What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-05-25 17:15:13 | Linguistic Analysis Suggests WannaCry Ransomware Is the Work of a Chinese-Speaking Crook (lien direct) | According to a linguistic analysis of the WannaCry ransom notes, the ransomware appears to be the work of a Chinese-speaking author, according to Jon Condra and John Costello, two Flashpoint researchers. [...] | Wannacry | |||
| 2017-05-25 17:05:22 | Linguistic Analysis Suggests WannaCry Authors Speak Chinese (lien direct) | 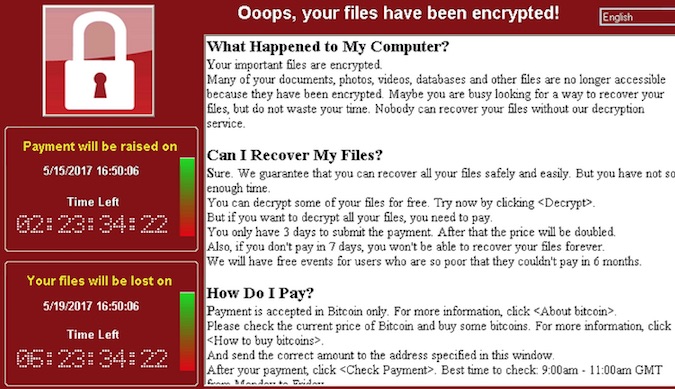
|
Wannacry | |||
| 2017-05-25 17:00:43 | WannaCry Ransom Note Written by Chinese, English Speaking Authors (lien direct) | A linguistics analysis of the 28 ransom notes included with WannaCry indicate that native Chinese and English speakers wrote the original note, Flashpoint said. | Wannacry | |||
| 2017-05-25 16:00:37 | 5 Things to Know About WannaCrypt (lien direct) | The world saw one of the largest ransomware attacks conducted so far just a couple of weeks ago. The story has captured public attention for longer than most digital security stories, and for good reason. From its shadowy origins to its very visible effects, the ransomware known as 'WannaCrypt' or 'WannaCry' is the topic for today's edition of The Checklist. | Wannacry | |||
| 2017-05-25 15:21:13 | Unwrapping the Mystery: Did a Big, Slimy Internet Worm Make Hundreds of Organizations WannaCry? (lien direct) | IBM X-Force revealed that WannaCry spread to its targets like a computer worm. But unlike a classic worm, it carried a malicious payload of ransomware. | Wannacry | |||
| 2017-05-25 13:00:00 | Lucky Security (lien direct) |
 Many years ago, I was working at a financial institute that processed several millions in transactions every night. Like many institutes, it relied on a (t)rusty mainframe to crunch through the numbers overnight.
These were the days where business continuity was a relatively simple process. You simply had two of everything. So there were two overnight batch processes to process payments, the primary and a backup.
The backup was only used in emergencies, and there was a process to swap systems to use the backup if need be.
It so happened that there was a developer who had grown tired of working and decided it would be a good idea to plot a heist and retire.
The plan was relatively simple. To introduce an extra payment instruction of several million to be transferred to an offshore personal account.
All that was needed was a few lines of code inserted into the overnight batch process to make it all happen.
However, the slight snag was that it wasn't very easy to make any changes to the production system. It was closely monitored, and all changes were subject to strict scrutiny and several layers of approval. Any changes would have raised many questions, ones for which there were no good answers. But the devilishly-minded developer had other plans. The backup batch job wasn't subject to the same rigour. So, the developer figured that if they inserted the code into the backup system it could go undetected.
As the developer anticipated, the commands were successfully inserted into the backup process without raising any alarm bells. Now, all the developer needed to do was to wait for the production system to hit an issue and for processing to take place through the backup system.
This presented a problem though. Once the payment instruction had been executed, sending millions into their offshore account, the developer would need to get out of the country quickly before the payment discrepancy was discovered.
The plan was relatively simple, take a flight to a country that had a non-extradition treaty. Second was to extract all of the money out and place into several other accounts to limit any chances of payment being reversed and to make tracking difficult.
Everything was set and ready to go. The developer just had no way of predicting when the overnight process would switch from production to the backup system.
So the developer took a chance and booked the first flight out of the country for the next morning. Then, before leaving work that night, the developer manually forced the system to process from the backup process overnight.
It was the almost perfect heist. Almost. Police arrested the developer at the airport just before boarding the plane.
Many years ago, I was working at a financial institute that processed several millions in transactions every night. Like many institutes, it relied on a (t)rusty mainframe to crunch through the numbers overnight.
These were the days where business continuity was a relatively simple process. You simply had two of everything. So there were two overnight batch processes to process payments, the primary and a backup.
The backup was only used in emergencies, and there was a process to swap systems to use the backup if need be.
It so happened that there was a developer who had grown tired of working and decided it would be a good idea to plot a heist and retire.
The plan was relatively simple. To introduce an extra payment instruction of several million to be transferred to an offshore personal account.
All that was needed was a few lines of code inserted into the overnight batch process to make it all happen.
However, the slight snag was that it wasn't very easy to make any changes to the production system. It was closely monitored, and all changes were subject to strict scrutiny and several layers of approval. Any changes would have raised many questions, ones for which there were no good answers. But the devilishly-minded developer had other plans. The backup batch job wasn't subject to the same rigour. So, the developer figured that if they inserted the code into the backup system it could go undetected.
As the developer anticipated, the commands were successfully inserted into the backup process without raising any alarm bells. Now, all the developer needed to do was to wait for the production system to hit an issue and for processing to take place through the backup system.
This presented a problem though. Once the payment instruction had been executed, sending millions into their offshore account, the developer would need to get out of the country quickly before the payment discrepancy was discovered.
The plan was relatively simple, take a flight to a country that had a non-extradition treaty. Second was to extract all of the money out and place into several other accounts to limit any chances of payment being reversed and to make tracking difficult.
Everything was set and ready to go. The developer just had no way of predicting when the overnight process would switch from production to the backup system.
So the developer took a chance and booked the first flight out of the country for the next morning. Then, before leaving work that night, the developer manually forced the system to process from the backup process overnight.
It was the almost perfect heist. Almost. Police arrested the developer at the airport just before boarding the plane.
 Our manager was a nice guy. One of those people who cared about his team, but was perceived as being too soft to hang with the senior managers of the company.
Several weeks after the incident he presented the timeline of events and findings to his senior management on the attempted heist. Everyone was rather pleased at the outcome and one executive piped up about how, "we were lucky to catch the developer."
It was at that moment that our manager displayed an assertive trait that no-one in the team thought he possessed.
Luck? Do you mean that we were lucky to have extensive monitoring controls on the production system? Or that we were lucky to automatically raise an incident whenever an overnight job switched to the backup system. Perhaps it was luck that we captured all administrator level access to highlight any unauthorised changes. Or that it was by pure luck that we had existing relationships with law enforcement who could arrest our suspect within a few hours. If that's what you mean by luck, then yes, absolutely, were very lucky.
Good securit
Our manager was a nice guy. One of those people who cared about his team, but was perceived as being too soft to hang with the senior managers of the company.
Several weeks after the incident he presented the timeline of events and findings to his senior management on the attempted heist. Everyone was rather pleased at the outcome and one executive piped up about how, "we were lucky to catch the developer."
It was at that moment that our manager displayed an assertive trait that no-one in the team thought he possessed.
Luck? Do you mean that we were lucky to have extensive monitoring controls on the production system? Or that we were lucky to automatically raise an incident whenever an overnight job switched to the backup system. Perhaps it was luck that we captured all administrator level access to highlight any unauthorised changes. Or that it was by pure luck that we had existing relationships with law enforcement who could arrest our suspect within a few hours. If that's what you mean by luck, then yes, absolutely, were very lucky.
Good securit |
Wannacry | |||
| 2017-05-25 12:06:16 | The Impact of WannaCry on the Ransomware Conversation (lien direct) | By this point, we've all heard about the major ransomware attack that impacted an estimated 200,000 computers across 150 countries earlier this month. A malware variant dubbed WannaCry made its way into network infrastructure globally, encrypting data and demanding a ransom of $300 USD per infected computer. | Wannacry | |||
| 2017-05-25 11:15:58 | WannaCry Hits Russian Postal Service, Exposes Wider Security Shortcomings (lien direct) | The ISBuzz Post: This Post WannaCry Hits Russian Postal Service, Exposes Wider Security Shortcomings | Wannacry | |||
| 2017-05-25 08:36:59 | Yup, the Android app store is full of useless, unwanted anti-WannaCry apps (lien direct) |  Apps claiming to protect Android users against WannaCry ransomware are popping up on Google Play, but all of them are a bunch of hogwash.
David Bisson reports. Apps claiming to protect Android users against WannaCry ransomware are popping up on Google Play, but all of them are a bunch of hogwash.
David Bisson reports.
|
Wannacry | |||
| 2017-05-25 05:32:25 | Adylkuzz: WannaCry\'s Older and More Devious Cousin (lien direct) | You might be immune to infection by WannaCry because you've already been infected by Adylkuzz. | Wannacry | |||
| 2017-05-25 05:12:51 | Wanna Cry Again? NSA\'s Windows \'EsteemAudit\' RDP Exploit Remains Unpatched (lien direct) | Brace yourselves for a possible 'second wave' of massive global cyber attack, as SMB (Server Message Block) was not the only network protocol whose zero-day exploits created by NSA were exposed in the Shadow Brokers dump last month.
Although Microsoft released patches for SMB flaws for supported versions in March and unsupported versions immediately after the outbreak of the WannaCry
|
Wannacry | |||
| 2017-05-25 01:15:15 | WannaCry Ransomware Attacks: Hard Lessons For 200,000 Victims (lien direct) | The ISBuzz Post: This Post WannaCry Ransomware Attacks: Hard Lessons For 200,000 Victims | Wannacry | |||
| 2017-05-24 20:33:45 | New Jaff Ransomware Variant Emerges (lien direct) | Although it dominated headlines over the past couple of weeks, WannaCry wasn't the only ransomware family running rampant. Another active threat was Jaff, a ransomware family that emerged just days before the WannaCry outbreak. | Wannacry | |||
| 2017-05-24 16:18:11 | Tech Support Scammers Are Exploiting Mass Hysteria Surrounding WannaCry (lien direct) | As everyone expected, scammers are attempting to cash in on the mass hysteria currently surrounding the WannaCry ransomware outbreak, a mass-infection took place over the weekend of May 12 and 14, and whose effects we still feel today. [...] | Wannacry | |||
| 2017-05-24 15:30:51 | WannaCryptor, aka WannaCry interview with Stephen Cobb and Marc Saltzman (lien direct) | Stephen Cobb, a senior security researcher at ESET, talks about one of the biggest cyberattacks of 2017 – WannaCryptor, aka WannaCry with radio and TV personality Marc Saltzman. | Wannacry | |||
| 2017-05-24 12:00:36 | Victims Lost US$1B to Ransomware (lien direct) | Over the course of 2016, ransomware operators trailed their sights on bigger targets-companies and organizations, both large and small-and raked in US$1 billion for their efforts. Even before WannaCry reared its ugly head, companies and individuals worldwide have already been suffering the threat's dire consequences-all documented in our report, “Ransomware: Past, Present, and Future.†After just one year, we saw a staggering 752% increase in the number of ransomware families. Post from: Trendlabs Security Intelligence Blog - by Trend Micro Victims Lost US$1B to Ransomware | Wannacry | |||
| 2017-05-24 11:11:11 | Stopping Threats in Their Tracks With Proactive Monitoring (lien direct) | An effective response to an advanced threat such as WannaCry can be broken down into two phases: vulnerability management and proactive monitoring. | Wannacry | |||
| 2017-05-24 09:05:00 | WannaCry Shows World the Need for Endpoint Security (lien direct) | Ransomware attacks will continue to become more sophisticated and effective as the year goes on. It is now imperative that organizations prepare their networks and devices for a ransomware attack. | Wannacry | |||
| 2017-05-24 00:05:29 | Jaff ransomware gets a makeover, (Wed, May 24th) (lien direct) | Introduction Since 2017-05-11, a new ransomware named Jaff has been distributed through malicious spam (malspam) from the Necurs botnet. This malspam uses PDF attachments with embedded Word documents containing malicious macros. border-width:2px" /> Shown above: Flow chart for this infection chain. Prior to Jaff, weve seen waves of malspam using the same PDF attachment/embedded Word doc scheme to push Locky ransomware. Prior to that, this type of malspam was pushing Dridex. With all the recent news about WannaCry ransomware, people might forget Jaff is an ongoing threat. Worse yet, some people might not know about it at all since its debut about 2 weeks ago. Jaff has already gotten a makeover, so an infected host looks noticeably different now. With that in mind, todays diary reviews a wave of malspam pushing Jaff ransomware from Tuesday 2017-05-23. The emails This specific wave of malspam used a fake invoice theme. It started on Tuesday 2017-05-23 as early as 13:22 UTC and lasted until sometime after 20:00 UTC. I collected 20 emails for today border-width:2px" /> Shown above: border-width:2px" /> Shown above: border-width:2px" /> Shown above: Screenshot from one of the emails. As stated earlier, these emails all have PDF attachments, and each one contains an embedded Word document. border-width:2px" /> Shown above: border-width:2px" /> Shown above: The embedded Word document with malicious macros. The traffic Follow the entire infection chain, and youll see minimal network traffic compared to other types of malware. The Word macros generate an initial URL to download an encoded Jaff binary, then we see one other URL for post-infection callback from an infected host. The initial HTTP request for Jaff returns an encoded binary thats been XORed with the ASCII string I6cqcYo7wQ. Post-infection traffic merely returns the string Created border-width:2px" /> Shown above: border-width:2px" /> Shown above: border-width:2px" /> Shown above: border-width:2px" /> Shown above: Alerts on the traffic using Security Onion with Suricata and the EmergingThreats Open ruleset. The infected Windows host The encoded binary from this wave of malspam was stored to the users AppData\Local\Temp directory as lodockap8. Then it was decoded and stored as levinsky8.exe in the same directory. border-width:2px" /> Shown above: The users AppData\Local\Temp directory from an infected host on 2017-05-23. On Tuesday 2017-05-23, Jaff ransomware had a makeover. border-width:2px" /> Shown above: border-width:2px" /> Shown above: Desktop of a Windows host infected with a Jaff ransomware sample from 2017-05-23. Encrypted files had been previously appended with the .jaff file extension. On Tuesday 2017-05 | Wannacry | |||
| 2017-05-23 17:47:25 | La France, 5ème pays le plus touché par Wannacry (lien direct) | Malwarebytes dévoile un ranking des pays les plus touchés par la cyberattaque mondiale de mai. La France,... Cet article La France, 5ème pays le plus touché par Wannacry est diffusé par Data Security Breach. | Wannacry | |||
| 2017-05-23 17:41:02 | WannaCry un coup de semonce mondial à moindre frais pour les RSSI ? (lien direct) | RSSI versus pirate ! La propagation mondiale d’une rapidité sans précédent de WannaCry et de ses variantes... Cet article WannaCry un coup de semonce mondial à moindre frais pour les RSSI ? est diffusé par Data Security Breach. | Wannacry | |||
| 2017-05-23 16:00:43 | XData ransomware making rounds amid global WannaCryptor scare (lien direct) | A week after the global outbreak of WannaCryptor, also known as WannaCry, another ransomware, known as XData, has been making rounds. | Wannacry | |||
| 2017-05-23 15:37:42 | Automating Security Operations: What It Takes to Defend Against Something Like WannaCry (lien direct) | A major challenge facing security vendors today is that most solutions and products are developed based on knowledge of previous threats that already exist. This makes many security solutions reactive by their very design, which is not a tenable strategy for facing the volume of new attacks and strategies arising today. This arms race of identifying new threats, then reacting has been the primary strategy since the dawn of malware: A new virus is identified and then security vendors write the antivirus signature to block it; a polymorphic virus... | Wannacry | |||
| 2017-05-23 14:59:46 | What did we Learn from WannaCry? - Oh Wait, We Already Knew That!, (Tue, May 23rd) (lien direct) | In the aftermath of last weeks excitement over the WannaCry malware, Ive had a lot of lessons learned meetings with clients. The results are exactly what youd expect, but in some cases came as a surprise to the organizations we met with. There was a whole outcry about not victim shaming during and after this outbreak, and I get that, but in most cases infections were process failures that the IT group didnt know they had, these lessons learned sessions have contributed to improving the situation at many organizations. The short list is below - affected companies had one or more of the issues below: 1/ Patch Plain and simple, when vendor patches come out, apply them. In a lot of cases, Patch Tuesday means Reboot Wednesday for a lot of organizations, or worst case Reboot Saturday. If you dont have a test the patches process, then in a lot of cases simply waiting a day or two (to let all the early birds test them for you) will do the job. If you do have a test process, in todays world it truly needs to take 7 days or less. There are some hosts that you wont be patching. The million dollar MRI machine, the IV pump or the 20 ton punch press in the factory for instance. But you know about those, and youve segmented them away (in an appropriate way) from the internet and your production assets. This outbreak wasnt about those assets, what got hammered by Wannacry was the actual workstations and servers, the hospital stations in admitting and emergency room, the tablet that the nurse enters your stats into and so on. Normal user workstations that either werent patched, or were still running Windows XP. That being said, there are always some hosts that can be patched, but cant be patched regularly. The host thats running active military operations for instance, or the host thats running the callcenter for flood/rescue operations, e-health or suicide hotline. But you cant give just up on those - in most cases there is redundancy in place so that you can update half of those clusters at a time. If there isnt, you do still need to somehow get them updated on a regular schedule. Lesson learned? If your patch cycle is longer than a week, in todays world you need to revisit your process and somehow shorten it up. Document your exceptions, put something in to mitigate that risk (network segmentation is a common one), and get Sr Management to sign off on the risk and the mitigation. 2/ Unknown Assets are waiting to Ambush You A factor in this last attack were hosts that werent in ITs inventory. In my group of clients, what this meant was hosts controlling billboards or TVs running ads in customer service areas (the menu board at the coffee shop, the screen telling you about retirement funds where you wait in line at the bank and so on). If this had been a linux worm, wed be talking about projectors, TVs and access points today. One and all, I pointed those folks back to the Critical Controls list (https://www.cisecurity.org/controls/ ). In plain english, the first item is know whats on your network and the second item is know what is running on whats on your network. If you dont have a complete picture of these two, you will always be exposed to whatever new malware (or old malware) that tests the locks at your organization. 3/ Watch the News. .... And I dont mean the news on TV. Your vendors (in this case Microsoft) have news feeds, and there are a ton of security-related news sites, podcasts and feeds (this site is one of those, our StormCast podcast is another). Folks that watch the news knew about this issue starting back in 2015, when Microsoft started advising us to disable SMB1, then again last year (2016) when Microsoft posted their Were Pleading with you, PLEASE disable SMB1 post. We knew specifically about the vulnerabilities used by Wannacry in January when the Shadowbrokers dump happened, we knew again when the patches were released in March, and we knew (again, much mor | Guideline | Wannacry | ||
| 2017-05-23 13:00:00 | Are We Learning the Right Lessons from WannaCry? (lien direct) |
 Encouraging organizations to follow the usual security best practices didn’t prevent the spread of WannaCry. Let’s acknowledge that and focus on new ideas that will.
In the aftermath of the WannaCry ransomware outbreak, a familiar pattern is beginning to play itself out. Now that we all know the general details behind how WannaCry infections were initiated and spread (by exploiting a known vulnerability that Microsoft patched back in March), initial alarm and concern is gradually giving way to an expected reaction from the security community.
“How could they not have patched yet?” “Why are they still running Windows XP?” “Who leaves port 445 open to the Internet?”
Before we go blaming the estimated 300,000 victims for bringing this attack on themselves, and before we pigeonhole the cause of the attack as simple negligence, we should consider that overly simplistic assessments may be part of the reason these attacks appear to be so frustratingly “inevitable”.
The real revelation of the WannaCry outbreak isn’t that there are a staggering number of outdated and unsecured systems out there, it’s that anyone believes that making the same old pleas and showering victims with blame will change anything.
If you read most recommendations from security vendors and experts in response to this attack out loud, you’ll sound like a broken record: Patch regularly. Don’t use outdated systems. Update your antivirus. Tell users not to click on things. Run backups.
These are all good pieces of advice. So are “Get more exercise,” “Avoid sweets,” and “Obey the speed limit.” But when the rubber meets the road, as it has in the WannaCry outbreak, they sound like security industry platitudes, not solutions. At best, they’re proved difficult to follow in the face of competing business pressures. At worst, they fail to address the real issues that leave companies vulnerable as we watch for repeat and copycat attacks undoubtedly coming down the pike.
So, rather than repeat these same old recommendations and throw up our hands when no one seems to listen, let’s break them down, describe where they fall short, and suggest alternatives that will help companies to take more productive steps toward protecting themselves.
Updating the 5 Most Common Recommendations for Protecting Your Company from the Next WannaCry
1) Patching
Current advice: “Keep all systems up to date with all patches.”
Better advice: “Treat security patches seriously.”
WannaCry was able to spread far and wide by utilizing an exploit called ETERNALBLUE, one of the NSA hacking tools leaked by a group called the Shadow Brokers in April. Microsoft released a patch addressing the vulnerability that ETERNALBLUE targets in March (MS17-010). Following the WannaCry outbreak, it also took the unusual step of rolling out additional patches for older versions of Windows. With
Encouraging organizations to follow the usual security best practices didn’t prevent the spread of WannaCry. Let’s acknowledge that and focus on new ideas that will.
In the aftermath of the WannaCry ransomware outbreak, a familiar pattern is beginning to play itself out. Now that we all know the general details behind how WannaCry infections were initiated and spread (by exploiting a known vulnerability that Microsoft patched back in March), initial alarm and concern is gradually giving way to an expected reaction from the security community.
“How could they not have patched yet?” “Why are they still running Windows XP?” “Who leaves port 445 open to the Internet?”
Before we go blaming the estimated 300,000 victims for bringing this attack on themselves, and before we pigeonhole the cause of the attack as simple negligence, we should consider that overly simplistic assessments may be part of the reason these attacks appear to be so frustratingly “inevitable”.
The real revelation of the WannaCry outbreak isn’t that there are a staggering number of outdated and unsecured systems out there, it’s that anyone believes that making the same old pleas and showering victims with blame will change anything.
If you read most recommendations from security vendors and experts in response to this attack out loud, you’ll sound like a broken record: Patch regularly. Don’t use outdated systems. Update your antivirus. Tell users not to click on things. Run backups.
These are all good pieces of advice. So are “Get more exercise,” “Avoid sweets,” and “Obey the speed limit.” But when the rubber meets the road, as it has in the WannaCry outbreak, they sound like security industry platitudes, not solutions. At best, they’re proved difficult to follow in the face of competing business pressures. At worst, they fail to address the real issues that leave companies vulnerable as we watch for repeat and copycat attacks undoubtedly coming down the pike.
So, rather than repeat these same old recommendations and throw up our hands when no one seems to listen, let’s break them down, describe where they fall short, and suggest alternatives that will help companies to take more productive steps toward protecting themselves.
Updating the 5 Most Common Recommendations for Protecting Your Company from the Next WannaCry
1) Patching
Current advice: “Keep all systems up to date with all patches.”
Better advice: “Treat security patches seriously.”
WannaCry was able to spread far and wide by utilizing an exploit called ETERNALBLUE, one of the NSA hacking tools leaked by a group called the Shadow Brokers in April. Microsoft released a patch addressing the vulnerability that ETERNALBLUE targets in March (MS17-010). Following the WannaCry outbreak, it also took the unusual step of rolling out additional patches for older versions of Windows. With |
Wannacry | |||
| 2017-05-23 12:30:00 | Profil de logiciel malveillant Wannacry WannaCry Malware Profile (lien direct) |
MALWARE WANNACRY (également connu sous le nom de WCRY ou WANACRYPTOR) est un ransomware d'auto-propagation (semblable à des vers) qui se propage dans les réseaux internes et sur Internet public en exploitant une vulnérabilité dans le bloc de messages du serveur de Microsoft \\ (SMB)Protocole, MS17-010.Le wannacry se compose de deux composants distincts, unqui fournit des fonctionnalités de ransomware et un composant utilisé pour la propagation, qui contient des fonctionnalités pour permettre les capacités d'exploitation des SMB.
Le malware exploite un exploit, nommé «EternalBlue», publié par les Shadow Brokers le 14 avril 2017.
le
WannaCry (also known as WCry or WanaCryptor) malware is a self-propagating (worm-like) ransomware that spreads through internal networks and over the public internet by exploiting a vulnerability in Microsoft\'s Server Message Block (SMB) protocol, MS17-010. The WannaCry malware consists of two distinct components, one that provides ransomware functionality and a component used for propagation, which contains functionality to enable SMB exploitation capabilities. The malware leverages an exploit, codenamed “EternalBlue”, that was released by the Shadow Brokers on April 14, 2017. The |
Ransomware Malware Vulnerability Technical | Wannacry | ★★★★ | |
| 2017-05-23 11:11:31 | WannaCry \'Highly Likely\' Work of North Korean-linked Hackers, Symantec Says (lien direct) | North Korea-linked Lazarus Hacking Group is "Highly Likely" to be Responsible for the Global "WannaCry" Ransomware Attack, Symantec Says | Wannacry APT 38 | |||
| 2017-05-23 11:08:47 | WhiteOut : code pirate connu dans WannaCry made in Corée du Nord ? (lien direct) | Un bout de code informatique utilisé dans l’outil d’espionnage WhiteOut aurait été retrouvé dans le logiciel malveillant WannaCry. Une signature proche de la Corée du Nord ! La société FireEye a trouvé que le malware de WannaCry partageait un code unique avec des logiciels malveillants ... Cet article WhiteOut : code pirate connu dans WannaCry made in Corée du Nord ? est apparu en premier sur ZATAZ. | Wannacry | |||
| 2017-05-23 10:35:15 | WannaCry connection to North Korea hacking group \'compelling\' (lien direct) | WannaCry, the ransomware that spread through the UK's National Health Service and companies around the world, shows “compelling evidence†of a link to North Korean hacking group Lazarus, according to a new report by Symantec.  The cyber security company believes there is a “close connection†to Lazarus, the group behind the cyber attacks on Sony ... | Wannacry APT 38 | ★★ | ||
| 2017-05-23 10:30:10 | Warning after WannaCry sets off fake BT phishing attack (lien direct) | It's a sad fact that we end up seeing warnings about warnings in the aftermath of a major cybersecurity event |
Wannacry | |||
| 2017-05-23 09:43:21 | WannaCry? Not really. A report from the 11th Eskenzi PR IT Analyst and CISO Forum (lien direct) | May 16th and 17th 2017 saw Eskenzi PR stage its 11th 2-day IT Security Analyst Forum, as usual, in London. The morning of the second day (which was a Wednesday) was the customary CISO (chief information security officer) roundtable. A coming together of 20 or so IT security leaders from blue chip UK enterprises and ... | Guideline | Wannacry | ||
| 2017-05-23 09:42:30 | WannaCry partage un code unique avec des logiciels malveillants WHITEOUT (lien direct) |  D'après les experts en sécurité du cabinet FireEye, le malware de WannaCry partagerait un code unique avec des logiciels malveillants WHITEOUT, précédemment attribués à des acteurs suspects en Corée du Nord. D'après les experts en sécurité du cabinet FireEye, le malware de WannaCry partagerait un code unique avec des logiciels malveillants WHITEOUT, précédemment attribués à des acteurs suspects en Corée du Nord. |
Wannacry | |||
| 2017-05-23 09:30:02 | WannaCry Successor Is New \'Doomsday\' SMB Worm That Uses 7 NSA Hacking Tools (lien direct) | The ISBuzz Post: This Post WannaCry Successor Is New ‘Doomsday’ SMB Worm That Uses 7 NSA Hacking Tools | Wannacry | |||
| 2017-05-23 09:00:39 | Cisco Ramps up Security for Things with IOT Threat Defense (lien direct) | In-brief: Networking giant Cisco Systems said on Tuesday that a new package of products and services, dubbed IoT Threat Defense. Networking giant Cisco Systems said on Tuesday that a new package of products and services, dubbed IoT Threat Defense that it says will help segregate critical systems used for medical care and in critical...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/330714696/0/thesecurityledger -->»Related StoriesReport warns of Robot Hacks, TamperingFDA: St. Judes knew about Device Flaws 2 Years Before Muddy Waters ReportThe WannaCry Missing: Federal Systems, Consumers | Wannacry | |||
| 2017-05-23 08:57:02 | WannaCry attack \'linked\' to North Korea hacking group (lien direct) | Tools that helped WannaCry spread were also used in attacks linked to North Korea, says security firm. | Wannacry | |||
| 2017-05-23 08:30:40 | WannaCry : de nouveaux indices pointent vers la Corée du Nord (lien direct) | Une société de sécurité informatique a enquêté sur l'attaque WannaCry. Elle a détecté plusieurs indices mettant en cause le groupe de hackers Lazarus, lié à la Corée du Nord.  |
Wannacry APT 38 | |||
| 2017-05-23 06:47:20 | Et si WannaCry, le terrible ransomware, n\'était qu\'un accident de laboratoire ? (lien direct) | D'après un chercheur en sécurité, WannaCry était encore en phase de développement et s'est probablement échappé de façon involontaire et incontrôlée. Une thèse qui serait soutenue par plusieurs aspects techniques de cette attaque.  |
Wannacry | |||
| 2017-05-23 06:35:27 | 386 WannaCry ransomware samples discovered in the wild (lien direct) | The destructive ransomware has caused chaos and it may be that cyberattackers want to continue capitalizing on the malware. | Wannacry | |||
| 2017-05-23 06:23:20 | US politicians think companies should be allowed to \'hack back\' after WannaCry (lien direct) |  ACDC bill would give green light for firms to launch counterattacks against hackers. But is that really a good idea? ACDC bill would give green light for firms to launch counterattacks against hackers. But is that really a good idea?
|
Wannacry | |||
| 2017-05-23 04:21:54 | EternalRocks worm combines seven leaked NSA attack tools (lien direct) | Hard on the heels of the WannaCry ransomware attacks, a researcher has found a worm that combines four NSA exploits and associated attack tools, including EternalBlue used by WannaCry | Wannacry | |||
| 2017-05-22 22:19:59 | WannaCry: Ransomware attacks show strong links to Lazarus group (lien direct) | Similarities in code and infrastructure indicate close connection to group that was linked to Sony Pictures and Bangladesh Bank attacks | Wannacry APT 38 | |||
| 2017-05-22 18:04:42 | Video: How to survive the global cyberwar (lien direct) | Dr. Kenneth Geers, senior research scientist at Comodo and NATO Cyber Center Ambassador, explains #WannaCry and the steps business should take to protect critical assets during the next cyberattack. | Wannacry | |||
| 2017-05-22 17:54:54 | News in brief: Bitcoin price bubbles up; Uber uses AI to boost its take; WannaCry \'hero\' censures tabloids (lien direct) | Your daily round-up of some of the other stories in the news |
Wannacry Uber | |||
| 2017-05-22 17:05:29 | EternalRocks Worm Spreads Seven NSA SMB Exploits (lien direct) | A worm called EternalRocks has been spreading seven Windows SMB exploits leaked by the ShadowBrokers, including EternalBlue, which was used to spread WannaCry. | Wannacry | |||
| 2017-05-22 16:31:10 | Health Care and Ransomware: A Marriage Made in Hades (lien direct) | A widespread ransomware attack such as WannaCry can cause problems for any business. For a health care organization, it can cause an utter catastrophe. | Wannacry | |||
| 2017-05-22 15:52:41 | After WannaCry, EternalRocks digs deeper into the NSA\'s exploit toolbox (lien direct) | WannaCry may be behind us, but fears that the crooks might create new malware from the NSA's stash of exploits seem to be coming true |
Wannacry | |||
| 2017-05-22 14:10:17 | North Korea Denies Involvement in WannaCry Ransomware Outbreak (lien direct) | On Friday, North Korea denied allegations that it was somehow responsible for the WannaCry ransomware outbreak that affected over 240,000 computers in nearly 200 countries across the globe. [...] | Wannacry | |||
| 2017-05-22 14:08:25 | Meet the 22-year-old saviour who stopped the WannaCry ransomware attack (lien direct) | Marcus Hutchins: The 'Accidental Hero' Who Saved The World From The WannaCry Ransomware The world last week witnessed one of the most widespread cyberattacks in history that brought more than 2,30,000 computers running Windows operating system in 150 countries to a standstill. The biggest unprecedented ransomware attack could have got even worse had it not [...] | Wannacry | |||
| 2017-05-22 13:59:59 | A week in security (May 15 – May 21) (lien direct) |
 A compilation of notable security news and blog posts from the 15th of May to the 21st. We covered WannaCry, Privacy Awareness week, and what to do when you suspect stolen personal data.
Categories:
Security world
Week in security
Tags: biohacketernalrocksprivacy awareness weekssd vulnerabilitystolen dataWannaCryweekly blog roundupwikileaks
(Read more...)
A compilation of notable security news and blog posts from the 15th of May to the 21st. We covered WannaCry, Privacy Awareness week, and what to do when you suspect stolen personal data.
Categories:
Security world
Week in security
Tags: biohacketernalrocksprivacy awareness weekssd vulnerabilitystolen dataWannaCryweekly blog roundupwikileaks
(Read more...)
|
Wannacry | |||
| 2017-05-22 13:40:31 | North Korea denies link to WannaCry ransomware attack (lien direct) |  Some security researchers have found similarities between WannaCry and malware previously written by a hacking group linked to North Korea.
Read more in my article on the Hot for Security blog. Some security researchers have found similarities between WannaCry and malware previously written by a hacking group linked to North Korea.
Read more in my article on the Hot for Security blog.
|
Wannacry |
To see everything:
Our RSS (filtrered)
