What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-11-14 09:24:29 | NBlog November 13 - a rich seam (lien direct) |  So much of human interaction involves techniques that could legitimately be called social engineering that we're spoilt for choice on the awareness front for December. December's topic exemplifies the limitations of "cybersecurity" with its myopic focus on IT and the Internet. Social engineers bypass, undermine or totally ignore the IT route with all its tech controls, and that's partly what makes them such a formidable threat. IT may be a convenient mechanism for identifying, researching and communicating with potential victims, for putting on the appearance of legitimate, trustworthy individuals and organizations, and for administering the scams, but it's incidental to the main action: fooling the people.Maybe it's true that you can't fool all of the people all of the time, depending on precisely what is meant by 'all'. I think it's fair to say that we are all (virtually without exception) prone, predisposed or vulnerable to social engineering of one form or another. We can't help it: social interaction is genetically programmed into us and reinforced throughout our lives from the moment we're born, or even before. Some expectant mothers report their babies respond to the music and other sounds around them. A newborn baby probably recognizes its mother's and other familiar voices and sounds immediately. To what extent it trusts or could be fooled by them is a separate issue though!The idea that we are inherently vulnerable, while powerful, is only part of the story. We're also inherently capable of social engineering. We have the capacity, the tools and capabilities to influence and manipulate others to varying extents. Again, that newborn baby is sending out an avalanche of signals to humans in the area, from the moment of its first gasp and cry. The communications may be non-verbal but they are loud and clear! So much of human interaction involves techniques that could legitimately be called social engineering that we're spoilt for choice on the awareness front for December. December's topic exemplifies the limitations of "cybersecurity" with its myopic focus on IT and the Internet. Social engineers bypass, undermine or totally ignore the IT route with all its tech controls, and that's partly what makes them such a formidable threat. IT may be a convenient mechanism for identifying, researching and communicating with potential victims, for putting on the appearance of legitimate, trustworthy individuals and organizations, and for administering the scams, but it's incidental to the main action: fooling the people.Maybe it's true that you can't fool all of the people all of the time, depending on precisely what is meant by 'all'. I think it's fair to say that we are all (virtually without exception) prone, predisposed or vulnerable to social engineering of one form or another. We can't help it: social interaction is genetically programmed into us and reinforced throughout our lives from the moment we're born, or even before. Some expectant mothers report their babies respond to the music and other sounds around them. A newborn baby probably recognizes its mother's and other familiar voices and sounds immediately. To what extent it trusts or could be fooled by them is a separate issue though!The idea that we are inherently vulnerable, while powerful, is only part of the story. We're also inherently capable of social engineering. We have the capacity, the tools and capabilities to influence and manipulate others to varying extents. Again, that newborn baby is sending out an avalanche of signals to humans in the area, from the moment of its first gasp and cry. The communications may be non-verbal but they are loud and clear! |
||||
| 2017-11-10 16:37:41 | NBlog November 10 - one step at a time (lien direct) | 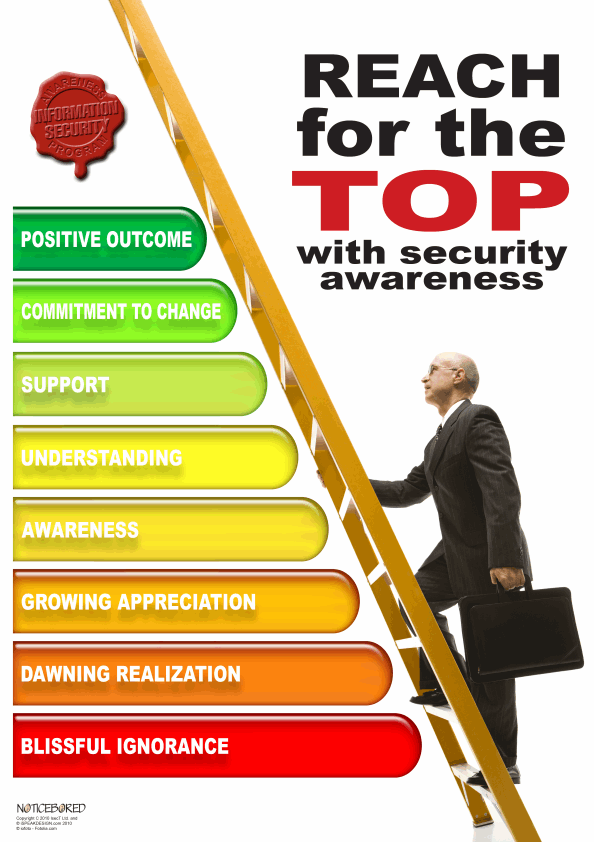 This colorful image popped onto my screen as I searched our stash of security awareness content for social engineering-related graphics. It's a simple but striking visual expression of the concept that security awareness is not the ultimate goal, but an important step on the way towards achieving a positive outcome for the organization. A major part of the art of raising awareness in any area is actively engaging with people in such a way that they think and behave differently as a result of the awareness activities. For some people, providing cold, hard, factual information may be all it takes, which even the most basic awareness programs aim to do. That's not enough for the majority though: most of us need things to be explained to us in terms that resonate and motivate us to respond in some fashion. In physical terms, we need to overcome inertia. In biology, we need to break bad habits to form better ones.Social engineering is a particular challenge for awareness since scammers, fraudsters and other social engineers actively exploit our lack of awareness or (if that fails) subvert the very security mechanisms we put in place. "Your password has expired: pick a new one now to avoid losing access to your account!" is a classic example used by many a phisher. It hinges on tricking victims into accepting the premise (password expired) at face value and taking the easy option, clicking a link that leads them to the phisher's lair while thinking they are going to a legitimate password-change function. Our raising awareness of the need to choose strong passwords may be counterproductive if employees unwittingly associate phishing messages with user authentication and security!Part of our awareness approach in December's NoticeBored materials on social engineering will be to hook-in to our natural tendency to notice something amiss, something strange and different. Humans are strong at spotting patterns at a subconscious level. For instance, did you even notice the gradation from red to green on the ladder image? That was a deliberate choice in designing the image, a fairly crude and obvious example ... once it has been pointed out anyway! See if you can spot the other, more subtle visual cues (and by all means email me to see what you missed!). This colorful image popped onto my screen as I searched our stash of security awareness content for social engineering-related graphics. It's a simple but striking visual expression of the concept that security awareness is not the ultimate goal, but an important step on the way towards achieving a positive outcome for the organization. A major part of the art of raising awareness in any area is actively engaging with people in such a way that they think and behave differently as a result of the awareness activities. For some people, providing cold, hard, factual information may be all it takes, which even the most basic awareness programs aim to do. That's not enough for the majority though: most of us need things to be explained to us in terms that resonate and motivate us to respond in some fashion. In physical terms, we need to overcome inertia. In biology, we need to break bad habits to form better ones.Social engineering is a particular challenge for awareness since scammers, fraudsters and other social engineers actively exploit our lack of awareness or (if that fails) subvert the very security mechanisms we put in place. "Your password has expired: pick a new one now to avoid losing access to your account!" is a classic example used by many a phisher. It hinges on tricking victims into accepting the premise (password expired) at face value and taking the easy option, clicking a link that leads them to the phisher's lair while thinking they are going to a legitimate password-change function. Our raising awareness of the need to choose strong passwords may be counterproductive if employees unwittingly associate phishing messages with user authentication and security!Part of our awareness approach in December's NoticeBored materials on social engineering will be to hook-in to our natural tendency to notice something amiss, something strange and different. Humans are strong at spotting patterns at a subconscious level. For instance, did you even notice the gradation from red to green on the ladder image? That was a deliberate choice in designing the image, a fairly crude and obvious example ... once it has been pointed out anyway! See if you can spot the other, more subtle visual cues (and by all means email me to see what you missed!). |
Guideline | |||
| 2017-11-07 18:38:07 | NBlog November 7 - pipes and bikes (lien direct) | The past few days have been very successful. Yesterday, at last, I fixed the water pipe feeding water to the stock tanks in the nick of time before the animals went thirsty, a mammoth job for this long-time office worker (!). The pipe is an old galvanized steel pipe, laid when this was a working farm, well before it became a pine forest. An ancient Lister diesel engine and piston pump sends water in two directions, either to the house tanks or to the stock tanks. The house line was fine, luckily but the stock line wasn't, and evidently hadn't been maintained in a long time. Just getting to the start of the line across the stream was a mission with a 60 degree muddy incline going up about 8m, then a strip of native bush, then the pines ... which had been toppled by a cyclone back in April. What would once have been just forest is now a forest clearing with a few hundred near full-sized trees laying on the ground, toppled like the matchsticks some of them were destined to become. Spurred on by the falling firs, the vicious NZ bramble seized the opportunity to flourish in the Spring sunshine, forming man-eating bramble patches a few metres high and several metres across the hillside. Here's the easy bit at the bottom of the hill after a day or two's clambering, de-brambling and chainsawing ... |
||||
| 2017-11-03 09:35:50 | NBlog November 3 - audit sampling (LONG) (lien direct) | [This piece was stimulated by a question on the ISO27k Forum about ISO27k certification auditors checking information security controls, and a response about compliance audit requirements. It's a backgrounder, an essay or a rant if you like. Feel free to skip it, or wait until you have a spare 10 mins, a strong coffee and the urge to read and think on!]“Sampling†is an important concept in both auditing and science. Sampling (i.e. selecting a sample of a set or population for review) is necessary because under most circumstances it is practically impossible to assess every single member – in fact it is often uncertain how many items belong to the set, where they are, what state they are in etc. There is often lots of uncertainty.For example, imagine an auditor needs to check an organization's “information security policies†in connection with an internal audit or certification/compliance audit.  Some organizations make that quite easy by having a policy library or manual or database, typically a single place on the intranet where all the official corporate policies exist and are maintained and controlled as a suite. In a large/diverse organization there may be hundreds of policies, thousands if you include procedures and guidelines and work instructions and forms and so forth. Some of them may be tagged or organized under an “information security†heading, so the auditor can simply work down that list … but almost straight away he/she will run into the issue that information security is part of information risk is part of risk, and information security management is part of risk management is part of management, hence there should be lots of cross-references to other kinds of policy. A “privacy policyâ€, for instance, may well refer to policies on identification and authentication, access control, encryption etc. (within the information security domain) plus other policies in areas such as accountability, compliance, awareness and training, incident management etc. which may or may not fall outside the information security domain depending on how it is defined, plus applicable privacy-related laws and regulations, plus contracts and agreements (e.g.nondisclosure agreements) … hence the auditor could potentially end up attempting to audit the entire corporate policy suite and beyond! In practice, that's not going to happen. Some organizations make that quite easy by having a policy library or manual or database, typically a single place on the intranet where all the official corporate policies exist and are maintained and controlled as a suite. In a large/diverse organization there may be hundreds of policies, thousands if you include procedures and guidelines and work instructions and forms and so forth. Some of them may be tagged or organized under an “information security†heading, so the auditor can simply work down that list … but almost straight away he/she will run into the issue that information security is part of information risk is part of risk, and information security management is part of risk management is part of management, hence there should be lots of cross-references to other kinds of policy. A “privacy policyâ€, for instance, may well refer to policies on identification and authentication, access control, encryption etc. (within the information security domain) plus other policies in areas such as accountability, compliance, awareness and training, incident management etc. which may or may not fall outside the information security domain depending on how it is defined, plus applicable privacy-related laws and regulations, plus contracts and agreements (e.g.nondisclosure agreements) … hence the auditor could potentially end up attempting to audit the entire corporate policy suite and beyond! In practice, that's not going to happen. |
Guideline | |||
| 2017-11-02 10:01:10 | NBlog November 1 - privacy & GDPR update (lien direct) | We have revised and re-issued the privacy awareness module with a particular focus on the General Data Protection Regulation this time around. GDPR is a major shake-up in European privacy laws with global implications. Does your organization know what's coming? Do you understand the implications? Will you (your employees, IT systems, policies, procedures and websites) plus your suppliers and business partners, be ready by May 2018? One of six new high-res poster imagesprovided in November's NoticeBored moduleBringing workers up to speed on privacy through awareness and training is an essential part of business for all organizations. Persuading everyone to take care of the personal information they handle means more than just informing them about their compliance obligations: they need to be sufficiently motivated to change their ways.The break-glass poster is meant to catch the eye and make people think. It's not literal, of course, but every organization should have a suitable process in place to handle reporting of privacy breaches plus other incidents and near-misses. Encouraging people to report issues is one of the objectives of the awareness materials. The 3-day breach reporting deadline under GDPR will be challenging even for organizations that have a strong approach to privacy. For those with low awareness, it may prove impossible.Taking that idea a step further, in addition to poster graphics, NoticeBored subscribers have the benefit of seminar slide-decks and briefings, FAQs, policy and procedure templates and the usual range of goodies designed to make it easy to raise awareness in this important area. It's basically a privacy and GDPR awareness kit.So what about you? What are you doing in the way of awareness on privacy, GDPR and compliance? If awareness is just another thing on your lengthy to-do list, get in touch, preferably well before May 25th 2018 - urgently if your organization is blissfully unaware of what's coming. Management-level awareness is the key to making stuff happen. Let us help you with that. One of six new high-res poster imagesprovided in November's NoticeBored moduleBringing workers up to speed on privacy through awareness and training is an essential part of business for all organizations. Persuading everyone to take care of the personal information they handle means more than just informing them about their compliance obligations: they need to be sufficiently motivated to change their ways.The break-glass poster is meant to catch the eye and make people think. It's not literal, of course, but every organization should have a suitable process in place to handle reporting of privacy breaches plus other incidents and near-misses. Encouraging people to report issues is one of the objectives of the awareness materials. The 3-day breach reporting deadline under GDPR will be challenging even for organizations that have a strong approach to privacy. For those with low awareness, it may prove impossible.Taking that idea a step further, in addition to poster graphics, NoticeBored subscribers have the benefit of seminar slide-decks and briefings, FAQs, policy and procedure templates and the usual range of goodies designed to make it easy to raise awareness in this important area. It's basically a privacy and GDPR awareness kit.So what about you? What are you doing in the way of awareness on privacy, GDPR and compliance? If awareness is just another thing on your lengthy to-do list, get in touch, preferably well before May 25th 2018 - urgently if your organization is blissfully unaware of what's coming. Management-level awareness is the key to making stuff happen. Let us help you with that. |
||||
| 2017-10-31 13:48:56 | NBlog October 31 - spooky happenings in NZ (lien direct) |  Last night as darkness draped itself across the IsecT office, an eerie silence descended. No more tippy tappy on the keyboards, the writing finished, our job almost done for another month - the end of another chapter. A fantastic horror/thriller on the movie channel delivered the perfect stress antidote, a different kind of tension entirely. More poppycocck than Hitchcock but fun nevertheless.Today we've packaged up November's privacy awareness materials, just under 100 megs of it, ready to deliver to our subscribers, and updated the website with details of the new module. My energy sapped, even strong coffee has lost its potency. It's time for a break! I'll have a bit more to say about the module tomorrow, if I evade the demons and survive the night that is. Last night as darkness draped itself across the IsecT office, an eerie silence descended. No more tippy tappy on the keyboards, the writing finished, our job almost done for another month - the end of another chapter. A fantastic horror/thriller on the movie channel delivered the perfect stress antidote, a different kind of tension entirely. More poppycocck than Hitchcock but fun nevertheless.Today we've packaged up November's privacy awareness materials, just under 100 megs of it, ready to deliver to our subscribers, and updated the website with details of the new module. My energy sapped, even strong coffee has lost its potency. It's time for a break! I'll have a bit more to say about the module tomorrow, if I evade the demons and survive the night that is. |
||||
| 2017-10-30 15:59:25 | NBlog October 30 - polish til it gleams (lien direct) |  Today we're busy finalizing the privacy awareness materials for delivery to subscribers imminently. It is always a bit fraught at this time of the month as the deadline looms but things are going well this time around - no IT hardware failures or other crises at least. The new materials are proofread and gleaming, ready to package up and upload as soon as the poster graphics come in. I even managed a few hours off yesterday to visit friends at the radio club. Luxury!We'll have a bit of a break before starting the next awareness module on social engineering, long enough hopefully to repair a broken pipe supplying water for the animals. I've been patiently chainsawing fallen pine trees out of the way for some while now, finding three breaks in the pipe so far. The stock water tanks have nearly run dry so it's a priority to fix the breaks, pump the water and finish the job. Our contingency plans involve carting water around in portable containers or getting a tanker delivery direct to the tanks, not exactly ideal with temperatures starting to climb towards summer, and a pregnant 'house cow' due to give birth any day now. We'll update the NoticeBored website soon too with details of the privacy module, taking the opportunity to make a few other changes while we're at it. I need to update ISO27001security.com as well, incorporating some additional materials kindly donated for the ISO27k Toolkit. It's all systems go here! Today we're busy finalizing the privacy awareness materials for delivery to subscribers imminently. It is always a bit fraught at this time of the month as the deadline looms but things are going well this time around - no IT hardware failures or other crises at least. The new materials are proofread and gleaming, ready to package up and upload as soon as the poster graphics come in. I even managed a few hours off yesterday to visit friends at the radio club. Luxury!We'll have a bit of a break before starting the next awareness module on social engineering, long enough hopefully to repair a broken pipe supplying water for the animals. I've been patiently chainsawing fallen pine trees out of the way for some while now, finding three breaks in the pipe so far. The stock water tanks have nearly run dry so it's a priority to fix the breaks, pump the water and finish the job. Our contingency plans involve carting water around in portable containers or getting a tanker delivery direct to the tanks, not exactly ideal with temperatures starting to climb towards summer, and a pregnant 'house cow' due to give birth any day now. We'll update the NoticeBored website soon too with details of the privacy module, taking the opportunity to make a few other changes while we're at it. I need to update ISO27001security.com as well, incorporating some additional materials kindly donated for the ISO27k Toolkit. It's all systems go here! |
||||
| 2017-10-29 11:54:31 | NBlog October 29 - peddling personal data (lien direct) |  Earlier this month, I blogged about personal data being valuable and hence worth protecting like any asset. But what about commercial exploitation such as selling it to third parties? Is that OK too?Some companies find it perfectly acceptable to Hoover-up all the personal information they can to use or sell to third parties, whereas others take a more conservative and (to my mind) ethical position, limiting personal data collection, using it for necessary internal business activities and refusing to sell or disclose it further (not even to the authorities in the case of Apple). The EU position on this is clear: personal information belongs to the people, not the corporations. Since privacy is a fundamental human right, people must retain control over their personal information, including the ability to limit its collection, accuracy, use and disclosure. The US position is ambiguous, at best. Efforts to tighten-up US laws around privacy and surveillance have been lackluster so far, often being stalled or knocked back by those same tech companies that are busy profiting from personal information, or by the spooks.With the battle lines drawn up, once GDPR comes into effect next May the charge is on. Privacy and unrestricted commercial exploitation of personal information are essentially incompatible, so something has to give. We've already witnessed the failure of a half-baked attempt at self-regulation (Safe Harbor) and it seems Privacy Shield is also faltering. What next?One possibility is a commercial response, where organizations increasingly decline doing business with US corporations that openly exploit and fail to protect personal information. That, coupled with the massive fines under GDPR, might finally drive home the message where it hurts them most: the bottom line. As Rana Foroohar from the Financial Times puts it "Privacy is a competitive advantage. Technology co Earlier this month, I blogged about personal data being valuable and hence worth protecting like any asset. But what about commercial exploitation such as selling it to third parties? Is that OK too?Some companies find it perfectly acceptable to Hoover-up all the personal information they can to use or sell to third parties, whereas others take a more conservative and (to my mind) ethical position, limiting personal data collection, using it for necessary internal business activities and refusing to sell or disclose it further (not even to the authorities in the case of Apple). The EU position on this is clear: personal information belongs to the people, not the corporations. Since privacy is a fundamental human right, people must retain control over their personal information, including the ability to limit its collection, accuracy, use and disclosure. The US position is ambiguous, at best. Efforts to tighten-up US laws around privacy and surveillance have been lackluster so far, often being stalled or knocked back by those same tech companies that are busy profiting from personal information, or by the spooks.With the battle lines drawn up, once GDPR comes into effect next May the charge is on. Privacy and unrestricted commercial exploitation of personal information are essentially incompatible, so something has to give. We've already witnessed the failure of a half-baked attempt at self-regulation (Safe Harbor) and it seems Privacy Shield is also faltering. What next?One possibility is a commercial response, where organizations increasingly decline doing business with US corporations that openly exploit and fail to protect personal information. That, coupled with the massive fines under GDPR, might finally drive home the message where it hurts them most: the bottom line. As Rana Foroohar from the Financial Times puts it "Privacy is a competitive advantage. Technology co |
||||
| 2017-10-27 15:57:11 | NBlog October 27 - Equifax cultural issues (lien direct) |   Motherboard reveals a catalog of issues and failings within Equifax that seem likely to have contributed to, or patently failed to prevent, May's breach of sensitive personal information on over 145 million Americans, almost half the population.Although we'll be using the Equifax breach to illustrate November's awareness materials on privacy, we could equally have used them in this month's module on security culture since, according to BoingBoing:"Motherboard's Lorenzo Franceschi-Bicchierai spoke to several Equifax sources who described a culture of IT negligence and neglect, in which security audits and warnings were routinely disregarded, and where IT staff were unable to believe that their employers were so cavalier with the sensitive data the company had amassed."'A culture of IT negligence and neglect' is almost the opposite of a security culture, more of a toxic culture you could say. Workers who simply don't give a stuff about information security or privacy are hardly likely to lift a finger if someone reports issues to them, especially if (as seems likely) senior managers are complicit, perhaps even the source of the toxin. Their lack of support, leadership, prioritization and resourcing for the activities necessary to identify and address information risks makes it hard for professionals, staff members and even management Motherboard reveals a catalog of issues and failings within Equifax that seem likely to have contributed to, or patently failed to prevent, May's breach of sensitive personal information on over 145 million Americans, almost half the population.Although we'll be using the Equifax breach to illustrate November's awareness materials on privacy, we could equally have used them in this month's module on security culture since, according to BoingBoing:"Motherboard's Lorenzo Franceschi-Bicchierai spoke to several Equifax sources who described a culture of IT negligence and neglect, in which security audits and warnings were routinely disregarded, and where IT staff were unable to believe that their employers were so cavalier with the sensitive data the company had amassed."'A culture of IT negligence and neglect' is almost the opposite of a security culture, more of a toxic culture you could say. Workers who simply don't give a stuff about information security or privacy are hardly likely to lift a finger if someone reports issues to them, especially if (as seems likely) senior managers are complicit, perhaps even the source of the toxin. Their lack of support, leadership, prioritization and resourcing for the activities necessary to identify and address information risks makes it hard for professionals, staff members and even management |
Guideline | Equifax | ||
| 2017-10-20 21:01:04 | NBlog October 20 - privacy & personal choice (lien direct) |  Control is at the core of privacy - not just information security controls but a person's control over personal information about themselves, and their self-control. It's fundamentally a matter of choice, whether or not to disclose our personal information, when, to whom, and how it is to be used and secured ... which presents a conundrum for those of us who choose to use social media, cellphones, email, the web and so on - the chattering classes.Every time I update this very blog (and sometimes even when I don't!), I'm revealing a bit more about myself. As with my body language, the way I express things may be as telling as the literal content. In the midst of writing the security awareness materials on privacy, I'm especially conscious of that aspect right now so I'm being extra careful about what I say here and (to some extent) how I say it ... but I'm only human. There are limits to my ability to control myself. Those of you who have been tracking and reading this blog for a while now could probably identify my style of writing, pointing out characteristics that have caught your eye, both good points and bad. I'm talking (well writing!) about metadata gleaned from this blog and perhaps other sources that tells you it's probably me at the keyboard - things such as:My choice of language, vocabulary and grammar, doubtless including spelling and grammatical errors, inconsistencies and quirks some of which I am probably not aware of, and others perhaps deliberate;My phrasing, sentence and paragraph structure, sentence length, word length; My use of punctuation, parenthesis, ellipses, bullet points, CaPiTaLs, abbreviations etc. (and, yes, italicising non-English words and abbreviations is a habit I picked up decades ago in the science labs);The way I quote, cite and reference sources, paying respect to those whose efforts I draw upon (the scientific approach, again);Idioms and turns-of-phrase, ways of expressing things that hint at my cultural background and gram Control is at the core of privacy - not just information security controls but a person's control over personal information about themselves, and their self-control. It's fundamentally a matter of choice, whether or not to disclose our personal information, when, to whom, and how it is to be used and secured ... which presents a conundrum for those of us who choose to use social media, cellphones, email, the web and so on - the chattering classes.Every time I update this very blog (and sometimes even when I don't!), I'm revealing a bit more about myself. As with my body language, the way I express things may be as telling as the literal content. In the midst of writing the security awareness materials on privacy, I'm especially conscious of that aspect right now so I'm being extra careful about what I say here and (to some extent) how I say it ... but I'm only human. There are limits to my ability to control myself. Those of you who have been tracking and reading this blog for a while now could probably identify my style of writing, pointing out characteristics that have caught your eye, both good points and bad. I'm talking (well writing!) about metadata gleaned from this blog and perhaps other sources that tells you it's probably me at the keyboard - things such as:My choice of language, vocabulary and grammar, doubtless including spelling and grammatical errors, inconsistencies and quirks some of which I am probably not aware of, and others perhaps deliberate;My phrasing, sentence and paragraph structure, sentence length, word length; My use of punctuation, parenthesis, ellipses, bullet points, CaPiTaLs, abbreviations etc. (and, yes, italicising non-English words and abbreviations is a habit I picked up decades ago in the science labs);The way I quote, cite and reference sources, paying respect to those whose efforts I draw upon (the scientific approach, again);Idioms and turns-of-phrase, ways of expressing things that hint at my cultural background and gram |
||||
| 2017-10-16 18:37:18 | NBlog October 16 - is privacy a lost cause? (lien direct) |  Today I've been thinking and writing about privacy risks, comparing the differing perspectives of individual people and organizations.Something that stands out from the risk analysis is that, despite journalists, authorities, privacy pro's and victims being aghast when privacy breaches occur, we all gladly accept significant privacy risks as a matter of course. In a few cases (e.g. tax), we have virtually no choice in the matter, but mostly we choose to share our personal information, trusting that the recipients will protect it on our behalf.To be honest, privacy doesn't even enter our minds most of the time. It doesn't occur to us, because of our blase attitudes.Admittedly, it would take extreme measures to be reasonably assured of complete privacy, and even then there would still be risks: consider people in 'witness protection schemes' for example, or moles, spies, criminals and terrorists doing their level best to remain anonymous, below the radar. We know they don't always succeed.Extremists aside, ordinary people like you and me mostly pay scant attention to our privacy. We use the Internet, and cellphones, and all manner of government and commercial services either under our own names, or with superficial efforts to conceal our identities. We share or post selfies online, email and text others, and wander about in public spaces under the full gaze of myriad CCTV cameras. We use our credit and debit cards to buy stuff, register for various services, and generally anticipate nothing untoward ... which in turn places even more pressure on the organizations and individuals to whom we disclose our personal information, hence the reason that privacy laws such as GDPR are so important in a societal sense.Attitudes have changed markedly within a generation or three. Way back when I was a naive young lad, the very concept of taking, let alone sharing explicit selfies was alien to me. Porn was available, of course, but access was discreet, guilt-ridden and exceptional, despite the raging hormones. As Victorian values have relaxed, we've been through "free love", page 3 girls, Hugh Heffner, tolerated or legalized prostitution, gay rights and other largely sexual revolutions - in most Western nations anyway: clearly there are cultural discrepancies with distinct differences of opinion o Today I've been thinking and writing about privacy risks, comparing the differing perspectives of individual people and organizations.Something that stands out from the risk analysis is that, despite journalists, authorities, privacy pro's and victims being aghast when privacy breaches occur, we all gladly accept significant privacy risks as a matter of course. In a few cases (e.g. tax), we have virtually no choice in the matter, but mostly we choose to share our personal information, trusting that the recipients will protect it on our behalf.To be honest, privacy doesn't even enter our minds most of the time. It doesn't occur to us, because of our blase attitudes.Admittedly, it would take extreme measures to be reasonably assured of complete privacy, and even then there would still be risks: consider people in 'witness protection schemes' for example, or moles, spies, criminals and terrorists doing their level best to remain anonymous, below the radar. We know they don't always succeed.Extremists aside, ordinary people like you and me mostly pay scant attention to our privacy. We use the Internet, and cellphones, and all manner of government and commercial services either under our own names, or with superficial efforts to conceal our identities. We share or post selfies online, email and text others, and wander about in public spaces under the full gaze of myriad CCTV cameras. We use our credit and debit cards to buy stuff, register for various services, and generally anticipate nothing untoward ... which in turn places even more pressure on the organizations and individuals to whom we disclose our personal information, hence the reason that privacy laws such as GDPR are so important in a societal sense.Attitudes have changed markedly within a generation or three. Way back when I was a naive young lad, the very concept of taking, let alone sharing explicit selfies was alien to me. Porn was available, of course, but access was discreet, guilt-ridden and exceptional, despite the raging hormones. As Victorian values have relaxed, we've been through "free love", page 3 girls, Hugh Heffner, tolerated or legalized prostitution, gay rights and other largely sexual revolutions - in most Western nations anyway: clearly there are cultural discrepancies with distinct differences of opinion o |
||||
| 2017-10-14 09:00:24 | NBlog October 14 - a different tack (lien direct) |  There are several good reasons for protecting personal information, of which compliance with privacy laws and regulations is just one. For example, personal information can be extremely valuable in its own right - a business asset in fact. Consider the adverse consequences of personal information being lost or corrupted, perhaps the result of a system/hardware failure, a software bug, an inept or malicious system administrator, malware, ransomware or .... well anything that can damage/destroy or deny legitimate access to information could of course affect personal information. In a sense, it is "just" information. At the same time, its commercial value is strongly linked to its confidentiality. This is why we are invited to pay $thousands for various mailing lists, offers which we either ignore or robustly decline since we are strongly ethical and most certainly not spammers! It's why sales professionals jealously guard their personal contacts. They are truly concerned about identity theft, as opposed to identity fraud. Treating personal information as a business asset worth protecting and exploiting puts an unusual slant on privacy. In particular, it emphasizes the commercial value of controls securing personal information, beyond the begrudging 'avoidance of fines' angle. It's also, I believe, a way to increase the pressure on senior management to do what needs to be done in order to secure personal information, even if they are not that fussed about privacy laws - a carrot-and-stick approach.We'll expand on this and other good reasons to take privacy seriously in November's awareness module. There are several good reasons for protecting personal information, of which compliance with privacy laws and regulations is just one. For example, personal information can be extremely valuable in its own right - a business asset in fact. Consider the adverse consequences of personal information being lost or corrupted, perhaps the result of a system/hardware failure, a software bug, an inept or malicious system administrator, malware, ransomware or .... well anything that can damage/destroy or deny legitimate access to information could of course affect personal information. In a sense, it is "just" information. At the same time, its commercial value is strongly linked to its confidentiality. This is why we are invited to pay $thousands for various mailing lists, offers which we either ignore or robustly decline since we are strongly ethical and most certainly not spammers! It's why sales professionals jealously guard their personal contacts. They are truly concerned about identity theft, as opposed to identity fraud. Treating personal information as a business asset worth protecting and exploiting puts an unusual slant on privacy. In particular, it emphasizes the commercial value of controls securing personal information, beyond the begrudging 'avoidance of fines' angle. It's also, I believe, a way to increase the pressure on senior management to do what needs to be done in order to secure personal information, even if they are not that fussed about privacy laws - a carrot-and-stick approach.We'll expand on this and other good reasons to take privacy seriously in November's awareness module. |
||||
| 2017-10-13 10:09:20 | NBlog October 13 - data breach reality check (lien direct) | In searching for information relating to GDPR and privacy for next month's awareness module, I bumped into the Business Continuity Institute's Horizon Scan 2017 report.The report's headline data come from a survey of 666 business continuity and risk management professionals from Europe and North America (mostly), concerning their perceptions about threats and incidents ... and immediately a few issues spring out at me.First of all, the survey population is naturally biased given their field of expertise: although sizable, this was clearly not a random sample. As with all professionals, they probably overemphasize the things that matter most to them, meaning serious incidents that actually or are believed to threaten to disrupt their organizations. It's no surprise at all that 88% of BC pro's are concerned or extremely concerned about "cyber attack" - if anything, I wonder what planet the remaining 12% inhabit! On the other hand, BC pro's ought to know what they are talking about, so their opinions are credible ... just not as much as hard, factual data concerning the actual incidents.On that score, this year's report provides information on actual incidents:"A new metric introduced in the BCI Horizon Scan Report measures actual disruption levels caused by the threats listed in figure 1 in order to provide a comparison against organizations' concerns. Figure 2 shows a contrast between the levels of disruption caused by a particular threat and how concerned an organization is about it. The study shows the actual causes of business disruption slightly differ from the threats practitioners list as significant concerns. The top causes of business disruption according to the same respondents include unplanned IT and telecommunications outages (72%), adverse weather (43%), interruption to utility supply (40%), cyber attacks (35%) and security incidents (24%)."The discrepancy between BC pros' perceptions and reality is quite marked. I'll come back to that in a moment.Second, the way incidents (and/or threats - the report is somewhat ambiguous over the difference) are described puzzles me. Here are the top 7, ranked according to the proportion of respondents who claimed to be "extremely concerned":Cyber attack (e.g. malware, denial of service) Data breach (i.e. loss or theft of confidential information) Unplanned IT and telecom outages Security incident (e.g. vandalism, theft, fraud, protest) | ||||
| 2017-10-07 07:37:18 | NBlog October 7 - privacy update (lien direct) |  This month we are updating the privacy awareness module for delivery in November, with a particular focus on GDPR just six months away. By the time it comes into force in May 2018, compliance with the EU General Data Protection Regulation will be a strategic objective for most organizations, thanks to the potential for massive fines and adverse publicity for any who are caught in contravention. Provided they are aware of it, we believe managers will welcome assurance either that everything is on track to make the organization compliant by the deadline, or that GDPR is definitely not applicable to them. Our job is to make managers aware of GDPR, emphasizing the governance and compliance plus information risk and security management aspects - updating corporate privacy policies for example, and ensuring that suppliers and business partners are on-track as well as the organization itself. If cloud service providers were struggling to meet the compliance deadline, for instance, there would be implications for their customers - another thing for management to consider. A GDPR compliance checklist would therefore be a worthwhile and timely addition to the NoticeBored materials.The task of achieving GDPR compliance largely falls to IT and compliance specialists. Our awareness objectives for that audience are more tactical in nature, relating to project management, technical challenges and change management. The compliance checklist may help them consider the compliance project status from management's perspective, perhaps re-prioritizing and re-energizing the remaining activities.For the general worker awareness audience, we plan to tackle the personal angle, addressing rhetorical questions such as "What's all the fuss?", "What's GDPR?" and "What's in it for me?" ... suggesting three awareness posters similar to the one above. We'll be developing those and other ideas into a brief for the graphics team this weekend.GD This month we are updating the privacy awareness module for delivery in November, with a particular focus on GDPR just six months away. By the time it comes into force in May 2018, compliance with the EU General Data Protection Regulation will be a strategic objective for most organizations, thanks to the potential for massive fines and adverse publicity for any who are caught in contravention. Provided they are aware of it, we believe managers will welcome assurance either that everything is on track to make the organization compliant by the deadline, or that GDPR is definitely not applicable to them. Our job is to make managers aware of GDPR, emphasizing the governance and compliance plus information risk and security management aspects - updating corporate privacy policies for example, and ensuring that suppliers and business partners are on-track as well as the organization itself. If cloud service providers were struggling to meet the compliance deadline, for instance, there would be implications for their customers - another thing for management to consider. A GDPR compliance checklist would therefore be a worthwhile and timely addition to the NoticeBored materials.The task of achieving GDPR compliance largely falls to IT and compliance specialists. Our awareness objectives for that audience are more tactical in nature, relating to project management, technical challenges and change management. The compliance checklist may help them consider the compliance project status from management's perspective, perhaps re-prioritizing and re-energizing the remaining activities.For the general worker awareness audience, we plan to tackle the personal angle, addressing rhetorical questions such as "What's all the fuss?", "What's GDPR?" and "What's in it for me?" ... suggesting three awareness posters similar to the one above. We'll be developing those and other ideas into a brief for the graphics team this weekend.GD |
||||
| 2017-10-02 10:51:19 | NBlog October 2 - a 2-phase approach to bolster the security culture (lien direct) |  We've just updated the NoticeBored website to describe the new awareness module on security culture and delivered the latest batch of security awareness materials to subscribers. Culture is a nebulous, hand-waving concept, hard to pin down and yet an important, far-reaching factor in any organization. The new module (the 63rd topic in our bulging security awareness portfolio) is essentially a recruitment drive, aimed at persuading workers to join and become integral parts of the Information Security function. The basic idea is straightforward in theory but in practice it is a challenge to get people to sit up and take notice, then to change their attitudes and behaviors. During September, we developed a two-phased approach:Strong leadership is critically important which means first convincing management (all the way up to the exec team and Board) that they are the lynch-pins. In setting the tone at the top, the way managers treat information risk, security, privacy, compliance and related issues has a marked effect on the entire organization. Their leverage is enormous, with the potential to enable or undermine the entire approach, as illustrated by the Enron, Sony and Equifax incidents.With management support in the bag, the next task is to persuade workers in general to participate actively in the organization's information security arrangements. Aside from directly appealing to staff on a personal level, we enlist the help of professionals and specialists since they too are a powerful influence on the organization - including management. October's awareness materials follow hot on the heels of the revised Information Security 101 module delivered in September. That set the scene, positioning information security as an essential part of modern business. Future modules will expand on different aspects, each one reinforcing the fundamentals ... which is part of the process of enhancing the security cu We've just updated the NoticeBored website to describe the new awareness module on security culture and delivered the latest batch of security awareness materials to subscribers. Culture is a nebulous, hand-waving concept, hard to pin down and yet an important, far-reaching factor in any organization. The new module (the 63rd topic in our bulging security awareness portfolio) is essentially a recruitment drive, aimed at persuading workers to join and become integral parts of the Information Security function. The basic idea is straightforward in theory but in practice it is a challenge to get people to sit up and take notice, then to change their attitudes and behaviors. During September, we developed a two-phased approach:Strong leadership is critically important which means first convincing management (all the way up to the exec team and Board) that they are the lynch-pins. In setting the tone at the top, the way managers treat information risk, security, privacy, compliance and related issues has a marked effect on the entire organization. Their leverage is enormous, with the potential to enable or undermine the entire approach, as illustrated by the Enron, Sony and Equifax incidents.With management support in the bag, the next task is to persuade workers in general to participate actively in the organization's information security arrangements. Aside from directly appealing to staff on a personal level, we enlist the help of professionals and specialists since they too are a powerful influence on the organization - including management. October's awareness materials follow hot on the heels of the revised Information Security 101 module delivered in September. That set the scene, positioning information security as an essential part of modern business. Future modules will expand on different aspects, each one reinforcing the fundamentals ... which is part of the process of enhancing the security cu |
Guideline | Equifax | ||
| 2017-10-01 20:32:41 | NBlog October 1 - security culture module (lien direct) |  Well, despite Finagle's Law, we've limped home over the finishing line. Another tidy stack of NoticeBored security awareness content is packaged up and will shortly be ready for our subscribers to download, customize and deploy.'Security culture' is the 63rd awareness topic we've covered, among the most challenging module to develop and yet also the most rewarding: it's clear, in retrospect, what an important topic this is for any organization that takes information security seriously enough to run an awareness program. In short, there is no better mechanism than an effective security awareness program with which to foster a security culture. How on Earth have we ducked the issue for so long? Perhaps it's a maturity thing. Perhaps it's cultural: we are forging new paths, heading way off the track well-beaten by more conventional security awareness programs. Just in case you missed it, there's so much more tosecurity awareness than phishing!I pity organizations that rely solely on their security and privacy policies. 'Laying down the law' is undoubtedly an important part of the process, necessary but not sufficient. If it were, speed limit signs coupled with the threat of prosecution would have long since curbed driving incidents: we'd be left dealing with genuine accidents, mechanical failures and so forth, but excess speed would hardly ever be an issue. Patently, it is not ... and that's despite the parallel investment in awareness, training and education. It doesn't take much to imagine the carnage on our roads if 'laying down the law' was all that happened. Well, despite Finagle's Law, we've limped home over the finishing line. Another tidy stack of NoticeBored security awareness content is packaged up and will shortly be ready for our subscribers to download, customize and deploy.'Security culture' is the 63rd awareness topic we've covered, among the most challenging module to develop and yet also the most rewarding: it's clear, in retrospect, what an important topic this is for any organization that takes information security seriously enough to run an awareness program. In short, there is no better mechanism than an effective security awareness program with which to foster a security culture. How on Earth have we ducked the issue for so long? Perhaps it's a maturity thing. Perhaps it's cultural: we are forging new paths, heading way off the track well-beaten by more conventional security awareness programs. Just in case you missed it, there's so much more tosecurity awareness than phishing!I pity organizations that rely solely on their security and privacy policies. 'Laying down the law' is undoubtedly an important part of the process, necessary but not sufficient. If it were, speed limit signs coupled with the threat of prosecution would have long since curbed driving incidents: we'd be left dealing with genuine accidents, mechanical failures and so forth, but excess speed would hardly ever be an issue. Patently, it is not ... and that's despite the parallel investment in awareness, training and education. It doesn't take much to imagine the carnage on our roads if 'laying down the law' was all that happened. |
Equifax | |||
| 2017-09-30 22:12:42 | NBlog September 30 - complying with Finagle\'s Law (lien direct) |  Finagle's law elaborates on Sod's law: not only will anything that can go wrong, go wrong, but it will do so at the worst possible time.With our self-imposed end of month deadline fast approaching, October's awareness module was close to being completed ... until a hardware failure caused a day's delay. A solid state disk drive gave up the ghost without warning last night. Naturally being highly security-aware we have backups, lots of backups, but rebuilding/restoring the system on a new disk inevitably takes time. Bang went my Saturday!October's module is entirely new, being a new awareness topic for us, so it has taken longer than normal to prepare the module, leaving little slack in our schedule. Such is life. So, tomorrow I'll be slogging through what remains of the weekend, doing my level best to catch up and complete the materials for delivery on Monday, hopefully.On the upside, our backups worked! We had enough spare hardware to survive this incident with relatively little impact except a day's lost work and elevated stress levels. An unplanned business continuity exercise. Finagle's law elaborates on Sod's law: not only will anything that can go wrong, go wrong, but it will do so at the worst possible time.With our self-imposed end of month deadline fast approaching, October's awareness module was close to being completed ... until a hardware failure caused a day's delay. A solid state disk drive gave up the ghost without warning last night. Naturally being highly security-aware we have backups, lots of backups, but rebuilding/restoring the system on a new disk inevitably takes time. Bang went my Saturday!October's module is entirely new, being a new awareness topic for us, so it has taken longer than normal to prepare the module, leaving little slack in our schedule. Such is life. So, tomorrow I'll be slogging through what remains of the weekend, doing my level best to catch up and complete the materials for delivery on Monday, hopefully.On the upside, our backups worked! We had enough spare hardware to survive this incident with relatively little impact except a day's lost work and elevated stress levels. An unplanned business continuity exercise. |
||||
| 2017-09-29 13:04:05 | NBlog September 29 - strategic alignment (lien direct) |  On the ISO27k Forum this morning, a member from a financial services company asked for some advice on aligning IT and Security with overall corporate/business strategies. He said, in part: "Organizational level strategic plan, covering its core business, has been derived. And it includes what is expected form Technology and Security departments, I.E. to keep customers, shareholders happy and to provide safe and secure technology services. [I need] to prepare a strategic plan decoded from organization's strategy, specifically for Technology and Security department, with goals, objectives, principles etc. So for achieving this, my approach is to understand each business strategy and determine the possible ways that Technology and Security team can help it. Business strategy -> Technology strategy -> Security Strategy"I strongly support the idea of explicitly linking 'our stuff' with corporate/business strategies (plus initiatives, projects and policies) but 'our stuff' is more than just technology security, or IT security, or cybersecurity, or data security .... I encourage everyone to refer to information risk, defined as 'risk pertaining to information', an all-encompassing term for what we are managing and doing. Especially in the strategic context, we should all be thinking beyond securing bits and bytes. [The mere fact that they have a department, team or whatever named "Security" that he and presumably others consider a part of, if not very closely tied to, "Technology", strongly suggests a very IT-centric view in the organization. To me, there's the merest whiff of a governance issue there: treating this as 'IT's problem', with the emphasis on security (as in controls, restrictions and prohibitions, as much as protection and safety) is a common but, in my view, sadly misguided and outdated approach - a widespread cultural issue in fact.]Identifying information risk aspects of the corporate strategies is a creative risk assessment activity. In stark contrast to financial risks, information risks tend to be largely unstated, if not unrecognized, at that level but can generally be teased out from the assumptions (both explicit and implicit). For instance, if a business strategy talks about "Expanding into a new market", consider what that actually means and how it will be achieved, then examine each of those proposed activities f On the ISO27k Forum this morning, a member from a financial services company asked for some advice on aligning IT and Security with overall corporate/business strategies. He said, in part: "Organizational level strategic plan, covering its core business, has been derived. And it includes what is expected form Technology and Security departments, I.E. to keep customers, shareholders happy and to provide safe and secure technology services. [I need] to prepare a strategic plan decoded from organization's strategy, specifically for Technology and Security department, with goals, objectives, principles etc. So for achieving this, my approach is to understand each business strategy and determine the possible ways that Technology and Security team can help it. Business strategy -> Technology strategy -> Security Strategy"I strongly support the idea of explicitly linking 'our stuff' with corporate/business strategies (plus initiatives, projects and policies) but 'our stuff' is more than just technology security, or IT security, or cybersecurity, or data security .... I encourage everyone to refer to information risk, defined as 'risk pertaining to information', an all-encompassing term for what we are managing and doing. Especially in the strategic context, we should all be thinking beyond securing bits and bytes. [The mere fact that they have a department, team or whatever named "Security" that he and presumably others consider a part of, if not very closely tied to, "Technology", strongly suggests a very IT-centric view in the organization. To me, there's the merest whiff of a governance issue there: treating this as 'IT's problem', with the emphasis on security (as in controls, restrictions and prohibitions, as much as protection and safety) is a common but, in my view, sadly misguided and outdated approach - a widespread cultural issue in fact.]Identifying information risk aspects of the corporate strategies is a creative risk assessment activity. In stark contrast to financial risks, information risks tend to be largely unstated, if not unrecognized, at that level but can generally be teased out from the assumptions (both explicit and implicit). For instance, if a business strategy talks about "Expanding into a new market", consider what that actually means and how it will be achieved, then examine each of those proposed activities f |
||||
| 2017-09-28 13:46:22 | NBlog September 28 - safe & secure (lien direct) |  The Coming Software Apocalypse is a long, well-written article about the growing difficulties of coding extremely complex modern software systems. With something in the order of 30 to 100 million lines of program code controlling fly-by-wire planes and cars, these are way too large and complicated for even gifted programmers to master single-handedly, while inadequate specifications, resource constraints, tight/unrealistic delivery deadlines, laziness/corner-cutting, bloat, cloud, teamwork, compliance assessments plus airtight change controls, and integrated development environments can make matters worse. Author James Somers spins the article around a central point. The coding part of software development is a tough intellectual challenge: programmers write programs telling computers to do stuff, leaving them divorced from the stuff - the business end of their efforts - by several intervening, dynamic and interactive layers of complexity. Since there's only so much they can do to ensure everything goes to plan, they largely rely on the integrity and function of those other layers ... and yet despite being pieces of a bigger puzzle, they may be held to account for the end result in its entirety.As if that's not bad enough already, the human beings who actually use, manage, hack and secure IT systems present further challenges. We're even harder to predict and control than computers, some quite deliberately so! From the information risk and security perspective, complexity is our kryptonite, our Achilles heel.Author James Somers brings up numerous safety-related software/system incidents, many of which I have seen discussed on the excellent RISKS List. Design flaws and bugs in software controlling medical and transportation systems are recurrent topics on RISKS, due to the obvious (and not so obvious!) health and safety implications of, say, autonomous trains and cars.All of this has set me thinking about 'safety' as a future awareness topic for NoticeBored, given the implications for all three of our target audiences:Workers in general increasingly rely on IT systems for safety-critical activities. It won't be hard to think up everyday examples - in fact it might be tough to focus on just a few!With a bit of prompting, manager The Coming Software Apocalypse is a long, well-written article about the growing difficulties of coding extremely complex modern software systems. With something in the order of 30 to 100 million lines of program code controlling fly-by-wire planes and cars, these are way too large and complicated for even gifted programmers to master single-handedly, while inadequate specifications, resource constraints, tight/unrealistic delivery deadlines, laziness/corner-cutting, bloat, cloud, teamwork, compliance assessments plus airtight change controls, and integrated development environments can make matters worse. Author James Somers spins the article around a central point. The coding part of software development is a tough intellectual challenge: programmers write programs telling computers to do stuff, leaving them divorced from the stuff - the business end of their efforts - by several intervening, dynamic and interactive layers of complexity. Since there's only so much they can do to ensure everything goes to plan, they largely rely on the integrity and function of those other layers ... and yet despite being pieces of a bigger puzzle, they may be held to account for the end result in its entirety.As if that's not bad enough already, the human beings who actually use, manage, hack and secure IT systems present further challenges. We're even harder to predict and control than computers, some quite deliberately so! From the information risk and security perspective, complexity is our kryptonite, our Achilles heel.Author James Somers brings up numerous safety-related software/system incidents, many of which I have seen discussed on the excellent RISKS List. Design flaws and bugs in software controlling medical and transportation systems are recurrent topics on RISKS, due to the obvious (and not so obvious!) health and safety implications of, say, autonomous trains and cars.All of this has set me thinking about 'safety' as a future awareness topic for NoticeBored, given the implications for all three of our target audiences:Workers in general increasingly rely on IT systems for safety-critical activities. It won't be hard to think up everyday examples - in fact it might be tough to focus on just a few!With a bit of prompting, manager |
||||
| 2017-09-27 13:08:17 | NBlog September 27 - compliance culture (lien direct) |  A discussion thread on CISSPforum about the security consequences of (some) software developers taking the easy option by grabbing code snippets off the Web rather than figuring things out for themselves (making sure they are appropriate and, of course, secure) set me thinking about human nature. We're all prone to 'taking the easy option'. You could say humans, and in fact all animals, are inherently lazy. Given the choice, we are inclined to cut corners and do the least amount possible, making this the default approach in almost all circumstances. We'd rather conserve our energy for more important things such as feeding and procreating.Yesterday, Deborah mentioned being parked at a junction in town near a one-way side road. In the few minutes she was there, she saw at least 3 cars disregard the no-entry signs, breaking the law rather than driving around the block to enter the side road from the proper direction. Sure they saved themselves a minute or so, but at what cost? Aside from the possibility of being fined, apparently there's a school just along the side road. It's not hard to imagine kids, teachers and parents rushing out of school in a bit of a hurry to get home, looking 'up the road' for oncoming vehicles and not bothering to look 'down the road' (yes, they take the easy option too).The same issue occurs often in information security. 'Doing the right thing' involves people minimizing risks to protect information, but there's a cost. It takes additional time and effort, compared to corner-cutting. Recognizing that there is a right and a wrong way is a starting point - easy enough when there are bloody great "No entry" signs on the road, or with assorted warning messages, bleeps, popup alerts and so forth when the computer spots something risky such as a possible phishing message. Informing people about risks and rules is part of security awareness, but it's not enough. We also need to persuade them to act appropriately, making the effort that it takes not to cut the corner.You may think this is a purely personal matter: some people are naturally compliant law-abiding citizens, others are naturally averse to rules (sometimes on principle!), with a large swathe in the middle who are ambiguous or inconsistent, some plain ignorant or careless. How they react depends partly on the particular circumstances, including their past experience in similar situations ... which hints at another aspect of security awareness, namely the educational value of describing situations, explaining the consequences of different courses of action, guid A discussion thread on CISSPforum about the security consequences of (some) software developers taking the easy option by grabbing code snippets off the Web rather than figuring things out for themselves (making sure they are appropriate and, of course, secure) set me thinking about human nature. We're all prone to 'taking the easy option'. You could say humans, and in fact all animals, are inherently lazy. Given the choice, we are inclined to cut corners and do the least amount possible, making this the default approach in almost all circumstances. We'd rather conserve our energy for more important things such as feeding and procreating.Yesterday, Deborah mentioned being parked at a junction in town near a one-way side road. In the few minutes she was there, she saw at least 3 cars disregard the no-entry signs, breaking the law rather than driving around the block to enter the side road from the proper direction. Sure they saved themselves a minute or so, but at what cost? Aside from the possibility of being fined, apparently there's a school just along the side road. It's not hard to imagine kids, teachers and parents rushing out of school in a bit of a hurry to get home, looking 'up the road' for oncoming vehicles and not bothering to look 'down the road' (yes, they take the easy option too).The same issue occurs often in information security. 'Doing the right thing' involves people minimizing risks to protect information, but there's a cost. It takes additional time and effort, compared to corner-cutting. Recognizing that there is a right and a wrong way is a starting point - easy enough when there are bloody great "No entry" signs on the road, or with assorted warning messages, bleeps, popup alerts and so forth when the computer spots something risky such as a possible phishing message. Informing people about risks and rules is part of security awareness, but it's not enough. We also need to persuade them to act appropriately, making the effort that it takes not to cut the corner.You may think this is a purely personal matter: some people are naturally compliant law-abiding citizens, others are naturally averse to rules (sometimes on principle!), with a large swathe in the middle who are ambiguous or inconsistent, some plain ignorant or careless. How they react depends partly on the particular circumstances, including their past experience in similar situations ... which hints at another aspect of security awareness, namely the educational value of describing situations, explaining the consequences of different courses of action, guid |
||||
| 2017-09-25 15:51:23 | NBlog September 24 - five-step bulletproofing? (lien direct) | In the course of searching for case study materials and quotations to illustrate October's awareness materials, I came across 5 ways to create a bulletproof security culture by Brian Stafford. Brian's 5 ways are, roughly: Get Back to Basics - address human behaviors including errors. Fair enough. The NoticeBored InfoSec 101 awareness module we updated last month is precisely for a back-to-basics approach, including fundamental concepts, attitudes and behaviors.Reinvent the Org Chart - have the CISO report to the CEO. Brian doesn't explain why but it's pretty obvious, especially if you accept that the organization's culture is like a cloak that covers everyone, and strong leadership is the primary way of influencing it. The reporting relationship is only part of the issue though: proper governance is a bigger consideration, for example aligning the management of information risks and assets with that for other kinds of risk and asset. Also security metrics - a gaping hole in the governance of most organizations.Invest in Education - "Any company that seeks to have a strong security culture must not only offer robust trainings to all employees-including the c-suite-but also encourage professional development opportunities tailored to their unique focus areas." Awareness, training and education go hand-in-hand: they are complementary.Incentivize & Reward Wanted Behavior e.g. by career advancement options. Again, the InfoSec 101 module proposes a structured gold-silver-bronze approach to rewards and incentives, and I've discussed the idea here on the blog several times. Compliance reinforcement through rewards and encouragement is far more positive and motivational than the negative compliance enforcement approach through pressure, penalties and grief. Penalties may still be necessary but as a last resort than the default option.Apply the Right Technology - hmm, an important consideration, for sure, although I'm not sure what this has to do with security culture. I guess I would say that technical controls need to work in concert with non-tech controls, and the selection, operation, use and management of all kinds of control is itself largely a human activity. The fact that Brian included this as one of his 5 ways betrays the widespread bias towards technology and cybersecurity. I'd go so far as to call it myopic. Personally, and despite Personally, and despite |
Guideline | |||
| 2017-09-23 18:02:02 | NBlog September 23 - security culture sit rep (lien direct) |  October's awareness module is gradually taking shape. The management and professionals' seminar slide decks and notes are about 80% done. They're quite intenst, earnest and rather dull though, so we need something inspiring to liven things up a bit. More thinking and digging around required yet.Meanwhile, the staff/general materials are coming along too. The next 7 days will be busy, systematically writing, revising, aligning and polishing the content until it gleams and glints in the sun - talking of which, we set the clocks forward an hour tonight for summer time: it has been a long, wet NZ Winter this year. October's awareness module is gradually taking shape. The management and professionals' seminar slide decks and notes are about 80% done. They're quite intenst, earnest and rather dull though, so we need something inspiring to liven things up a bit. More thinking and digging around required yet.Meanwhile, the staff/general materials are coming along too. The next 7 days will be busy, systematically writing, revising, aligning and polishing the content until it gleams and glints in the sun - talking of which, we set the clocks forward an hour tonight for summer time: it has been a long, wet NZ Winter this year. |
||||
| 2017-09-22 08:59:43 | NBlog September 22 - cultured security (lien direct) |  Aside from concerning the attitudes and values shared within groups, or its use in microbiology (!), there's another meaning of 'culture' relating to being suave and sophisticated. In the information risk and security context, it's about both being and appearing professional, exuding competence and quality - and that can be quite important if you consider the alternative. Given the choice, would you be happy interacting and doing business with an organization that is, or appears to be, uncultured - crude, slapdash, unreliable etc.? Or would you be somewhat reluctant to trust them?There are some obvious examples in the news headlines most weeks: any organization that suffers a major privacy breach, hack, ransomware or other incident comes across as a victim and arguably perhaps culpable for the situation. It's hardly a glowing endorsement of their information risk, security, privacy and compliance arrangements! Contrast their position against the majority of organizations, particularly the banks that exude trustworthiness. Corporate cultures, brands and reputations are bound strongly together.The two meanings of 'culture' are linked in the sense that the overall impression an organization portrays is the combination of many individual factors or elements. Through marketing, advertising and promotions, public relations, social media etc., management naturally strives to present a polished, impressive, business-like, trustworthy external corporate image, but has limited control over all the day-to-day goings on. Myriad interactions between workers and the outside world are largely independent, driven by the individuals, individually, and by the corporate culture as a whole.Management may try to control the latter, espousing 'corporate values' through motivational speeches and posters, but in most organizations it's like herding cats or plaiting fog. Much like managing change, managing the corporate culture is a tough challenge in practice. Realistically, the best management can hope for is to influence things in the right direction, perhaps rounding-off the sharpest corners and presenting a more consistently positive front. Aside from concerning the attitudes and values shared within groups, or its use in microbiology (!), there's another meaning of 'culture' relating to being suave and sophisticated. In the information risk and security context, it's about both being and appearing professional, exuding competence and quality - and that can be quite important if you consider the alternative. Given the choice, would you be happy interacting and doing business with an organization that is, or appears to be, uncultured - crude, slapdash, unreliable etc.? Or would you be somewhat reluctant to trust them?There are some obvious examples in the news headlines most weeks: any organization that suffers a major privacy breach, hack, ransomware or other incident comes across as a victim and arguably perhaps culpable for the situation. It's hardly a glowing endorsement of their information risk, security, privacy and compliance arrangements! Contrast their position against the majority of organizations, particularly the banks that exude trustworthiness. Corporate cultures, brands and reputations are bound strongly together.The two meanings of 'culture' are linked in the sense that the overall impression an organization portrays is the combination of many individual factors or elements. Through marketing, advertising and promotions, public relations, social media etc., management naturally strives to present a polished, impressive, business-like, trustworthy external corporate image, but has limited control over all the day-to-day goings on. Myriad interactions between workers and the outside world are largely independent, driven by the individuals, individually, and by the corporate culture as a whole.Management may try to control the latter, espousing 'corporate values' through motivational speeches and posters, but in most organizations it's like herding cats or plaiting fog. Much like managing change, managing the corporate culture is a tough challenge in practice. Realistically, the best management can hope for is to influence things in the right direction, perhaps rounding-off the sharpest corners and presenting a more consistently positive front. |
Guideline | |||
| 2017-09-20 08:27:57 | NBlog September 20 - Phishing awareness & cultural change (lien direct) |  This plopped into my inbox last evening at about 8pm, when both ANZ customers and the ANZ fraud and security pros are mostly off-guard, relaxing at home. It's clearly a phishing attack, obvious for all sorts of reasons (e.g. the spelling and grammatical errors, the spurious justification and call to action, the non-ANZ hyperlink, oh and the fact that I don't have an ANZ account!) - obvious to me, anyway, and I hope obvious to ANZ customers, assuming they are sufficiently security-aware to spot the clues.I guess the phishers are either hoping to trick victims into disclosing their ANZ credentials directly, or persuade them to reveal enough that they can trick the bank into accepting a change of the mobile phone number presumably being used for two-factor authentication, or for password resets.Right now (8 am, 12 hours after the attack) I can't see this particular attack mentioned explicitly on the ANZ site, although there is some basic guidance on "hoax messages" with a few other phishing examples. The warnings and advice are not exactly prominent, however, so you need to go digging to find the information, which means you need to be alert and concerned enough in the first place, which implies a level of awareness - a classic chicken-and-egg situation. I presume ANZ has other security awareness materials, advisories and reminders for customers. If not, perhaps we can help!Aside from the authentication and fraud angle, I'm interested in the cultural aspects. Down here in NZ, people generally seem to be quite honest and trusting: it's a charming feature of the friendly and welcoming Pacific culture that pervades our lives. Given its size and history, things may be different in Australia - I don't know. But I do know that phishing and other forms of fraud are problematic in NZ. The Pacific culture is changing, becoming more careful as a result of these and other scams, but very slowly. Increasing distrust and cynicism seems likely to knock the corners off the charm that I mentioned, with adverse implications for tourism and commerce - in other words cultural changes can create as well as solve problems. The same issue applies within organizations: pushing security awareness will lead (eventually, if sustained) to changes in the corporate culture, only some of which are beneficial. It's possible to be too security-conscious, too risk-averse, to the point that it interferes with business. October's awareness seminar and briefings for management will discuss a strategic approach ai This plopped into my inbox last evening at about 8pm, when both ANZ customers and the ANZ fraud and security pros are mostly off-guard, relaxing at home. It's clearly a phishing attack, obvious for all sorts of reasons (e.g. the spelling and grammatical errors, the spurious justification and call to action, the non-ANZ hyperlink, oh and the fact that I don't have an ANZ account!) - obvious to me, anyway, and I hope obvious to ANZ customers, assuming they are sufficiently security-aware to spot the clues.I guess the phishers are either hoping to trick victims into disclosing their ANZ credentials directly, or persuade them to reveal enough that they can trick the bank into accepting a change of the mobile phone number presumably being used for two-factor authentication, or for password resets.Right now (8 am, 12 hours after the attack) I can't see this particular attack mentioned explicitly on the ANZ site, although there is some basic guidance on "hoax messages" with a few other phishing examples. The warnings and advice are not exactly prominent, however, so you need to go digging to find the information, which means you need to be alert and concerned enough in the first place, which implies a level of awareness - a classic chicken-and-egg situation. I presume ANZ has other security awareness materials, advisories and reminders for customers. If not, perhaps we can help!Aside from the authentication and fraud angle, I'm interested in the cultural aspects. Down here in NZ, people generally seem to be quite honest and trusting: it's a charming feature of the friendly and welcoming Pacific culture that pervades our lives. Given its size and history, things may be different in Australia - I don't know. But I do know that phishing and other forms of fraud are problematic in NZ. The Pacific culture is changing, becoming more careful as a result of these and other scams, but very slowly. Increasing distrust and cynicism seems likely to knock the corners off the charm that I mentioned, with adverse implications for tourism and commerce - in other words cultural changes can create as well as solve problems. The same issue applies within organizations: pushing security awareness will lead (eventually, if sustained) to changes in the corporate culture, only some of which are beneficial. It's possible to be too security-conscious, too risk-averse, to the point that it interferes with business. October's awareness seminar and briefings for management will discuss a strategic approach ai |
Guideline | |||
| 2017-09-19 07:01:06 | NBlog September 19 - what is \'security culture\'? (lien direct) |  For some while now, I've been contemplating what security culture actually means, in practice. Thinking back to the organizations in which I have worked, they have all had it some extent (otherwise they probably wouldn't have employed someone like me!) but there were differences in the cultures. What were they?Weaknesses in corporate security cultures are also evident in organizations that end up on the 6 o'clock news as a result of security and privacy incidents. In the extreme, the marked absence of a security culture implies more than just casual risk-taking. There's a reckless air to them with people (including management - in fact managers in particular) deliberately doing things they know they shouldn't, not just bending the rules and pushing the boundaries of acceptable behavior but, in some cases, breaking laws and regulations. That's an insecurity culture!The strength of the security culture is a relative rather than absolute measure: it's a matter of degree. So, with my metrics hat on, what are the measurable characteristics? How would we go about measuring them? What are the scales? What's important to the organization in this domain?A notable feature of organizations with relatively strong security cultures is that information security is an endemic part of the business - neither ignored nor treated as something special, an optional extra tacked-on the side (suggesting that 'information risk and security integration' might be one of those measurable characteristics). When IT systems and business processes are changed, for instance, the information risk, security and related aspects are naturally taken into account almost without being pushed by management. On a broader front, there's a general expectation that things will be done properly. By default, workers generally act in the organization's best interests, doing the right thing normally without even being asked. Information security is integral to the organization's approach, alongside other considerations and approaches such as quality, efficiency, ethics, compliance and ... well ... maturity. Maturity hints at a journey, a sequence of stages that organizations go through as their security culture emerges and grows stronger. That's what October's For some while now, I've been contemplating what security culture actually means, in practice. Thinking back to the organizations in which I have worked, they have all had it some extent (otherwise they probably wouldn't have employed someone like me!) but there were differences in the cultures. What were they?Weaknesses in corporate security cultures are also evident in organizations that end up on the 6 o'clock news as a result of security and privacy incidents. In the extreme, the marked absence of a security culture implies more than just casual risk-taking. There's a reckless air to them with people (including management - in fact managers in particular) deliberately doing things they know they shouldn't, not just bending the rules and pushing the boundaries of acceptable behavior but, in some cases, breaking laws and regulations. That's an insecurity culture!The strength of the security culture is a relative rather than absolute measure: it's a matter of degree. So, with my metrics hat on, what are the measurable characteristics? How would we go about measuring them? What are the scales? What's important to the organization in this domain?A notable feature of organizations with relatively strong security cultures is that information security is an endemic part of the business - neither ignored nor treated as something special, an optional extra tacked-on the side (suggesting that 'information risk and security integration' might be one of those measurable characteristics). When IT systems and business processes are changed, for instance, the information risk, security and related aspects are naturally taken into account almost without being pushed by management. On a broader front, there's a general expectation that things will be done properly. By default, workers generally act in the organization's best interests, doing the right thing normally without even being asked. Information security is integral to the organization's approach, alongside other considerations and approaches such as quality, efficiency, ethics, compliance and ... well ... maturity. Maturity hints at a journey, a sequence of stages that organizations go through as their security culture emerges and grows stronger. That's what October's |
||||
| 2017-09-15 14:13:45 | NBlog September 15 - symbolic security (lien direct) |  An article bemoaning the lack of an iconic image for the field of “risk management†(e.g. the insurance industry) applies to information risk and security as well. We don't really have one either. Well maybe we do: there are padlocks, chains and keys, hackers in hoodies and those Anonymous facemasks a-plenty (a minute's image-Googling easily demonstrates that). Trouble is that the common images tend to emphasize threats and controls, constraints and costs. All very negative. A big downer.Information risk and security may never be soft and cuddly ... but I'm sure we can do more to distance ourselves from the usual negative imagery and perceptions. I really like the idea of information security being an enabler, allowing the organization do stuff (business!) that would otherwise be too risky. So I'll be spending idle moments at the weekend thinking how to sum that concept up in an iconic image. Preferably something pink and fluffy, with no threatening overtones. An article bemoaning the lack of an iconic image for the field of “risk management†(e.g. the insurance industry) applies to information risk and security as well. We don't really have one either. Well maybe we do: there are padlocks, chains and keys, hackers in hoodies and those Anonymous facemasks a-plenty (a minute's image-Googling easily demonstrates that). Trouble is that the common images tend to emphasize threats and controls, constraints and costs. All very negative. A big downer.Information risk and security may never be soft and cuddly ... but I'm sure we can do more to distance ourselves from the usual negative imagery and perceptions. I really like the idea of information security being an enabler, allowing the organization do stuff (business!) that would otherwise be too risky. So I'll be spending idle moments at the weekend thinking how to sum that concept up in an iconic image. Preferably something pink and fluffy, with no threatening overtones. |
||||
| 2017-09-13 20:07:44 | NBlog September 13 - surveying the corporate security culture (lien direct) |  Inspired perhaps by yesterday's blog about the Security Culture Framework, today we have been busy on a security culture survey, metrics being the first stage of the SCF. We've designed a disarmingly straightforward single-sided form posing just a few simple but carefully-crafted questions around the corporate security culture. Despite its apparent simplicity, the survey form is quite complex with several distinct but related purposes or objectives:Although the form is being prepared as an MS Word document with the intention of being self-completed on paper by respondents (primarily general staff), the form could just as easily be used for an online survey on the corporate intranet, a survey app, or a facilitated survey (like shoppers being stopped in the shopping mall by friendly people with clipboards ... and free product samples to give away).The survey form is of course part of our security awareness product, linking-in with and supporting the other awareness content in October's module on 'security culture', and more broadly with the ongoing awareness program. The style and format of the form should be instantly familiar to anyone who has seen our awareness materials. A short introduction on the form succinctly explains what 'security culture' means and why it is of concern and value to the organization, hence why the survey is being carried out. I'm intrigued by the idea of positioning the entire organization as a 'safe pair of hands' that protects and looks after information: a reasonable objective given the effort involved in influencing the corporate security culture. Even the survey form is intended to raise awareness, in this case making the subtle point that management cares enough about the topic to survey workers' security-related perceptions and behaviors including their attitudes towards management. Conducting the survey naturally implies that management will consider and act appropriately on the results. We take that implied obligation seriously, and will have more to say about it in the module's train-the-trainer guide. The survey is more than just a paper exercise or an awareness item: respondents will have perfectly reasonable expectations merely as a result of participating.The survey questions themselves are designed to gather measurable responses i.e. data on a few key criteria or aspects of 'security culture'. We have more work to do on the questions, and even when we're done we hope our customers will adapt them to suit their specific needs (e.g. Inspired perhaps by yesterday's blog about the Security Culture Framework, today we have been busy on a security culture survey, metrics being the first stage of the SCF. We've designed a disarmingly straightforward single-sided form posing just a few simple but carefully-crafted questions around the corporate security culture. Despite its apparent simplicity, the survey form is quite complex with several distinct but related purposes or objectives:Although the form is being prepared as an MS Word document with the intention of being self-completed on paper by respondents (primarily general staff), the form could just as easily be used for an online survey on the corporate intranet, a survey app, or a facilitated survey (like shoppers being stopped in the shopping mall by friendly people with clipboards ... and free product samples to give away).The survey form is of course part of our security awareness product, linking-in with and supporting the other awareness content in October's module on 'security culture', and more broadly with the ongoing awareness program. The style and format of the form should be instantly familiar to anyone who has seen our awareness materials. A short introduction on the form succinctly explains what 'security culture' means and why it is of concern and value to the organization, hence why the survey is being carried out. I'm intrigued by the idea of positioning the entire organization as a 'safe pair of hands' that protects and looks after information: a reasonable objective given the effort involved in influencing the corporate security culture. Even the survey form is intended to raise awareness, in this case making the subtle point that management cares enough about the topic to survey workers' security-related perceptions and behaviors including their attitudes towards management. Conducting the survey naturally implies that management will consider and act appropriately on the results. We take that implied obligation seriously, and will have more to say about it in the module's train-the-trainer guide. The survey is more than just a paper exercise or an awareness item: respondents will have perfectly reasonable expectations merely as a result of participating.The survey questions themselves are designed to gather measurable responses i.e. data on a few key criteria or aspects of 'security culture'. We have more work to do on the questions, and even when we're done we hope our customers will adapt them to suit their specific needs (e.g. |
||||
| 2017-09-12 16:58:10 | NBlog September 12 - Security Culture Framework (lien direct) |  In preparing for our forthcoming awareness module on security culture, I've been re-reading and contemplating Kai Roer's Security Culture Framework (SCF) - a structured management approach with 4 phases.1. Metrics: set goals and measureSpeaking as an advocate of security metrics, this sounds a good place to start - or at least it would be if SCF explored the goals in some depth first, rather than leaping directly into SMART metrics: there's not much point evaluating or designing possible metrics until you know what needs to be measured. In this context, understanding the organization's strategic objectives would be a useful setting-off point. SCF talks about 'result goals' (are there any other kind?) and 'learning outcomes' (which implies that learning is a goal - but why? What is the value or purpose of learning?): what about business objectives for safely exploiting and protecting valuable information?SCF seems to have sidestepped more fundamental issues. What is the organization trying to achieve? How would what we are thinking of doing support or enable achievement of those organizational objectives? Security awareness, and information security as a whole, is not in itself a goal but a means to an end. I would start there: what is or are the ends? What is information security awareness meant to achieve? Having discussed that issue many times before, I'm not going to elaborate further on today, here except to say that if the Goals are clear, the Questions arising are fairly obvious, which in turn makes it straightforward to come up with a whole bunch of possible Metrics (the GQM method). From there, SMART is not such a smart way to filter out the few metrics with a positive value to the organization, whereas the PRAGMATIC metametrics method was expressly designed for the purpose.SCF further muddies the waters by mentioning a conventional Lewin-style approach to change management (figure out where you are, identify where you want to be, then systematically close the gap) plus Deming's Plan-Do-Check-Act approach to quality assurance. I'm not entirely convinced these are helpful in setting goals and identifying measures. I would have preferred to elaborate on the process of analyzing the organization's core business, teasing ou In preparing for our forthcoming awareness module on security culture, I've been re-reading and contemplating Kai Roer's Security Culture Framework (SCF) - a structured management approach with 4 phases.1. Metrics: set goals and measureSpeaking as an advocate of security metrics, this sounds a good place to start - or at least it would be if SCF explored the goals in some depth first, rather than leaping directly into SMART metrics: there's not much point evaluating or designing possible metrics until you know what needs to be measured. In this context, understanding the organization's strategic objectives would be a useful setting-off point. SCF talks about 'result goals' (are there any other kind?) and 'learning outcomes' (which implies that learning is a goal - but why? What is the value or purpose of learning?): what about business objectives for safely exploiting and protecting valuable information?SCF seems to have sidestepped more fundamental issues. What is the organization trying to achieve? How would what we are thinking of doing support or enable achievement of those organizational objectives? Security awareness, and information security as a whole, is not in itself a goal but a means to an end. I would start there: what is or are the ends? What is information security awareness meant to achieve? Having discussed that issue many times before, I'm not going to elaborate further on today, here except to say that if the Goals are clear, the Questions arising are fairly obvious, which in turn makes it straightforward to come up with a whole bunch of possible Metrics (the GQM method). From there, SMART is not such a smart way to filter out the few metrics with a positive value to the organization, whereas the PRAGMATIC metametrics method was expressly designed for the purpose.SCF further muddies the waters by mentioning a conventional Lewin-style approach to change management (figure out where you are, identify where you want to be, then systematically close the gap) plus Deming's Plan-Do-Check-Act approach to quality assurance. I'm not entirely convinced these are helpful in setting goals and identifying measures. I would have preferred to elaborate on the process of analyzing the organization's core business, teasing ou |
||||
| 2017-09-11 18:11:13 | NBlog September 11 - Security culture (lien direct) |  Last night we watched a documentary on the History Channel about 9-11 - a mix of amateur and professional footage that took me back to a Belgian hotel room in 2001, watching incredulously as the nightmare unfolded on TV. Tonight there are more 9-11 documentaries, one of which concerns The War On Terror. As with The War On Drugs and The War On Poverty, we're never going to celebrate victory as such: as fast as we approach the target, it morphs and recedes from view. It's an endless journey.The idea of waging war on something is a rallying cry, meant to sound inspirational and positive. In some (but not all) cultures it is ... and yet, in a literal sense, it's hard to imagine any sane, level-headed person truly relishing the thought of going to war. According to Margaret Atwood, "War is what happens when language fails", in other words when negotiations fail to the point that violent action is perceived as the best, or last remaining, option.In truth, The War On Whatever involves more than just violent action: the negotiations don't stop, they just change. In public, they evolve into rhetoric and propaganda, fake news and extremism intended to elicit deeply emotional responses. In private, there's the whole issue of reaching agreement, defining the bottom line, stopping the untenable costs, saving face and redefining the boundaries.National cultures and attitudes towards war and safety go way beyond the remit of our awareness service, and yet the corporate security culture has its roots in human perceptions, beliefs, ethics and moral values. We're unlikely to make much headway in changing those, although that alone needn't stop us trying! Hopefully we can influence some attitudes and hence some behaviors, perhaps drawing on cultural cues as part of the process.There's plenty more to say on security culture as we work our way through the month: I promise future episodes will be less jingoistic and more upbeat. Last night we watched a documentary on the History Channel about 9-11 - a mix of amateur and professional footage that took me back to a Belgian hotel room in 2001, watching incredulously as the nightmare unfolded on TV. Tonight there are more 9-11 documentaries, one of which concerns The War On Terror. As with The War On Drugs and The War On Poverty, we're never going to celebrate victory as such: as fast as we approach the target, it morphs and recedes from view. It's an endless journey.The idea of waging war on something is a rallying cry, meant to sound inspirational and positive. In some (but not all) cultures it is ... and yet, in a literal sense, it's hard to imagine any sane, level-headed person truly relishing the thought of going to war. According to Margaret Atwood, "War is what happens when language fails", in other words when negotiations fail to the point that violent action is perceived as the best, or last remaining, option.In truth, The War On Whatever involves more than just violent action: the negotiations don't stop, they just change. In public, they evolve into rhetoric and propaganda, fake news and extremism intended to elicit deeply emotional responses. In private, there's the whole issue of reaching agreement, defining the bottom line, stopping the untenable costs, saving face and redefining the boundaries.National cultures and attitudes towards war and safety go way beyond the remit of our awareness service, and yet the corporate security culture has its roots in human perceptions, beliefs, ethics and moral values. We're unlikely to make much headway in changing those, although that alone needn't stop us trying! Hopefully we can influence some attitudes and hence some behaviors, perhaps drawing on cultural cues as part of the process.There's plenty more to say on security culture as we work our way through the month: I promise future episodes will be less jingoistic and more upbeat. |
||||
| 2017-09-08 18:35:37 | NBlog September 8 - security certification (lien direct) |  Aside from the elevator pitch, another short awareness item in our newly-revised Information Security 101 module is a course completion certificate, simply acknowledging that someone has been through the induction or orientation course.I say 'simply' but as usual with NoticeBored, there's more to it.For a start, some of us (especially those who consider ourselves 'professionals') just love our certificates: our qualifications and the letters before/after our names mean something to us and hopefully other people. This is a personal thing with cultural relevance, and it's context-dependent (my 30-year-old PhD in microbial genetics has next to nothing to do with my present role!). My even older cycling proficiency certificate is meaningless now, barely a memory, but at the time I was proud of my achievement. Receiving it boosted my self-esteem, as valuable a benefit as being able to demonstrate my prowess on two wheels. I'm tempted to use Cprof on my business cards just to see if anyone reads them!On the other hand, a certificate indicating a pass mark in some assessment or test can be misleading. The driving test, for example, is a fairly low hurdle in terms of all the situations that a driver may have to deal with over the remainder of their driving career. There is clearly a risk that a newly-certified and licensed driver might be over-confident as a result of passing the test and going solo, a time when accidents are more likely hence some countries encourage a subsequent period of driving with special P-plates (meaning probationary, or passed or potential or ...) in the hope that others will give new drivers more space. In risk terms, there are risk-reduction benefits in letting new drivers continue to hone their new-found skills, offsetting the increased risk of incidents.In the same way with the InfoSec 101 course completion certificate, we're glad to acknowledge the personal achievement and boost people's self-esteem (yay - something positive associated with information risk and security!), although there is a risk they might believe themselves more competent in this area that they truly are. On balance, we'd rather deal with that issue, in part through the ongoing security awareness activities that delve deeper into areas covered quite superficially in the 101 module, across a br Aside from the elevator pitch, another short awareness item in our newly-revised Information Security 101 module is a course completion certificate, simply acknowledging that someone has been through the induction or orientation course.I say 'simply' but as usual with NoticeBored, there's more to it.For a start, some of us (especially those who consider ourselves 'professionals') just love our certificates: our qualifications and the letters before/after our names mean something to us and hopefully other people. This is a personal thing with cultural relevance, and it's context-dependent (my 30-year-old PhD in microbial genetics has next to nothing to do with my present role!). My even older cycling proficiency certificate is meaningless now, barely a memory, but at the time I was proud of my achievement. Receiving it boosted my self-esteem, as valuable a benefit as being able to demonstrate my prowess on two wheels. I'm tempted to use Cprof on my business cards just to see if anyone reads them!On the other hand, a certificate indicating a pass mark in some assessment or test can be misleading. The driving test, for example, is a fairly low hurdle in terms of all the situations that a driver may have to deal with over the remainder of their driving career. There is clearly a risk that a newly-certified and licensed driver might be over-confident as a result of passing the test and going solo, a time when accidents are more likely hence some countries encourage a subsequent period of driving with special P-plates (meaning probationary, or passed or potential or ...) in the hope that others will give new drivers more space. In risk terms, there are risk-reduction benefits in letting new drivers continue to hone their new-found skills, offsetting the increased risk of incidents.In the same way with the InfoSec 101 course completion certificate, we're glad to acknowledge the personal achievement and boost people's self-esteem (yay - something positive associated with information risk and security!), although there is a risk they might believe themselves more competent in this area that they truly are. On balance, we'd rather deal with that issue, in part through the ongoing security awareness activities that delve deeper into areas covered quite superficially in the 101 module, across a br |
Guideline | |||
| 2017-09-06 16:33:56 | NBlog September 6 - passwords are dead (lien direct) |  I've blogged about passwords several times. It's a zombie topic, one that refuses to go away or just lie down and die quietly.On CISSPforum, we've been idly chatting about user authentication for a week or so. The consensus is that passwords are a lousy way to authenticate, for several reasons.First the obvious. Passwords are:Hard to remember, at least good ones are, especially if we are forced to think up new ones periodically for no particular reason;Generally weak and easily guessed, due to the previous point;Sometimes generated and issued not chosen or changeable by the user;Readily shared or disclosed (e.g. by watching us type), or written down;Readily obtained by force, coercion, deception and other forms of social engineering such as phishing or password reset tricks, or interception, or hacking, or brute force attacks, or spyware or .. well clearly there are lots of attacks;Often re-used (for different sites/apps etc., and over time).Next comes some less obvious, more pernicious lousiness:Badly-designed sites/systems sometimes prevent us using strong passwords (e.g. they must be less than 20 characters with no spaces nor special characters ...; must be typed or clicked manually - no automation allowed);Poor guidance on choosing passwords encourages poor choices, Passwords are sometimes weakened covertly by even lousier sites/systems (e.g. we can enter complex 50 character passwords but they only actually use 6, or store them in plaintext, or use a pathetically weak or broken hashing algorithm, often without a salt ...).In short, passwords are not a reliable way to authenticate people. As a security control, they are weak to mediocre at best, not strong ... which is obvously I've blogged about passwords several times. It's a zombie topic, one that refuses to go away or just lie down and die quietly.On CISSPforum, we've been idly chatting about user authentication for a week or so. The consensus is that passwords are a lousy way to authenticate, for several reasons.First the obvious. Passwords are:Hard to remember, at least good ones are, especially if we are forced to think up new ones periodically for no particular reason;Generally weak and easily guessed, due to the previous point;Sometimes generated and issued not chosen or changeable by the user;Readily shared or disclosed (e.g. by watching us type), or written down;Readily obtained by force, coercion, deception and other forms of social engineering such as phishing or password reset tricks, or interception, or hacking, or brute force attacks, or spyware or .. well clearly there are lots of attacks;Often re-used (for different sites/apps etc., and over time).Next comes some less obvious, more pernicious lousiness:Badly-designed sites/systems sometimes prevent us using strong passwords (e.g. they must be less than 20 characters with no spaces nor special characters ...; must be typed or clicked manually - no automation allowed);Poor guidance on choosing passwords encourages poor choices, Passwords are sometimes weakened covertly by even lousier sites/systems (e.g. we can enter complex 50 character passwords but they only actually use 6, or store them in plaintext, or use a pathetically weak or broken hashing algorithm, often without a salt ...).In short, passwords are not a reliable way to authenticate people. As a security control, they are weak to mediocre at best, not strong ... which is obvously |
||||
| 2017-09-04 15:31:24 | NBlog September 4 - InfoSec 101 elevator pitch, final part (lien direct) | Moving on from our discussion of the first two paragraphs of this month's elevator pitch paper in part 1 and part 2, here's the closing paragraph:As a manager, you play a vital governance, leadership and oversight rôle. Please make the effort to engage with and support the security awareness program, discuss information risk and security with your colleagues, and help us strengthen the corporate security culture. In classical marketing terms, it's the call-to-action for people who have been lured and hooked. Having presented our case, what do we actually want them to do? Compared to the preceding two, the third paragraph is quite long. While we could easily have dropped the first sentence, it serves a purpose. It shows deference to the management audience, acknowledging their influential and powerful status, gently reminding them that they are expected to direct and oversee things. Essentially (in not so many word), it says "Pay attention! This is an obligation, one of your duties as a manager."The final sentence, including those three words in bold, was especially tricky to write for the InfoSec 101 module. What is it, exactly, that we expect senior managers to do in relation to this very broad introductory-level topic? Think about that question for a moment. There are many possible answers e.g.:Show leadershipDemonstrate commitmentSupport the Information Security Management System (in an ISO27k organization)Get actively involved in information risk and security management activities, such as risk assessment and risk treatment decisionsRaise the profile and priority of information risk and security mattersProvide adequate resources to do this stuff properly for once (!)Encourage or enforce compliance In classical marketing terms, it's the call-to-action for people who have been lured and hooked. Having presented our case, what do we actually want them to do? Compared to the preceding two, the third paragraph is quite long. While we could easily have dropped the first sentence, it serves a purpose. It shows deference to the management audience, acknowledging their influential and powerful status, gently reminding them that they are expected to direct and oversee things. Essentially (in not so many word), it says "Pay attention! This is an obligation, one of your duties as a manager."The final sentence, including those three words in bold, was especially tricky to write for the InfoSec 101 module. What is it, exactly, that we expect senior managers to do in relation to this very broad introductory-level topic? Think about that question for a moment. There are many possible answers e.g.:Show leadershipDemonstrate commitmentSupport the Information Security Management System (in an ISO27k organization)Get actively involved in information risk and security management activities, such as risk assessment and risk treatment decisionsRaise the profile and priority of information risk and security mattersProvide adequate resources to do this stuff properly for once (!)Encourage or enforce compliance |
Guideline | |||
| 2017-09-03 12:28:08 | NBlog September 3 - InfoSec 101 elevator pitch, part 2 of 3 (lien direct) |  Yesterday, I started telling you about one of the smallest deliverables in our awareness portfolio, the elevator pitch aimed at senior executive management. Despite its diminutive size, a lot of effort goes into selecting and fine-tuning those 100-odd words.[Sorry if this detailed deconstruction of the pitch one paragraph at a time is tedious but I think it's useful to understand the design, the purpose of the page and the thinking that goes into it. As far as I know, we are the only security awareness provider specifically targeting senior management in this way. I've made disparaging comments in the past about awareness programs aimed at "end-users": neglecting other employees - especially managers and professionals - seems incredibly short-sighted to me, a bit like trying to teach the passengers how to drive a car, ignoring the driver and the mechanics.] OK, pressing swiftly ahead, the elevator pitch can be interrupted at any point. If someone is presenting or talking it through with an exec, they may well need to break off answer questions or respond to comments. If a busy exec is quickly skimming the piece online or on paper, they might get distracted by a phone call or email. We may only have their attention fleetingly, if at all. If we're lucky, the exec will swallow the bait and be hooked ... so the second paragraph has the essential barb:Cybersecurity is important but there's more to it than IT. Information security enables the business to exploit information in ways that would otherwise be too risky.'Cybersecurity' is all the rage, of course. It's a term we see frequently in the media. Although it's rarely defined, it is generally interpreted as IT and network security, specifically around Internet-related tech incidents such as hacking and malware. That's all very well, but what about all the rest of information risk and security? What about social engineering scams and frauds, piracy, industrial espionage and so forth? What about the whole insider-threat thing: where does that fit in relation to 'cyber'? Oh, hang on a moment: explain Yesterday, I started telling you about one of the smallest deliverables in our awareness portfolio, the elevator pitch aimed at senior executive management. Despite its diminutive size, a lot of effort goes into selecting and fine-tuning those 100-odd words.[Sorry if this detailed deconstruction of the pitch one paragraph at a time is tedious but I think it's useful to understand the design, the purpose of the page and the thinking that goes into it. As far as I know, we are the only security awareness provider specifically targeting senior management in this way. I've made disparaging comments in the past about awareness programs aimed at "end-users": neglecting other employees - especially managers and professionals - seems incredibly short-sighted to me, a bit like trying to teach the passengers how to drive a car, ignoring the driver and the mechanics.] OK, pressing swiftly ahead, the elevator pitch can be interrupted at any point. If someone is presenting or talking it through with an exec, they may well need to break off answer questions or respond to comments. If a busy exec is quickly skimming the piece online or on paper, they might get distracted by a phone call or email. We may only have their attention fleetingly, if at all. If we're lucky, the exec will swallow the bait and be hooked ... so the second paragraph has the essential barb:Cybersecurity is important but there's more to it than IT. Information security enables the business to exploit information in ways that would otherwise be too risky.'Cybersecurity' is all the rage, of course. It's a term we see frequently in the media. Although it's rarely defined, it is generally interpreted as IT and network security, specifically around Internet-related tech incidents such as hacking and malware. That's all very well, but what about all the rest of information risk and security? What about social engineering scams and frauds, piracy, industrial espionage and so forth? What about the whole insider-threat thing: where does that fit in relation to 'cyber'? Oh, hang on a moment: explain |
||||
| 2017-09-02 14:17:13 | NBlog September 2 - InfoSec 101 elevator pitch, part 1 of 3 (lien direct) |  The elevator pitch is an awareness format we developed specifically for busy senior executives and other senior managers. Its main aim is to tell them just enough so they know what the awareness topic concerns. We'd like to intrigue them, prompting them to ask questions and seek more information, ideally influencing their decisions and actions as they go about their business in a more secure fashion.The 'elevator pitch' name and button panel image alludes to the idea of condensing a complex subject down to a short statement that could literally be expressed during a short elevator ride. We don't actually envisage someone standing there in the elevator car reading out a prepared script to the captive audience, so much as being primed and ready to respond off-the-cuff to an informal opener from an exec along the lines of "So, how are things with you?".We limit ourselves to about 100 words per topic. As you'll see from the example above, that works out to just 3 paragraphs or so, of 2 or 3 sentences each. It takes a surprising amount of effort to put things across so succinctly: the real art is in figuring out what's appropriate to leave out, and how to express the essentials in a way likely to resonate with senior managers.Imagine being a fisherman selecting some juicy morsel to bait the hook. Ideally the pitch needs to catch the target's eye, intriguing them and sparking their imagination so they gulp it down ... but being realistic, very few execs are going to have the time and interest to drop everything and focus on information security, at least not on the strength of a snatched conversation in the elevator or a casual corridor chat. Let's look at the InfoSec 101 elevator pitch in more detail, breaking it down a paragraph at a time:Information is a valuable but vulnerable business asset that requires protection against risks. Responding to the risks through suitable controls involves all those who create, use and handle information. Yes, that's everyone.Those first few words are crucial, explicitly positioning information risk and security as a busine The elevator pitch is an awareness format we developed specifically for busy senior executives and other senior managers. Its main aim is to tell them just enough so they know what the awareness topic concerns. We'd like to intrigue them, prompting them to ask questions and seek more information, ideally influencing their decisions and actions as they go about their business in a more secure fashion.The 'elevator pitch' name and button panel image alludes to the idea of condensing a complex subject down to a short statement that could literally be expressed during a short elevator ride. We don't actually envisage someone standing there in the elevator car reading out a prepared script to the captive audience, so much as being primed and ready to respond off-the-cuff to an informal opener from an exec along the lines of "So, how are things with you?".We limit ourselves to about 100 words per topic. As you'll see from the example above, that works out to just 3 paragraphs or so, of 2 or 3 sentences each. It takes a surprising amount of effort to put things across so succinctly: the real art is in figuring out what's appropriate to leave out, and how to express the essentials in a way likely to resonate with senior managers.Imagine being a fisherman selecting some juicy morsel to bait the hook. Ideally the pitch needs to catch the target's eye, intriguing them and sparking their imagination so they gulp it down ... but being realistic, very few execs are going to have the time and interest to drop everything and focus on information security, at least not on the strength of a snatched conversation in the elevator or a casual corridor chat. Let's look at the InfoSec 101 elevator pitch in more detail, breaking it down a paragraph at a time:Information is a valuable but vulnerable business asset that requires protection against risks. Responding to the risks through suitable controls involves all those who create, use and handle information. Yes, that's everyone.Those first few words are crucial, explicitly positioning information risk and security as a busine |
||||
| 2017-09-01 10:00:07 | NBlog September 1 - back to basics: InfoSec 101 (lien direct) |  When someone initially joins an organization, they immediately start absorbing the corporate culture – 'the way we do things here' – gradually becoming a part of it. Most organizations run security orientation or induction sessions to welcome newcomers and kick-start the cultural integration process, with individual sessions lasting between a few minutes and a few hours depending on the topics to be covered, local practice, and of course the audience (e.g. there may be a quick-start process for managers, and more in-depth training for technical specialists).Let's be honest: orientation tends to be as dull as a lecture on the dangers of teenage pregnancy. It's trial-by-fire, something to be endured rather than enjoyed. The new NoticeBored Information Security 101 module covers common information risks (e.g. malware) and controls that are more-or-less universal (e.g. antivirus). The awareness materials are deliberately succinct and quite superficial: they outline key things without delving into the details. Given the context of a continuous NoticeBored-style security awareness program delivering a stream of fresh materials, there's no need to cover everything about information risk and security in one hit. The pressure's off. Relax! All we really need in the induction session do is help newcomers set off on the right foot, engaging them as integral and valuable parts of the organization's Information Security Management System. That leaves room to focus on an even more important objective, one that we will expand upon in next month's module. Building relationships between Information Security professionals and business people in general, makes a huge difference to the corporate security culture. Think about it: would you rather pick up the phone to the friendly professional who took time to meet you when you joined the organization, or a total stranger? When someone initially joins an organization, they immediately start absorbing the corporate culture – 'the way we do things here' – gradually becoming a part of it. Most organizations run security orientation or induction sessions to welcome newcomers and kick-start the cultural integration process, with individual sessions lasting between a few minutes and a few hours depending on the topics to be covered, local practice, and of course the audience (e.g. there may be a quick-start process for managers, and more in-depth training for technical specialists).Let's be honest: orientation tends to be as dull as a lecture on the dangers of teenage pregnancy. It's trial-by-fire, something to be endured rather than enjoyed. The new NoticeBored Information Security 101 module covers common information risks (e.g. malware) and controls that are more-or-less universal (e.g. antivirus). The awareness materials are deliberately succinct and quite superficial: they outline key things without delving into the details. Given the context of a continuous NoticeBored-style security awareness program delivering a stream of fresh materials, there's no need to cover everything about information risk and security in one hit. The pressure's off. Relax! All we really need in the induction session do is help newcomers set off on the right foot, engaging them as integral and valuable parts of the organization's Information Security Management System. That leaves room to focus on an even more important objective, one that we will expand upon in next month's module. Building relationships between Information Security professionals and business people in general, makes a huge difference to the corporate security culture. Think about it: would you rather pick up the phone to the friendly professional who took time to meet you when you joined the organization, or a total stranger? |
||||
| 2017-08-31 17:01:53 | NBlog August 31 - strengthening Information Security\'s social network (lien direct) |  Some security awareness programs simply broadcast messages at the organization. Messages flow from the Information Security function to the audience - specifically an audience dubbed "end users" in many cases, a disparaging term implying low-level staff who use computers (neglecting all others). A more effective approach, however, is to emphasize social networking and socialization of security as a primary driver of cultural change, with bidirectional communications increasing the chances that the awareness program reflects and responds to the business.Establishing a strong social network of friends and supporters of information security throughout the organization takes commitment and sustained effort on the part of the entire Information Security function. The payback over the medium to long-term, however, makes it an approach well worth considering. An actively engaged and supportive social network will keep the awareness program, and in fact the information security program as a whole, business-aligned and relevant to current security issues in the organization, broadening and deepening the department's influence. On top of that, you can achieve far more through a distributed network of supportive contacts than you can possibly manage alone.Support from senior management is great but, in our experience, many of the most well-connected and influential workers are low-ranking individuals. They are 'people people' with the common touch, a natural flair for social interaction. This is why we're providing a template rôle description for the Information Security Awareness Contact in September's Information Security 101 module to get you started if you decide to structure and formalize the rôle to this extent. That may not be appropriate or necessary, depending on how your organization handles such issues. Speak to your management and HR about the concept before going too far down that line, including aspects such as recruiting, guiding/coordinating, motivating and rewarding people who accept the rôle. Colleagues in HR, Security Administration, IT/PC Support, Business Continuity, Risk Management, Compliance and Health & Safety may have similar social networks already in place (e.g. departmental reps, fire marshals and first responders). Invest some time in meeting both those colleagues and their best contacts to find out how the arrangements work on both sides, pick up useful tips ... and hopefully make a few solid-gold contacts of your own. Some security awareness programs simply broadcast messages at the organization. Messages flow from the Information Security function to the audience - specifically an audience dubbed "end users" in many cases, a disparaging term implying low-level staff who use computers (neglecting all others). A more effective approach, however, is to emphasize social networking and socialization of security as a primary driver of cultural change, with bidirectional communications increasing the chances that the awareness program reflects and responds to the business.Establishing a strong social network of friends and supporters of information security throughout the organization takes commitment and sustained effort on the part of the entire Information Security function. The payback over the medium to long-term, however, makes it an approach well worth considering. An actively engaged and supportive social network will keep the awareness program, and in fact the information security program as a whole, business-aligned and relevant to current security issues in the organization, broadening and deepening the department's influence. On top of that, you can achieve far more through a distributed network of supportive contacts than you can possibly manage alone.Support from senior management is great but, in our experience, many of the most well-connected and influential workers are low-ranking individuals. They are 'people people' with the common touch, a natural flair for social interaction. This is why we're providing a template rôle description for the Information Security Awareness Contact in September's Information Security 101 module to get you started if you decide to structure and formalize the rôle to this extent. That may not be appropriate or necessary, depending on how your organization handles such issues. Speak to your management and HR about the concept before going too far down that line, including aspects such as recruiting, guiding/coordinating, motivating and rewarding people who accept the rôle. Colleagues in HR, Security Administration, IT/PC Support, Business Continuity, Risk Management, Compliance and Health & Safety may have similar social networks already in place (e.g. departmental reps, fire marshals and first responders). Invest some time in meeting both those colleagues and their best contacts to find out how the arrangements work on both sides, pick up useful tips ... and hopefully make a few solid-gold contacts of your own. |
||||
| 2017-08-30 09:19:09 | NBlog August 30 - information risk assessment (reprise) (lien direct) |  On ISO27k Forum this morning, an FAQ made yet another appearance. SR asked:"I am planning to do risk assessment based on Process/Business based. Kindly share if you have any templates and also suggest me how it can be done."Bhushan Kaluvakolan responded first by proposing a risk assessment method based on threats and vulnerabilities (and impacts, I guess), a classical information-security-centric approach that I've used many times. Fair enough.I followed up by proposing an alternative (and perhaps complementary) business-centric approach that I've brought up previously both on the Forum and here on NBlog:Consider the kinds of incidents and scenarios that might affect the process, both directly and indirectly. Especially if the process is already operating, check for any incident reports, review/audit comments, known issues, management concerns, expert opinions etc., and/or run a risk workshop with a range of business people and specialists to come up with a bunch of things – I call them 'information risks'. This is a creative, lateral thinking process – brainstorming. Focus on the information, as much as possible, especially information that is plainly valuable/essential for the business. If necessary, remind the experts that this is a business situation, a genuine organizational concern that needs pragmatic answers, not some academic exercise in precision.Review each of those information risks in turn and try to relate/group them where applicable. Some of them will be more or less severe variants on a common theme (e.g. an upstream supply chain incident can range from mild e.g. minor delays and quality issues on non-critical supplies, to severe e.g. sudden/unanticipated total failure of one or more key suppliers due to some catastrophe, such as the Japanese tsunami). Others will be quite different in nature (e.g. various problems with individual employees, IT systems etc.). A neat way to do this is to write each risk on a separate sticky note, then stick them on a white board and briefly explain them, then move them into related/different groups of various sizes and shapes. On ISO27k Forum this morning, an FAQ made yet another appearance. SR asked:"I am planning to do risk assessment based on Process/Business based. Kindly share if you have any templates and also suggest me how it can be done."Bhushan Kaluvakolan responded first by proposing a risk assessment method based on threats and vulnerabilities (and impacts, I guess), a classical information-security-centric approach that I've used many times. Fair enough.I followed up by proposing an alternative (and perhaps complementary) business-centric approach that I've brought up previously both on the Forum and here on NBlog:Consider the kinds of incidents and scenarios that might affect the process, both directly and indirectly. Especially if the process is already operating, check for any incident reports, review/audit comments, known issues, management concerns, expert opinions etc., and/or run a risk workshop with a range of business people and specialists to come up with a bunch of things – I call them 'information risks'. This is a creative, lateral thinking process – brainstorming. Focus on the information, as much as possible, especially information that is plainly valuable/essential for the business. If necessary, remind the experts that this is a business situation, a genuine organizational concern that needs pragmatic answers, not some academic exercise in precision.Review each of those information risks in turn and try to relate/group them where applicable. Some of them will be more or less severe variants on a common theme (e.g. an upstream supply chain incident can range from mild e.g. minor delays and quality issues on non-critical supplies, to severe e.g. sudden/unanticipated total failure of one or more key suppliers due to some catastrophe, such as the Japanese tsunami). Others will be quite different in nature (e.g. various problems with individual employees, IT systems etc.). A neat way to do this is to write each risk on a separate sticky note, then stick them on a white board and briefly explain them, then move them into related/different groups of various sizes and shapes. |
Wannacry | |||
| 2017-08-28 08:34:54 | NBlog August 27 - thanks a million (lien direct) |  According to Google's Blogger stats, over the weekend this blog topped 1 million page views so I guess we must be doing something right! It would be hard to come up with something new to say every day, if it weren't for the fact that we are all bombarded by stuff from other blogs and groups, from advisories and committees, and from several billion Websites. There's lots of stuff going on in the world of infosec which keeps me interested and hopefully you too.My main concern is the human as opposed to technological aspects, hence my overriding interest in promoting good practices in information risk and security governance and management (especially ISO27k and security metrics), security awareness, policies, procedures etc. to keep a lid on social engineering scams, frauds, hacks and malware attacks, ineptitude, thievery, spying, piracy and so forth. Having said that, managing technology requires understanding it (IT especially) so I try my best to keep an eye on that too. And the physical side. And compliance. And risk management. And business ...I interpret and react to the news rather than simply passing things on, an approach I hope rubs off on you. I'm expressing personal opinions here, hopefully adding value based on my experience and knowledge. I encourage you all to think about what you read, reinterpret it in your context, be critical and by all means disagree with me. I don't hold all the answers. I know I am outspoken, cranky and off-base sometimes. I'm human too. This blog is my catchpa!OK, must press on. We have sick animals to tend plus an awareness module to complete. Back soon. According to Google's Blogger stats, over the weekend this blog topped 1 million page views so I guess we must be doing something right! It would be hard to come up with something new to say every day, if it weren't for the fact that we are all bombarded by stuff from other blogs and groups, from advisories and committees, and from several billion Websites. There's lots of stuff going on in the world of infosec which keeps me interested and hopefully you too.My main concern is the human as opposed to technological aspects, hence my overriding interest in promoting good practices in information risk and security governance and management (especially ISO27k and security metrics), security awareness, policies, procedures etc. to keep a lid on social engineering scams, frauds, hacks and malware attacks, ineptitude, thievery, spying, piracy and so forth. Having said that, managing technology requires understanding it (IT especially) so I try my best to keep an eye on that too. And the physical side. And compliance. And risk management. And business ...I interpret and react to the news rather than simply passing things on, an approach I hope rubs off on you. I'm expressing personal opinions here, hopefully adding value based on my experience and knowledge. I encourage you all to think about what you read, reinterpret it in your context, be critical and by all means disagree with me. I don't hold all the answers. I know I am outspoken, cranky and off-base sometimes. I'm human too. This blog is my catchpa!OK, must press on. We have sick animals to tend plus an awareness module to complete. Back soon. |
||||
| 2017-08-25 14:13:47 | NBlog August 25 - awareness boosters (lien direct) |  The Information Security 101 awareness module update is going well. We might even finish slightly ahead of the deadline, provided I can resist the temptation to keep polishing and adding to the content!One of the deliverables is a 'menu' of rewards for workers who uphold the information risk and security practises, controls and behaviors we wish to encourage. The rewards are divided into bronze, silver and gold categories.Bronze rewards are generally free or cheap, and yet welcome - a nice way to thank workers for simply participating in awareness seminars, case study/workshop session or quiz maybe. Here are just a few examples:A phone call, personal thank-you note and/or emailLetter of participation or commendation to be placed in the employee's personnel file (whatever that means!)Relaxed dress code for the recipient – for a defined period such as a day or a week Generic certificate acknowledging a level of competence (e.g. on completion of security induction training - there's a template in the module)Note and/or photo on hall-of-fame, newsletter and/or the Security Zone (Information Security's intranet website - again there's a generic website design specification in the module)Plain (dull bronze) pin badge or sticker with awareness program logoPlain (dull bronze) staff pass lanyard with awareness program logo and stock message (such as how to contact the Help Desk or Site Security)Moving up a level, silver awards are more valuable and attractive, requiring a little more money and effort:[if !supportLists]-->Polo/tee-shirt printed with corporate and/or awareness program logo and a relevant quotation or catch-phrase The Information Security 101 awareness module update is going well. We might even finish slightly ahead of the deadline, provided I can resist the temptation to keep polishing and adding to the content!One of the deliverables is a 'menu' of rewards for workers who uphold the information risk and security practises, controls and behaviors we wish to encourage. The rewards are divided into bronze, silver and gold categories.Bronze rewards are generally free or cheap, and yet welcome - a nice way to thank workers for simply participating in awareness seminars, case study/workshop session or quiz maybe. Here are just a few examples:A phone call, personal thank-you note and/or emailLetter of participation or commendation to be placed in the employee's personnel file (whatever that means!)Relaxed dress code for the recipient – for a defined period such as a day or a week Generic certificate acknowledging a level of competence (e.g. on completion of security induction training - there's a template in the module)Note and/or photo on hall-of-fame, newsletter and/or the Security Zone (Information Security's intranet website - again there's a generic website design specification in the module)Plain (dull bronze) pin badge or sticker with awareness program logoPlain (dull bronze) staff pass lanyard with awareness program logo and stock message (such as how to contact the Help Desk or Site Security)Moving up a level, silver awards are more valuable and attractive, requiring a little more money and effort:[if !supportLists]-->Polo/tee-shirt printed with corporate and/or awareness program logo and a relevant quotation or catch-phrase |
Guideline | |||
| 2017-08-24 18:20:50 | NBlog August 24 - hot potato or mash? (lien direct) |  I'm currently working on a couple of interrelated matters concerning ISO/IEC JTC 1/SC 27 business. One is the possibility of renaming and perhaps re-scoping the committee's work. The other is a study period exploring cybersecurity.They are related because cyber is a hot potato - a bandwagon no less. Some on the committee are raring to disable the brakes and jump aboard.When asked to describe what cybersecurity is, one expert replied "Budget!". That's more than just a cynical retort. Cyber risk, cyber security, cyber threats, cyber attacks, cyber incidents and cyberinsurance are all over the headlines. Several countries have invested in cyber strategies and units. There is money in cyber, so that's a good thing, right?As I've said before, the focus on cyber is problematic for several reasons, not least distinctly different interpretations of the very term, a gaping chasm separating two distinct domains of understanding:In informal use (including most journalists and commentators in the blogophere), cyber means almost anything to do with IT, the Internet in particular. The primary concerns here are everyday hackers and malware (or rather "viruses").In (some?) government and defense circles, cyber alludes to cyberwar, meaning state-sponsored extreme threats exploiting all means possible to compromise an enemy's critical infrastructures, IT systems, comms, economy and society. Compared to the other interpretation, this off-the-scale nastiness requires a fundamentally different approach. Firewalls and antivirus just won't cut it, not by a long chalk. If anything, those everyday hackers and malware are a source of chaff, handy to conceal much more insidious compromises such as APT (Advanced Persistent Threats) and malicious processor hardware/firmware. Authorities stockpiling rather than disclosing vulnerabilities, and building red teams like there's no tomorrow, hints at what's going on right now.As if that's not enough, every man and his dog is either coming up with his own unique definition or ducking the issue by remaining (deliberately?) vague and imprecise. There's little consensus, hence lots of confusion and talking at cross purposes.It is entirely possible that SC 27 might find itself lumbered with the cyber moniker because it's sexy, in which case those diffe I'm currently working on a couple of interrelated matters concerning ISO/IEC JTC 1/SC 27 business. One is the possibility of renaming and perhaps re-scoping the committee's work. The other is a study period exploring cybersecurity.They are related because cyber is a hot potato - a bandwagon no less. Some on the committee are raring to disable the brakes and jump aboard.When asked to describe what cybersecurity is, one expert replied "Budget!". That's more than just a cynical retort. Cyber risk, cyber security, cyber threats, cyber attacks, cyber incidents and cyberinsurance are all over the headlines. Several countries have invested in cyber strategies and units. There is money in cyber, so that's a good thing, right?As I've said before, the focus on cyber is problematic for several reasons, not least distinctly different interpretations of the very term, a gaping chasm separating two distinct domains of understanding:In informal use (including most journalists and commentators in the blogophere), cyber means almost anything to do with IT, the Internet in particular. The primary concerns here are everyday hackers and malware (or rather "viruses").In (some?) government and defense circles, cyber alludes to cyberwar, meaning state-sponsored extreme threats exploiting all means possible to compromise an enemy's critical infrastructures, IT systems, comms, economy and society. Compared to the other interpretation, this off-the-scale nastiness requires a fundamentally different approach. Firewalls and antivirus just won't cut it, not by a long chalk. If anything, those everyday hackers and malware are a source of chaff, handy to conceal much more insidious compromises such as APT (Advanced Persistent Threats) and malicious processor hardware/firmware. Authorities stockpiling rather than disclosing vulnerabilities, and building red teams like there's no tomorrow, hints at what's going on right now.As if that's not enough, every man and his dog is either coming up with his own unique definition or ducking the issue by remaining (deliberately?) vague and imprecise. There's little consensus, hence lots of confusion and talking at cross purposes.It is entirely possible that SC 27 might find itself lumbered with the cyber moniker because it's sexy, in which case those diffe |
||||
| 2017-08-23 13:14:19 | NBlog August 23 - Information Security outreach (lien direct) |  Further to yesterday's ISO27k Forum thread and blog piece, I've been contemplating the idea of extending the security awareness program into an "outreach" initiative for Information Security, or at least viewing it in that way. I have in mind a planned, systematic, proactive approach not just to spread the information risk and security gospel, but to forge stronger more productive working relationships throughout the organization, perhaps even beyond. Virtually every interaction between anyone from Information Security and The Business is a relationship-enhancing opportunity, a chance to inform, communicate/exchange information in both directions, assist, guide, and generally build the credibility and information Security's brand. Doing so has the potential to:Drive or enhance the corporate security culture through Information Security becoming increasingly respected, trusted, approachable, consulted, informed and most of all used, rather than being ignored, feared and shunned (the "No Department");Improve understanding on all sides, such as identifying business initiatives, issues, concerns and demands for Information Security involvement, at an early enough stage to be able to specify, plan, resource and deliver the work at a sensible pace rather than at the last possible moment with next to no available resources; also knowing when to back-off, leaving the business to its own devices if there are other more pressing demands, including situations where accepting information risks is necessary or appropriate for various business reasons;Encourage and facilitate collaboration, cooperation and alignment around common goals;Improve the productivity and effectiveness of Information Security by being more customer-oriented - always a concern with ivory-tower expert functions staffed by professionals who think they (OK, we!) know best;Improve the management and treatment of information risks as a whole through better information security, supporting key business objectives such as being able to exploit business opportunities that would otherwise be too risky, while complying with applicable laws and regulations. Further to yesterday's ISO27k Forum thread and blog piece, I've been contemplating the idea of extending the security awareness program into an "outreach" initiative for Information Security, or at least viewing it in that way. I have in mind a planned, systematic, proactive approach not just to spread the information risk and security gospel, but to forge stronger more productive working relationships throughout the organization, perhaps even beyond. Virtually every interaction between anyone from Information Security and The Business is a relationship-enhancing opportunity, a chance to inform, communicate/exchange information in both directions, assist, guide, and generally build the credibility and information Security's brand. Doing so has the potential to:Drive or enhance the corporate security culture through Information Security becoming increasingly respected, trusted, approachable, consulted, informed and most of all used, rather than being ignored, feared and shunned (the "No Department");Improve understanding on all sides, such as identifying business initiatives, issues, concerns and demands for Information Security involvement, at an early enough stage to be able to specify, plan, resource and deliver the work at a sensible pace rather than at the last possible moment with next to no available resources; also knowing when to back-off, leaving the business to its own devices if there are other more pressing demands, including situations where accepting information risks is necessary or appropriate for various business reasons;Encourage and facilitate collaboration, cooperation and alignment around common goals;Improve the productivity and effectiveness of Information Security by being more customer-oriented - always a concern with ivory-tower expert functions staffed by professionals who think they (OK, we!) know best;Improve the management and treatment of information risks as a whole through better information security, supporting key business objectives such as being able to exploit business opportunities that would otherwise be too risky, while complying with applicable laws and regulations. |
Cloud | APT 37 | ||
| 2017-08-22 15:51:29 | NBlog August 22 - what to ask in a gap assessment (lien direct) |  A relatively simple and naive question on the ISO27k Forum this morning set me thinking. "RP" asked:"Does anybody have a generic [set of] high level questions for business departments other than IT, that can be asked during gap assessment?"As is so often the way with newcomers to the Forum, RP evidently hasn't caught up with past Forum threads (e.g. we recently chatted about various forms of gap analysis, and the markedly different ways that people [including dentists!] use and interpret the term), paid scant attention to forum etiquette (e.g. he/she didn't tell us his/her name), and provided little to no context in which to address the question (e.g. what size and kind of organization is it? What industry/sector? Does it have a functional, certified and mature ISO27k ISMS already, is it working towards one, or is RP just idly thinking about it over coffee?).Despite that, a couple of us responded as best we could, making assumptions about the context, the meaning and purpose of the 'gap assessment', and RP's situation. I suggesting posing questions along these lines:"What kinds of information do you use? Tell me more. Which is the most important information for your business activities, and why? What would happen if it was lost, damaged, out of date, inaccurate, incomplete, misleading, fraudulent, or disclosed e.g. on the Web?Roughly how much of the information you handle is classified? How much is SECRET/TOP-SECRET? [You'd probably need to be security cleared, and have management support, to get a meaningful answer to that!]What information do you generate? What happens to it? Where does it go? Who uses it, and for what? Would it matter to them if it stopped coming, or was late, or inaccurate, or incomplete, or was disclosed on the Web?When was the last time you examined your information risks? What was the result? Show me! What changed as a result?When was the last time you completed a business impact analysis and business continuity p A relatively simple and naive question on the ISO27k Forum this morning set me thinking. "RP" asked:"Does anybody have a generic [set of] high level questions for business departments other than IT, that can be asked during gap assessment?"As is so often the way with newcomers to the Forum, RP evidently hasn't caught up with past Forum threads (e.g. we recently chatted about various forms of gap analysis, and the markedly different ways that people [including dentists!] use and interpret the term), paid scant attention to forum etiquette (e.g. he/she didn't tell us his/her name), and provided little to no context in which to address the question (e.g. what size and kind of organization is it? What industry/sector? Does it have a functional, certified and mature ISO27k ISMS already, is it working towards one, or is RP just idly thinking about it over coffee?).Despite that, a couple of us responded as best we could, making assumptions about the context, the meaning and purpose of the 'gap assessment', and RP's situation. I suggesting posing questions along these lines:"What kinds of information do you use? Tell me more. Which is the most important information for your business activities, and why? What would happen if it was lost, damaged, out of date, inaccurate, incomplete, misleading, fraudulent, or disclosed e.g. on the Web?Roughly how much of the information you handle is classified? How much is SECRET/TOP-SECRET? [You'd probably need to be security cleared, and have management support, to get a meaningful answer to that!]What information do you generate? What happens to it? Where does it go? Who uses it, and for what? Would it matter to them if it stopped coming, or was late, or inaccurate, or incomplete, or was disclosed on the Web?When was the last time you examined your information risks? What was the result? Show me! What changed as a result?When was the last time you completed a business impact analysis and business continuity p |
Guideline | |||
| 2017-08-21 11:38:34 | NBlog August 21 - Internal Control Questionnaires (lien direct) |  Further to yesterday's piece about a free ISMS audit guideline, I normally prepare Internal Controls Questionnaires to structure and record my audit fieldwork. As the illustrative extract above shows, these work nicely as landscape tables in MS Word with the following 4 columns:Check: these are the audit tests, written before the audit fieldwork starts. As well as the classic audit 'show me' and 'tell me about ...', I much prefer open-ended questions and general prompts such as 'check', 'review' and 'evaluate'. ICQs are intended to be used by reasonably competent and experienced auditors, not spouted verbatim by novices. [The ISMS audit guideline includes an extensive but generic set of audit checks ready to cut-n-paste into this column, then trim and modify according to your specific audit requirements and situation.]SWOT: these record the auditor's first impressions - an initial evaluation of the findings. Is this area a Strength (the findings are good, risks well under control), a Weakness (there are some issues but nothing too desperate), an Opportunity (generally meaning an 'opportunity for improvement' i.e. a change that will benefit the business) or a Threat (a significant risk or concern that ought to be addressed in order to avoid a serious incident)?Notes: briefly state the audit findings. Factual evidence is crucially important to the audit process, and needs to be recorded carefully. For example, I sometimes quote the precise words spoken by auditees in audit interviews, and incorporate or cite relevant extracts from policies, procedures, logs, reports etc. The auditor's comments and interpretation are a valuable output too (e.g. explaining the context and possible consequences), but strong facts speak for t Further to yesterday's piece about a free ISMS audit guideline, I normally prepare Internal Controls Questionnaires to structure and record my audit fieldwork. As the illustrative extract above shows, these work nicely as landscape tables in MS Word with the following 4 columns:Check: these are the audit tests, written before the audit fieldwork starts. As well as the classic audit 'show me' and 'tell me about ...', I much prefer open-ended questions and general prompts such as 'check', 'review' and 'evaluate'. ICQs are intended to be used by reasonably competent and experienced auditors, not spouted verbatim by novices. [The ISMS audit guideline includes an extensive but generic set of audit checks ready to cut-n-paste into this column, then trim and modify according to your specific audit requirements and situation.]SWOT: these record the auditor's first impressions - an initial evaluation of the findings. Is this area a Strength (the findings are good, risks well under control), a Weakness (there are some issues but nothing too desperate), an Opportunity (generally meaning an 'opportunity for improvement' i.e. a change that will benefit the business) or a Threat (a significant risk or concern that ought to be addressed in order to avoid a serious incident)?Notes: briefly state the audit findings. Factual evidence is crucially important to the audit process, and needs to be recorded carefully. For example, I sometimes quote the precise words spoken by auditees in audit interviews, and incorporate or cite relevant extracts from policies, procedures, logs, reports etc. The auditor's comments and interpretation are a valuable output too (e.g. explaining the context and possible consequences), but strong facts speak for t |
||||
| 2017-08-20 08:05:50 | NBlog August 20 - FREE ISO27k audit guideline (lien direct) |  Over the last few weeks, I've been busy with a virtual team of volunteers updating an ISMS audit guideline written prior to the 2011 release of the ISO/IEC standards 27007 (Guidelines for information security management systems auditing) and 27008 (Guidelines for auditors on information security controls). One of our goals at the time was to contribute to the development of the standards.Meantime, not only have those two standards been published, but ISO/IEC 27001 and 27002 have also been updated ... so there was a lot of updating to do.Our guideline is aimed at internal auditors, specifically IT auditors tasked with auditing either:the management system parts of an Information Security Management System; orthe information security controls being managed by the ISMS.In ISO27k, the management system is a combined governance and management framework - a structured approach similar to those for managing quality assurance, environmental protection and more. Auditing it is fairly straightforward because 27001 is quite explicit about what it should be. The guideline goes beyond certification auditing, though. Even if the ISMS fulfills the requirements of the standard, it may not satisfy the organization's needs. Over the last few weeks, I've been busy with a virtual team of volunteers updating an ISMS audit guideline written prior to the 2011 release of the ISO/IEC standards 27007 (Guidelines for information security management systems auditing) and 27008 (Guidelines for auditors on information security controls). One of our goals at the time was to contribute to the development of the standards.Meantime, not only have those two standards been published, but ISO/IEC 27001 and 27002 have also been updated ... so there was a lot of updating to do.Our guideline is aimed at internal auditors, specifically IT auditors tasked with auditing either:the management system parts of an Information Security Management System; orthe information security controls being managed by the ISMS.In ISO27k, the management system is a combined governance and management framework - a structured approach similar to those for managing quality assurance, environmental protection and more. Auditing it is fairly straightforward because 27001 is quite explicit about what it should be. The guideline goes beyond certification auditing, though. Even if the ISMS fulfills the requirements of the standard, it may not satisfy the organization's needs. |
||||
| 2017-08-18 18:09:14 | NBlog August 18 - security culture through awareness (lien direct) |  That sums-up our approach to using security awareness as a mechanism to foster a 'culture of security'. In the spirit of yesterday's blog, rather than wax lyrical, I'll let the diagram speak for itself. 'Nuff said. That sums-up our approach to using security awareness as a mechanism to foster a 'culture of security'. In the spirit of yesterday's blog, rather than wax lyrical, I'll let the diagram speak for itself. 'Nuff said. |
||||
| 2017-08-17 14:41:54 | NBlog August 17 - InfoSec 101 for management (lien direct) |  Today I've revised the management seminar for Information Security 101. Given our deliberately wide brief, there's quite a lot to say even at the relatively superficial 101/introductory level, so we're using thought-provoking pictures (mind maps, process diagrams and conceptual imagery) in place of reams of text and tedious bullet points. The whole seminar works out at just 12 slides ... at least that's the management seminar slide deck we'll be providing to subscribers. They can adapt the content, perhaps incorporating extras or indeed cutting back on the supplied content - and that's fine by us.In fact, more than that, we actively recommend it! Much as we would like to offer awareness materials tailored for each customer, we simply don't have the resources. For starters, we would need to spend time getting to know and then keeping abreast of each customer's specific circumstances and needs ... and being information security related, there are confidentiality implications in that. Instead, we prefer to invest in research and development of high-quality cutting-edge awareness content, delivering editable materials that our valued customers can customize as they wish.Keeping up with the field is quite a challenge, a fun one for us. In the 3 years or so since the InfoSec 101 module was last revised, we've witnessed the rise of BYOD, ransomware and cybersecurity. Current issues include IoT security and, looking forward, GDPR is set to make big waves in privacy in less than a year's time.Most months we encourage customers to check and update their induction and other training course materials, picking and choosing from each new batch of NB content as appropriate. On a more subtle level, we're gently hinting that they should be proactively maintaining and refreshing their awareness and training content as a whole because outdated material can literally be worse than useless. If you work for a mid- to large-sized fairly mature organization, chances are your security awareness content includes stuff that is no longer relevant and misses out on emerging issues, even if you have someone dedicated to running the awareness and training program. If you are in a small organization with very limited resources, or one that depends on course materials updated 'whenever, if-ever', is it any surprise if newcomers get the impression that information security is unimportant, not a priority? Today I've revised the management seminar for Information Security 101. Given our deliberately wide brief, there's quite a lot to say even at the relatively superficial 101/introductory level, so we're using thought-provoking pictures (mind maps, process diagrams and conceptual imagery) in place of reams of text and tedious bullet points. The whole seminar works out at just 12 slides ... at least that's the management seminar slide deck we'll be providing to subscribers. They can adapt the content, perhaps incorporating extras or indeed cutting back on the supplied content - and that's fine by us.In fact, more than that, we actively recommend it! Much as we would like to offer awareness materials tailored for each customer, we simply don't have the resources. For starters, we would need to spend time getting to know and then keeping abreast of each customer's specific circumstances and needs ... and being information security related, there are confidentiality implications in that. Instead, we prefer to invest in research and development of high-quality cutting-edge awareness content, delivering editable materials that our valued customers can customize as they wish.Keeping up with the field is quite a challenge, a fun one for us. In the 3 years or so since the InfoSec 101 module was last revised, we've witnessed the rise of BYOD, ransomware and cybersecurity. Current issues include IoT security and, looking forward, GDPR is set to make big waves in privacy in less than a year's time.Most months we encourage customers to check and update their induction and other training course materials, picking and choosing from each new batch of NB content as appropriate. On a more subtle level, we're gently hinting that they should be proactively maintaining and refreshing their awareness and training content as a whole because outdated material can literally be worse than useless. If you work for a mid- to large-sized fairly mature organization, chances are your security awareness content includes stuff that is no longer relevant and misses out on emerging issues, even if you have someone dedicated to running the awareness and training program. If you are in a small organization with very limited resources, or one that depends on course materials updated 'whenever, if-ever', is it any surprise if newcomers get the impression that information security is unimportant, not a priority? |
||||
| 2017-08-16 10:45:46 | NBlog August 16 - NIST SP800-53 draft v5 (lien direct) |  [if gte vml 1]> [if !vml]-->[endif]-->A public draft of NIST SP800-53 revision 5 is worth checking out.Major changes in this draft:"Making the security and privacy controls more outcome-based by changing the structure of the controls;Fully integrating the privacy controls into the security control catalog creating a consolidated and unified set of controls for information systems and organizations, while providing summary and mapping tables for privacy-related controls;Separating the control selection process from the actual controls, thus allowing the controls to be used by different communities of interest including systems engineers, software developers, enterprise architects; and mission/business owners;Promoting integration with different risk management and cybersecurity approaches and lexicons, including the Cybersecurity Framework; [if gte vml 1]> [if !vml]-->[endif]-->A public draft of NIST SP800-53 revision 5 is worth checking out.Major changes in this draft:"Making the security and privacy controls more outcome-based by changing the structure of the controls;Fully integrating the privacy controls into the security control catalog creating a consolidated and unified set of controls for information systems and organizations, while providing summary and mapping tables for privacy-related controls;Separating the control selection process from the actual controls, thus allowing the controls to be used by different communities of interest including systems engineers, software developers, enterprise architects; and mission/business owners;Promoting integration with different risk management and cybersecurity approaches and lexicons, including the Cybersecurity Framework; |
||||
| 2017-08-15 16:10:26 | NBlog August 15 - work goes on (lien direct) |  We've updated more stuff for the Infosec 101 module today:8 two-page case studies based on commonplace incidents; 13 one-page scam alerts on common scams (yes, 13); Generic job descriptions for an Information Security Awareness Manager, plus an Awareness Officer, and Awareness Contacts (part timers, distributed throughout the organization). Ticks are appearing and darkening on the contents listing at a reasonable rate.Meanwhile, over on the ISO27k Forum, we've been discussing terminology and the pros and cons of various information security frameworks, and CISSP Forum has been yakkin' about quantum crypto key exchange and fake news. Oh and we've arranged for the tractor repair man to come over tomorrow to fix a broken valve and solenoid, and I popped down to the vet for antibiotics for 3 sick animals.Quite a varied and productive day, all in all. We've updated more stuff for the Infosec 101 module today:8 two-page case studies based on commonplace incidents; 13 one-page scam alerts on common scams (yes, 13); Generic job descriptions for an Information Security Awareness Manager, plus an Awareness Officer, and Awareness Contacts (part timers, distributed throughout the organization). Ticks are appearing and darkening on the contents listing at a reasonable rate.Meanwhile, over on the ISO27k Forum, we've been discussing terminology and the pros and cons of various information security frameworks, and CISSP Forum has been yakkin' about quantum crypto key exchange and fake news. Oh and we've arranged for the tractor repair man to come over tomorrow to fix a broken valve and solenoid, and I popped down to the vet for antibiotics for 3 sick animals.Quite a varied and productive day, all in all. |
||||
| 2017-08-14 15:29:01 | NBlog August 14 - why infosec? (lien direct) |  Today I'm revising the InfoSec 101 presentation for general employees, starting with a brief introductory slide addressing questions along the lines of "What's the point of information security?" and "Why are you even telling me about it?".It's not as easy as you might think to answer such fundamental questions, simply, for someone who may have no background or interest in the topic. So I went Googling for inspiration, and came across this neat list of infosec benefits from a company called Global Strategic:Demonstrates a clear commitment to data security- including confidentiality and strict accessibility rules;Provides procedures to manage risk;Keeps confidential information secure;Provides a significant competitive advantage;Ensures a secure exchange of information;Creates consistency in the delivery our services;Allows for inter-operability between organizations or groups within an organization;Builds a culture of security;Protects the company, assets, shareholders, employees and clients;Gives assurance that a third party provider takes your data security (and your business) as seriously as you doSome of those are not terribly helpful for our awareness purposes. A benefit of information security is security or protection [of information], yes, but that's obvious from the phrase! It doesn't move us forward.Risk management is definitely a core purpose of infosec. I'm not keen on the idea that infosec 'provides procedures' though. Infosec is an overall approach, rather than simply a set of procedures or processes. "Infosec lets us manage risks" is closer to the mark, I think, or maybe "We use infosec to manage information risks". Hmmm.Competitive advantage is another good one, although I think I would prefer talk about 'enabling the business'. Whereas managers are presumably familiar with the concept of competitive advantage, I'm not sure about general employees. 'Enabling' is a fairly complex concept too, so "Infosec is good for business" would be an even better way to express it.Re the notions of securely exchanging information and inter-operability: those seem quite narrow and specific to me - parts of infosec, for sure, but arguably too obscure for a relatively naive audience. They are technocentric, too, whereas we are keen to position infosec more broadly than just IT or cybersecurity. Today I'm revising the InfoSec 101 presentation for general employees, starting with a brief introductory slide addressing questions along the lines of "What's the point of information security?" and "Why are you even telling me about it?".It's not as easy as you might think to answer such fundamental questions, simply, for someone who may have no background or interest in the topic. So I went Googling for inspiration, and came across this neat list of infosec benefits from a company called Global Strategic:Demonstrates a clear commitment to data security- including confidentiality and strict accessibility rules;Provides procedures to manage risk;Keeps confidential information secure;Provides a significant competitive advantage;Ensures a secure exchange of information;Creates consistency in the delivery our services;Allows for inter-operability between organizations or groups within an organization;Builds a culture of security;Protects the company, assets, shareholders, employees and clients;Gives assurance that a third party provider takes your data security (and your business) as seriously as you doSome of those are not terribly helpful for our awareness purposes. A benefit of information security is security or protection [of information], yes, but that's obvious from the phrase! It doesn't move us forward.Risk management is definitely a core purpose of infosec. I'm not keen on the idea that infosec 'provides procedures' though. Infosec is an overall approach, rather than simply a set of procedures or processes. "Infosec lets us manage risks" is closer to the mark, I think, or maybe "We use infosec to manage information risks". Hmmm.Competitive advantage is another good one, although I think I would prefer talk about 'enabling the business'. Whereas managers are presumably familiar with the concept of competitive advantage, I'm not sure about general employees. 'Enabling' is a fairly complex concept too, so "Infosec is good for business" would be an even better way to express it.Re the notions of securely exchanging information and inter-operability: those seem quite narrow and specific to me - parts of infosec, for sure, but arguably too obscure for a relatively naive audience. They are technocentric, too, whereas we are keen to position infosec more broadly than just IT or cybersecurity. |
||||
| 2017-08-13 18:00:58 | NBlog August 13 - updating (lien direct) |  Another basic information security practice is updating e.g.:Patch promptly (update software)Lock-n-load (physical security)Counter cons (social engineering)Nuke nasties (update antivirus) Read rules (security policies)Those short alliterative phrases are memory-joggers to catch people's imagination and remind them about the things they ought to be doing regularly.Conspicuously missing from the list is changing passwords: once upon a time, it was generally accepted practice to force people to change their passwords every few weeks or months. I have never quite understood the rationale for this. It takes effort to think up and commit to memory yet another strong password, and there are security costs when people forget their passwords, so what's the benefit? I suppose it might frustrate someone who has been surreptitiously watching a colleague enter their password every day, trying to figure out what they are typing ... but really? Arguably it would reduce the success rate of repeated brute-force password guesses - that ought to be triggering alarms anyway. I just don't get it and nor, now, does NIST:"Verifiers SHOULD NOT impose other composition rules (e.g., requiring mixtures of different character types or prohibiting consecutively repeated characters) for memorized secrets. Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator."That comes from NIST Special Publication 800-63B - Digital Identity Guidelines: Authentication and Lifecycle Management, published in June and recently picked up by the security press.The list of things to include in the InfoSec 101 awareness module is becoming clearer by the day. Another basic information security practice is updating e.g.:Patch promptly (update software)Lock-n-load (physical security)Counter cons (social engineering)Nuke nasties (update antivirus) Read rules (security policies)Those short alliterative phrases are memory-joggers to catch people's imagination and remind them about the things they ought to be doing regularly.Conspicuously missing from the list is changing passwords: once upon a time, it was generally accepted practice to force people to change their passwords every few weeks or months. I have never quite understood the rationale for this. It takes effort to think up and commit to memory yet another strong password, and there are security costs when people forget their passwords, so what's the benefit? I suppose it might frustrate someone who has been surreptitiously watching a colleague enter their password every day, trying to figure out what they are typing ... but really? Arguably it would reduce the success rate of repeated brute-force password guesses - that ought to be triggering alarms anyway. I just don't get it and nor, now, does NIST:"Verifiers SHOULD NOT impose other composition rules (e.g., requiring mixtures of different character types or prohibiting consecutively repeated characters) for memorized secrets. Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator."That comes from NIST Special Publication 800-63B - Digital Identity Guidelines: Authentication and Lifecycle Management, published in June and recently picked up by the security press.The list of things to include in the InfoSec 101 awareness module is becoming clearer by the day. |
To see everything:
Our RSS (filtrered)
