoring everyone else's.The Internet was not “monitored from day oneâ€, because until the 1990s, it wasn't even an important enough network to monitor. As late as 1993, the Internet was dwarfed in size and importance by numerous other computer networks – until the web took off that year, the Internet was considered a temporary research project. Those like Novak writing the history of the Internet are astonishingly ignorant of the competing networks of those years. They miss XNS | ||||
| 2016-11-21 21:55:31 | The false-false-balance problem (lien direct) | Until recently, journalism in America prided itself on objectivity -- to report the truth, without taking sides. That's because big debates are always complexed and nuanced, and that both sides are equally reasonable. Therefore, when writing an article, reporters attempt to achieve balance by quoting people/experts/proponents on both sides of an issue.But what about those times when one side is clearly unreasonable? You'd never try to achieve balance by citing those who believe in aliens and big-foot, for example.Thus, journalists have come up with the theory of false-balance to justify being partisan and one-sided on certain issues.Typical examples where journalists cite false-balance is reporting on anti-vaxxers, climate-change denialists, and Creationists. More recently, false-balance has become an issue in the 2016 Trump election.But this concept of false-balance is wrong. It's not that anti-vaxxers, denialists, Creationists, and white supremacists are reasonable. Instead, the issue is that the left-wing has reframed the debate. They've simplified it into something black-and-white, removing nuance, in a way that shows their opponents as being unreasonable. The media then adopts the reframed debate.Let's talk anti-vaxxers. One of the policy debates is whether the government has the power to force vaccinations on people (or on people's children). Reasonable people say the government doesn't have this power. Many (if not most) people hold this opinion while agreeing that vaccines are both safe and effective (that they don't cause autism).Consider this February 2015 interview with Chris Christy. He's one of the few politicians who have taken the position that government can override personal choice, such as in the case of an outbreak. Yet, when he said "parents need to have some measure of choice in things as well, so that's the balance that the government has to decide", he was broadly reviled as an anti-vaxxer throughout the media. The press reviled other Republican candidates the same way, even while ignoring almost identical statements made at the same time by the Obama administration. They also ignored clearly anti-vax comments from both Hillary and Obama during the 2008 election.Yes, we can all agree that anti-vaxxers are a bunch of crazy nutjobs. In calling for objectivity, we aren't saying that you should take them seriously. Instead, we are pointing out the obvious bias in the way the media attacked Republican candidates as being anti-vaxxers, and then hiding behind "false-balance".Now let's talk evolution. The issue is this: Darwinism has been set up as some sort of competing religion against belief in God(s). High-schools teach children to believe in Darwinism, but not to understand Darwinism. Few kids graduate understanding Darwinism, which is why it's invariably misrepresented in mass-media (X-Men, Planet of the Apes, Waterworld, Godzilla, Jurassic Park, etc.). The only movie I can recall getting evolution correct is Idiocracy.Also, evolution has holes in it. This isn't a bad thing in science, every scientific theory has holes. Science isn't a religion. We don't care about the holes. That some things remain unexplained by a theory doesn't bother us. Science has no problem with gaps in knowledge, where we admit "I don't know". It's religion that has "God of the gaps", where ignorance isn't tolerated, and everything unexplained is explained by a deity.The hole in evolution is how the cell evolved. The fossil record teaches us a lot about multi-cellular organisms over the last 400-million years, but not much about how the cell evolved in th | Guideline | |||
| 2016-11-14 23:30:27 | Comments for my biracial niece (lien direct) | I spent the night after Trump's victory consoling my biracial niece worried about the election. Here are my comments. You won't like them, expecting the opposite given the title. But it's what I said. I preferred Hillary, but that doesn't mean Trump is an evil choice.Don't give into the hate. You get most of your news via social media sites like Facebook and Twitter, which are at best one-sided and unfair. At worst, they are completely inaccurate. Social media posts are driven by emotion, not logic. Sometimes that emotion is love of cute puppies. Mostly it's anger, fear, and hate. Instead of blindly accepting what you read, challenge it. Find the original source. Find a better explanation. Search for context.Don't give into the hate. The political issues that you are most concerned about are not simple and one-sided with obvious answers. They are complex and nuanced. Just because somebody disagrees with you doesn't mean they are unreasonable or evil. In today's politics, it has become the norm that we can't simply disagree with somebody, but must also vilify and hate them. We've redefined politics to be the fight between the virtuous (whatever side we are on) and the villains (the other side). The reality is that both sides are equally reasonable, equally virtuous.Don't give into the hate. Learn “critical thinkingâ€. Learn how “cherry picking†the fringe of the opposing side is used to tarnish the mainstream. Learn how “strawman arguments†makes the other side sound dumb. Learn how “appeal to emotion†replaces logic. Learn how “ad hominem†statements attack the credibility of opponent's arguments. Learn how issues are simplified into “back vs. white†options rather than the nuance and complexity that actually exists.Don't give into the hate. The easy argument is that it's okay to be hateful and bigoted toward Trump and his supporters because they are bigoted against you. No, it's not okay to hate anybody, not even Hitler, as Atticus Finch explains in “To Kill A Mockingbirdâ€. In that book, Atticus even tries to understand, and not hate, Robert Ewell, the racist antagonist in the book who eventually tries to stab Scout (Atticus's daughter). Trump's supporters may be wrong, but it's a wrongness largely based on ignorance, not malice. Yes, they probably need to be kindly educated, but they don't deserve punishment and hate.America is the same country it was last week. It's citizens haven't changed, only one man in an office has changed. The President has little actual power, either to fix things (as his supporters want) or to break things (as his opponents fear). We have strong institutions, from Congress, to the Courts, to the military, that will hold him check. The biggest worries are that he's the first President in history with no government experience, and that he's strongly "populist" (which historically has been damaging for countries). We should be watchful, and more willing to stand up and fight when Trump does something bad. However, we shouldn't give into hate. |
||||
| 2016-11-14 22:29:16 | How to teach endian (lien direct) | On /r/programming is this post about byte-order/endianness. It gives the same information as most documents on the topic. It is wrong. It's been wrong for over 30 years. Here's how it should be taught.One of the major disciplines in computer science is parsing/formatting. This is the process of converting the external format of data (file formats, network protocols, hardware registers) into the internal format (the data structures that software operates on).It should be a formal computer-science discipline, because it's actually a lot more difficult than you'd expect. That's because the majority of vulnerabilities in software that hackers exploit are due to parsing bugs. Since programmers don't learn about parsing formally, they figure it out for themselves, creating ad hoc solutions that are prone to bugs. For example, programmers assume external buffers cannot be larger than internal ones, leading to buffer overflows.An external format must be well-defined. What the first byte means must be written down somewhere, then what the second byte means, and so on. For Internet protocols, these formats are written in RFCs, such as RFC 791 for the "Internet Protocol". For file formats, these are written in documents, such as those describing GIF files, JPEG files, MPEG files, and so forth.Among the issues is how integers should be represented. The definition must include the size, whether signed/unsigned, what the bits means (almost always 2s-compliment), and the byte-order. Integers that have values above 255 must be represented with more than one byte. Whether those bytes go left-to-right or right-to-left is known as byte-order.We also called this endianness, where one form is big-endian and the other form is little-endian. This is a joke, referring back to Jonathan Swift's tale Gulliver's Travels, where two nations were at war arguing whether an egg should be cracked on the big end or the little end. The joke refers to the Holy Wars in computing where two sides argued strongly for one byte-order or the other. The commentary using the term "endianess" is that neither format matters.However, big-endian is how humans naturally process numbers. If we have the hex value 0x2211, then we expect that representing this number in a file/protocol will consist of one byte with the value 0x22 followed by another byte with the value 0x11. In a little-endian format specification, however, the order of bytes will be reversed, with a value of 0x2211 represented with 0x11 followed by 0x22.This is further confused by the fact that the nibbles in the byte will still be written in conventional, big-endian order. In other words, the big-endian format for the number 0x1234 is 0x12 0x34. however, the little-endian format is 0x34 0x12 -- not 0x43 0x21 as you might naively expect trying to swap everything around in your mind.If little-endian is so confusing to the human mind, why would anybody ever use it? The answer is that it can be more efficient for logic circuits. Or at least, back in the 1970s, when CPUs had only a few thousand logic gates, it could be more efficient. Therefore, a lot of internal processing was little-endian, and this bled over into external formats as well.On the other hand, most network protocols and file formats remain big-endian. Format specifications are written for humans to understand, and big-endian is easier for us humans.So once you understand the byte-order issue in external formats, the next problem is figuring out how to parse it, to convert it into an internal data structure. Well, we first have to understand how to parse things in general.There are two ways of parsing thing: buffered or streaming. In the buffered model, you read in the entire input f | Guideline | |||
| 2016-11-06 20:06:58 | Yes, the FBI can review 650,000 emails in 8 days (lien direct) | In today's news, Comey announces the FBI have reviewed all 650,000 emails found on Anthony Wiener's computer and determined there's nothing new. Some have questioned whether this could be done in 8 days. Of course it could be -- those were 650,000 emails to Wiener, not Hillary.IMPOSSIBLE: There R 691,200 seconds in 8 days. DIR Comey has thoroughly reviewed 650,000 emails in 8 days? An email / second? IMPOSSIBLE RT- General Flynn (@GenFlynn) November 6, 2016Reading Wiener's own emails, those unrelated to his wife Huma or Hillary, is unlikely to be productive. Therefore, the FBI is going to filter those 650,000 Wiener emails to get at those emails that were also sent to/from Hillary and Huma.That's easy for automated tools to do. Just search the From: and To: fields for email addresses known to be used by Hillary and associates. For example, search for hdr29@hrcoffice.com (Hillary's current email address) and ha16@hillaryclinton.com (Huma Abedin's current email).Below is an example email header from the Podesta dump:From: Jennifer Palmieri Date: Sat, 2 May 2015 11:23:56 -0400Message-ID: Subject: WJC NBC interviewTo: H , John Podesta , Huma Abedin , Robby Mook , Kristina Schake This is likely to filter down the emails to a manageable few thousand.Next, filter the emails for ones already in the FBI's possession. The easiest way is using the Message-ID: header. It's a random value created for every email. If a Weiner email has the same Message-ID as an email already retrieved from Huma and Hillary, then the FBI can ignore it.This is then like to reduce the number of emails need for review to less than a thousand, or less than 100, or even all the way down to zero. And indeed, that's what NBC news is reporting:NBC's Pete Williams reports that nearly all of the e-mails found on the Weiner laptop were duplicates of e-mails FBI already reviewed.- Tom Winter (@Tom_Winter) November 6, 2016The point is is this. Computer geeks have tools that make searching the emails extremely easy. Given those emails, and a list of known email accounts from Hillary and associates, and a list of other search terms, it would take me only a few hours to do reduce the workload from 650,000 emails to only a couple hundred, which a single person can read in less than a day.The question isn't whether the FBI could review all those emails in 8 days, but why the FBI couldn't have reviewed them all in one or two days. Or even why they couldn't have reviewed them before Comey made that horrendous announcement that they were reviewing the emails.@SarahClapp @BernardKerik | ||||
| 2016-11-03 00:20:33 | In which I have to debunk a second time (lien direct) | So Slate is doubling-down on their discredited story of a secret Trump server. Tip for journalists: if you are going to argue against an expert debunking your story, try to contact that expert first, so they don't have to do what I'm going to do here, showing obvious flaws.The experts didn't find anythingThe story claims:"I spoke with many DNS experts. They found the evidence strongly suggestive of a relationship between the Trump Organization and the bank".No, you didn't. You gave experts limited information and asked them whether it's consistent with your conspiracy theory. Of course it's consistent with almost any conspiracy theory you want to concoct. What you didn't ask is for experts to try to disprove the theory.Go back and ask Chris Davis and Paul Vixie which is more credible, your version of events, or my version. I will vouch that these two are really top experts in this field, and you should trust them.This is why people quoted in the press need to go through "media training", to avoid getting your reputation harmed by bad journalists who try their best to put words in your mouth. You'll be trained to recognize bad journalists like this, and how not to get sucked into their fabrications.Jean Camp isn't an expertOn the other hand, Jean Camp isn't an expert. I've never heard of her before. She gets details wrong. Take for example in this blogpost of here's where she discusses strange lookups. Specifically, she comments on lookups for the domain mail.trump-email.com.moscow.alfaintra.net. She says:This query is unusual in that is merges two hostnames into one. It makes the most sense as a human error in inserting a new hostname in some dialog window, but neglected to hit the backspace to delete the old hostname.Uh, no. It's normal DNS behavior with non-FQDNs. If the lookup for a name fails, computers will try again, pasting the local domain on the end. In other words, when Twitter's DNS was taken offline by the DDoS attack a couple weeks ago, those monitoring DNS saw a zillion lookups for names like "www.twitter.com.example.com".I don't know what Jean Camp is an expert of, but this is sorta a basic DNS concept. It's surprising she'd get it wrong. Of course, she may be an expert in DNS who simply had a brain fart (this happens to all of us), but looking across her posts and tweets, she doesn't seem to be somebody who has a lot of experience with DNS.Call up your own IT department at Slate. Ask your IT nerds if this is how DNS operates. Note: I'm saying your average, unremarkable IT nerds can debunk an "expert" you quote in your story.There is no IP address limitationThe story repeats the theory, which I already debunked, that the server has a weird configuration that limits who can talk to it:The scientists theorized that the Trump and Alfa Bank servers had a secretive relationship after testing the behavior of mail1.trump-email.com using sites like Pingability. When they attempted to ping the site, they received the message “521 lvpmta14.lstrk.net does not accept mail from you.â€No, that's how Listrake (who is the one who actually controls the server) configures all their marketing servers. Anybody can confirm this themselves by ping all the servers in this range: | ||||
| 2016-11-01 01:58:23 | Debunking Trump\'s "secret server" (lien direct) | According to this Slate article, Trump has a secret server for communicating with Russia. Even Hillary has piled onto this story.It's time for Trump to answer serious questions about his ties to Russia. https://t.co/D8oSmyVAR4 pic.twitter.com/07dRyEmPjX- Hillary Clinton (@HillaryClinton) October 31, 2016This is nonsense. The evidence available on the Internet is that Trump neither (directly) controls the domain "trump-email.com", nor has access to the server. Instead, the domain was setup and controlled by Cendyn, a company that does marketing/promotions for hotels, including many of Trump's hotels. Cendyn outsources the email portions of its campaigns to a company called Listrak, which actually owns/operates the physical server in a data center in Philidelphia.In other words, Trump's response is (minus the political bits) likely true, supported by the evidence. It's the conclusion I came to even before seeing the response.When you view this "secret" server in context, surrounded by the other email servers operated by Listrak on behalf of Cendyn, it becomes more obvious what's going on. In the same Internet address range of Trump's servers you see a bunch of similar servers, many named [client]-email.com. In other words, trump-email.com is not intended as a normal email server you and I are familiar with, but as a server used for marketing/promotional campaigns. It's Cendyn that registered and who controls the trump-email.com domain, as seen in the WHOIS information. That the Trump Organization is the registrant, but not the admin, demonstrates that they don't have direct control over it. It's Cendyn that registered and who controls the trump-email.com domain, as seen in the WHOIS information. That the Trump Organization is the registrant, but not the admin, demonstrates that they don't have direct control over it. When the domain information was changed last September 23, it was Cendyn who did the change, not the Trump Organization. This link lists a bunch of other hotel-related domains that Cendyn likewise controls, some Trump related, some of Trump's competitors.Cendyn's claim they are reusing the server for some other purpose is likely true. If you are an enterprising journalist with $399 in your budget, you can find this out. Use the website http://reversewhois.domaintools.com/ to get a complete list of the 641 other domains controlled by Cendyn, then do an MX query for each one to find out which of them is using mail1.trump-email.com as their email server. When the domain information was changed last September 23, it was Cendyn who did the change, not the Trump Organization. This link lists a bunch of other hotel-related domains that Cendyn likewise controls, some Trump related, some of Trump's competitors.Cendyn's claim they are reusing the server for some other purpose is likely true. If you are an enterprising journalist with $399 in your budget, you can find this out. Use the website http://reversewhois.domaintools.com/ to get a complete list of the 641 other domains controlled by Cendyn, then do an MX query for each one to find out which of them is using mail1.trump-email.com as their email server. |
To see everything:
Our RSS (filtrered)
