What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2020-07-17 16:53:31 | NBlog July 17 - an appetite for risk (lien direct) |  Today we've been chatting about this on the ISO27k Forum: "Let's assume that the company is willing to accept risks with a potential financial impact less than $50k. Obviously after performing risk assessment, we need to decide which treatment option we should follow. In case when the potential impact of the risk is below $50k - (risk appetite), we should accept the risk, right? My question is: what happens if for some reason, multiple Low Risks (below risk appetite value/already accepted) occur at the same time? Should the Risk Appetite represent an aggregation of all low risks or just reflect the appetite for a single risk?"I suggested considering 'coincident risks' as another entire category or class of risks, some of which may well be above the risk appetite/acceptance threshold even if the individual risks fall below it. It gets worse. There are many other coincidences, errors, failures, issues and exceptional circumstances that could occur - in extremis, it's an infinite set of possibilities given all the permutations and combinations.Our collective failure to identify and take seriously the possibility of a pandemic landed us in the poo we're in now. Even those organisations that did have pandemic controls in place have found the going tougher than anticipated, some discovering that their stockpile of sanitizer and masks had not been properly stored and maintained, and hence was next to useless when called upon. Trust me, it can be a sobering exercise to run a risk workshop focused on rare but extremely impactful events, the outliers that we tend to ignore in routine risk management because it's hard enough dealing with the commonplace extreme events, let alone the rarities. Every well-managed organisation needs to deal sensibly with the scarily vague “something else happens and lands us in serious trouble” situations, when classical scenario planning runs out of steam. There are far too many possibilities to even enumerate, let alone evaluate and treat individually: a more general-purpose approach is required. Today we've been chatting about this on the ISO27k Forum: "Let's assume that the company is willing to accept risks with a potential financial impact less than $50k. Obviously after performing risk assessment, we need to decide which treatment option we should follow. In case when the potential impact of the risk is below $50k - (risk appetite), we should accept the risk, right? My question is: what happens if for some reason, multiple Low Risks (below risk appetite value/already accepted) occur at the same time? Should the Risk Appetite represent an aggregation of all low risks or just reflect the appetite for a single risk?"I suggested considering 'coincident risks' as another entire category or class of risks, some of which may well be above the risk appetite/acceptance threshold even if the individual risks fall below it. It gets worse. There are many other coincidences, errors, failures, issues and exceptional circumstances that could occur - in extremis, it's an infinite set of possibilities given all the permutations and combinations.Our collective failure to identify and take seriously the possibility of a pandemic landed us in the poo we're in now. Even those organisations that did have pandemic controls in place have found the going tougher than anticipated, some discovering that their stockpile of sanitizer and masks had not been properly stored and maintained, and hence was next to useless when called upon. Trust me, it can be a sobering exercise to run a risk workshop focused on rare but extremely impactful events, the outliers that we tend to ignore in routine risk management because it's hard enough dealing with the commonplace extreme events, let alone the rarities. Every well-managed organisation needs to deal sensibly with the scarily vague “something else happens and lands us in serious trouble” situations, when classical scenario planning runs out of steam. There are far too many possibilities to even enumerate, let alone evaluate and treat individually: a more general-purpose approach is required. |
Guideline | |||
| 2020-07-16 13:45:31 | NBlog July 16 - tips on preparing successful proposals (lien direct) |  "The Winning Business Case: how to create a compelling conceptual, analytical and pitch model that your audience will love" is a free eBook from OCEG - more than 20,000 words of advice about generating and pitching a business case for investment in some sort of risk-based project or initiative.The Open Compliance and Ethics Group identifies as: "a global nonprofit think tank that helps organizations reliably achieve objectives, address uncertainty and act with integrity ... We inform, empower, and help advance our 85,000+ members on governance, risk management, and compliance (GRC). Independent of specific professions, we provide content, best practices, education, and certifications to drive leadership and business strategy through the application of the OCEG GRC Capability Model™ and Principled Performance®. An OCEG differentiator, Principled Performance enables the reliable achievement of objectives while addressing uncertainty and acting with integrity. Our members include c-suite, executive, management, and other professionals from small and midsize businesses, international corporations, nonprofits, and government agencies. Founded in 2002, OCEG has locations around the globe."The eBook lays out and explains 15 activities or steps in the process. The sequence and of course the details within each step may vary according to circumstances but it's a comprehensive, well-written document, worth studying if you need to justify investment in risk or security management projects or related areas such as compliance, assurance, cybersecurity, business continuity and ISO27k. With some adjustments, the process could also be valuable for operational budgets too: securing next year's budget for a business department or function is similar to getting approval for a project, especially if management takes a longer-term, strategic view rather than being solely annual in focus. Thinking more broadly still, it could be useful for other kinds of proposal, such as when bidding for consultancy work. Maybe if prospective clients had a bet "The Winning Business Case: how to create a compelling conceptual, analytical and pitch model that your audience will love" is a free eBook from OCEG - more than 20,000 words of advice about generating and pitching a business case for investment in some sort of risk-based project or initiative.The Open Compliance and Ethics Group identifies as: "a global nonprofit think tank that helps organizations reliably achieve objectives, address uncertainty and act with integrity ... We inform, empower, and help advance our 85,000+ members on governance, risk management, and compliance (GRC). Independent of specific professions, we provide content, best practices, education, and certifications to drive leadership and business strategy through the application of the OCEG GRC Capability Model™ and Principled Performance®. An OCEG differentiator, Principled Performance enables the reliable achievement of objectives while addressing uncertainty and acting with integrity. Our members include c-suite, executive, management, and other professionals from small and midsize businesses, international corporations, nonprofits, and government agencies. Founded in 2002, OCEG has locations around the globe."The eBook lays out and explains 15 activities or steps in the process. The sequence and of course the details within each step may vary according to circumstances but it's a comprehensive, well-written document, worth studying if you need to justify investment in risk or security management projects or related areas such as compliance, assurance, cybersecurity, business continuity and ISO27k. With some adjustments, the process could also be valuable for operational budgets too: securing next year's budget for a business department or function is similar to getting approval for a project, especially if management takes a longer-term, strategic view rather than being solely annual in focus. Thinking more broadly still, it could be useful for other kinds of proposal, such as when bidding for consultancy work. Maybe if prospective clients had a bet |
Guideline | ★★★ | ||
| 2020-07-10 19:01:37 | NBlog July 11 - the small but perfectly formed ISMS (lien direct) |  Consulting for small organisations lately to design and implement their ISO/IEC 27001 Information Security Management Systems, resourcing constraints often come to light, particularly the lack of information security expertise and knowledge in-house. I have previously taken this to indicate lack of understanding, support and commitment from senior management, insufficient priority relative to all the other important stuff going on, hence my abiding interest in elaborating on the business case for investing in information risk and security management. Currently, though, I'm gaining a new-found appreciation of the realities of running a small business where even IT may be done on a shoestring, leaving information security way out on a limb. With barely enough cash-flow to sustain the business during COVID-19 and the obvious need to focus on core business activities, it's no surprise if ISO27k implementation and certification projects take a back seat for now. That delaying tactic, however, leaves the business more exposed meanwhile, increasing the probability and impacts of incidents that should have been avoided, prevented or mitigated. It can lead to missed business opportunities and customer defections as they turn to certified competitors rather than waiting for the assurance an ISO/IEC 27001 compliance certificate would bring. It reduces trust and devalues brands. All in all, it's a risky approach.Putting the ISMS implementation on hold is not the only option, however. With some creative thinking, it is possible to keep the project moving along, albeit at a slower pace:A bare-bones minimalist ISMS, barely adequate to satisfy the standard's mandatory requirements, may not deliver all the business benefits of good practice information risk and security management ... but it is both certifiable and better than nothing. A small but perfectly formed ISMS demonstrates the organisation's genuine commitment to information risk and security management, gaining the assurance value of the certificate to third parties without the investment necessary for a full-blown ISMS. Furthermore it is a perfectly valid and sensible starting point, a platform or basis from which to mature the organization's information risk and security management practices as and when it proves its value. It's a pragmatic approach. Being a pragmatist, I like that. Partnering with consultants reduces the pressure on employees, demonstrates management's support (more than just the intention to resume the ISMS project 'at some point'), and keeps up the momentum. Based on our practical experience and knowledge of the standards, we can generally help clients navigate the process by the shortest and most direct route, perhaps making small diversions only where it makes business sense. Speaking for myself, I'm happy to regulate m Consulting for small organisations lately to design and implement their ISO/IEC 27001 Information Security Management Systems, resourcing constraints often come to light, particularly the lack of information security expertise and knowledge in-house. I have previously taken this to indicate lack of understanding, support and commitment from senior management, insufficient priority relative to all the other important stuff going on, hence my abiding interest in elaborating on the business case for investing in information risk and security management. Currently, though, I'm gaining a new-found appreciation of the realities of running a small business where even IT may be done on a shoestring, leaving information security way out on a limb. With barely enough cash-flow to sustain the business during COVID-19 and the obvious need to focus on core business activities, it's no surprise if ISO27k implementation and certification projects take a back seat for now. That delaying tactic, however, leaves the business more exposed meanwhile, increasing the probability and impacts of incidents that should have been avoided, prevented or mitigated. It can lead to missed business opportunities and customer defections as they turn to certified competitors rather than waiting for the assurance an ISO/IEC 27001 compliance certificate would bring. It reduces trust and devalues brands. All in all, it's a risky approach.Putting the ISMS implementation on hold is not the only option, however. With some creative thinking, it is possible to keep the project moving along, albeit at a slower pace:A bare-bones minimalist ISMS, barely adequate to satisfy the standard's mandatory requirements, may not deliver all the business benefits of good practice information risk and security management ... but it is both certifiable and better than nothing. A small but perfectly formed ISMS demonstrates the organisation's genuine commitment to information risk and security management, gaining the assurance value of the certificate to third parties without the investment necessary for a full-blown ISMS. Furthermore it is a perfectly valid and sensible starting point, a platform or basis from which to mature the organization's information risk and security management practices as and when it proves its value. It's a pragmatic approach. Being a pragmatist, I like that. Partnering with consultants reduces the pressure on employees, demonstrates management's support (more than just the intention to resume the ISMS project 'at some point'), and keeps up the momentum. Based on our practical experience and knowledge of the standards, we can generally help clients navigate the process by the shortest and most direct route, perhaps making small diversions only where it makes business sense. Speaking for myself, I'm happy to regulate m |
Guideline | |||
| 2020-07-09 12:53:22 | NBlog July 9 - the day the Earth stopped spinning (lien direct) | Here's something we don't see very often, well for no more than a fraction of a second, normally, discreetly tucked away at the bottom left corner of the browser window. Today was different. Today the message was there long enough for me to grab that little screen shot.Meanwhile, I had to waits e v e r a ll o n gm i n u t e sfor the Google search results to appear. Minutes I tell you, minutes! Several of them! Shock! Horror! My little world stood still for a moment, my online life on hold.In an instant, I realised that not only have we grown accustomed to near instantaneous access to Google's gigantic Web catalogue, but that I am actually quite dependent on it. I do sometimes use other search engines but I always scurry back to Google because it works well, almost always. The only reason I am bloggering on about it here is that a Google service failing is so unusual, exceptional in fact. Almost unheard of. The technology to achieve that outstanding level of service in terms of capacity, performance and reliability is awesome in both scale and cost, and yet most Google services appear free to use (well OK, they're not really free: we provide our search terms and a fair amount of personal information in return, plus Google's commercial services are charged at commercial rates. But at least we can opt out if we choose). Today was different. Today the message was there long enough for me to grab that little screen shot.Meanwhile, I had to waits e v e r a ll o n gm i n u t e sfor the Google search results to appear. Minutes I tell you, minutes! Several of them! Shock! Horror! My little world stood still for a moment, my online life on hold.In an instant, I realised that not only have we grown accustomed to near instantaneous access to Google's gigantic Web catalogue, but that I am actually quite dependent on it. I do sometimes use other search engines but I always scurry back to Google because it works well, almost always. The only reason I am bloggering on about it here is that a Google service failing is so unusual, exceptional in fact. Almost unheard of. The technology to achieve that outstanding level of service in terms of capacity, performance and reliability is awesome in both scale and cost, and yet most Google services appear free to use (well OK, they're not really free: we provide our search terms and a fair amount of personal information in return, plus Google's commercial services are charged at commercial rates. But at least we can opt out if we choose). |
||||
| 2020-07-06 17:45:47 | NBlog July 6 - of APTs and RPTs (lien direct) |  Do you recall when APTs were A Thing? Advanced Persistent Threats were exemplified by Stuxnet, a species of malware that was stealthy enough to penetrate the defences of an Iranian nuclear fuel processing plant ten years ago, persistent enough to undermine numerous layers of control, and sophisticated enough to over-speed and wreck the centrifuges without alerting the plant operators until the damage was done. We seldom hear of weapons-grade APTs these days, suggesting they are no longer newsworthy or effective. Maybe they have gone the way of the trebuchet or musket ... but I believe it's much more likely that APTs have become even more sophisticated, stealthier and more damaging now than ever before, especially given the ascendance of IoT, IIoT and 'cyber-physical systems'. Now, Things are A Thing.Meanwhile, we are frequently constantly assaulted by ordinary, conventional, old-school malware - Retarded Persistent Threats as it were.In contrast to APTs, RPTs are relatively crude and commonplace - more blunderbuss than sniper's rifle but every bit as devastating at close range. Despite becoming increasingly sophisticated and capable, they are presumably well behind APTs, especially given governmental investments in cyber capabilities as part of national defence spending.RPTs 'persist' in the sense that they steadfastly refuse to go away. Bog-standard malware has dogged computer systems, networks and users since the 1980s. It has grown in prevalence at least as fast as IT, and in some ways it has driven advances in IT. The few percent of system resources needed to run today's antivirus packages and firewalls would surely have brought systems from previous decades to their little silicon knees.Whereas most RPT incidents are, well, incidental in relation to our global society, they threaten the very large number of vulnerable systems, individuals and organisations out there. It has become painfully obvious during COVID-19 that vanishingly few organisations stand alone, immune to the global repercussions. We are all entangled in, and highly dependent upon, a global mesh of information, goods and services. Just as a single COVID case causes knock-on effects, an RPT incident creates ripples.We're lucky that, so far, neither real-world nor Do you recall when APTs were A Thing? Advanced Persistent Threats were exemplified by Stuxnet, a species of malware that was stealthy enough to penetrate the defences of an Iranian nuclear fuel processing plant ten years ago, persistent enough to undermine numerous layers of control, and sophisticated enough to over-speed and wreck the centrifuges without alerting the plant operators until the damage was done. We seldom hear of weapons-grade APTs these days, suggesting they are no longer newsworthy or effective. Maybe they have gone the way of the trebuchet or musket ... but I believe it's much more likely that APTs have become even more sophisticated, stealthier and more damaging now than ever before, especially given the ascendance of IoT, IIoT and 'cyber-physical systems'. Now, Things are A Thing.Meanwhile, we are frequently constantly assaulted by ordinary, conventional, old-school malware - Retarded Persistent Threats as it were.In contrast to APTs, RPTs are relatively crude and commonplace - more blunderbuss than sniper's rifle but every bit as devastating at close range. Despite becoming increasingly sophisticated and capable, they are presumably well behind APTs, especially given governmental investments in cyber capabilities as part of national defence spending.RPTs 'persist' in the sense that they steadfastly refuse to go away. Bog-standard malware has dogged computer systems, networks and users since the 1980s. It has grown in prevalence at least as fast as IT, and in some ways it has driven advances in IT. The few percent of system resources needed to run today's antivirus packages and firewalls would surely have brought systems from previous decades to their little silicon knees.Whereas most RPT incidents are, well, incidental in relation to our global society, they threaten the very large number of vulnerable systems, individuals and organisations out there. It has become painfully obvious during COVID-19 that vanishingly few organisations stand alone, immune to the global repercussions. We are all entangled in, and highly dependent upon, a global mesh of information, goods and services. Just as a single COVID case causes knock-on effects, an RPT incident creates ripples.We're lucky that, so far, neither real-world nor |
Malware | |||
| 2020-06-27 09:50:37 | NBlog June 26 - things an ISO27k SoA doesn\'t say (lien direct) | According to ISO/IEC 27001:2013, organisations are supposed to consider all the information security controls outlined in Annex A, confirming that they have done so by preparing a Statement of Applicability "that contains the necessary controls .... and justification for inclusions, [states] whether they are implemented or not, and [gives] the justification for exclusions of controls from Annex A".That ineptly-worded requirement in a poorly-constructed and in fact self-contradictory clause of the standard is generally interpreted, in practice, in the form of an SoA table with a row for every Annex A control* and columns for applicability, justifications and implementation status of each control*.Three exclusive states are generally used. Each control* is either:Applicable and implemented; orApplicable but not implemented; orNot applicable.... implying a simple decision tree with just two binary questions: First, is the control* applicable (yes or no)?If the control* is applicable, is it implemented (yes or no)?Hmmmm, that's all very well in theory but here are some of the options I've heard as an auditor, or thought if not expressed as an auditee:Applicable under some circumstances – the control applies in specific situations only and is not generally applicablePartially applicable – the control is not enough to mitigate the risk and needs to be modified and/or complemented by other controls; as described, it's not really what we want to doApplicable and partially implemented – we did this at least onceApplicable and allegedly implemented – someone claims to have done this at least onceApplicable and apparently implemented - someone genuinely but naively and perhaps inadvisedly believes they have truly nailed this oneImplemented but inapplicable – to pacify out auditors, we “just did it” ... even th | ||||
| 2020-06-20 18:13:14 | NBlog April 30 - blursday metrics (lien direct) |  The past 6 weeks or so have been quite surreal for us, and I guess for you too. Yesterday we went shopping, leaving our property for the first time since our shopping expedition a week before NZ went into "level 4" lockdown. As of a couple of days ago, we're now at "level 3". Don't ask me what the differences are between the levels, nor what levels 2, 1 and 0 might look like. All I know is that it was a relief to see other people out and about, most of us making obvious efforts to keep our distance. The new normal isn't so bad as I imagined, certainly nothing like a zombie apocalypse or police state.Those 6 weeks blurred into one. At some point I stopped counting up and blogging about the passing days ... and eventually started counting down to the end of "level 4", or more importantly the impending exhaustion of some of our most essential supplies: coffee, wine and chocolate. Some valuable lessons there for when we replenish our "earthquake kit"!Meanwhile, NZ's COVID-19 numbers have apparently peaked and fallen. I say "apparently" because the metrics are dubious - again, that's not just our situation in NZ, but a global issue. Differences in the way the metrics are defined, collected and interpreted are layered on top of cultural/national differences in the populations, health systems, economies and more. In particular, there are substantial differences in the amount and quality (reliability, utility) of COVID-19 testing, which is important because COVID-19 infections are cryptic: some of us are infected but have little to no symptoms and hence we don't know it, at least not right now (during the incubation period, the virus multiplies and the symptoms may - or may not - show). Some aren't so lucky and a few are seriously, even gravely ill, at which point the infection is obvious and hard (but not impossible) to ignore or discount. There's still the issue that it appears the most vulnerable patients have other "underlying medical conditions", which is the phrase of the moment and points to yet another issue with the metrics.Two valuable metrics in infectious disease are:The rate of spread of the infection throughout the population. This is akin to the 'probability' factor in classical risk management. Essentially, it's a gross measure of the chances of anyone becoming infected. For the reasons just stated, it is tricky to measure in practice.The proportion of infected people who become sick - more specifically, sick enough to show symptoms, affect their lives, require treatment and hospitalisation, a The past 6 weeks or so have been quite surreal for us, and I guess for you too. Yesterday we went shopping, leaving our property for the first time since our shopping expedition a week before NZ went into "level 4" lockdown. As of a couple of days ago, we're now at "level 3". Don't ask me what the differences are between the levels, nor what levels 2, 1 and 0 might look like. All I know is that it was a relief to see other people out and about, most of us making obvious efforts to keep our distance. The new normal isn't so bad as I imagined, certainly nothing like a zombie apocalypse or police state.Those 6 weeks blurred into one. At some point I stopped counting up and blogging about the passing days ... and eventually started counting down to the end of "level 4", or more importantly the impending exhaustion of some of our most essential supplies: coffee, wine and chocolate. Some valuable lessons there for when we replenish our "earthquake kit"!Meanwhile, NZ's COVID-19 numbers have apparently peaked and fallen. I say "apparently" because the metrics are dubious - again, that's not just our situation in NZ, but a global issue. Differences in the way the metrics are defined, collected and interpreted are layered on top of cultural/national differences in the populations, health systems, economies and more. In particular, there are substantial differences in the amount and quality (reliability, utility) of COVID-19 testing, which is important because COVID-19 infections are cryptic: some of us are infected but have little to no symptoms and hence we don't know it, at least not right now (during the incubation period, the virus multiplies and the symptoms may - or may not - show). Some aren't so lucky and a few are seriously, even gravely ill, at which point the infection is obvious and hard (but not impossible) to ignore or discount. There's still the issue that it appears the most vulnerable patients have other "underlying medical conditions", which is the phrase of the moment and points to yet another issue with the metrics.Two valuable metrics in infectious disease are:The rate of spread of the infection throughout the population. This is akin to the 'probability' factor in classical risk management. Essentially, it's a gross measure of the chances of anyone becoming infected. For the reasons just stated, it is tricky to measure in practice.The proportion of infected people who become sick - more specifically, sick enough to show symptoms, affect their lives, require treatment and hospitalisation, a |
||||
| 2020-06-18 07:58:14 | NBlog June 17 - phishing evolution (lien direct) | The Interweb drums have been beating out news of an upsurge in phishing attacks over the past month or so. I've certainly had more than the normal number of things along these lines lately: [if gte vml 1]> [if !vml]-->[endif]--> As usual, these are relatively crude and (for most reasonably alert people) easy to spot thanks to the obvious spelling and grammatical errors, often using spurious technobabble and urgency as well as the fake branding and sender email address in an attempt to trick victims. The 'blocked emails' and 'storage limit' memes are popular in my spam box right now, suggesting that these are basic phishing-as-a-service or phishing-kit products being used by idiots to lure, hook, land and gut other idiots. They are, however, using my first name in place of “Dear subscriber” or “Hello, how are you doing?” that we used to see, implying the use of mailmerge-type content customisation with databases of email addresses and other info on potential victims*.Moving up the scale, some current phishing attempts are more sophisticated, more convincing. Sometimes it's just a lucky coincidence e.g. when the lure glints alluringly because it just happens to mention something I am currently doing - for example if I am dealing with American Express o [if gte vml 1]> [if !vml]-->[endif]--> As usual, these are relatively crude and (for most reasonably alert people) easy to spot thanks to the obvious spelling and grammatical errors, often using spurious technobabble and urgency as well as the fake branding and sender email address in an attempt to trick victims. The 'blocked emails' and 'storage limit' memes are popular in my spam box right now, suggesting that these are basic phishing-as-a-service or phishing-kit products being used by idiots to lure, hook, land and gut other idiots. They are, however, using my first name in place of “Dear subscriber” or “Hello, how are you doing?” that we used to see, implying the use of mailmerge-type content customisation with databases of email addresses and other info on potential victims*.Moving up the scale, some current phishing attempts are more sophisticated, more convincing. Sometimes it's just a lucky coincidence e.g. when the lure glints alluringly because it just happens to mention something I am currently doing - for example if I am dealing with American Express o |
Ransomware Spam Guideline | |||
| 2020-05-25 08:14:25 | NBlog May 25 - gap-and-fill (lien direct) |  Aside from the conventional 'gap analysis', it is possible to do a 'fill analysis' to discover the things that the organization is doing successfully already – its strengths, foundations on which to build. The analytical processes are almost the same but a fill analysis aims to identify, learn from and expand upon the strengths - the positives - whereas a gap analysis involves hunting down and addressing the weaknesses - the negatives.These are complementary not alternative approaches.So, for instance, if the organization is poor at compliance, OK at policies and excellent at impact assessment: A gap analysis would focus on closing the compliance gaps; Aside from the conventional 'gap analysis', it is possible to do a 'fill analysis' to discover the things that the organization is doing successfully already – its strengths, foundations on which to build. The analytical processes are almost the same but a fill analysis aims to identify, learn from and expand upon the strengths - the positives - whereas a gap analysis involves hunting down and addressing the weaknesses - the negatives.These are complementary not alternative approaches.So, for instance, if the organization is poor at compliance, OK at policies and excellent at impact assessment: A gap analysis would focus on closing the compliance gaps; |
Guideline | |||
| 2020-05-16 17:38:09 | NBlog May 16 - adjusting to the new normal (lien direct) |  According to alert AA20-133A from US-CERT:"The U.S. Government has reported that the following vulnerabilities are being routinely exploited by sophisticated foreign cyber actors in 2020:Malicious cyber actors are increasingly targeting unpatched Virtual Private Network vulnerabilities. An arbitrary code execution vulnerability in Citrix VPN appliances, known as CVE-2019-19781, has been detected in exploits in the wild.An arbitrary file reading vulnerability in Pulse Secure VPN servers, known as CVE-2019-11510, continues to be an attractive target for malicious actors.March 2020 brought an abrupt shift to work-from-home that necessitated, for many organizations, rapid deployment of cloud collaboration services, such as Microsoft Office 365 (O365). Malicious cyber actors are targeting organizations whose hasty deployment of Microsoft O365 may have led to oversights in security configurations and vulnerable to attack.Cybersecurity weaknesses-such as poor employee education on social engineering attacks and a lack of system recovery and contingency plans-have continued to make organizations susceptible to ransomware attacks in 2020."Well whadyaknow?The US government blames "sophisticated foreign cyber actors" - the usual xenophobic, somewhat paranoid and conspiratorial stance towards those filthy rotten foreigners, desperately attacking little old US of A (today's version of reds under beds I guess);"Unpatched" VPNs and insecurely configured Office 365 services are being targeted, implicitly blaming customers for failing to patch and configure the software correctly, blithely ignoring the fact that it was US-based software vendors behind the systems that required patching and configuring to address exploitable vulnerabilities; According to alert AA20-133A from US-CERT:"The U.S. Government has reported that the following vulnerabilities are being routinely exploited by sophisticated foreign cyber actors in 2020:Malicious cyber actors are increasingly targeting unpatched Virtual Private Network vulnerabilities. An arbitrary code execution vulnerability in Citrix VPN appliances, known as CVE-2019-19781, has been detected in exploits in the wild.An arbitrary file reading vulnerability in Pulse Secure VPN servers, known as CVE-2019-11510, continues to be an attractive target for malicious actors.March 2020 brought an abrupt shift to work-from-home that necessitated, for many organizations, rapid deployment of cloud collaboration services, such as Microsoft Office 365 (O365). Malicious cyber actors are targeting organizations whose hasty deployment of Microsoft O365 may have led to oversights in security configurations and vulnerable to attack.Cybersecurity weaknesses-such as poor employee education on social engineering attacks and a lack of system recovery and contingency plans-have continued to make organizations susceptible to ransomware attacks in 2020."Well whadyaknow?The US government blames "sophisticated foreign cyber actors" - the usual xenophobic, somewhat paranoid and conspiratorial stance towards those filthy rotten foreigners, desperately attacking little old US of A (today's version of reds under beds I guess);"Unpatched" VPNs and insecurely configured Office 365 services are being targeted, implicitly blaming customers for failing to patch and configure the software correctly, blithely ignoring the fact that it was US-based software vendors behind the systems that required patching and configuring to address exploitable vulnerabilities; |
Ransomware Vulnerability Patching | |||
| 2020-05-03 13:19:31 | NBlog May 3 - COVID-19 is like infosec because ... (lien direct) |  ... Despite the history and the experts' warnings that a pandemic was likely to happen again at some point, it turns out we were ill-prepared for it, not as resilient as we thought and should have been... Experts disagree on the details, sometimes even the fundamentals, and love their models... Commentary and advice is plentiful, but sound, reasoned, appropriate advice by competent advisors is at a premium and partly lost in the noise... Whereas information is important, information integrity, quality and trustworthiness are vital, hence there is also value in assurance and other information controls, including the pundits' reputations and credibility... Most of us are non-experts, hence it is tricky for us to distinguish fact from fiction and make sense of conflicting advice ... Perfect, complete information is seldom available, so there are bound to be compromises and errors - and we should be ready to spot and deal with them too... Controls against COVID-19 are imperfect, at best; some are purely for appearance sake; some are as much use as a bubble level in space; others are literally worse than useless (the cure really can be worse than the disease!); in most cases, we simply don't know how well they will work in practice... Many people and organizations struggle to cope with a serious crisis, whereas some shine and thrive - but even the best may crumble at some point... They are all about risk and risk management, not just protection, control, safety and security: we are where we are partly as a result of our prior decisions about priorities, resources etc. ... We are mutually dependent and hence collectively vulnerable since total isolation is impract ... Despite the history and the experts' warnings that a pandemic was likely to happen again at some point, it turns out we were ill-prepared for it, not as resilient as we thought and should have been... Experts disagree on the details, sometimes even the fundamentals, and love their models... Commentary and advice is plentiful, but sound, reasoned, appropriate advice by competent advisors is at a premium and partly lost in the noise... Whereas information is important, information integrity, quality and trustworthiness are vital, hence there is also value in assurance and other information controls, including the pundits' reputations and credibility... Most of us are non-experts, hence it is tricky for us to distinguish fact from fiction and make sense of conflicting advice ... Perfect, complete information is seldom available, so there are bound to be compromises and errors - and we should be ready to spot and deal with them too... Controls against COVID-19 are imperfect, at best; some are purely for appearance sake; some are as much use as a bubble level in space; others are literally worse than useless (the cure really can be worse than the disease!); in most cases, we simply don't know how well they will work in practice... Many people and organizations struggle to cope with a serious crisis, whereas some shine and thrive - but even the best may crumble at some point... They are all about risk and risk management, not just protection, control, safety and security: we are where we are partly as a result of our prior decisions about priorities, resources etc. ... We are mutually dependent and hence collectively vulnerable since total isolation is impract |
Guideline | |||
| 2020-04-11 13:51:06 | NBlog April 11 - NZ lockdown day X of N (lien direct) |  There's a slew of social media posts promoting business continuity management, resilience, ISO 22301 and the like, right now, during COVID-19. That's like promoting birth control to a family of twenty. It's 20-20 hindsight.Now is the time to promote the planning and preparations needed to cope with the aftermath of COVID-19, taking account of things such as:Lingering uncertainties/doubts about business, the economy, life, health, management and workforce capabilities/competence, supply chains ... whatever Inertia - the additional effort needed to spin-up to normal speeds after the go-slow Low morale resulting from isolation depression, sickness, stress, over-work etc.Lack of motivation to 'get back into the swing of things' as if nothing happenedVarious adjustments to the new working, home and social lifeCoping with losses of all sorts (money, people, jobs, opportunities ...)Realisation (for some) that working from home beats working from workFamilial, cultural and social factorsLong term effects such as paying back the loans needed to get throughLearning hard lessons from the incident, making genuine efforts to improve business continuity arrangements for the next one e.g. investing in risk management, resilience, contingency, security, change management Introspection (busily getting our own house in order) diverting attention from the (changed) outside world - new challenges, new opportunitiesThe practicalities of getting back into the nine-to-five routine and dealing with a backlog of problems, deferred work, various mini-crises and shortages etc.Things will eventually settle down into the (new) normal. Organizations that make the transition There's a slew of social media posts promoting business continuity management, resilience, ISO 22301 and the like, right now, during COVID-19. That's like promoting birth control to a family of twenty. It's 20-20 hindsight.Now is the time to promote the planning and preparations needed to cope with the aftermath of COVID-19, taking account of things such as:Lingering uncertainties/doubts about business, the economy, life, health, management and workforce capabilities/competence, supply chains ... whatever Inertia - the additional effort needed to spin-up to normal speeds after the go-slow Low morale resulting from isolation depression, sickness, stress, over-work etc.Lack of motivation to 'get back into the swing of things' as if nothing happenedVarious adjustments to the new working, home and social lifeCoping with losses of all sorts (money, people, jobs, opportunities ...)Realisation (for some) that working from home beats working from workFamilial, cultural and social factorsLong term effects such as paying back the loans needed to get throughLearning hard lessons from the incident, making genuine efforts to improve business continuity arrangements for the next one e.g. investing in risk management, resilience, contingency, security, change management Introspection (busily getting our own house in order) diverting attention from the (changed) outside world - new challenges, new opportunitiesThe practicalities of getting back into the nine-to-five routine and dealing with a backlog of problems, deferred work, various mini-crises and shortages etc.Things will eventually settle down into the (new) normal. Organizations that make the transition |
||||
| 2020-04-02 12:16:40 | NBlog April 2 - NZ lockdown day 8 of N (lien direct) | These are the headline metrics noted by the NZ Ministry of Health:Confirmed and probable cases of COVID-19The number of people who have recoveredHow many people are (and have been) in hospitalCases by District Health Board, and by age and gender.The metrics are updated daily and reported dutifully by the NZ news media, but what use are they, in fact? What information and knowledge can we glean from the data? Here is the current summary (snapshot at 7am on April 2nd):  There are no detailed definiti There are no detailed definiti |
||||
| 2020-03-31 19:48:03 | NBlog March 31 - NZ lockdown day 6 of N (lien direct) |  The NZ politicians and news media are updating us daily on selected COVID-19 statistics (metrics), particularly concerning NZ of course but also the global situation. Countries with the largest numbers (regardless of which metric) are naturally media-fodder.It's fair to ask, though, what all these numbers mean, why we should care about them, and why they are being reported rather than others.As with information risk and security metrics, there are various audiences of the metrics with numerous concerns, objectives, purposes, uses for or interests in them e.g.:Those actually managing the national response, day-by-day, need to know how they are doing relative to their plans and intentions, and how they might improveCentral and local government politicians giving oversight and direction to the response ... with a keen eye on their popular standing, given that an election is in the offing (unless deferred) ... plus administrators in the civil serviceThe Treasury and Inland Revenue, overseeing the financial aspects of NZ's impacts from COVID-19, not least the costs of the controls and handouts intended to keep businesses and other organizations afloat, the national debt and tax burden on those who make it through The stock market and financial industry generally - interested for the same reasonsThe NZ general public with a personal, familial and general interest in the situation, mostly concerned non-specialistsThe news media - specifically journalists, editors and proprietors The social media - specifically bloggers, Twits, Facebookers, community members and influencers, commentators and assorted 'interested parties' ... including me Specialists in public health, infectious disease, virology, epidemiology, genetics, risk and incident management etc.Healthcare professionals - in particular those planning for, leading and administering the public health response to COVID-19The police and justice system, largely responsible for administering the lockdown and dealing with noncompliance The NZ politicians and news media are updating us daily on selected COVID-19 statistics (metrics), particularly concerning NZ of course but also the global situation. Countries with the largest numbers (regardless of which metric) are naturally media-fodder.It's fair to ask, though, what all these numbers mean, why we should care about them, and why they are being reported rather than others.As with information risk and security metrics, there are various audiences of the metrics with numerous concerns, objectives, purposes, uses for or interests in them e.g.:Those actually managing the national response, day-by-day, need to know how they are doing relative to their plans and intentions, and how they might improveCentral and local government politicians giving oversight and direction to the response ... with a keen eye on their popular standing, given that an election is in the offing (unless deferred) ... plus administrators in the civil serviceThe Treasury and Inland Revenue, overseeing the financial aspects of NZ's impacts from COVID-19, not least the costs of the controls and handouts intended to keep businesses and other organizations afloat, the national debt and tax burden on those who make it through The stock market and financial industry generally - interested for the same reasonsThe NZ general public with a personal, familial and general interest in the situation, mostly concerned non-specialistsThe news media - specifically journalists, editors and proprietors The social media - specifically bloggers, Twits, Facebookers, community members and influencers, commentators and assorted 'interested parties' ... including me Specialists in public health, infectious disease, virology, epidemiology, genetics, risk and incident management etc.Healthcare professionals - in particular those planning for, leading and administering the public health response to COVID-19The police and justice system, largely responsible for administering the lockdown and dealing with noncompliance |
Guideline | |||
| 2020-03-30 16:47:35 | NBlog March 30 - NZ lockdown day 5 of N (lien direct) |  Our "broadband" is gradually becoming narrower by the day as an increasing number of Kiwis on staycation are working from home, downloading/watching videos, playing online games or whatever.Normally I listen to online music stations while working and I still can: thanks to bufferuffering and the relatively little bandwidth required, streaming audio still works OK ... but instead I'm listening to my music CDs for a change, figuring there are those out there who need the Interweb bandwidth more than me.Besides which, I like my CDs and it's easy to skip the duff tracks. Our "broadband" is gradually becoming narrower by the day as an increasing number of Kiwis on staycation are working from home, downloading/watching videos, playing online games or whatever.Normally I listen to online music stations while working and I still can: thanks to bufferuffering and the relatively little bandwidth required, streaming audio still works OK ... but instead I'm listening to my music CDs for a change, figuring there are those out there who need the Interweb bandwidth more than me.Besides which, I like my CDs and it's easy to skip the duff tracks. |
||||
| 2020-03-29 22:03:55 | NBlog March 29 - NZ lockdown day 4 of N (lien direct) |  Yesterday I wrote about exploiting/making the most of opportunities that arise in a crisis. Here's an example - using COVID-19 as an analogy to help explain a concept.A question came up on the ISO27k Forum about how to handle 'primary and secondary assets' in the risk assessment processes described by ISO/IEC 27005. This is my response ...“Primary assets (business processes and activities, information) … usually the core processes and information of the activity in the scope” [ISO/IEC 27005:2018 section B.1.2] are the focal point: that's what we need to protect. However, in order to do that, we also need to take care of other matters, including the supporting/enabling information systems, networks etc. Those have someintrinsic value (e.g. used but now redundant servers can be upgraded, redeployed, sold or scrapped) but their main value relates to their roles in relation to the primary assets.A topical analogy is “health” – an asset we all need to protect. ]For virtually everyone, it's clearly primary - #1, The Most Important Thing Of All. There are many threats to our health (not just coronavirus!) and we have many vulnerabilities (e.g. we need to breathe, we have mucosa, we need to interact with the world around us to gather essential supplies …), while the impacts of health incidents are many and varied (from 'feeling a bit off colour' to death). We can't directly protect “health” (which is intangible and cloudy), but we can work on various related aspects that, in turn, support good health – like for instance staying out of range of coronavirus and flu sufferers coughing and sneezing; staying well nourished; exercising to maintain physical fitness; thinking about hard stuff like this to maintain mental agility; being vigilant for the symptoms of poor or deteriorating health; having the health services, docs, drugs, respirators etc. to increase our ability to survive disease etc. In infosec terms, that's a blend of preventive, detective and corrective controls designed to protect our continued integrity and availability Yesterday I wrote about exploiting/making the most of opportunities that arise in a crisis. Here's an example - using COVID-19 as an analogy to help explain a concept.A question came up on the ISO27k Forum about how to handle 'primary and secondary assets' in the risk assessment processes described by ISO/IEC 27005. This is my response ...“Primary assets (business processes and activities, information) … usually the core processes and information of the activity in the scope” [ISO/IEC 27005:2018 section B.1.2] are the focal point: that's what we need to protect. However, in order to do that, we also need to take care of other matters, including the supporting/enabling information systems, networks etc. Those have someintrinsic value (e.g. used but now redundant servers can be upgraded, redeployed, sold or scrapped) but their main value relates to their roles in relation to the primary assets.A topical analogy is “health” – an asset we all need to protect. ]For virtually everyone, it's clearly primary - #1, The Most Important Thing Of All. There are many threats to our health (not just coronavirus!) and we have many vulnerabilities (e.g. we need to breathe, we have mucosa, we need to interact with the world around us to gather essential supplies …), while the impacts of health incidents are many and varied (from 'feeling a bit off colour' to death). We can't directly protect “health” (which is intangible and cloudy), but we can work on various related aspects that, in turn, support good health – like for instance staying out of range of coronavirus and flu sufferers coughing and sneezing; staying well nourished; exercising to maintain physical fitness; thinking about hard stuff like this to maintain mental agility; being vigilant for the symptoms of poor or deteriorating health; having the health services, docs, drugs, respirators etc. to increase our ability to survive disease etc. In infosec terms, that's a blend of preventive, detective and corrective controls designed to protect our continued integrity and availability |
||||
| 2020-03-28 10:50:40 | NBlog March 28 - NZ lockdown day 3 of N (lien direct) |  With a bit of lateral thinking, there are ways to hook-in to and even exploit the COVID-19 brouhaha. More time for reflection is one of the advantages of the lockdown, for some of us at least. Many organizations, for instance, have sent out customer comms about what they are doing to maintain services during/despite the pandemic. Although most are matter-of-fact and boring (maybe not even branded), some are more creative and engaging, even acknowledging that COVID is not going to blow over in a couple of weeks. Most are generic, superficial and bland, often supplier-focused, whereas some are personalised, unique, detailed and customer-focused. Most appear to be one-off broadcasts, hurriedly cobbled together by teams immersed in the chaos and confusion, then slowly refined and authorized. Not many that I've seen so far even hint that there might be more to come. The odd tinge of humour is welcome. Unlike the vast majority of incidents and crises, a global incident such as COVID-19 or world war extends way beyond the individual organization, even its primary supply chain. The conventional incident and crisis management comms, often pre-canned as templated press releases, may not therefore be appropriate, relevant and helpful. The context, and hence the messages, are materially different. Even the anticipated modes of delivery are not guaranteed if, say, a cyberwar takes down the Internet.I'm exploring some of the many lessons here for those of us vigilant enough to notice and think about what's going on around us, rather than being totally introspective and absorbed by dealing with the crisis. We're lucky in that we don't feel as if we are in immediate danger, we were well prepared for this and we're resilient ... which frees us from the grief and torment that others are experiencing and allows us to think clearly, but our situation could easily change if someone close to us (whether literally or figuratively) gets sick, or if the global or national crisis deepens. With a bit of lateral thinking, there are ways to hook-in to and even exploit the COVID-19 brouhaha. More time for reflection is one of the advantages of the lockdown, for some of us at least. Many organizations, for instance, have sent out customer comms about what they are doing to maintain services during/despite the pandemic. Although most are matter-of-fact and boring (maybe not even branded), some are more creative and engaging, even acknowledging that COVID is not going to blow over in a couple of weeks. Most are generic, superficial and bland, often supplier-focused, whereas some are personalised, unique, detailed and customer-focused. Most appear to be one-off broadcasts, hurriedly cobbled together by teams immersed in the chaos and confusion, then slowly refined and authorized. Not many that I've seen so far even hint that there might be more to come. The odd tinge of humour is welcome. Unlike the vast majority of incidents and crises, a global incident such as COVID-19 or world war extends way beyond the individual organization, even its primary supply chain. The conventional incident and crisis management comms, often pre-canned as templated press releases, may not therefore be appropriate, relevant and helpful. The context, and hence the messages, are materially different. Even the anticipated modes of delivery are not guaranteed if, say, a cyberwar takes down the Internet.I'm exploring some of the many lessons here for those of us vigilant enough to notice and think about what's going on around us, rather than being totally introspective and absorbed by dealing with the crisis. We're lucky in that we don't feel as if we are in immediate danger, we were well prepared for this and we're resilient ... which frees us from the grief and torment that others are experiencing and allows us to think clearly, but our situation could easily change if someone close to us (whether literally or figuratively) gets sick, or if the global or national crisis deepens. |
||||
| 2020-03-27 10:00:15 | NBlog March 27 - NZ lockdown day 2 of N (lien direct) |  I said yesterday that we've identified our home essentials - things such as food, fuel, booze, the web etc. - and stocked up accordingly, like any sensible family would do. Those are the thing we all need. Pretty obvious really and not particularly interesting.But what about the things we don't need? What would we rather not have during this pandemic, or in general? While painstakingly giving my chisels a long-overdue regrind and manual sharpen in the man-shed, I came up with the following A-to-Z list. These are the things I can do without:AccidentsAches & painsAlzheimer'sArmed forcesAuthoritiesBad backsBad breathBad debtsBad decisionsBad designBad dreamsBad engineeringBad habitsBad healthBad memoriesBadges & thumbs-upBadness generallyBiasBrambleBreakagesBriscoes salesBroken promisesCancerCheatingClassroomsClimate changeCoffinsCompliance enforcementConcertsConstraintsCrappy software & patching I said yesterday that we've identified our home essentials - things such as food, fuel, booze, the web etc. - and stocked up accordingly, like any sensible family would do. Those are the thing we all need. Pretty obvious really and not particularly interesting.But what about the things we don't need? What would we rather not have during this pandemic, or in general? While painstakingly giving my chisels a long-overdue regrind and manual sharpen in the man-shed, I came up with the following A-to-Z list. These are the things I can do without:AccidentsAches & painsAlzheimer'sArmed forcesAuthoritiesBad backsBad breathBad debtsBad decisionsBad designBad dreamsBad engineeringBad habitsBad healthBad memoriesBadges & thumbs-upBadness generallyBiasBrambleBreakagesBriscoes salesBroken promisesCancerCheatingClassroomsClimate changeCoffinsCompliance enforcementConcertsConstraintsCrappy software & patching |
||||
| 2020-03-26 09:27:21 | NBlog March 26 - NZ lockdown day 1 of N (lien direct) | From midnight last night, New Zealand is now at civil emergency "stage 4", which means all except essential services personnel are supposed to stay isolated at home for about a month. The official NZ government list of essential services appears to have been finalised and published hastily. Naturally, 'the authorities' consider themselves essential as overnight we've become a police state: police and courts are working through the lockdown, albeit providing limited services, health and immigration/customs services too. What will happen as their workers are or suspect themselves to be infected with coronavirus is unclear at this point. Presumably they have contingency plans, plus controls to limit the spread of infection within police stations, court houses, hospitals, customs halls, mail sorting offices etc. ... but staffing and service problems are entirely possible as the lockdown continues.Since they aren't entirely self-contained, there's also a second tier of organizations supporting the essential services and here the lines get blurry. For example, police cars need tyres, fuel and servicing. Today we will be revising our personal list of essential home services in light of the lockdown. More tomorrow. The official NZ government list of essential services appears to have been finalised and published hastily. Naturally, 'the authorities' consider themselves essential as overnight we've become a police state: police and courts are working through the lockdown, albeit providing limited services, health and immigration/customs services too. What will happen as their workers are or suspect themselves to be infected with coronavirus is unclear at this point. Presumably they have contingency plans, plus controls to limit the spread of infection within police stations, court houses, hospitals, customs halls, mail sorting offices etc. ... but staffing and service problems are entirely possible as the lockdown continues.Since they aren't entirely self-contained, there's also a second tier of organizations supporting the essential services and here the lines get blurry. For example, police cars need tyres, fuel and servicing. Today we will be revising our personal list of essential home services in light of the lockdown. More tomorrow. |
||||
| 2020-03-25 08:31:13 | NBlog March 25 - coping with the COVID crisis (lien direct) |  I bumped into an insightful piece by Jeff Immelt 'Lead through a crisis' yesterday. This paragraph really caught my eye: I bumped into an insightful piece by Jeff Immelt 'Lead through a crisis' yesterday. This paragraph really caught my eye:  I agree there are material differences between us in how we react under pressure, differences that are exaggerated during a crisis. The same applies to social groups and families as well as work teams: some of us are (or at least give the appearance of being) fully on top of things, some are 'coping', some are struggling, and some are in turmoil, overwhelmed by it all.The current situation reminds me of the Kübler-Ross grieving curve. Here's a version I've used to help explain our emotional responses to traumatic events such as information security incidents and changes: I agree there are material differences between us in how we react under pressure, differences that are exaggerated during a crisis. The same applies to social groups and families as well as work teams: some of us are (or at least give the appearance of being) fully on top of things, some are 'coping', some are struggling, and some are in turmoil, overwhelmed by it all.The current situation reminds me of the Kübler-Ross grieving curve. Here's a version I've used to help explain our emotional responses to traumatic events such as information security incidents and changes: |
Guideline | |||
| 2020-03-23 13:19:46 | NBlog March 20 - COVID-19 PIG update (lien direct) | Here's today's update to my COVID-19 information risk Probability Impact Graphic: I've slightly shifted and revised the wording of some of the risks but there's nothing really new (as far as I know anyway). Reports of panic buying from the UK and US are concerning, given the possible escalation to social disorder and looting … but hopefully sanity will soon return, aided by the authorities promoting “social distancing” and “self-isolation”. Meanwhile, I hope those of you responsible for physically securing corporate premises have appropriate security arrangements in place. Remotely monitored alarms and CCTV are all very well, but what if the guards that would be expected to do their rounds and respond to an incident are off sick or isolated at home? Do you have contingency arrangements for physical security?'Sanity' is a fragile condition: there is clearly a lot of anxiety, stress and tension around, due to the sudden social changes, fear about the infectious disease etc., which is my rationale for including 'mental health issues' in the middle of the PIG. There is some genuinely good news in the medical world concerning progress on coronavirus testing, antiviral drugs and vaccines, although it's hard to spot among the large volume of dubious information and rumours sloshing around on social media (another information risk on the PIG). There's even some good news for infosec pro's. COVID-19 is a golden opportunity for those of us with an interest in security awareness and business continuity. Essentially, we are in the midst of a dramatic case study. I've slightly shifted and revised the wording of some of the risks but there's nothing really new (as far as I know anyway). Reports of panic buying from the UK and US are concerning, given the possible escalation to social disorder and looting … but hopefully sanity will soon return, aided by the authorities promoting “social distancing” and “self-isolation”. Meanwhile, I hope those of you responsible for physically securing corporate premises have appropriate security arrangements in place. Remotely monitored alarms and CCTV are all very well, but what if the guards that would be expected to do their rounds and respond to an incident are off sick or isolated at home? Do you have contingency arrangements for physical security?'Sanity' is a fragile condition: there is clearly a lot of anxiety, stress and tension around, due to the sudden social changes, fear about the infectious disease etc., which is my rationale for including 'mental health issues' in the middle of the PIG. There is some genuinely good news in the medical world concerning progress on coronavirus testing, antiviral drugs and vaccines, although it's hard to spot among the large volume of dubious information and rumours sloshing around on social media (another information risk on the PIG). There's even some good news for infosec pro's. COVID-19 is a golden opportunity for those of us with an interest in security awareness and business continuity. Essentially, we are in the midst of a dramatic case study. |
Patching Guideline | |||
| 2020-03-21 06:49:12 | NBlog March 13 - COVID-19 information risk analysis (lien direct) | I'll kick off with a disclaimer: IANAV*. I have a scientific background in microbial genetics but left the field more than 3 decades ago. I have far more experience in information risk management, so what follows is my personal assessment of the information risks ('risks pertaining to information') associated with the Coronavirus pandemic.Here's my initial draft of a Probability-Impact-Graphic showing what I see as the main information risk aspects right now, today, with a few words of explanation below: Top left, the reported shortages of toilet rolls, facemasks, hand sanitiser and soap qualify as information incidents because they are the result of panic buying by people over-reacting to initial media coverage of shortages. The impacts are low because most people are just not that daft. Fear, Uncertainty and Doubt, however, is largely what drives those panic buyers. To an extent, I blame the media (mostly social media but also the traditional news media, desperate for their next headline) for frenziedly whipping up a storm of information. There are potentially significant personal and social consequences arising from FUD that I'll cover later.In amongst the frenzied bad news, there are a few good things coming out of this incident. The global scientific, medical and public services communities are quietly sharing information about the virus, infections, symptoms, morbidity, treatments, contributory factors, social responses etc. There is excellent work going on to characterise the virus, understand its morphology and genetics, understand the disease progression, understand the modes of transmission etc. It's a shame this isn't as widely reported as the bad news but I think I understand why that is: scientists, generally, are reluctant to publish information they aren't reasonably sure about, and "reasonably sure" means if a reporter asks for a categorical statement of fact, most scientists will at least hesitate if not refuse. An example of this is the face mask issue: good quality face masks are designed to trap small particles but not as small as viruses. They help by impeding airborne particles and so reducing the spread of airborne viruses, but do not total Top left, the reported shortages of toilet rolls, facemasks, hand sanitiser and soap qualify as information incidents because they are the result of panic buying by people over-reacting to initial media coverage of shortages. The impacts are low because most people are just not that daft. Fear, Uncertainty and Doubt, however, is largely what drives those panic buyers. To an extent, I blame the media (mostly social media but also the traditional news media, desperate for their next headline) for frenziedly whipping up a storm of information. There are potentially significant personal and social consequences arising from FUD that I'll cover later.In amongst the frenzied bad news, there are a few good things coming out of this incident. The global scientific, medical and public services communities are quietly sharing information about the virus, infections, symptoms, morbidity, treatments, contributory factors, social responses etc. There is excellent work going on to characterise the virus, understand its morphology and genetics, understand the disease progression, understand the modes of transmission etc. It's a shame this isn't as widely reported as the bad news but I think I understand why that is: scientists, generally, are reluctant to publish information they aren't reasonably sure about, and "reasonably sure" means if a reporter asks for a categorical statement of fact, most scientists will at least hesitate if not refuse. An example of this is the face mask issue: good quality face masks are designed to trap small particles but not as small as viruses. They help by impeding airborne particles and so reducing the spread of airborne viruses, but do not total |
Guideline | |||
| 2020-03-20 16:30:54 | NBlog March 20 - COVID-19 infosec awareness special (lien direct) |  Today I trawled through our back catalog of information security awareness content for anything pertinent to COVID-19. The "Off-site working" security awareness module published less than a year ago is right on the button. "Off-site working" complements the "on-site working" awareness module, about the information risk and security aspects of working on corporate premises in conventional offices and similar workplaces. Off-site concerns the information risk and security aspects of working from home or on-the-road (e.g. from hotels or customer premises), often using portable IT equipment and working independently ... which is exactly the situation many of us are in right now.Off-site working changes the information risks compared to working in purpose-built corporate offices. Mostly, the risks increase in line with the complexities of remote access, portability and physical dispersion … but offsetting that, off-site working can be convenient, productive and popular, and patently there are business continuity advantages in working through incidents such as COVID-19. Implementing appropriate security controls makes it work, on the whole, with security awareness being an essential part of the mix. People need to know about and follow the rules.To assist organizations through the crisis and showcase our awareness materials, we're currently offering the off-site working security awareness module at just under $400 - that's half price. Several other awareness modules may also be pertinent, delving into related topics such as:Business continuityBYOD and IoT securityCybersecurityIncidents and disastersInternet securityPhishing Today I trawled through our back catalog of information security awareness content for anything pertinent to COVID-19. The "Off-site working" security awareness module published less than a year ago is right on the button. "Off-site working" complements the "on-site working" awareness module, about the information risk and security aspects of working on corporate premises in conventional offices and similar workplaces. Off-site concerns the information risk and security aspects of working from home or on-the-road (e.g. from hotels or customer premises), often using portable IT equipment and working independently ... which is exactly the situation many of us are in right now.Off-site working changes the information risks compared to working in purpose-built corporate offices. Mostly, the risks increase in line with the complexities of remote access, portability and physical dispersion … but offsetting that, off-site working can be convenient, productive and popular, and patently there are business continuity advantages in working through incidents such as COVID-19. Implementing appropriate security controls makes it work, on the whole, with security awareness being an essential part of the mix. People need to know about and follow the rules.To assist organizations through the crisis and showcase our awareness materials, we're currently offering the off-site working security awareness module at just under $400 - that's half price. Several other awareness modules may also be pertinent, delving into related topics such as:Business continuityBYOD and IoT securityCybersecurityIncidents and disastersInternet securityPhishing |
||||
| 2020-03-18 11:50:47 | NBlog March 18 - COVID-19 PIG update (lien direct) | I've updated the PIG showing information risks relating to COVID-19, originally published here five days ago:  Two additional information risks now feature in the middle:Mental health issues arising from the sudden widespread introduction of work-from-home, social distancing, cancellation of many leisure activities etc., on top of the stress of potentially being infected and becoming sick. Laid-off workers are basically cast adrift, placing them under immense personal stress at this difficult time because of the scale of COVID-19: they are unlikely to walk directly into their next contract or permanent role with some other organisation if everyone is in crisis. Remaining workers may have 'survivor guilt', and fear also being laid off - hardly conducive to productive working. It may increase 'insider threats'. Also, this risk may increase over time once we get beyond the honeymoon period as workers settle in to their more isolated workspaces, and face up to the realities of being largely self-directed.I brought up the increased information risks associated with working-from-home four days ago. Scrambling to get workers set up for home working probably means corner-cutting here and there, for example making do with whatever comms and IT technology people already have, rather than the organization providing suitable new equipment pre-configured for security and perhaps dedicated for work purposes. Another tech risk here relates to our suddenly increased reliance on comms and collaborative working tools: the Internet and cloud service providers so far seem to be coping quite well but things could change quickly - for example if they are hit by ransomware ... which in turn begs questions about their customers' readiness to cope with service issues and incidents.I'll stress once again that IANAV and my assessment is focused on risks pertaining to information.I'll have more to say about treating these information risks soon (still contemplating!). Meanwhile, there is quite a lot of advice already circulating on social media such as LinkeDin. We've seen outpourings of sympathy before following natural disasters, but the global real-time sharing of pragmatic advice on dealing with a health crisis in progress is unprecedented. See it's not all bad news! Two additional information risks now feature in the middle:Mental health issues arising from the sudden widespread introduction of work-from-home, social distancing, cancellation of many leisure activities etc., on top of the stress of potentially being infected and becoming sick. Laid-off workers are basically cast adrift, placing them under immense personal stress at this difficult time because of the scale of COVID-19: they are unlikely to walk directly into their next contract or permanent role with some other organisation if everyone is in crisis. Remaining workers may have 'survivor guilt', and fear also being laid off - hardly conducive to productive working. It may increase 'insider threats'. Also, this risk may increase over time once we get beyond the honeymoon period as workers settle in to their more isolated workspaces, and face up to the realities of being largely self-directed.I brought up the increased information risks associated with working-from-home four days ago. Scrambling to get workers set up for home working probably means corner-cutting here and there, for example making do with whatever comms and IT technology people already have, rather than the organization providing suitable new equipment pre-configured for security and perhaps dedicated for work purposes. Another tech risk here relates to our suddenly increased reliance on comms and collaborative working tools: the Internet and cloud service providers so far seem to be coping quite well but things could change quickly - for example if they are hit by ransomware ... which in turn begs questions about their customers' readiness to cope with service issues and incidents.I'll stress once again that IANAV and my assessment is focused on risks pertaining to information.I'll have more to say about treating these information risks soon (still contemplating!). Meanwhile, there is quite a lot of advice already circulating on social media such as LinkeDin. We've seen outpourings of sympathy before following natural disasters, but the global real-time sharing of pragmatic advice on dealing with a health crisis in progress is unprecedented. See it's not all bad news! |
Ransomware | |||
| 2020-03-17 08:58:05 | NBlog March 17 - COVID-19 BCM (lien direct) |  From my narrow perspective as a practitioner, manager and consultant in the field, some 20-30 years ago, Business Continuity Planning revolved around IT Disaster Recovery which generally involved (at the time) either powering up an alternative data centre or hiring a few servers on the back of a truck and plugging them in to restore services taken out when the data centre was flooded/burnt. It was almost entirely IT focused, expensive, and could cope with very few disaster scenarios (there still had to be somewhere for the truck to park up and plug in, while the backups to be restored had to have survived miraculously, plus of course the rest of the organization - including the alternative data centre plus the people and associated essential services).From that primitive origin, BCP started to get better organised, with scenario planning and tabletop exercises, and actual 'management' instead of just 'planning' - leading to Business Continuity Management. The scenarios expanded, and before long organisations realised that they couldn't reasonably plan and prepare playbooks for every possible situation, every single risk. Also, the process linkages with incident management grew stronger, including the shortcuts necessary to escalate serious incidents, authorise and initiate significant responses quickly etc. Oh and warm-site and hot-site concepts appeared, along with Recovery Time Objective, Recovery Point Objective and a few other basic metrics. Then, about 10 to 15 years ago, resilience popped out of the ether as a supplement for IT DR and other recovery approaches, the idea being to do whatever it takes to maintain essential services supporting essential business processes. Even today, some organisations struggle with this concept, and yet "high availability" systems and networks, dual-live/distributed systems, load-sharing, multi-sourced supplies, customer diversity etc. are reasonably straightforward and generally-accepted concepts. I guess they have trouble joining the dots - particularly in the area of workforce resilience, and the cultural aspects of "We WILL get through this: now, what can I do to help? Here, hold my beer ..." During the past 10 years or so, true contingency approaches have appeared, in some organizations at least, partly in rec From my narrow perspective as a practitioner, manager and consultant in the field, some 20-30 years ago, Business Continuity Planning revolved around IT Disaster Recovery which generally involved (at the time) either powering up an alternative data centre or hiring a few servers on the back of a truck and plugging them in to restore services taken out when the data centre was flooded/burnt. It was almost entirely IT focused, expensive, and could cope with very few disaster scenarios (there still had to be somewhere for the truck to park up and plug in, while the backups to be restored had to have survived miraculously, plus of course the rest of the organization - including the alternative data centre plus the people and associated essential services).From that primitive origin, BCP started to get better organised, with scenario planning and tabletop exercises, and actual 'management' instead of just 'planning' - leading to Business Continuity Management. The scenarios expanded, and before long organisations realised that they couldn't reasonably plan and prepare playbooks for every possible situation, every single risk. Also, the process linkages with incident management grew stronger, including the shortcuts necessary to escalate serious incidents, authorise and initiate significant responses quickly etc. Oh and warm-site and hot-site concepts appeared, along with Recovery Time Objective, Recovery Point Objective and a few other basic metrics. Then, about 10 to 15 years ago, resilience popped out of the ether as a supplement for IT DR and other recovery approaches, the idea being to do whatever it takes to maintain essential services supporting essential business processes. Even today, some organisations struggle with this concept, and yet "high availability" systems and networks, dual-live/distributed systems, load-sharing, multi-sourced supplies, customer diversity etc. are reasonably straightforward and generally-accepted concepts. I guess they have trouble joining the dots - particularly in the area of workforce resilience, and the cultural aspects of "We WILL get through this: now, what can I do to help? Here, hold my beer ..." During the past 10 years or so, true contingency approaches have appeared, in some organizations at least, partly in rec |
Guideline | |||
| 2020-03-14 09:25:28 | NBlog March 14 - COVID-19 information risk update (lien direct) | Further to yesterday's assessment of the information risks associated with the coronavirus pandemic and the discussion arising, here are a few more aspects.An increased number of knowledge workers are now working from home, some of them for the first time. What equipment and services are they using? What are the information risks and security arrangements? Who knows? Larger organizations tend to have in place suitable policies plus structured, systematic approaches towards home and other off-site working, with controls such as management authorization, remote security management of end user devices (corporate or BYOD), VPNs, network security monitoring, network backups, automated patching, antivirus etc. Hopefully they have all scaled easily to cope with the changing proportions of off-siters. Medium and especially small organizations, however, may be less well prepared ... and all of them are likely to be feeling the strain of changed working practices and social interaction. The managers, supervisors, network security pro's and others who are meant to be keeping an eye on all this are also more likely to be working off-site, relying more on automation and information through the systems. That smells like a green or borderline amber information risk to me, redder for those ill-prepared SMEs maybe, or for larger organizations that for some reason were not on top of this already. Given that managers and execs generally have been working off-site for years, they really have no excuse for failing to identify, evaluate and treat the associated information risks. If they now deserve to be called to account, so be it. Which reminds me, another bit of good news is that organizations are running and hopefully proving the adequacy of their business continuity arrangements, including the resilience aspects of keeping the information flowing more or less normally. This is better than the normal business continuity exercise in that everyone is participating (like it or not!) ... but as to whether everyone is coping well, we shall see. Some supply chains/networks are clearly under stress (toilet rolls, for instance!), and others probably too. If they fail due to inadequate resilience, the consequences may ripple outwards, meaning that some organizations will also get to use and prove their contingency arrangements. There are some more green/amber information risks in there, judging largely by what we see today i.e. nothing significantly amiss so far, no dramatic failures or industry collapses (except perhaps for the financial industry - a red risk already on the chart). Oh and there's more good news: most of the population now knows the basics of personal hygiene such as covering their sneezes and washing their hands. These aren't totally effective co | ||||
| 2020-03-12 15:17:34 | NBlog March 8 - meshy policies [UPDATED] (lien direct) |  I'm reviewing and revising our information security policy templates, again. At the moment I'm systematically compiling a cross-reference matrix in Excel showing how each of the 65 policies relates to others in the set - quite a laborious job but it will result in greater consistency. The objective is to make the policies knit together coherently, without significant overlaps or gaps in coverage - less mess, more mesh.All our policies include a reference section noting other relevant policies, procedures, guidelines etc. but only the main ones: the information risk management policy, for instance, is relevant to all the others but there's no point listing it as a reference in all of them, nor listing all of them in it.I have shortened the titles of a few policies for readability, and need to check/update the formatting then generate new screenshots for the website. Once that is all done, I will be checking coverage: a couple of policies are similar enough that they might perhaps be combined, and I'm always on the lookout for gaps that need plugging.In all of this, it helps enormously that I wrote them all in the first place, and have maintained them all through the NoticeBored monthly updates. Organisational policies usually accumulate over time from a variety of sources and authors, with different writing styles and mind-sets. Conflicts and holes are not uncommon, creating problems for awareness and compliance. Hot issues tend to have current, up-to-date policies, whereas policies covering longstanding aspects tend to go stale, unless someone takes the time to review and update the entire suite as I am doing now. Even something as simple as using a common MS Word template with styles for headings and text makes a huge difference to the readability and consistency, but the template itself has evolved over the years I've been doing this, and is changing again now. It takes concentration to work systematically through the whole suite, updating them to the same standard.The end result is worth it though. The policy suite is already a polished, professional product at a good price (a fraction of the cost of developing this much content from scratch). It sells well and I'm proud of it! We are using it to develop custom, branded policies for clients and would love to do the same for you, so if your infosec policies are looking a bit shabby, messy, the worse for wear, I'm reviewing and revising our information security policy templates, again. At the moment I'm systematically compiling a cross-reference matrix in Excel showing how each of the 65 policies relates to others in the set - quite a laborious job but it will result in greater consistency. The objective is to make the policies knit together coherently, without significant overlaps or gaps in coverage - less mess, more mesh.All our policies include a reference section noting other relevant policies, procedures, guidelines etc. but only the main ones: the information risk management policy, for instance, is relevant to all the others but there's no point listing it as a reference in all of them, nor listing all of them in it.I have shortened the titles of a few policies for readability, and need to check/update the formatting then generate new screenshots for the website. Once that is all done, I will be checking coverage: a couple of policies are similar enough that they might perhaps be combined, and I'm always on the lookout for gaps that need plugging.In all of this, it helps enormously that I wrote them all in the first place, and have maintained them all through the NoticeBored monthly updates. Organisational policies usually accumulate over time from a variety of sources and authors, with different writing styles and mind-sets. Conflicts and holes are not uncommon, creating problems for awareness and compliance. Hot issues tend to have current, up-to-date policies, whereas policies covering longstanding aspects tend to go stale, unless someone takes the time to review and update the entire suite as I am doing now. Even something as simple as using a common MS Word template with styles for headings and text makes a huge difference to the readability and consistency, but the template itself has evolved over the years I've been doing this, and is changing again now. It takes concentration to work systematically through the whole suite, updating them to the same standard.The end result is worth it though. The policy suite is already a polished, professional product at a good price (a fraction of the cost of developing this much content from scratch). It sells well and I'm proud of it! We are using it to develop custom, branded policies for clients and would love to do the same for you, so if your infosec policies are looking a bit shabby, messy, the worse for wear, |
||||
| 2020-03-12 09:41:18 | NBlog March 12 - reflecting on privacy (lien direct) |  Anyone who read Orwell's masterpiece or saw the film "1984" appreciates the threat of mass surveillance by the state a.k.a. Big Brother. Anyone who has followed Ed Snowden's revelations knows that mass surveillance is no longer fanciful fiction. There are clearly privacy impacts from surveillance with implications for personal freedoms, assurance and compliance. At the same time, surveillance offers significant social benefits too, in other words, pros and cons which vary with one's perspective. Big Brother sees overwhelming benefits from mass surveillance and has the power, capability and (these days) the technology to conduct both overt and covert mass or targeted surveillance more or less at will. The same thing applies to other forms of surveillance and other contexts: many of us gleefully carry surveillance devices with us wherever we go, continuously transmitting information about our activities, conversations, locations, contacts and more. We may call them 'smartphones' but is that really a smart thing to do? Drug dealers and other criminals appreciate the value of burner phones, essentially buying a modicum of privacy. What about the rest of us? Are we wise to rely on the technologies, the phone companies and the authorities not to invade our privacy? Some of us are introducing IoT things into our homes, seduced by the convenience of being able to tell our smart TV to order a pizza without even getting up from the sofa. Evidently people either don't even consider the privacy implications, or accept them presumably on the basis that they own and chose to introduce the surveillance devices, and could just as easily stop and remove them (fine in theory, doesn't happen in practice).Then there are the surveillance devices we use to monitor, track or snoop on various others: baby monitors, nanny-cams, commercial and home CCTV systems, webcams, dashcams, audio bugs, covert cameras, spyware, keyloggers and more. Surveillance tech is big business, both retail, commercial and governmental/military. Need to know where a recent arrival from China has been? Simply collect the surveillance jigsaw pieces into a credible sequence and despatch the hazmat teams.Overt surveillance in the form of obvious CCTV camera installations are just the tip of the iceberg. Covert cams and bugs are already snooping on us in changing rooms, toilets, video-conference facilities, courts and mor Anyone who read Orwell's masterpiece or saw the film "1984" appreciates the threat of mass surveillance by the state a.k.a. Big Brother. Anyone who has followed Ed Snowden's revelations knows that mass surveillance is no longer fanciful fiction. There are clearly privacy impacts from surveillance with implications for personal freedoms, assurance and compliance. At the same time, surveillance offers significant social benefits too, in other words, pros and cons which vary with one's perspective. Big Brother sees overwhelming benefits from mass surveillance and has the power, capability and (these days) the technology to conduct both overt and covert mass or targeted surveillance more or less at will. The same thing applies to other forms of surveillance and other contexts: many of us gleefully carry surveillance devices with us wherever we go, continuously transmitting information about our activities, conversations, locations, contacts and more. We may call them 'smartphones' but is that really a smart thing to do? Drug dealers and other criminals appreciate the value of burner phones, essentially buying a modicum of privacy. What about the rest of us? Are we wise to rely on the technologies, the phone companies and the authorities not to invade our privacy? Some of us are introducing IoT things into our homes, seduced by the convenience of being able to tell our smart TV to order a pizza without even getting up from the sofa. Evidently people either don't even consider the privacy implications, or accept them presumably on the basis that they own and chose to introduce the surveillance devices, and could just as easily stop and remove them (fine in theory, doesn't happen in practice).Then there are the surveillance devices we use to monitor, track or snoop on various others: baby monitors, nanny-cams, commercial and home CCTV systems, webcams, dashcams, audio bugs, covert cameras, spyware, keyloggers and more. Surveillance tech is big business, both retail, commercial and governmental/military. Need to know where a recent arrival from China has been? Simply collect the surveillance jigsaw pieces into a credible sequence and despatch the hazmat teams.Overt surveillance in the form of obvious CCTV camera installations are just the tip of the iceberg. Covert cams and bugs are already snooping on us in changing rooms, toilets, video-conference facilities, courts and mor |
Threat | Uber | ||
| 2020-03-06 10:00:03 | NBlog March 6 - cry-ber-security (lien direct) |  ◄ This amuses me - part of an advertisement by NZ farm supplies company FFM for their quad bike safety helmets ... but the principle applies equally to knowledge workers in any industry. ◄ This amuses me - part of an advertisement by NZ farm supplies company FFM for their quad bike safety helmets ... but the principle applies equally to knowledge workers in any industry. We used a similar concept for one of our social engineering awareness posters, emphasising the manipulation rather than protection ►Earlier this week, Gelo asked on the ISO We used a similar concept for one of our social engineering awareness posters, emphasising the manipulation rather than protection ►Earlier this week, Gelo asked on the ISO |
||||
| 2020-03-05 09:44:29 | NBlog March 5 - SIM swap fraud (lien direct) |  I've heard rumours about the possibility of SIM-swap "identity theft" (fraud) but wasn't aware of the details ... until reading a couple of recent articles pointing to an academic paper from a team at Princeton University.The fraud involves socially-engineering the cellphone companies into migrating a victim's cellphone number onto a new SIM card, one in the fraudster's possession. That gives the fraudster control of a factor used in several multifactor authentication schemes ... and in some cases, that's enough to take full control (e.g. resetting the victim's password - another factor). Otherwise, it might take them a bit more effort to guess, steal or brute-force the victim's password or PIN code first. Authentication is usually a key control, yet authentication schemes often turn out to have vulnerabilities due to:Fundamental design flaws (e.g. saving passwords unencrypted or weakly encrypted) Bugs in the software and firmware (e.g. cheat codes - bypasses and backdoors in production, and broken crypto in CPU microcode)Physical hardware limitations (e.g. the tolerances needed for biometrics, allowing fakes and forgeries)Issues in their implementation, configuration and administration (e.g. giving new users the same well-known default passwords or weak password reset mechanisms) Operational "user" issues (e.g. naively falling for phishing attacks)Multifactor is stronger than single factor authentication but still not perfect ... hence aside from addressing the vulnerabilities, we should also anticipate control failures and put in place further, supplementary controls to detect and respond to incidents.The risks are there for authentication to networks, systems, apps and online services in general, but the greater potential impacts in the case of, say, banking, law enforcement and defence imply greater risks, justifying the investment in stronger controls. I've heard rumours about the possibility of SIM-swap "identity theft" (fraud) but wasn't aware of the details ... until reading a couple of recent articles pointing to an academic paper from a team at Princeton University.The fraud involves socially-engineering the cellphone companies into migrating a victim's cellphone number onto a new SIM card, one in the fraudster's possession. That gives the fraudster control of a factor used in several multifactor authentication schemes ... and in some cases, that's enough to take full control (e.g. resetting the victim's password - another factor). Otherwise, it might take them a bit more effort to guess, steal or brute-force the victim's password or PIN code first. Authentication is usually a key control, yet authentication schemes often turn out to have vulnerabilities due to:Fundamental design flaws (e.g. saving passwords unencrypted or weakly encrypted) Bugs in the software and firmware (e.g. cheat codes - bypasses and backdoors in production, and broken crypto in CPU microcode)Physical hardware limitations (e.g. the tolerances needed for biometrics, allowing fakes and forgeries)Issues in their implementation, configuration and administration (e.g. giving new users the same well-known default passwords or weak password reset mechanisms) Operational "user" issues (e.g. naively falling for phishing attacks)Multifactor is stronger than single factor authentication but still not perfect ... hence aside from addressing the vulnerabilities, we should also anticipate control failures and put in place further, supplementary controls to detect and respond to incidents.The risks are there for authentication to networks, systems, apps and online services in general, but the greater potential impacts in the case of, say, banking, law enforcement and defence imply greater risks, justifying the investment in stronger controls. |
||||
| 2020-02-29 16:46:00 | NBlog March - InfoSec 101 module released (lien direct) |  Whereas usually our awareness and training modules focus in some depth on one of the 70 information security topics in our portfolio, Information Security 101 is a broad but shallow module. It is intended to bring workers quickly up to speed on the basics of information risk and security during security induction courses, for periodic refresher training, or when launching an awareness program.As soon as a new worker arrives, they start absorbing and being assimilated into the corporate culture, picking up 'the way we do things here'. Sensible organizations run orientation sessions to welcome newcomers and kick-start the cultural integration. Whereas usually our awareness and training modules focus in some depth on one of the 70 information security topics in our portfolio, Information Security 101 is a broad but shallow module. It is intended to bring workers quickly up to speed on the basics of information risk and security during security induction courses, for periodic refresher training, or when launching an awareness program.As soon as a new worker arrives, they start absorbing and being assimilated into the corporate culture, picking up 'the way we do things here'. Sensible organizations run orientation sessions to welcome newcomers and kick-start the cultural integration.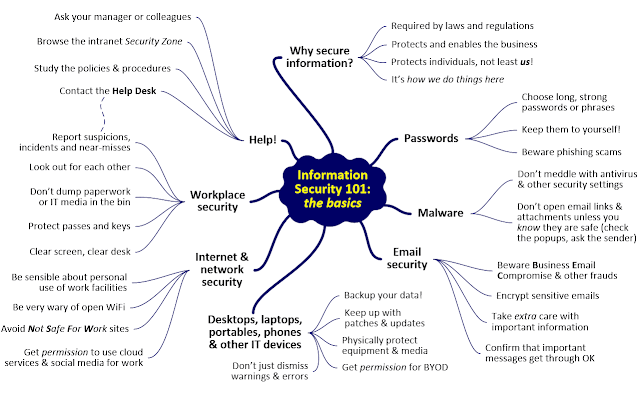 InfoSec 101 covers common information risks (e.g. malware) and information security controls (e.g.& antivirus). The materials are deliberately succinct, outlining key aspects without delving into the details. We're not trying to tell workers everything about information risk and security all at once but to set them off on the right foot, engaging them as integral and valuable parts of the organisation's Information Security Management System. It's a gentle introduction, more splash in the paddling pool than high dive at the deep end!First impressions matter, so the module helps Information Security, HR or training professionals deliver interesting and engaging awareness sessions accompanied by impressive, top-quality supporting materials. Establishing personal contacts throughout the organization gradually expands the Information Security team across the enterprise - more 'eyes and ears' out there. This alone would be well worth the investment!As well as induction or orientation purposes, InfoSec InfoSec 101 covers common information risks (e.g. malware) and information security controls (e.g.& antivirus). The materials are deliberately succinct, outlining key aspects without delving into the details. We're not trying to tell workers everything about information risk and security all at once but to set them off on the right foot, engaging them as integral and valuable parts of the organisation's Information Security Management System. It's a gentle introduction, more splash in the paddling pool than high dive at the deep end!First impressions matter, so the module helps Information Security, HR or training professionals deliver interesting and engaging awareness sessions accompanied by impressive, top-quality supporting materials. Establishing personal contacts throughout the organization gradually expands the Information Security team across the enterprise - more 'eyes and ears' out there. This alone would be well worth the investment!As well as induction or orientation purposes, InfoSec |
Guideline | |||
| 2020-02-26 20:23:36 | NBlog Feb 26 - a good day down the salt mine (lien direct) |  The remaining items for the recycled InfoSec 101 module are falling rapidly into place. It will be a bumper delivery with fifty (yes, 50) files already in the bag.One of the regular end-of-month jobs involves matching up the awareness items - the files - with the contents listing and their descriptions in the train-the-trainer guide. Years back I came up with a simple numeric naming scheme to make it easier to get the files in order and link them with the listings. Good thing too: this afternoon I came across one listed item that I've decided to drop from the module, and about three additions that need to be listed and described. There's still a little time left before delivery to change things further and renumber, again, if we need to ... which emphasises the value of these final quality checks before packaging and despatch.Another part of the quality assurance process is to open and review the content of all the files. This is our last chance to spot speling mishtakes, errror, omissons and half-finishedI've already made a couple of passes through the materials: the first pass often reminds me of things I've brought up in one item that ought to be repeated or reflected in others, so there's a bit of back-and-forth refinement ... but the looming deadline means eventually I have call a halt to the spit-n-polish phase. It's tough for me to stop when the materials are 'good enough' rather than 'perfect' but I console (or is it delude?) myself by thinking that nobody but me will spot most of what I consider to be the remaining errors, while it's unlikely I will ever a some further tranche of errors due to my inherent blind spots.So I keep calm and carry on.In risk terms, I'm consciously making a trade-off. I could carry on checking and refining the content indefinitely but I'd blow the delivery deadline. Alternatively I could stop right now and deliver the module as-is, but I'd be distraught to discover significant problems later on ... which does happen sometimes when I re-read stuff I have written, checked and published some months or years earlier. Some of the problems that catch my beady now are genuine boo-boos that I should really have spotted corrected at the time. Some are things I would put differently now because I've changed and the infosec world has mov The remaining items for the recycled InfoSec 101 module are falling rapidly into place. It will be a bumper delivery with fifty (yes, 50) files already in the bag.One of the regular end-of-month jobs involves matching up the awareness items - the files - with the contents listing and their descriptions in the train-the-trainer guide. Years back I came up with a simple numeric naming scheme to make it easier to get the files in order and link them with the listings. Good thing too: this afternoon I came across one listed item that I've decided to drop from the module, and about three additions that need to be listed and described. There's still a little time left before delivery to change things further and renumber, again, if we need to ... which emphasises the value of these final quality checks before packaging and despatch.Another part of the quality assurance process is to open and review the content of all the files. This is our last chance to spot speling mishtakes, errror, omissons and half-finishedI've already made a couple of passes through the materials: the first pass often reminds me of things I've brought up in one item that ought to be repeated or reflected in others, so there's a bit of back-and-forth refinement ... but the looming deadline means eventually I have call a halt to the spit-n-polish phase. It's tough for me to stop when the materials are 'good enough' rather than 'perfect' but I console (or is it delude?) myself by thinking that nobody but me will spot most of what I consider to be the remaining errors, while it's unlikely I will ever a some further tranche of errors due to my inherent blind spots.So I keep calm and carry on.In risk terms, I'm consciously making a trade-off. I could carry on checking and refining the content indefinitely but I'd blow the delivery deadline. Alternatively I could stop right now and deliver the module as-is, but I'd be distraught to discover significant problems later on ... which does happen sometimes when I re-read stuff I have written, checked and published some months or years earlier. Some of the problems that catch my beady now are genuine boo-boos that I should really have spotted corrected at the time. Some are things I would put differently now because I've changed and the infosec world has mov |
||||
| 2020-02-24 12:37:21 | NBlog Feb 24 - InfoSec 101 for pro\'s (lien direct) | Today I'm working on the InfoSec 101 awareness seminar for professionals, by which I mean workers with a professional interest in information security. As with the staff and management seminars, the aim is to cover the basics in a way that appeals to the audience: I figure the professionals are more clued-up than most, particularly on technology, so it's appropriate to go into a little more depth here on the fundamental concepts ... starting with risk and control.  The diagram above represents the nature of risk i.e. 'uncertain outcome'. That's a seminar slide's worth, with a few words from the presenter briefly explaining each of the red-amber-green spectra as they appear on the screen.The next slide contrasts two complementary forms of control: either we stop harmful things from occurring by avoiding, preventing or mitigating incidents, or we ensure that good things occur - and that's an intriguing thought. What does that actually mean in this context? The diagram above represents the nature of risk i.e. 'uncertain outcome'. That's a seminar slide's worth, with a few words from the presenter briefly explaining each of the red-amber-green spectra as they appear on the screen.The next slide contrasts two complementary forms of control: either we stop harmful things from occurring by avoiding, preventing or mitigating incidents, or we ensure that good things occur - and that's an intriguing thought. What does that actually mean in this context?  'Prevent bad stuff' is what most people think security is all about ... but wait, there's more. 'Protect good stuff' refers to maintaining the confidentiality, integrity and availability of information, thereby supporting and enabling business activities which use and depend on information.Looking again at those two images, the simpler, cleaner style of the 'control' one seems more elegant and better suited to InfoSec 101, so I will redraw the 'risk' one in the same style. We could stop right there with a 2-slide InfoSec 101 pro seminar but, 'Prevent bad stuff' is what most people think security is all about ... but wait, there's more. 'Protect good stuff' refers to maintaining the confidentiality, integrity and availability of information, thereby supporting and enabling business activities which use and depend on information.Looking again at those two images, the simpler, cleaner style of the 'control' one seems more elegant and better suited to InfoSec 101, so I will redraw the 'risk' one in the same style. We could stop right there with a 2-slide InfoSec 101 pro seminar but, |
||||
| 2020-02-22 15:11:12 | NBlog Feb 22 - the educator virus (lien direct) |  From time to time, people get all excited about micro-learning, the educational equivalent of eating a chocolate elephant - one bite or byte at a time."It's easy", the line goes. "Simply break down large indigestible topics into lots of smaller edible chunks, spreading them out enticingly for people to snack on whenever they feel peckish."I've tried that with our digital awareness content. For some strange reason, nobody was hungry enough to consume the random assortment of ones and zeroes, hundreds and thousands of bits all over the disk.Evidently it's not quite that easy. Education is never easy, if you want it to work well that is. Micro-, milli- and macro-learning, online learning, traditional classroom-based courses, webinars and seminars, conferences, educational events, rote and experiential learning, on-the-job training and demonstration classes, mentoring and so on are neither simple nor universal solutions. They each have their pros and cons. For one thing, they all just tools in the box. For an educator who happens to be a master craftsman, almost any tool will do, but he has preferences and a range of experience. Likewise for the students: some of us like reading and thinking things through in private, or debating the ins-and-outs at length with colleagues. Others need to be shown stuff, just briefly, or put through an intensive boot camp complete with sadistic 'instructors', hard beds and nasty food. Some appear stubbornly resistant to all known edumacational techniques and do their level best to skip class, and we all have our cognitive issues occasionally.The fact that there is such a variety of techniques suggests that none of them is ideal for all learning situations. The advice to use, say, micro-learning could be taken to mean "use ONLY micro-learning" but that would be a mistake, in just the same way as "send them to college" or "gamify it"! It's well-meaning but naive silver bullet advice.Consider how we learn stuff in general. We take classes, go to night school, take driving or diving or cookery lessons, read-up on stuff, watch You Tube vids, read/listen to/watch/contemplate sage advisors, ask someone ... and generally muddle through by ourselves, learning as we go from our successes and failures. From time to time, people get all excited about micro-learning, the educational equivalent of eating a chocolate elephant - one bite or byte at a time."It's easy", the line goes. "Simply break down large indigestible topics into lots of smaller edible chunks, spreading them out enticingly for people to snack on whenever they feel peckish."I've tried that with our digital awareness content. For some strange reason, nobody was hungry enough to consume the random assortment of ones and zeroes, hundreds and thousands of bits all over the disk.Evidently it's not quite that easy. Education is never easy, if you want it to work well that is. Micro-, milli- and macro-learning, online learning, traditional classroom-based courses, webinars and seminars, conferences, educational events, rote and experiential learning, on-the-job training and demonstration classes, mentoring and so on are neither simple nor universal solutions. They each have their pros and cons. For one thing, they all just tools in the box. For an educator who happens to be a master craftsman, almost any tool will do, but he has preferences and a range of experience. Likewise for the students: some of us like reading and thinking things through in private, or debating the ins-and-outs at length with colleagues. Others need to be shown stuff, just briefly, or put through an intensive boot camp complete with sadistic 'instructors', hard beds and nasty food. Some appear stubbornly resistant to all known edumacational techniques and do their level best to skip class, and we all have our cognitive issues occasionally.The fact that there is such a variety of techniques suggests that none of them is ideal for all learning situations. The advice to use, say, micro-learning could be taken to mean "use ONLY micro-learning" but that would be a mistake, in just the same way as "send them to college" or "gamify it"! It's well-meaning but naive silver bullet advice.Consider how we learn stuff in general. We take classes, go to night school, take driving or diving or cookery lessons, read-up on stuff, watch You Tube vids, read/listen to/watch/contemplate sage advisors, ask someone ... and generally muddle through by ourselves, learning as we go from our successes and failures. |
Tool | |||
| 2020-02-20 16:41:25 | NBlog Feb 20 - proceed with caution (lien direct) |  Using the InfoSec 101 theme I mentioned on Feb 14th, I'm close to finishing the first set of presentation slides with a preponderance of yellow and black. Through a carefully chosen sequence of bright, clear images, no bullet points and very few written words, the slides tell a visual story based around risk. The core message is that information security is less a case of stopping the business from doing things, than of being vigilant. 'Proceed with caution' sums it up nicely.Given the elegance, simplicity and power of those 3 words, I'm not sure whether to elaborate on information risk and information security at all, in fact. I guess we'll mention a few current current threats, some recent incidents and typical controls in the speaker notes but I rather like the idea of leaving it up to the presenter/trainer to decide how to play things at run-time - during the induction courses and awareness program launch sessions for which the 101 module is destined. Some audiences will get it, effortlessly, while others might need a bit more of a steer, more of a clue about the point we're expressing here. I've blogged before about my strong preference for images over written words on training course and seminar slides. The audience should focus their energies on understanding what the present/trainer is putting across, rather than reading the words on the screen, and is there anything more sleep-inducing than an inept and often nervous presenter literally reading aloud his own slides, often great blocks of text in a dreadful monotone?It's not exactly death by PowerPoint, but close. "Take it easy, relax. Your eyelids feel heavy ..." The answer is glaringly obvious: swap the written words for diagrams and images. Visual impact is doubly important for induction courses since inductees are often assaulted by an avalanche of new information. There's a lot to take in - not just from the slides and maybe handouts but from the speakers/trainers too, plus their new colleagues. If our InfoSec 101 materials add to rather than slicing through the information fog, we\ Using the InfoSec 101 theme I mentioned on Feb 14th, I'm close to finishing the first set of presentation slides with a preponderance of yellow and black. Through a carefully chosen sequence of bright, clear images, no bullet points and very few written words, the slides tell a visual story based around risk. The core message is that information security is less a case of stopping the business from doing things, than of being vigilant. 'Proceed with caution' sums it up nicely.Given the elegance, simplicity and power of those 3 words, I'm not sure whether to elaborate on information risk and information security at all, in fact. I guess we'll mention a few current current threats, some recent incidents and typical controls in the speaker notes but I rather like the idea of leaving it up to the presenter/trainer to decide how to play things at run-time - during the induction courses and awareness program launch sessions for which the 101 module is destined. Some audiences will get it, effortlessly, while others might need a bit more of a steer, more of a clue about the point we're expressing here. I've blogged before about my strong preference for images over written words on training course and seminar slides. The audience should focus their energies on understanding what the present/trainer is putting across, rather than reading the words on the screen, and is there anything more sleep-inducing than an inept and often nervous presenter literally reading aloud his own slides, often great blocks of text in a dreadful monotone?It's not exactly death by PowerPoint, but close. "Take it easy, relax. Your eyelids feel heavy ..." The answer is glaringly obvious: swap the written words for diagrams and images. Visual impact is doubly important for induction courses since inductees are often assaulted by an avalanche of new information. There's a lot to take in - not just from the slides and maybe handouts but from the speakers/trainers too, plus their new colleagues. If our InfoSec 101 materials add to rather than slicing through the information fog, we\ |
||||
| 2020-02-19 18:03:26 | NBlog Feb 19 - Brahms and Liszt (lien direct) |  Fueled by a lot of Brahms and a wee tot of rum, half an hour's idle brainstorming on the purpose and objectives for information security awareness generated the following little Liszt:Rites, ritualsRite of passageRitual slaughterReligionsBelief systems Cult, visionary leader, positional power, faithSheep, lemmingsWolves, packs, threats, skillsGroup-think, conformityCompliance, rules, constraints, in the boxIndividuality, creativity, nonconformity, freedom, out of the boxHippies, communes, cliquesHallucinogensNoncomplianceCultural norms, expectationsCounter-cultural, bucking trendsConventions, habits, preferencesAutomatic behaviours, instinctsSocialising infosecSocial pressure, influence, shared valuesSocial acceptabilitySocial structures, hierarchies, linksNetworks and relationshipsFamilies, organizations, departments, teams, groups, cliquesNationsInteractions Fueled by a lot of Brahms and a wee tot of rum, half an hour's idle brainstorming on the purpose and objectives for information security awareness generated the following little Liszt:Rites, ritualsRite of passageRitual slaughterReligionsBelief systems Cult, visionary leader, positional power, faithSheep, lemmingsWolves, packs, threats, skillsGroup-think, conformityCompliance, rules, constraints, in the boxIndividuality, creativity, nonconformity, freedom, out of the boxHippies, communes, cliquesHallucinogensNoncomplianceCultural norms, expectationsCounter-cultural, bucking trendsConventions, habits, preferencesAutomatic behaviours, instinctsSocialising infosecSocial pressure, influence, shared valuesSocial acceptabilitySocial structures, hierarchies, linksNetworks and relationshipsFamilies, organizations, departments, teams, groups, cliquesNationsInteractions |
Guideline | |||
| 2020-02-17 19:25:21 | NBlog Feb 18 - neat and tidy (lien direct) |  My perfectionist streak flared up with a vengeance today.First I spent a productive couple of hours checking and revising the content of our generic/model Acceptable Use Policies, intending to include them in the updated InfoSec 101 module for March. Aside from reviewing and tinkering with the information content, this also involved standardising the formatting of the AUPs by using the same MS Word template with specific styles for all of them. The AUPs have been updated at various times in various NoticeBored modules and I noticed that, somewhere along the way, I must have changed the bullets and colouring for the 'acceptable use' and 'unacceptable use' points. Evidently I have also meddled with the boilerplate text that tops and tails each AUP, making them slightly inconsistent. To my beady eye, this will not do! Unsure how to name the model AUP files, I toyed with the idea of making a single multi-page document containing them all but customers may not want them all. Instead I settled on a numeric naming scheme. As I was doing that, I noticed the document properties also needed standardising. The properties are stored with each document and affect the directory listings. To get to this picture of neatness ... My perfectionist streak flared up with a vengeance today.First I spent a productive couple of hours checking and revising the content of our generic/model Acceptable Use Policies, intending to include them in the updated InfoSec 101 module for March. Aside from reviewing and tinkering with the information content, this also involved standardising the formatting of the AUPs by using the same MS Word template with specific styles for all of them. The AUPs have been updated at various times in various NoticeBored modules and I noticed that, somewhere along the way, I must have changed the bullets and colouring for the 'acceptable use' and 'unacceptable use' points. Evidently I have also meddled with the boilerplate text that tops and tails each AUP, making them slightly inconsistent. To my beady eye, this will not do! Unsure how to name the model AUP files, I toyed with the idea of making a single multi-page document containing them all but customers may not want them all. Instead I settled on a numeric naming scheme. As I was doing that, I noticed the document properties also needed standardising. The properties are stored with each document and affect the directory listings. To get to this picture of neatness ... ... I had to fiddle with the Tags and Authors for each of the 8 AUPs. The Tags are easy enough to update but changing the Author property is a little awkward: originally, the Author for all the files was "Gary" which, although technically ... I had to fiddle with the Tags and Authors for each of the 8 AUPs. The Tags are easy enough to update but changing the Author property is a little awkward: originally, the Author for all the files was "Gary" which, although technically |
||||
| 2020-02-17 07:40:03 | NBlog Feb 17 - tips on security induction sessions (lien direct) |  The InfoSec 101 management presentation is coming along ... but I'll need to rein in my enthusiasm for all things yellow to refocus on the information security essentials: one of the challenges with induction training is keeping it within a tight timescale. 'Speak fast!' is not the answer because the audience probably won't take it all in, given that information security is just one of several important induction topics. It's trial by fire for them.Some of our customers will have more time for induction training than others, so my cunning plan is to make the 101 presentations flexible. Customers who have the luxury of more time can elaborate on pertinent details and interact more extensively with the inductees. Those short of time may want to skim through or skip some of the slides ... but I hope to encourage them all to make the time to introduce inductees to the information security team. Making that personal link starts the long process of getting to know each other, with benefits on both sides as time goes on. For example, it's easier for workers to email, pick up the phone or drop in on someone they have already met, whether to ask a question, raise an issue or simply say "Hi!". 'Putting faces to names' is, to me, part of 'socialising information security', making it an integral part of the corporate culture. On that point, I will be encouraging NB customers to allocate suitable information risk and security pro's to conduct the induction courses, in person. Information Security's 'customer services' or 'help desk' people and experienced trainers are the obvious choices for this job. Furthermore, if the Information Security Manager or CISO or CEO turns up, in person, to say hello and reinforce some point or other (implying a little preparation), that sends a more subtle message about the importance of information security for new workers. It's a powerful technique to cut through the avalanche of information assaulting inductees.If it is simply not practicable for the relevant InfoSec people to make the time to attend induction courses, other approaches include:Playing a brief 'talking heads' video statement by the ISM, CISO or CEO;A quick live phone call or videoconference appearance by the ISM, CISO or CEO during the session;Showing 'meet the team' biographies - mugshots and a few choice words about the pro's in the InfoSec team (which, in fact, means everyone in the organization, including those currently in the induction session!). Another cool idea is to invite inductees to come along to Information Security eve The InfoSec 101 management presentation is coming along ... but I'll need to rein in my enthusiasm for all things yellow to refocus on the information security essentials: one of the challenges with induction training is keeping it within a tight timescale. 'Speak fast!' is not the answer because the audience probably won't take it all in, given that information security is just one of several important induction topics. It's trial by fire for them.Some of our customers will have more time for induction training than others, so my cunning plan is to make the 101 presentations flexible. Customers who have the luxury of more time can elaborate on pertinent details and interact more extensively with the inductees. Those short of time may want to skim through or skip some of the slides ... but I hope to encourage them all to make the time to introduce inductees to the information security team. Making that personal link starts the long process of getting to know each other, with benefits on both sides as time goes on. For example, it's easier for workers to email, pick up the phone or drop in on someone they have already met, whether to ask a question, raise an issue or simply say "Hi!". 'Putting faces to names' is, to me, part of 'socialising information security', making it an integral part of the corporate culture. On that point, I will be encouraging NB customers to allocate suitable information risk and security pro's to conduct the induction courses, in person. Information Security's 'customer services' or 'help desk' people and experienced trainers are the obvious choices for this job. Furthermore, if the Information Security Manager or CISO or CEO turns up, in person, to say hello and reinforce some point or other (implying a little preparation), that sends a more subtle message about the importance of information security for new workers. It's a powerful technique to cut through the avalanche of information assaulting inductees.If it is simply not practicable for the relevant InfoSec people to make the time to attend induction courses, other approaches include:Playing a brief 'talking heads' video statement by the ISM, CISO or CEO;A quick live phone call or videoconference appearance by the ISM, CISO or CEO during the session;Showing 'meet the team' biographies - mugshots and a few choice words about the pro's in the InfoSec team (which, in fact, means everyone in the organization, including those currently in the induction session!). Another cool idea is to invite inductees to come along to Information Security eve |
||||
| 2020-02-14 11:01:59 | NBlog Feb 14 - this year\'s InfoSec 101 theme (lien direct) |  I've come up with a new theme for the InfoSec 101 presentations this year, driven by a visual metaphor. As I was picking out general-purpose security-related graphics from our stock for the slide decks, I noticed a preponderance of yellow ... which led me to think about warnings in nature (such as the yellow and black stripes of this wasp) and on the roads (driving hazards), plus the classic Red-Amber-Green traffic lights. I've come up with a new theme for the InfoSec 101 presentations this year, driven by a visual metaphor. As I was picking out general-purpose security-related graphics from our stock for the slide decks, I noticed a preponderance of yellow ... which led me to think about warnings in nature (such as the yellow and black stripes of this wasp) and on the roads (driving hazards), plus the classic Red-Amber-Green traffic lights. RAG colours are a simple visual cue, well suited to a basic induction or awareness refresher module. The concept gradually forming in my head is that we would like to get to green (as in "Go ahead, get on with the business ... safely") and, wherever possible, avoid the reds ("STOP! Dangerous!"), so amber ("Caution: hazards") is the path trodden by the security awareness and training program. I have in mind using a few reds and greens to illustrate the range but mostly I think we'll focus on those ambers in the middle ground. RAG colours are a simple visual cue, well suited to a basic induction or awareness refresher module. The concept gradually forming in my head is that we would like to get to green (as in "Go ahead, get on with the business ... safely") and, wherever possible, avoid the reds ("STOP! Dangerous!"), so amber ("Caution: hazards") is the path trodden by the security awareness and training program. I have in mind using a few reds and greens to illustrate the range but mostly I think we'll focus on those ambers in the middle ground.  The core message concerns vigilance, caution and situational awareness. We can't be there all the time, pointing out dangers to our colleagues, so they need to take responsibility for their own well-being - for example, hesitating and thinking twice about clicking those too-good-to-be-true offers sitting in their email inboxes and social media messaging.We can even have a bit of fun with the roadsigns while we're at it, raise the odd laugh or wry smile maybe. Who says warning notices and awareness sessions should be dull and boring? The core message concerns vigilance, caution and situational awareness. We can't be there all the time, pointing out dangers to our colleagues, so they need to take responsibility for their own well-being - for example, hesitating and thinking twice about clicking those too-good-to-be-true offers sitting in their email inboxes and social media messaging.We can even have a bit of fun with the roadsigns while we're at it, raise the odd laugh or wry smile maybe. Who says warning notices and awareness sessions should be dull and boring? |
||||
| 2020-02-14 07:40:06 | NBlog Feb 12 - terms of art (lien direct) | Yesterday I wrote about the laborious process of condensing our comprehensive 300+ page information risk and security glossary to something much more succinct and appropriate for inductees, new to the organization and the topic. So far, the InfoSec 101 glossary is down to just 15 pages but it's not finished yet. I am systematically reconsidering the relevance of each term and, for those destined to remain in the glossary, composing a straightforward explanation that encapsulates the concept in just a few simple words. Well that's the aim anyway! I balked at describing cryptography, even though I'd quite like everyone to have at least a rough idea of what it is about. Maybe today the inspiration will come.  There's a nice bonus to all this: the terms that made it into the 101 glossary will go into a word-grid and possibly also a crossword if there's time. If people find unfamiliar words in the puzzles, they can look them up in the glossary to find out what they mean ... and it doesn't stop there: the glossary is designed to intrigue as well as inform. Any specialist terms in the explanations are hyperlinked to the corresponding entries, encouraging readers to click and read-on, hopefully browsing the whole thing. We want it to be as sticky as a tar-pit for newbies. In millennia to come, paleontologists will be digging out the bones of Novi operatur, a long-forgotten but remarkably vigilant humanoid species from the 21st Century. But wait, there's more! We also use word lists to generate word clouds, visual depictions of the topic that again intrigue and inform - this sort of thing: There's a nice bonus to all this: the terms that made it into the 101 glossary will go into a word-grid and possibly also a crossword if there's time. If people find unfamiliar words in the puzzles, they can look them up in the glossary to find out what they mean ... and it doesn't stop there: the glossary is designed to intrigue as well as inform. Any specialist terms in the explanations are hyperlinked to the corresponding entries, encouraging readers to click and read-on, hopefully browsing the whole thing. We want it to be as sticky as a tar-pit for newbies. In millennia to come, paleontologists will be digging out the bones of Novi operatur, a long-forgotten but remarkably vigilant humanoid species from the 21st Century. But wait, there's more! We also use word lists to generate word clouds, visual depictions of the topic that again intrigue and inform - this sort of thing: That's one I created for the 'surveillance' awareness module, an unusual topic that led us through corporate oversight and security monitoring into the realm of spooks and spies. The words on the graphic remind me of our coverage when the module was prepared three years ago - things such as Ed Snowden's revelations about t That's one I created for the 'surveillance' awareness module, an unusual topic that led us through corporate oversight and security monitoring into the realm of spooks and spies. The words on the graphic remind me of our coverage when the module was prepared three years ago - things such as Ed Snowden's revelations about t |
||||
| 2020-02-11 14:01:46 | NBlog Feb 11 - InfoSec 101 terms (lien direct) |  Our information risk and security glossary has grown steadily over the years to a document of 100,000 words over 346 pages defining about 3,000 terms. That's easily a book's worth (maybe we should publish it!), and way too much information for the InfoSec 101 module, so I spent yesterday paring it down to a more sensible size. The easiest approach was to chop out obscure/specialist terms and their definitions, then go through again to catch the ones I missed. Next I set to work trimming down the definitions for the remaining terms, simplifying the wording and removing the quoted extracts from the ISO27k and other standards and references. Some terms are context-dependent - they normally mean one thing but can mean something else. For the purposes of the 101 module, I've chopped off the 'something else' explanations.So now we're down to 11,000 words and 40 pages, defining about 400 terms. Still more than I'd like. The most recent 2017 revision of the 101 module included a glossary of 2,000 words and 10 pages defining about 100 terms. Hmmm, it will be a struggle to get it down that far, but I'll give it a go. Time for another few cycles of chopping and trimming ... Our information risk and security glossary has grown steadily over the years to a document of 100,000 words over 346 pages defining about 3,000 terms. That's easily a book's worth (maybe we should publish it!), and way too much information for the InfoSec 101 module, so I spent yesterday paring it down to a more sensible size. The easiest approach was to chop out obscure/specialist terms and their definitions, then go through again to catch the ones I missed. Next I set to work trimming down the definitions for the remaining terms, simplifying the wording and removing the quoted extracts from the ISO27k and other standards and references. Some terms are context-dependent - they normally mean one thing but can mean something else. For the purposes of the 101 module, I've chopped off the 'something else' explanations.So now we're down to 11,000 words and 40 pages, defining about 400 terms. Still more than I'd like. The most recent 2017 revision of the 101 module included a glossary of 2,000 words and 10 pages defining about 100 terms. Hmmm, it will be a struggle to get it down that far, but I'll give it a go. Time for another few cycles of chopping and trimming ... |
||||
| 2020-02-11 13:36:19 | NBlog Feb 8 - InfoSec 101 (lien direct) |  For March, we're working on our final NoticeBored security awareness module, an update to "InfoSec 101". Unlike the other NoticeBored modules, this covers several information risk and security topics at a basic level. Its main purpose is to provide a gentle introduction, for example in new employee induction or orientation training, or as a launch module for organizations just starting or re-starting their awareness and training programs, bringing everybody quickly up to speed.So what should it cover? For the general staff audience, I'm thinking:Information risk and security fundamentals, including common terms Policies and procedures, with a touch of compliance User IDs and passwords ... and why they matter Backups Patching Phishing and other social engineering scams Apps and mobile security Ransomware and antivirus Physical security in the office Physical security when on the road or working from home Cloud, Internet, network and system security basics Vigilance: spotting, reacting to and reporting concerns Who's who - putting faces to the names behind information security For the management audience:Information risk and security management basics e.g. net value of incidents avoided/reduced less the costs of controlA little more on compliance e.g. privacy Roles, responsibilities and accountability, with a little on governance Strategies, architecture, plans and big-picture-stuff Insider/outsider threats includ For March, we're working on our final NoticeBored security awareness module, an update to "InfoSec 101". Unlike the other NoticeBored modules, this covers several information risk and security topics at a basic level. Its main purpose is to provide a gentle introduction, for example in new employee induction or orientation training, or as a launch module for organizations just starting or re-starting their awareness and training programs, bringing everybody quickly up to speed.So what should it cover? For the general staff audience, I'm thinking:Information risk and security fundamentals, including common terms Policies and procedures, with a touch of compliance User IDs and passwords ... and why they matter Backups Patching Phishing and other social engineering scams Apps and mobile security Ransomware and antivirus Physical security in the office Physical security when on the road or working from home Cloud, Internet, network and system security basics Vigilance: spotting, reacting to and reporting concerns Who's who - putting faces to the names behind information security For the management audience:Information risk and security management basics e.g. net value of incidents avoided/reduced less the costs of controlA little more on compliance e.g. privacy Roles, responsibilities and accountability, with a little on governance Strategies, architecture, plans and big-picture-stuff Insider/outsider threats includ |
||||
| 2020-02-05 20:01:16 | NBlog Feb 5 - YMMV (lien direct) |  Once more today I find myself drawn into an interminable discussion over on the ISO27k Forum.This time around, it's with a member who (as I see it) steadfastly refuses to remove his IT blinkers and acknowledge that - perhaps - there's more to information risk and security management than IT security, that he can't simply ignore the rest or claim/pretend that it's someone else's problem.His little IT world defines his horizon, and everything beyond the edge is (to him) at once both unseen and scary.And to be fair to him, I'm just the same. OK, so my blinkers don't say "IT" all over them but it's true I perceive the world in terms of information risks. I can't help it. It's how my brain works. I have something of an idea of what lies beyond that horizon, but nevertheless it's scary because that's not my domain of knowledge, experience and expertise. It's not my home turf. It makes me uncomfortable.Take 'financial risk' for example. I know a tiny bit about return on investment, exchange rates, stock markets, money markets and so on ... but I'm well out of my depth when it comes to, say, futures and options. I thoroughly enjoyed reading Nick Leeson's book about his shenanigans that brought down the veritable British financial institution of Barings Bank but I freely admit that, despite his patient and eloquent description in the book, I didn't entirely understand the ins-and-outs of his fraud (nor indeed did the bank's managers and auditors, until it was too late!). Although the story sort of made sense at the time, I was struggling to understand and, now, I'd fall in a heap if I tried to recall and explain it.Arguably there's a difference, though, between me and my rather naive, blinkered colleague on the ISO27k Forum. Specifically, I'm sufficiently self-aware to know my limits. If I wanted/needed to get into, say, financial risk, I'd seek out and rely on someone who's good at that stuff, someone with experience and reputati Once more today I find myself drawn into an interminable discussion over on the ISO27k Forum.This time around, it's with a member who (as I see it) steadfastly refuses to remove his IT blinkers and acknowledge that - perhaps - there's more to information risk and security management than IT security, that he can't simply ignore the rest or claim/pretend that it's someone else's problem.His little IT world defines his horizon, and everything beyond the edge is (to him) at once both unseen and scary.And to be fair to him, I'm just the same. OK, so my blinkers don't say "IT" all over them but it's true I perceive the world in terms of information risks. I can't help it. It's how my brain works. I have something of an idea of what lies beyond that horizon, but nevertheless it's scary because that's not my domain of knowledge, experience and expertise. It's not my home turf. It makes me uncomfortable.Take 'financial risk' for example. I know a tiny bit about return on investment, exchange rates, stock markets, money markets and so on ... but I'm well out of my depth when it comes to, say, futures and options. I thoroughly enjoyed reading Nick Leeson's book about his shenanigans that brought down the veritable British financial institution of Barings Bank but I freely admit that, despite his patient and eloquent description in the book, I didn't entirely understand the ins-and-outs of his fraud (nor indeed did the bank's managers and auditors, until it was too late!). Although the story sort of made sense at the time, I was struggling to understand and, now, I'd fall in a heap if I tried to recall and explain it.Arguably there's a difference, though, between me and my rather naive, blinkered colleague on the ISO27k Forum. Specifically, I'm sufficiently self-aware to know my limits. If I wanted/needed to get into, say, financial risk, I'd seek out and rely on someone who's good at that stuff, someone with experience and reputati |
||||
| 2020-01-31 18:57:10 | NBlog February - just-in-time security awareness (lien direct) |  This afternoon, we completed, proofread and published February's security awareness module on malware, a few short hours before our (self imposed!) end-of-month deadline. The atmosphere in the office has grown increasingly tense this week as the deadline loomed. Early in January we took the decision to use the Travelex ransomware incident as a very topical (live!) case study for the module, and as such we were hostage to their timeline. By sheer chance, the main Travelex websites were up and running again this very morning, neatly tying off the month's events.Comparing and contrasting the Sony and Travelex ransomware incidents has been fascinating: they each handled the situations in their own way, and yet there are common themes - for instance they were both forced to fend off an inquisitive (hostile!) pack of journalists. Travelex also made effective use of social media, and completed the main part of their recovery roughly twice as fast as Sony, so things have moved on in the five years since Sony Pictures Entertainment were all over the headlines with salacious gossip about film stars and wild speculation about North Korean cybertage.Meanwhile, down here in rural NZ, our 4G wireless broadband Internet connection has been playing up something rotten. It's not good at the best of times but has been notably unreliable this week until, with perfect timing, the connection dropped out entirely as I was uploading the completed awareness module to our server. You probably know that we're a micro-company. I am the network technician, the IT Department in fact. Also the Procurement, Finance, Production, Marketing and Customer Services Departments, and yes I even make the tea. I'm not doing this totally alone, quite, but we rely on third party suppliers for various essential services, such as our comms. This week I could really have done with some technical help to get the broadband connection fixed while finishing the awareness materials, but as it was I found myself lashing-up a temporary Internet connection just to deliver the module at the most stressful time of the month.On top of that, strong winds brought down trees across the track ... and guess who is the Chainsaw Operative part of the Grounds Maintenance Department!Such is life. Business continuity is a challenge even for a microbusiness in sleepy NZ. But, like Travelex, we made it through and live to fight another day. This afternoon, we completed, proofread and published February's security awareness module on malware, a few short hours before our (self imposed!) end-of-month deadline. The atmosphere in the office has grown increasingly tense this week as the deadline loomed. Early in January we took the decision to use the Travelex ransomware incident as a very topical (live!) case study for the module, and as such we were hostage to their timeline. By sheer chance, the main Travelex websites were up and running again this very morning, neatly tying off the month's events.Comparing and contrasting the Sony and Travelex ransomware incidents has been fascinating: they each handled the situations in their own way, and yet there are common themes - for instance they were both forced to fend off an inquisitive (hostile!) pack of journalists. Travelex also made effective use of social media, and completed the main part of their recovery roughly twice as fast as Sony, so things have moved on in the five years since Sony Pictures Entertainment were all over the headlines with salacious gossip about film stars and wild speculation about North Korean cybertage.Meanwhile, down here in rural NZ, our 4G wireless broadband Internet connection has been playing up something rotten. It's not good at the best of times but has been notably unreliable this week until, with perfect timing, the connection dropped out entirely as I was uploading the completed awareness module to our server. You probably know that we're a micro-company. I am the network technician, the IT Department in fact. Also the Procurement, Finance, Production, Marketing and Customer Services Departments, and yes I even make the tea. I'm not doing this totally alone, quite, but we rely on third party suppliers for various essential services, such as our comms. This week I could really have done with some technical help to get the broadband connection fixed while finishing the awareness materials, but as it was I found myself lashing-up a temporary Internet connection just to deliver the module at the most stressful time of the month.On top of that, strong winds brought down trees across the track ... and guess who is the Chainsaw Operative part of the Grounds Maintenance Department!Such is life. Business continuity is a challenge even for a microbusiness in sleepy NZ. But, like Travelex, we made it through and live to fight another day. |
Ransomware | |||
| 2020-01-30 11:02:19 | NBlog Jan 30 - simplicity itself (lien direct) |  "Simplicity is the default unless there's a good business reason to do something else. What is typically lacking are the business reasons ..."That comment on CISSPforum set me pondering during this morning's caffeine fix. We've been chatting about some training webinar sessions recently promoted by (ISC)2. Some say they over-simplify information security to the point of trivialising and perhaps misleading people.If you follow NBlog, you'll know that this month I have been slaving away on an awareness module covering malware, a topic we've covered many times before - particularly the avoidance or prevention of infections but this year a customer asked us for something on publicly disclosing incidents in progress, a disarmingly simple request that turned into a fascinating foray into the post-malware-infection incident management and resolution phase for a change. I've been exploring and writing about what does, could or should happen after malware 'hits' - from that dramatic moment the ransomware demands appear on everyone's screens, for example. What follows is quite an intricate and frantic dance, in fact, involving management, IT and other staff, customers, suppliers and partners, regulators/authorities, journalists and the news + social media etc. plus the Incident Management Team, infosec and business continuity pros trying to keep everything on track, the legal team figuring out who to sue, the compliance pros wondering how not to get sued, and various hired-hands helping with forensics, disinfection and finding then retrospectively plugging whatever holes were initially exploited by the malware. All the while, the menacing hackers and cybercrims are wielding big coshes in the shape of threats to make the disruption permanent and terminal, and/or to disclose whatever juicy tidbits of corporate and personal info they've previously stolen (the CEO's emails, or browser history perhaps?). And all the while the systems, data, business processes/activities, websites and apps are being maintained, recovered or restored. Brands and relationships are under pressure, along with all the dancers. It's an intensely stressful time for them, I'm sure. The approach we've taken is to explore the timeline of an actual incident, in real time as it happens (as it happens), building a case study around the ongoing Travelex ransomware incident: the sequence forms a convenient thread to lead people through the story, thinking about what's going on at each stage and imagining how it would be if a similar incident happened 'here'. I've drawn up a simplified Travelex incident timeline in the same style as the one I drew for the Sony Pictures Entertainment fiasco 5 years back, pointing out some of the key events plus the phases of the overall process. The new Travelex version ('in press'!) is simpler "Simplicity is the default unless there's a good business reason to do something else. What is typically lacking are the business reasons ..."That comment on CISSPforum set me pondering during this morning's caffeine fix. We've been chatting about some training webinar sessions recently promoted by (ISC)2. Some say they over-simplify information security to the point of trivialising and perhaps misleading people.If you follow NBlog, you'll know that this month I have been slaving away on an awareness module covering malware, a topic we've covered many times before - particularly the avoidance or prevention of infections but this year a customer asked us for something on publicly disclosing incidents in progress, a disarmingly simple request that turned into a fascinating foray into the post-malware-infection incident management and resolution phase for a change. I've been exploring and writing about what does, could or should happen after malware 'hits' - from that dramatic moment the ransomware demands appear on everyone's screens, for example. What follows is quite an intricate and frantic dance, in fact, involving management, IT and other staff, customers, suppliers and partners, regulators/authorities, journalists and the news + social media etc. plus the Incident Management Team, infosec and business continuity pros trying to keep everything on track, the legal team figuring out who to sue, the compliance pros wondering how not to get sued, and various hired-hands helping with forensics, disinfection and finding then retrospectively plugging whatever holes were initially exploited by the malware. All the while, the menacing hackers and cybercrims are wielding big coshes in the shape of threats to make the disruption permanent and terminal, and/or to disclose whatever juicy tidbits of corporate and personal info they've previously stolen (the CEO's emails, or browser history perhaps?). And all the while the systems, data, business processes/activities, websites and apps are being maintained, recovered or restored. Brands and relationships are under pressure, along with all the dancers. It's an intensely stressful time for them, I'm sure. The approach we've taken is to explore the timeline of an actual incident, in real time as it happens (as it happens), building a case study around the ongoing Travelex ransomware incident: the sequence forms a convenient thread to lead people through the story, thinking about what's going on at each stage and imagining how it would be if a similar incident happened 'here'. I've drawn up a simplified Travelex incident timeline in the same style as the one I drew for the Sony Pictures Entertainment fiasco 5 years back, pointing out some of the key events plus the phases of the overall process. The new Travelex version ('in press'!) is simpler |
Ransomware Malware Guideline | |||
| 2020-01-29 18:59:32 | NBlog Jan 29 - taking it to the wire (lien direct) |  Today since before 5am I've been slaving away over a hot keyboard in a steamy hot office on a flaming hot topic: malware awareness. As you may have noticed here on the blog, all month long I've been systematically tracking the ongoing Travelex incident, observing from a safe distance the unsightly aftermath of another ugly malware - and business continuity - incident unfolding before our very eyes.With our end-of-month delivery deadline looming large, it's time to draw out the lessons from the case study and weave the whole episode into a compelling tale for February's awareness module - well, three closely-related tales in fact since as always we're catering for the differing perspectives, concerns and information needs of our customers' staff, management and professional audiences. What have we learnt this month? What has happened, and why? What do we think might/should have been going on behind the scenes, out of the glare of the media spotlight? What were the dilemmas facing Travelex's management and IT people?How might things have played out if the incident had been handled differently?And, most importantly of all, what are our carry-outs, our take-home learning points and the Things We Ought to be Doing? Taking the whole sorry episode into account, what does it mean for us, our organization, right now?You'll find a few clues to the answers in the blog ... but for the full nine yards you'll need to hang on just a few short days until the awareness module is completed and published. Or of course Today since before 5am I've been slaving away over a hot keyboard in a steamy hot office on a flaming hot topic: malware awareness. As you may have noticed here on the blog, all month long I've been systematically tracking the ongoing Travelex incident, observing from a safe distance the unsightly aftermath of another ugly malware - and business continuity - incident unfolding before our very eyes.With our end-of-month delivery deadline looming large, it's time to draw out the lessons from the case study and weave the whole episode into a compelling tale for February's awareness module - well, three closely-related tales in fact since as always we're catering for the differing perspectives, concerns and information needs of our customers' staff, management and professional audiences. What have we learnt this month? What has happened, and why? What do we think might/should have been going on behind the scenes, out of the glare of the media spotlight? What were the dilemmas facing Travelex's management and IT people?How might things have played out if the incident had been handled differently?And, most importantly of all, what are our carry-outs, our take-home learning points and the Things We Ought to be Doing? Taking the whole sorry episode into account, what does it mean for us, our organization, right now?You'll find a few clues to the answers in the blog ... but for the full nine yards you'll need to hang on just a few short days until the awareness module is completed and published. Or of course |
Malware | |||
| 2020-01-29 05:30:36 | NBlog Jan 28 - woe betide ... (lien direct) |  .... any organization unfortunate enough to suffer a privacy breach today, of all days, being "Data Privacy Day". In the unlikely event that there are no new ones today, recent newsworthy breaches are liable to be trawled up and paraded across the media, again. I've been writing about preparing to deal with malware incidents all this month. Managing or controlling the publicity aspects is trickier than it may appear. Sony pulled a master stroke in getting its legal team to threaten action against journalists who continued to exploit the tittle-tattle disclosed in the Sony Pictures Entertainment breach five years ago - but that's not a universally applicable approach. Travelex did well to get basic, static web pages published quickly, plus a talking-heads video explanation/apology by the CEO ... but ask their retail customers whether they feel 'informed', while the promised restoration of services is patently taking longer than anyone (except perhaps the cybercrims behind the attack) wants.Blend in the compliance aspects as well for good measure. I suspect British Airways and Marriott International, for instance, would have much preferred to take their corporal punishment under GDPR in private, rather than baring their bottoms on News At Ten.There's a fine line between their being directly blamed for causing the incidents, and being blamed for failing to prevent them - a line which Public Relations teams might do well to consider. The real culprits here are the cunning VXers, hackers and cybercrims, rather than their targets. Defending all points at once is undoubtedly much tougher than exploiting one or more vulnerabilities. It's not a fair fight! Too bad: that's how it is ... but maybe it wouldn't hurt to explain that.By the way, the issues multiply when you take into account the wide range of people and organizations who want to know and/or should be kept informed. Take employees, for instance: .... any organization unfortunate enough to suffer a privacy breach today, of all days, being "Data Privacy Day". In the unlikely event that there are no new ones today, recent newsworthy breaches are liable to be trawled up and paraded across the media, again. I've been writing about preparing to deal with malware incidents all this month. Managing or controlling the publicity aspects is trickier than it may appear. Sony pulled a master stroke in getting its legal team to threaten action against journalists who continued to exploit the tittle-tattle disclosed in the Sony Pictures Entertainment breach five years ago - but that's not a universally applicable approach. Travelex did well to get basic, static web pages published quickly, plus a talking-heads video explanation/apology by the CEO ... but ask their retail customers whether they feel 'informed', while the promised restoration of services is patently taking longer than anyone (except perhaps the cybercrims behind the attack) wants.Blend in the compliance aspects as well for good measure. I suspect British Airways and Marriott International, for instance, would have much preferred to take their corporal punishment under GDPR in private, rather than baring their bottoms on News At Ten.There's a fine line between their being directly blamed for causing the incidents, and being blamed for failing to prevent them - a line which Public Relations teams might do well to consider. The real culprits here are the cunning VXers, hackers and cybercrims, rather than their targets. Defending all points at once is undoubtedly much tougher than exploiting one or more vulnerabilities. It's not a fair fight! Too bad: that's how it is ... but maybe it wouldn't hurt to explain that.By the way, the issues multiply when you take into account the wide range of people and organizations who want to know and/or should be kept informed. Take employees, for instance: |
Malware | |||
| 2020-01-29 05:23:20 | NBlog Jan 25 - data privacy day (lien direct) |  On Tuesday, data privacy day, privacy will be top of the agenda.Well, OK, not top exactly, not even very high if I'm honest.And apart from mine, I'm not sure whose agenda I'm talking about.Evidently it's about "data privacy", not other kinds of privacy, oh no.If I'm coming across just a little cynically, then evidently I need to try harder.I bumped into data privacy day while searching for something privacy related - I forget exactly what, now. Otherwise, it would surely have passed me by, and maybe you too, dear blog reader.Anyway, data privacy day appears to date back to Jan 28th 1981 when Convention 108 was signed in conventional Europe. "The Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data" was among the first, if not the very first, data protection regulation, predating today's privacy laws and regs.In 2006, the Council of Europe launched Data Privacy Day as an annual event on January 28th.Data privacy day was later taken up by some American organizations. On Tuesday, data privacy day, privacy will be top of the agenda.Well, OK, not top exactly, not even very high if I'm honest.And apart from mine, I'm not sure whose agenda I'm talking about.Evidently it's about "data privacy", not other kinds of privacy, oh no.If I'm coming across just a little cynically, then evidently I need to try harder.I bumped into data privacy day while searching for something privacy related - I forget exactly what, now. Otherwise, it would surely have passed me by, and maybe you too, dear blog reader.Anyway, data privacy day appears to date back to Jan 28th 1981 when Convention 108 was signed in conventional Europe. "The Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data" was among the first, if not the very first, data protection regulation, predating today's privacy laws and regs.In 2006, the Council of Europe launched Data Privacy Day as an annual event on January 28th.Data privacy day was later taken up by some American organizations. |
Guideline | |||
| 2020-01-27 16:54:17 | NBlog Jan 27 - MD/CISO\'s question time (lien direct) |  Seems I'm not the only ravenous shark circling the Travelex ransomware incident.Over at the Institute of Chartered Accountants in England and Wales website, Kirstin Gillon points out there are learning opportunities for senior management in this "horror story".Specifically, Kirstin suggests posing six awkward questions of those responsible for managing incidents and risks of this nature ... Seems I'm not the only ravenous shark circling the Travelex ransomware incident.Over at the Institute of Chartered Accountants in England and Wales website, Kirstin Gillon points out there are learning opportunities for senior management in this "horror story".Specifically, Kirstin suggests posing six awkward questions of those responsible for managing incidents and risks of this nature ... Rhetorical questions of this nature are not a bad way to get management thinking and talking about the important issues arising - a valuable activity in its own right although it falls some way short of taking decisions leading to appropriate action. Admittedly, there's an art to framing and posing such questions. Kirstin's questions are along the right lines, a good starting point at least.Faced with such questions, some Boards and management teams will immediately 'get it', initiating further work to explore the issues, evaluate the risks and controls more deeply, and if appropriate propose corrective actions to a Rhetorical questions of this nature are not a bad way to get management thinking and talking about the important issues arising - a valuable activity in its own right although it falls some way short of taking decisions leading to appropriate action. Admittedly, there's an art to framing and posing such questions. Kirstin's questions are along the right lines, a good starting point at least.Faced with such questions, some Boards and management teams will immediately 'get it', initiating further work to explore the issues, evaluate the risks and controls more deeply, and if appropriate propose corrective actions to a |
Ransomware Malware Guideline | |||
| 2020-01-24 08:37:48 | NBlog Jan 24 - information, data, knowledge And All That (lien direct) |  On the ISO27k Forum lately we've been discussing something that comes up repeatedly, a zombie topic you could say since the discussion is never really settled to everyone's complete satisfaction. There's always more to say.The discussion concerns the disarmingly simple phrase "information asset", used in some but no longer defined in any of the ISO27k standards. Among other things, we've discussed whether people/workers can be classed as information assets, hence information risks associated with people potentially fall within scope of an ISO27k ISMS.Yesterday, Mat said:"Knowledge is generally broken down into three different types - explicit, implicit, and tacit. When we are talking about classing employees as an asset or simply treating the information that they know as an asset, I think maybe this can be broken down further using these different knowledge types. Explicit knowledge is knowledge that is easily transferable, can be recorded and stored. Things like standard work instructions, guides, procedures, policies. Due to the nature of this information, it seems obvious to class the information itself as the asset here - you can mitigate the risk of information loss simply by recording the information. Implicit knowledge is the practical application of explicit knowledge. This can include knowing your way around a particular security product, or a particular piece of equipment. This type of knowledge is difficult to record, however, things like best practices are the best attempt although it's difficult to include the entire background knowledge of the best practice. Due to this, loss of this information is difficult to completely mitigate, and hence, I think the employee here could be classed as the information asset. The best mitigation is to keep the employee. Tacit knowledge is the practical application of implicit knowledge. Examples of this are knowing not only a particu On the ISO27k Forum lately we've been discussing something that comes up repeatedly, a zombie topic you could say since the discussion is never really settled to everyone's complete satisfaction. There's always more to say.The discussion concerns the disarmingly simple phrase "information asset", used in some but no longer defined in any of the ISO27k standards. Among other things, we've discussed whether people/workers can be classed as information assets, hence information risks associated with people potentially fall within scope of an ISO27k ISMS.Yesterday, Mat said:"Knowledge is generally broken down into three different types - explicit, implicit, and tacit. When we are talking about classing employees as an asset or simply treating the information that they know as an asset, I think maybe this can be broken down further using these different knowledge types. Explicit knowledge is knowledge that is easily transferable, can be recorded and stored. Things like standard work instructions, guides, procedures, policies. Due to the nature of this information, it seems obvious to class the information itself as the asset here - you can mitigate the risk of information loss simply by recording the information. Implicit knowledge is the practical application of explicit knowledge. This can include knowing your way around a particular security product, or a particular piece of equipment. This type of knowledge is difficult to record, however, things like best practices are the best attempt although it's difficult to include the entire background knowledge of the best practice. Due to this, loss of this information is difficult to completely mitigate, and hence, I think the employee here could be classed as the information asset. The best mitigation is to keep the employee. Tacit knowledge is the practical application of implicit knowledge. Examples of this are knowing not only a particu |
Guideline |
To see everything:
Our RSS (filtrered)
