What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2023-11-28 11:00:00 | Pour le manque de cyber ongle, le royaume est tombé For want of a cyber nail the kingdom fell (lien direct) |
An old proverb, dating to at least the 1360’s, states: "For want of a nail, the shoe was lost, for want of a shoe, the horse was lost, for want of a horse, the rider was lost, for want of a rider, the battle was lost, for want of a battle, the kingdom was lost, and all for the want of a horseshoe nail," When published in Ben Franklin’s Poor Richard’s Almanack in 1768, it was preceded by the cautionary words: “a little neglect may breed great mischief”. This simple proverb and added comment serve as emblematic examples of how seemingly inconsequential missteps or neglect can lead to sweeping, irreversible, catastrophic losses. The cascade of events resonates strongly within the increasingly complex domain of cybersecurity, in which the omission of even the most elementary precaution can result in a spiraling series of calamities. Indeed, the realm of cybersecurity is replete with elements that bear striking resemblance to the nail, shoe, horse, and rider in this proverb. Consider, for example, the ubiquitous and elementary software patch that may be considered the proverbial digital "nail." In isolation, this patch might seem trivial, but its role becomes crucial when viewed within the broader network of security measures. The 2017 WannaCry ransomware attack demonstrates the significance of such patches; an unpatched vulnerability in Microsoft Windows allowed the malware to infiltrate hundreds of thousands of computers across the globe. It wasn\'t just a single machine that was compromised due to this overlooked \'nail,\' but entire networks, echoing how a lost shoe leads to a lost horse in the proverb. This analogy further extends to the human elements of cybersecurity. Personnel tasked with maintaining an organization\'s cyber hygiene play the role of the "rider" in our metaphorical tale. However, the rider is only as effective as the horse they ride; likewise, even the most skilled IT professional cannot secure a network if the basic building blocks—the patches, firewalls, and antivirus software—resemble missing nails and shoes. Numerous reports and studies have indicated that human error constitutes one of the most common causes of data breaches, often acting as the \'rider\' who loses the \'battle\'. Once the \'battle\' of securing a particular network or system is lost, the ramifications can extend much further, jeopardizing the broader \'kingdom\' of an entire organization or, in more extreme cases, critical national infrastructure. One glaring example that serves as a cautionary tale is the Equifax data breach of 2017, wherein a failure to address a known vulnerability resulted in the personal data of 147 million Americans being compromised. Much like how the absence of a single rider can tip the scales of an entire battle, this singular oversight led to repercussions that went far beyond just the digital boundaries of Equifax, affecting millions of individuals and shaking trust in the security of financial systems. | Ransomware Data Breach Malware Vulnerability | Wannacry Wannacry Equifax Equifax | ★★ | |
| 2023-10-26 13:08:32 | Ransomware one year after WannaCry: attack vectors still commonly exploited by attackers (lien direct) | This article discusses some of the most common infection vectors and how the Darktrace Enterprise Immune System can assist security teams in catching ransomware threats.
This article discusses some of the most common infection vectors and how the Darktrace Enterprise Immune System can assist security teams in catching ransomware threats. |
Ransomware | Wannacry | ★★ | |
| 2023-08-08 15:00:00 | Opération des ransomwares d'origine vietnamienne imite les traits de Wannacry Vietnamese-Origin Ransomware Operation Mimics WannaCry Traits (lien direct) |
Cisco Talos a déclaré que ce qui distingue cette opération est la nouvelle approche pour fournir des notes de rançon
Cisco Talos said what sets this operation apart is the novel approach to delivering ransom notes |
Ransomware | Wannacry Wannacry | ★★ | |
| 2023-06-15 18:10:00 | Les pirates infectent les joueurs russophones avec de faux ransomwares de Wannacry Hackers infect Russian-speaking gamers with fake WannaCry ransomware (lien direct) |
 Les chercheurs ont découvert une campagne de phishing ciblant les joueurs russophones de Enrôlé, un tireur à la première personne multijoueur.Les pirates ont utilisé un faux site Web qui ressemble étroitement à la page Web officielle enrôlée pour distribuer des ransomwares, selon un rapport publié cette semaine par la société de cybersécurité Cyble.Alors que les chercheurs n'ont pas attribué cette attaque à un groupe particulier, ils croient que
Les chercheurs ont découvert une campagne de phishing ciblant les joueurs russophones de Enrôlé, un tireur à la première personne multijoueur.Les pirates ont utilisé un faux site Web qui ressemble étroitement à la page Web officielle enrôlée pour distribuer des ransomwares, selon un rapport publié cette semaine par la société de cybersécurité Cyble.Alors que les chercheurs n'ont pas attribué cette attaque à un groupe particulier, ils croient que
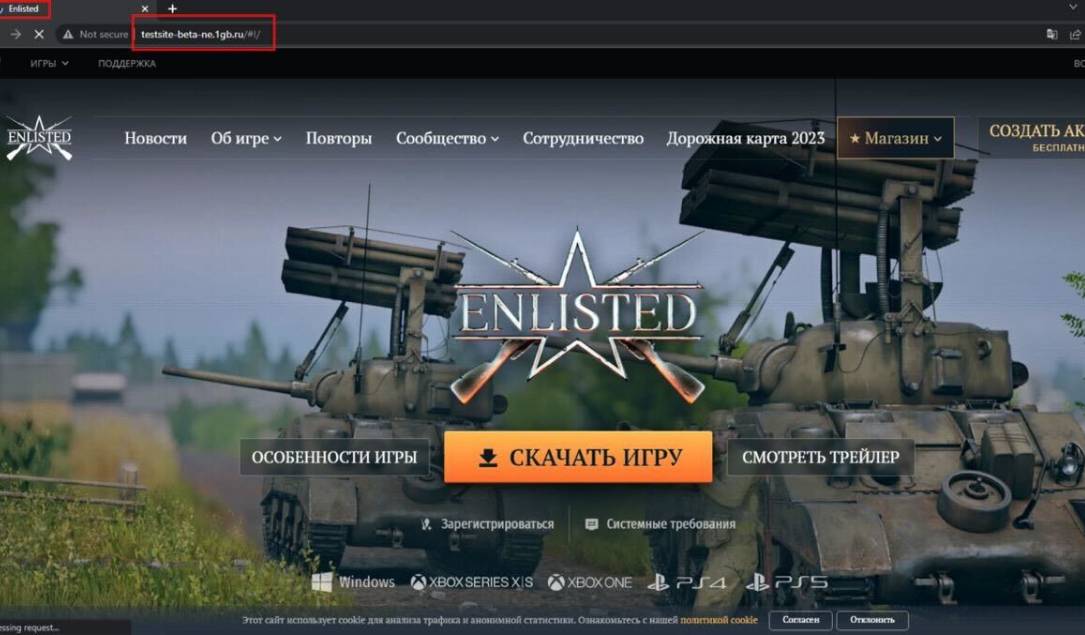 Researchers have uncovered a phishing campaign targeting Russian-speaking players of Enlisted, a multiplayer first-person shooter. The hackers used a fake website that closely resembles the official Enlisted webpage to distribute ransomware, according to a report published this week by cybersecurity firm Cyble. While researchers haven\'t attributed this attack to any particular group, they believe that
Researchers have uncovered a phishing campaign targeting Russian-speaking players of Enlisted, a multiplayer first-person shooter. The hackers used a fake website that closely resembles the official Enlisted webpage to distribute ransomware, according to a report published this week by cybersecurity firm Cyble. While researchers haven\'t attributed this attack to any particular group, they believe that |
Ransomware | Wannacry Wannacry | ★★ | |
| 2023-05-15 13:32:45 | Six ans après Wannacry: Pourquoi le ransomware est toujours un problème Sechs Jahre nach WannaCry: Warum Ransomware nach wie vor ein Problem ist (lien direct) |
Le 12 mai, non seulement la "Journée anti-ransomware" internationale, mais aussi le sixième anniversaire du Ber & uuml;. On peut constater que la réputation d'une entreprise est arrêtée, la réputation d'une entreprise est donnée et Des conséquences réelles surviennent. & ouml;, mais les attaques de ransomware représentent toujours tous les types et grands;
-
malware
/ /
ransomware ,
cybersecurite_home_droite
Der 12. Mai kennzeichnet nicht nur den internationalen „Anti-Ransomware-Tag", sondern auch den sechsten Jahrestag der berüchtigten und verheerenden WannaCry-Angriffe. Auch heute noch stellt Ransomware eine ständige Bedrohung für Organisationen dar. Sie kann dazu führen, dass Geschäftsabläufe gestoppt werden, der Ruf eines Unternehmens geschädigt wird und reale Folgen entstehen. Öffentlichkeitswirksame Angriffe auf z.B. Krankenhäuser und Kommunen sind bei der Bevölkerung zumeist besser bekannt, doch Ransomware-Attacken stellen nach wie vor für alle Arten und Größen von Unternehmen eine äußerst ernstzunehmende Bedrohung dar. - Malware / Ransomware, cybersecurite_home_droite |
Ransomware | Wannacry | ★★ | |
| 2023-03-22 12:30:00 | Le Royaume-Uni émet une stratégie pour protéger les services de santé nationaux contre les cyberattaques [UK issues strategy to protect National Health Service from cyberattacks] (lien direct) |
 Le gouvernement britannique a publié mercredi sa nouvelle stratégie de cybersécurité pour le National Health Service, visant à rendre le secteur de la santé du pays \\ «durcie considérablement à la cyberattaque, au plus tard en 2030».La stratégie vient dans le sillage de la [Wannacry] (https://www.theguardian.com/technology/2017/jun/16/wannacry-ransomware-attack-linked-north-korea-lazarus-group) Ransomware Attack en 2017, parallèlement à une attaque criminelle contre le fournisseur de logiciels [Advanced] (https://www.bbc.co.uk/news/technology-62725363) l'année dernière,
Le gouvernement britannique a publié mercredi sa nouvelle stratégie de cybersécurité pour le National Health Service, visant à rendre le secteur de la santé du pays \\ «durcie considérablement à la cyberattaque, au plus tard en 2030».La stratégie vient dans le sillage de la [Wannacry] (https://www.theguardian.com/technology/2017/jun/16/wannacry-ransomware-attack-linked-north-korea-lazarus-group) Ransomware Attack en 2017, parallèlement à une attaque criminelle contre le fournisseur de logiciels [Advanced] (https://www.bbc.co.uk/news/technology-62725363) l'année dernière,
 The British government published on Wednesday its new cybersecurity strategy for the National Health Service, aiming to make the country\'s healthcare sector “significantly hardened to cyber attack, no later than 2030.” The strategy comes in the wake of the [WannaCry](https://www.theguardian.com/technology/2017/jun/16/wannacry-ransomware-attack-linked-north-korea-lazarus-group) ransomware attack in 2017, alongside a criminal attack on the software supplier [Advanced](https://www.bbc.co.uk/news/technology-62725363) last year,
The British government published on Wednesday its new cybersecurity strategy for the National Health Service, aiming to make the country\'s healthcare sector “significantly hardened to cyber attack, no later than 2030.” The strategy comes in the wake of the [WannaCry](https://www.theguardian.com/technology/2017/jun/16/wannacry-ransomware-attack-linked-north-korea-lazarus-group) ransomware attack in 2017, alongside a criminal attack on the software supplier [Advanced](https://www.bbc.co.uk/news/technology-62725363) last year, |
Ransomware General Information | Wannacry APT 38 | ★★ | |
| 2022-11-28 14:00:00 | Worms of Wisdom: How WannaCry Shapes Cybersecurity Today (lien direct) | >WannaCry wasn’t a particularly complex or innovative ransomware attack. What made it unique, however, was its rapid spread. Using the EternalBlue exploit, malware could quickly move from device to device, leveraging a flaw in the Microsoft Windows Server Message Block (SMB) protocol. As a result, when the WannaCry “ransomworm” hit networks in 2017, it expanded […] | Ransomware Malware | Wannacry Wannacry | ★★ | |
| 2022-10-31 14:37:01 | Wannacry, the hybrid malware that brought the world to its knees (lien direct) | >Reflecting on the Wannacry ransomware attack, which is the lesson learnt e why most organizations are still ignoring it. In the early afternoon of Friday 12 May 2017, the media broke the news of a global computer security attack carried out through a malicious code capable of encrypting data residing in information systems and demanding […] | Ransomware Malware | Wannacry Wannacry | ★★ | |
| 2022-10-19 17:37:26 | Persistent pests: A taxonomy of computer worms (lien direct) | Many of the most notorious ransomware attacks, including WannaCry and NotPetya, began with a worm. Here's how you can help stop the spread. | Ransomware | NotPetya Wannacry Wannacry | ||
| 2022-10-06 10:00:00 | 7 Biggest Cybersecurity Threats of the 21st Century (lien direct) | This blog was written by an independent guest blogger. The 21st century has seen a dramatic increase in the number and sophistication of cybersecurity threats. Here are the 7 biggest threats that businesses and individuals need to be aware of. Ransomware as a service In the past few years, ransomware has become one of the most popular tools for cybercriminals. Ransomware as a service (RaaS) is a new business model that allows anyone with little to no technical expertise to launch their own ransomware attacks. All they need is to sign up for a RaaS platform and pay a fee (usually a percentage of the ransom they collect). RaaS is a growing threat because it makes it easy for anyone to launch attacks. Cybercriminals can target any organization, no matter its size or resources. And, because RaaS platforms typically take care of all the technical details, ransomware attacks can be launched with little effort. In the past several years, there have been a number of high-profile ransomware attacks that have made headlines. In May 2017, the WannaCry ransomware attack affected more than 200,000 computers in 150 countries. The attack caused billions of dollars in damage and disrupted critical infrastructure, such as hospitals and banks. In December 2017, the NotPetya ransomware attack hit more than 10,000 organizations in over 60 countries. The attack caused billions of dollars in damage and disrupted critical infrastructure, such as hospitals and banks. Ransomware attacks have become more sophisticated and targeted. Cybercriminals are now using RaaS platforms to launch targeted attacks against specific organizations. These attacks are often called "spear phishing" attacks because they use carefully crafted emails to trick people into clicking on malicious links or opening attachments that install ransomware on their computers. Organizations of all sizes need to be aware of the threat of ransomware and take steps to protect themselves. This includes having a robust backup and recovery plan in place in case of an attack. Internet of Things The Internet of Things (IoT) is a network of physical devices, vehicles, home appliances, and other items that are embedded with electronics, software, sensors, and connectivity enabling these objects to connect and exchange data. The IoT is a growing market with more and more devices being connected to the internet every day. However, this also creates new security risks. Because IoT devices are often connected to the internet, they can be hacked and used to launch attacks. In October 2016, a massive Distributed Denial of Service (DDoS) attack was launched against the Dyn DNS service using a network of IoT devices that had been infected with the Mirai malware. The attack caused widespread internet disruptions and took down major websites, such as Twitter and Netflix. The IoT presents a unique challenge for security because there are so many different types of devices that can be connected to the internet. Each type of device has its own security risks and vulnerabilities. And, as the number of IoT devices continues to grow, so do the opportunities for cybercriminals to exploit them. Cloud security The cloud has become an essential part of business for many organizations. It offers a number of advantages, such as flexibility, scalability, and cost savings. However, the cloud also creates new security risks. One of the biggest security risks associated with the cloud is data breaches. Because data is stored remotely on servers, it is more vulnerable to attack. In addition, cloud service providers often have access to customer data, which creates another potential point of entry for hackers. Another security risk associated with the | Ransomware Malware Threat | NotPetya NotPetya Wannacry Wannacry | ||
| 2022-09-08 03:01:00 | How Penetration Testing can help prevent Ransomware Attacks (lien direct) | >It is hard to believe, but ransomware is more than three decades old. While many would think that the ransomware mayhem started with the WannaCry attack of 2017, that is simply the most publicized example. Since then, dozens of ransomware strains have been utilized in a variety of cyberattacks. According to a PhishLabs report, by […]… Read More | Ransomware | Wannacry Wannacry | ||
| 2022-08-24 12:34:00 | WannaCry explained: A perfect ransomware storm (lien direct) | What is WannaCry? WannaCry is a ransomware worm that spread rapidly through across a number of computer networks in May of 2017. After infecting a Windows computer, it encrypts files on the PC's hard drive, making them impossible for users to access, then demands a ransom payment in bitcoin in order to decrypt them.A number of factors made the initial spread of WannaCry particularly noteworthy: it struck a number of important and high-profile systems, including many in Britain's National Health Service; it exploited a Windows vulnerability that was suspected to have been first discovered by the United States National Security Agency; and it was tentatively linked by Symantec and other security researchers to the Lazarus Group, a cybercrime organization that may be connected to the North Korean government.To read this article in full, please click here | Ransomware Vulnerability Medical | Wannacry Wannacry APT 38 | ||
| 2022-07-13 18:44:03 | Internet Searches Reveal Surprisingly Prevalent Ransomware (lien direct) | Two mostly defunct threats - WannaCry and NonPetya - top the list of ransomware searches, but does that mean they are still causing problems? | Ransomware | Wannacry Wannacry | ||
| 2022-07-07 08:14:35 | North Korean State-Sponsored Threat Actors Deploying "MAUI" Ransomware (lien direct) | Today, the United States Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Agency (CISA) and the Department of Treasury released a joint Cybersecurity Advisory on Maui Ransomware, which is attributed to state sponsored activity by the government of North Korea. The Joint CSA provides detailed insight on the various TTPs used by the threat actors behind Maui, which has targeted the Health and Public Health Sector.How Serious of an Issue is This?High. As ransomware activity causes downtime, theft of confidential and personally identifiable information (PII) and other significant impact to operations, it is important to ensure that various security measures are in place, like being up to date with patching vulnerable machines/infrastructure. Also, ensuring employees are trained and up to date on various social engineering attempts and tactics used by threat actors will be a first line of defense against such attacks.What is Maui Ransomware?Maui ransomware is unique in a way that it requires manual execution to start the encryption routine. Maui also features a CLI (command line interface) that is used by the threat actor to target specific files to encrypt. Maui also has the ability to identify previously encrypted files due to customer headers containing the original path of the file.Who are HIDDEN COBRA/LAZARUS/APT38/BeagleBoyz?HIDDEN COBRA also known as Lazarus/APT38/BeagleBoyz has been atributed to the government of North Korea. Also, they have been linked to multiple high-profile, financially-motivated attacks in various parts of the world - some of which have caused massive infrastructure disruptions. Notable attacks include the 2014 attack on a major entertainment company and a 2016 Bangladeshi financial institution heist that almost netted nearly $1 Billion (USD) for the attackers. Had it not been for a misspelling in an instruction that caused a bank to flag and block thirty transactions, HIDDEN COBRA would have pulled off a heist unlike any other. Although HIDDEN COBRA failed in their attempt, they were still able to net around 81 million dollars in total.The most recent notable attack attributed to HIDDEN COBRA was the Wannacry Ransomware attack, which resulted in massive disruption and damage worldwide to numerous organizations, especially those in manufacturing. Various estimates of the impact were in the hundreds of millions of dollars, with some estimates claiming billions. Other verticals which this group has targeted include critical infrastructures, entertainment, finance, healthcare, and telecommunication sectors across multiple countries.Who are the BeagleBoyz?The BeagleBoyz group is a newly identified group that is a subset of activity by the threat actors known as HIDDEN COBRA/LAZARUS/APT 38 and has been observed committing financial crimes, specifically cryptocurrency related thefts. Further information about the BeagleBoyz can be found here.What Operating Systems are Affected?Windows based operating systems are affected.What is the Status of Coverage?Fortinet customers running the latest definitions are protected against Maui with the following (AV) signatures:W32/Ransom_Win32_MAUICRYPT.YACC5W32/Agent.C5C2!trW32/PossibleThreatAnything Else to Note?Victims of ransomware are cautioned against paying ransoms by such organizations as CISA, NCSC, the FBI, and HHS. Payment does not guarantee files will be recovered. It may also embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and/or fund illicit activities which could potentially be illegal according to a U.S. Department of Treasury's Office of Foreign Assets Control (OFAC) advisory. | Ransomware Threat Patching Medical | Wannacry Wannacry APT 38 | ||
| 2022-06-27 10:00:00 | Stories from the SOC - Detecting internal reconnaissance (lien direct) | Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Extended Detection and Response customers.
Executive summary
Internal Reconnaissance, step one of the Cyber Kill Chain, is the process of collecting internal information about a target network to identify vulnerabilities that can potentially be exploited. Threat actors use the information gained from this activity to decide the most effective way to compromise the target network. Vulnerable services can be exploited by threat actors and potentially lead to a network breach. A network breach puts the company in the hands of cybercriminals. This can lead to ransomware attacks costing the company millions of dollars to remediate along with a tarnished public image.
The Managed Extended Detection and Response (MXDR) analyst team received two alarms regarding an asset performing network scans within a customer's environment. Further investigation into these alarms revealed that the source asset was able to scan 60 unique IPs within the environment and successfully detected numerous open ports with known vulnerabilities.
Investigation
Initial alarm review
Indicators of Compromise (IOC)
The initial alarm that prompted this investigation was a Darktrace Cyber Intelligence Platform event that was ingested by USM Anywhere. The priority level associated with this alarm was High, one level below the maximum priority of Critical. Network scanning is often one of the first steps a threat actor takes when attempting to compromise a network, so it is a red flag any time an unknown device is scanning the network without permission. From here, the SOC went deeper into associated events to see what activity was taking place in the customer’s environment. The image shown below is the Darktrace alarm that initiated the investigation.
 Expanded investigation
Events search
Utilizing the filters built into USM Anywhere , the events were narrowed down to the specific source asset IP address and Host Name to only query events associated to that specific asset. The following events were found that provide more information about the reconnaissance activity that was being observed.
Expanded investigation
Events search
Utilizing the filters built into USM Anywhere , the events were narrowed down to the specific source asset IP address and Host Name to only query events associated to that specific asset. The following events were found that provide more information about the reconnaissance activity that was being observed.

 Event deep dive
Upon reviewing the logs from the events shown above, the SOC was able to determine that the source asset scanned two separate Classless Inter-Domain Routing (CIDR) blocks, detecting, and scanning 60 unique internal devices for open ports. As shown in the log snippets below, the scans revealed multiple open ports with known vulnerabilities, most notable is Server Message Block (SMB) port 445 which is the key attack vector for the infamous WannaCry malware. Looking at the logs we can also see that the source asset detected port 5985, the port utilized by Windows Remote Management (WinRM). WinRM can be used by threat actors to move laterally in environments by executing remote commands on other assets from the compromised host. These remote commands are typically batch files performing malicious activity or implanting backdoors to maintain persistence in the network. Lastly, we can see the asset scanning for Lightweight Directory Access Protocol (LD
Event deep dive
Upon reviewing the logs from the events shown above, the SOC was able to determine that the source asset scanned two separate Classless Inter-Domain Routing (CIDR) blocks, detecting, and scanning 60 unique internal devices for open ports. As shown in the log snippets below, the scans revealed multiple open ports with known vulnerabilities, most notable is Server Message Block (SMB) port 445 which is the key attack vector for the infamous WannaCry malware. Looking at the logs we can also see that the source asset detected port 5985, the port utilized by Windows Remote Management (WinRM). WinRM can be used by threat actors to move laterally in environments by executing remote commands on other assets from the compromised host. These remote commands are typically batch files performing malicious activity or implanting backdoors to maintain persistence in the network. Lastly, we can see the asset scanning for Lightweight Directory Access Protocol (LD |
Ransomware Malware Threat Guideline | Wannacry | ||
| 2022-05-19 02:00:00 | WannaCry 5 years on: Still a top threat (lien direct) | Who doesn't love an anniversary and the opportunity to reminisce about “where we were” when an historical event happened? Such is the case over the last several days when it comes to remembering WannaCry, the ransomware that infected thousands of computers five years ago and cost companies all over the world billions of dollars in damages.WannaCry broke onto the infosec scene on May 12, 2017. Taking advantage of the vulnerable version of the Server Message Block (SMB) protocol, it ultimately infected approximately 200,000+ machines in more than 150 countries. While Microsoft had issued a patch for the SMB flaw more than a month before the attacks began, millions of computers had not been unpatched against the bug. The largest ransomware attack ever, it impacted several big names globally, including the UK's National Health Service, US delivery giant FedEx, and Deutsche Bahn, the German railway company.To read this article in full, please click here | Ransomware Threat | FedEx Wannacry | ||
| 2022-05-12 16:45:59 | Ransomware cyber-attacks in Costa Rica and Peru drives national response (lien direct) | >Highlights Effectively, one out of every 60 organizations globally have been impacted by attempted ransomware attacks every week, so far in in the first four months of 2022 A 14% increase of attempted ransomware attacks to organizations globally every week compared to the same period last year. To mark the 5th anniversary of the WannaCry… | Ransomware | Wannacry | ||
| 2022-05-12 00:37:30 | How the evolution of ransomware has changed the threat landscape (lien direct) | >From WannaCry to Conti: A 5-Year Perspective Five years ago, on May 12, 2017, the world fell victim to a major ransomware attack known as 'WannaCry'. The attack had an unprecedented scale, and spread around the world like wildfire, with more than 200,000 Windows computers across 150 countries affected outbreaking only a few days.… | Ransomware Threat | Wannacry Wannacry | ||
| 2022-05-11 12:57:31 | Wannacry – 5 Years On, 68% Of Enterprises Are Still At Risk (lien direct) | 5 years on from one of the world’s most damaging ransomware attacks, research from network detection and response leader ExtraHop has found that 68% of enterprises are still running insecure protocol that were exploited by the North Korean ransomware. | Ransomware Guideline | Wannacry | ★★★ | |
| 2022-03-24 18:09:09 | Smart Tips for Staying Safer Online (lien direct) | The recent WannaCry ransomware attack that infected more than 250,000 computers worldwide was a good reminder to everyone about staying... | Ransomware | Wannacry Wannacry | ||
| 2022-02-27 22:30:37 | Previously Unseen Backdoor Bvp47 Potentially Victimized Global Targets (lien direct) | FortiGuard Labs is aware of a report by Pangu Lab that a new Linux backdoor malware that reportedly belongs to the Equation group was used to potentially compromise more than 200 organizations across over 40 countries around the globe. The Equation group is regarded as one of the most highly skilled threat actors, which some speculate have close connections with National Security Agency (NSA). The threat actor is also reported have been tied to the Stuxnet malware that was used in 2010 cyber attack on a nuclear centrifuge facility in Iran.Why is this Significant?Bvp47 is a previously undiscovered backdoor malware that was reportedly used in cyber attacks carried out by the Equation group. According to the report and information available in the documents that presumably leaked from the Equation group, over 200 organizations spread across more than 40 countries may have been infected with the Bvp47 malware.The Bvp47 file called out in the report was first submitted to VirusTotal in late 2013, which indicates that Bvp47 was used and undiscovered for close to a decade.How was the Connection between the Bvp47 malware and the Equation Group Established?Pangu Lab concluded that Bvp47 belongs to the Equation group because one of the folders included in the documents leaked by the Shadow Brokers in 2017 contained a RSA private key required by Bvp47 for its command execution and other operations.What is the Shadow Brokers?The Shadow Brokers is a threat actor who claimed to have stolen highly classified information from the Equation group in 2016. The stolen information includes zero-day exploits, operation manuals and description of tools used by the Equation group. The Shadow Brokers then attempted to sell the information to the highest bidder. After no one purchased the information, The threat actor released the information to the public after the auction attempt failed.One of the most famous exploits included in the leaked documents is EternalBlue. Within a few weeks of the leak, EternalBlue was incorporated in Wannacry ransomware which caused global panic in 2017.What are the Characteristics of Bvp47?Bvp is a Linux backdoor that performs actions upon receiving commands from Command and Control (C2) servers.Because the Bvp47 framework is incorporated with components such as "dewdrops" and "solutionchar_agents" that are included in the Shadow Brokers leaks, the backdoor is for mainstream Linux distributions, FreeBSD, Solaris as well as JunOS,.Bvp47 also runs various environment checks. If the requirements are not met, the malware deletes itself.What is the Status of Coverage?FortiGuard Labs provide the following AV coverage against Bvp47:ELF/Agent.16DC!tr | Ransomware Malware Threat | Wannacry Wannacry | ||
| 2022-02-23 14:00:22 | Creaky Old WannaCry, GandCrab Top the Ransomware Scene (lien direct) | Nothing like zombie campaigns: WannaCry's old as dirt, and GandCrab threw in the towel years ago. They're on auto-pilot at this point, researchers say. | Ransomware | Wannacry | ||
| 2022-02-01 14:37:29 | CyberheistNews Vol 12 #05 [Heads Up] DHS Sounds Alarm on New Russian Destructive Disk Wiper Attack Potential (lien direct) |
![CyberheistNews Vol 12 #05 [Heads Up] DHS Sounds Alarm on New Russian Destructive Disk Wiper Attack Potential](https://blog.knowbe4.com/hubfs/Stu_Headshot_2021_resize.png)
|
Ransomware Malware Hack Tool Threat Guideline | NotPetya NotPetya Wannacry Wannacry APT 27 APT 27 | ||
| 2022-01-03 03:32:41 | Are Medical Devices at Risk of Ransomware Attacks? (lien direct) | In May 2017, the first documented ransomware assault on networked medical equipment happened. The worldwide ransomware assault WannaCry compromised radiological and other instruments in several hospitals during its height, after a software failure caused by a cyberattack on its third-party vendor's oncology cloud service, cancer patients having radiation therapy at four healthcare institutions | Ransomware | Wannacry Wannacry | ||
| 2021-10-25 12:44:44 | Malicious Life Podcast: Marcus Hutchins - A Controversial Hero (lien direct) |
 In May 2017, Marcus Hutchins - AKA MalwareTech - became a hero for stopping WannaCry, a particularly nasty ransomware that spread quickly all over the world. Yet his fame also brought to light his troubled past as the teenage Black Hat hacker who created KRONOS, a dangerous rootkit. Should a criminal-turned-hero be punished for his past crimes? Check it out...
In May 2017, Marcus Hutchins - AKA MalwareTech - became a hero for stopping WannaCry, a particularly nasty ransomware that spread quickly all over the world. Yet his fame also brought to light his troubled past as the teenage Black Hat hacker who created KRONOS, a dangerous rootkit. Should a criminal-turned-hero be punished for his past crimes? Check it out... |
Ransomware | Wannacry | ||
| 2021-09-01 16:00:00 | What Has Changed Since the 2017 WannaCry Ransomware Attack? (lien direct) | The cybersecurity world is still feeling the effects of the 2017 WannaCry ransomware attack today. While the majority of the damage occurred in the weeks after May 12, 2017, WannaCry ransomware attacks actually increased 53% from January 2021 to March 2021. While researching my in-depth article WannaCry: How the Widespread Ransomware Changed Cybersecurity, I learned […] | Ransomware | Wannacry Wannacry | ||
| 2021-06-29 15:00:34 | How to Proactively Increase Your Protection Against Ransomware with Threat Intelligence (lien direct) |  As Ransomware continues to spread and target organizations around the world, it is critical to leverage threat intelligence data. And not just any threat intelligence but actionable intelligence from MVISION Insights. Fortunately, there are several steps you can take to proactively increase your Endpoint Security to help minimize damage from the next Darkside, WannaCry, Ryuk, […]
As Ransomware continues to spread and target organizations around the world, it is critical to leverage threat intelligence data. And not just any threat intelligence but actionable intelligence from MVISION Insights. Fortunately, there are several steps you can take to proactively increase your Endpoint Security to help minimize damage from the next Darkside, WannaCry, Ryuk, […]
|
Ransomware Threat | Wannacry | ||
| 2021-06-15 12:02:15 | WannaCry est à nouveau sur le devant de la scène (lien direct) | L'attaque du Ransomware WannaCry a fêté son quatrième anniversaire après avoir fait des ravages dans le monde. Les chercheurs de Check-Points ont noté une augmentation de 53 % du nombre d'organisations affectées par le Ransomware. The post WannaCry est à nouveau sur le devant de la scène first appeared on UnderNews. | Ransomware | Wannacry Wannacry | ||
| 2021-05-10 12:16:40 | Experts Comments on Anti Ransomware Day – 12th May (lien direct) | WannaCry, notorious as the largest ransomware epidemic in history, reached its peak on May 12, 2017. To raise awareness of this ongoing threat, INTERPOL dubbed the 12th of May Anti-Ransomware Day and urged organisations… | Ransomware | Wannacry | ||
| 2021-04-27 17:24:00 | Anomali Cyber Watch: HabitsRAT Targeting Linux and Windows Servers, Lazarus Group Targetting South Korean Orgs, Multiple Zero-Days and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Android Malware, RATs, Phishing, QLocker Ransomware and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Zero-day Vulnerabilities in SonicWall Email Security Actively Exploited
(published: April 21, 2021)
US cybersecurity company SonicWall said fixes have been published to resolve three critical issues in its email security solution that are being actively exploited in the wild. The vulnerabilities are tracked as CVE-2021-20021, CVE-2021-20022, and CVE-2021-20023, impacting SonicWall ES/Hosted Email Security (HES) versions 10.0.1 and above.
Analyst Comment: The patches for these vulnerabilities have been issued and should be applied as soon as possible to avoid potential malicious behaviour. SonicWall’s security notice can be found here https://www.sonicwall.com/support/product-notification/security-notice-sonicwall-email-security-zero-day-vulnerabilities/210416112932360/. It is important that your company has patch-maintenance policies in place. Once a vulnerability has been publicly reported,, threat actors will likely attempt to incorporate the exploitation of the vulnerability into their malicious operations. Patches should be reviewed and applied as soon as possible to prevent potential malicious activity.
MITRE ATT&CK: [MITRE ATT&CK] Remote File Copy - T1105 | [MITRE ATT&CK] File and Directory Discovery - T1083
Tags: CVE-2021-20021, CVE-2021-20023, CVE-2021-20022
Massive Qlocker Ransomware Attack Uses 7zip to Encrypt QNAP Devices
(published: April 21, 2021)
The ransomware is called Qlocker and began targeting QNAP devices on April 19th, 2021. All victims are told to pay 0.01 Bitcoins, which is approximately $557.74, to get a password for their archived files. While the files are being locked, the Resource Monitor will display numerous '7z' processes which are the 7zip command-line executable.
Analyst Comment: Attackers are using legitimate tools like 7zip to evade detections by traditional antiviruses. EDR solutions can help tracking suspicious command line arguments and process creations to potentially detect such attacks. Customers should use backup solutions to be able recover encrypted files.
MITRE ATT&CK: [MITRE ATT&CK] Credentials in Files - T1081
Tags: Tor, Qlocker, CVE-2020-2509, CVE-2020-36195
Novel Email-Based Campaign Targets Bloomberg Clients with RATs
(published: April 21, 2021)
A new e-mail-based campaign by an emerging threat actor aims to spread various remote access trojans (RATs) to a very specific group of targets who use Bloomberg's industry-based services. Attacks start in the form of targeted emails to c
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Zero-day Vulnerabilities in SonicWall Email Security Actively Exploited
(published: April 21, 2021)
US cybersecurity company SonicWall said fixes have been published to resolve three critical issues in its email security solution that are being actively exploited in the wild. The vulnerabilities are tracked as CVE-2021-20021, CVE-2021-20022, and CVE-2021-20023, impacting SonicWall ES/Hosted Email Security (HES) versions 10.0.1 and above.
Analyst Comment: The patches for these vulnerabilities have been issued and should be applied as soon as possible to avoid potential malicious behaviour. SonicWall’s security notice can be found here https://www.sonicwall.com/support/product-notification/security-notice-sonicwall-email-security-zero-day-vulnerabilities/210416112932360/. It is important that your company has patch-maintenance policies in place. Once a vulnerability has been publicly reported,, threat actors will likely attempt to incorporate the exploitation of the vulnerability into their malicious operations. Patches should be reviewed and applied as soon as possible to prevent potential malicious activity.
MITRE ATT&CK: [MITRE ATT&CK] Remote File Copy - T1105 | [MITRE ATT&CK] File and Directory Discovery - T1083
Tags: CVE-2021-20021, CVE-2021-20023, CVE-2021-20022
Massive Qlocker Ransomware Attack Uses 7zip to Encrypt QNAP Devices
(published: April 21, 2021)
The ransomware is called Qlocker and began targeting QNAP devices on April 19th, 2021. All victims are told to pay 0.01 Bitcoins, which is approximately $557.74, to get a password for their archived files. While the files are being locked, the Resource Monitor will display numerous '7z' processes which are the 7zip command-line executable.
Analyst Comment: Attackers are using legitimate tools like 7zip to evade detections by traditional antiviruses. EDR solutions can help tracking suspicious command line arguments and process creations to potentially detect such attacks. Customers should use backup solutions to be able recover encrypted files.
MITRE ATT&CK: [MITRE ATT&CK] Credentials in Files - T1081
Tags: Tor, Qlocker, CVE-2020-2509, CVE-2020-36195
Novel Email-Based Campaign Targets Bloomberg Clients with RATs
(published: April 21, 2021)
A new e-mail-based campaign by an emerging threat actor aims to spread various remote access trojans (RATs) to a very specific group of targets who use Bloomberg's industry-based services. Attacks start in the form of targeted emails to c |
Ransomware Malware Tool Vulnerability Threat Medical | Wannacry Wannacry APT 38 APT 28 | ||
| 2021-03-17 18:03:00 | Anomali Cyber Watch: APT, Ransomware, Vulnerabilities and More (lien direct) | The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, AlientBot, Clast82, China, DearCry, RedXOR, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Google: This Spectre proof-of-concept shows how dangerous these attacks can be
(published: March 15, 2021)
Google has released a proof of concept (PoC) code to demonstrate the practicality of Spectre side-channel attacks against a browser's JavaScript engine to leak information from its memory. Spectre targeted the process in modern CPUs called speculative execution to leak secrets such as passwords from one site to another. While the PoC demonstrates the JavaScript Spectre attack against Chrome 88's V8 JavaScript engine on an Intel Core i7-6500U CPU on Linux, Google notes it can easily be tweaked for other CPUs, browser versions and operating systems.
Analyst Comment: As the density of microchip manufacturing continues to increase, side-channel attacks are likely to be found across many architectures and are difficult (and in some cases impossible) to remediate in software. The PoC of the practicality of performing such an attack using javascript emphasises that developers of both software and hardware be aware of these types of attacks and the means by which they can be used to invalidate existing security controls.
Tags: CVE-2017-5753
Threat Assessment: DearCry Ransomware
(published: March 12, 2021)
A new ransomware strain is being used by actors to attack unpatched Microsoft Exchange servers. Microsoft released patches for four vulnerabilities that are being exploited in the wild. The initial round of attacks included installation of web shells onto affected servers that could be used to infect additional computers. While the initial attack appears to have been done by sophisticated actors, the ease and publicity around these vulnerabilities has led to a diverse group of actors all attempting to compromise these servers.
Analyst Comment: Patch and asset management are a critical and often under-resourced aspect of defense in depth. As this particular set of vulnerabilities and attacks are against locally hosted Exchange servers, organization may want to assess whether a hosted solution may make sense from a risk standpoint
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] File and Directory Discovery - T1083 | [MITRE ATT&CK] Email Collection - T1114 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] System Service Discovery - T1007 | [MITRE ATT&CK] Data Encrypted for Impact - T1486 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Google: This Spectre proof-of-concept shows how dangerous these attacks can be
(published: March 15, 2021)
Google has released a proof of concept (PoC) code to demonstrate the practicality of Spectre side-channel attacks against a browser's JavaScript engine to leak information from its memory. Spectre targeted the process in modern CPUs called speculative execution to leak secrets such as passwords from one site to another. While the PoC demonstrates the JavaScript Spectre attack against Chrome 88's V8 JavaScript engine on an Intel Core i7-6500U CPU on Linux, Google notes it can easily be tweaked for other CPUs, browser versions and operating systems.
Analyst Comment: As the density of microchip manufacturing continues to increase, side-channel attacks are likely to be found across many architectures and are difficult (and in some cases impossible) to remediate in software. The PoC of the practicality of performing such an attack using javascript emphasises that developers of both software and hardware be aware of these types of attacks and the means by which they can be used to invalidate existing security controls.
Tags: CVE-2017-5753
Threat Assessment: DearCry Ransomware
(published: March 12, 2021)
A new ransomware strain is being used by actors to attack unpatched Microsoft Exchange servers. Microsoft released patches for four vulnerabilities that are being exploited in the wild. The initial round of attacks included installation of web shells onto affected servers that could be used to infect additional computers. While the initial attack appears to have been done by sophisticated actors, the ease and publicity around these vulnerabilities has led to a diverse group of actors all attempting to compromise these servers.
Analyst Comment: Patch and asset management are a critical and often under-resourced aspect of defense in depth. As this particular set of vulnerabilities and attacks are against locally hosted Exchange servers, organization may want to assess whether a hosted solution may make sense from a risk standpoint
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted - T1022 | [MITRE ATT&CK] Exploit Public-Facing Application - T1190 | [MITRE ATT&CK] File and Directory Discovery - T1083 | [MITRE ATT&CK] Email Collection - T1114 | [MITRE ATT&CK] Obfuscated Files or Information - T1027 | [MITRE ATT&CK] System Service Discovery - T1007 | [MITRE ATT&CK] Data Encrypted for Impact - T1486 | |
Ransomware Tool Vulnerability Threat Guideline | Wannacry APT 41 APT 34 | ||
| 2021-03-02 15:00:00 | Anomali Cyber Watch: APT Groups, Cobalt Strike, Russia, Malware, and More (lien direct) |
We are excited to announce Anomali Cyber Watch, your weekly intelligence digest. Replacing the Anomali Weekly Threat Briefing, Anomali Cyber Watch provides summaries of significant cybersecurity and threat intelligence events, analyst comments, and recommendations from Anomali Threat Research to increase situational awareness, and the associated tactics, techniques, and procedures (TTPs) to empower automated response actions proactively.
We hope you find this version informative and useful. If you haven’t already subscribed get signed up today so you can receive curated and summarized cybersecurity intelligence events weekly.
The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: China, Emotet, Go, Masslogger, Mustang Panda, OilRig, and Vulnerabilities. The IOCs related to these stories are attached to the Weekly Threat Briefing and can be used to check your logs for potential malicious activity.
 Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Hypervisor Jackpotting: CARBON SPIDER and SPRITE SPIDER Target ESXi Servers With Ransomware to Maximize Impact
(published: February 26, 2021)
Recent reporting indicates that two prolific cybercrime threat groups, CARBON SPIDER and SPRITE SPIDER, have begun targeting ESXi, a hypervisor developed by VMWare to run and manage virtual machines. SPRITE SPIDER uses PyXie's LaZagne module to recover vCenter credentials stored in web browsers and runs Mimikatz to steal credentials from host memory. After authenticating to vCenter, SPRITE SPIDER enables ssh to permit persistent access to ESXi devices. In some cases, they also change the root account password or the host’s ssh keys. Before deploying Defray 777, SPRITE SPIDER’s ransomware of choice, they terminate running VMs to allow the ransomware to encrypt files associated with those VMs. CARBON SPIDER has traditionally targeted companies operating POS devices, with initial access being gained using low-volume phishing campaigns against this sector. But throughout 2020 they were observed shifting focus to “Big Game Hunting” with the introduction of the Darkside Ransomware. CARBON SPIDER gains access to ESXi servers using valid credentials and reportedly also logs in over ssh using the Plink utility to drop the Darkside
Recommendation: Both CARBON SPIDER and SPRITE SPIDER likely intend to use ransomware targeting ESXi to inflict greater harm – and hopefully realize larger profits – than traditional ransomware operations against Windows systems. Should these campaigns continue and prove to be profitable, we would expect more threat actors to imitate these activities.
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | [MITRE ATT&CK] Process Discovery - T1057 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] Scheduled Transfer - T1029 |
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Hypervisor Jackpotting: CARBON SPIDER and SPRITE SPIDER Target ESXi Servers With Ransomware to Maximize Impact
(published: February 26, 2021)
Recent reporting indicates that two prolific cybercrime threat groups, CARBON SPIDER and SPRITE SPIDER, have begun targeting ESXi, a hypervisor developed by VMWare to run and manage virtual machines. SPRITE SPIDER uses PyXie's LaZagne module to recover vCenter credentials stored in web browsers and runs Mimikatz to steal credentials from host memory. After authenticating to vCenter, SPRITE SPIDER enables ssh to permit persistent access to ESXi devices. In some cases, they also change the root account password or the host’s ssh keys. Before deploying Defray 777, SPRITE SPIDER’s ransomware of choice, they terminate running VMs to allow the ransomware to encrypt files associated with those VMs. CARBON SPIDER has traditionally targeted companies operating POS devices, with initial access being gained using low-volume phishing campaigns against this sector. But throughout 2020 they were observed shifting focus to “Big Game Hunting” with the introduction of the Darkside Ransomware. CARBON SPIDER gains access to ESXi servers using valid credentials and reportedly also logs in over ssh using the Plink utility to drop the Darkside
Recommendation: Both CARBON SPIDER and SPRITE SPIDER likely intend to use ransomware targeting ESXi to inflict greater harm – and hopefully realize larger profits – than traditional ransomware operations against Windows systems. Should these campaigns continue and prove to be profitable, we would expect more threat actors to imitate these activities.
MITRE ATT&CK: [MITRE ATT&CK] Data Encrypted for Impact - T1486 | [MITRE ATT&CK] Hidden Files and Directories - T1158 | [MITRE ATT&CK] Process Discovery - T1057 | [MITRE ATT&CK] File Deletion - T1107 | [MITRE ATT&CK] Remote Services - T1021 | [MITRE ATT&CK] Scheduled Transfer - T1029 | |
Ransomware Malware Threat | Wannacry Wannacry APT 29 APT 28 APT 31 APT 34 | ||
| 2021-02-28 20:05:19 | We are living in 1984 (ETERNALBLUE) (lien direct) | In the book 1984, the protagonist questions his sanity, because his memory differs from what appears to be everybody else's memory.The Party said that Oceania had never been in alliance with Eurasia. He, Winston Smith, knew that Oceania had been in alliance with Eurasia as short a time as four years ago. But where did that knowledge exist? Only in his own consciousness, which in any case must soon be annihilated. And if all others accepted the lie which the Party imposed-if all records told the same tale-then the lie passed into history and became truth. 'Who controls the past,' ran the Party slogan, 'controls the future: who controls the present controls the past.' And yet the past, though of its nature alterable, never had been altered. Whatever was true now was true from everlasting to everlasting. It was quite simple. All that was needed was an unending series of victories over your own memory. 'Reality control', they called it: in Newspeak, 'doublethink'.I know that EternalBlue didn't cause the Baltimore ransomware attack. When the attack happened, the entire cybersecurity community agreed that EternalBlue wasn't responsible.But this New York Times article said otherwise, blaming the Baltimore attack on EternalBlue. And there are hundreds of other news articles [eg] that agree, citing the New York Times. There are no news articles that dispute this.In a recent book, the author of that article admits it's not true, that EternalBlue didn't cause the ransomware to spread. But they defend themselves as it being essentially true, that EternalBlue is responsible for a lot of bad things, even if technically, not in this case. Such errors are justified, on the grounds they are generalizations and simplifications needed for the mass audience.So we are left with the situation Orwell describes: all records tell the same tale -- when the lie passes into history, it becomes the truth.Orwell continues:He wondered, as he had many times wondered before, whether he himself was a lunatic. Perhaps a lunatic was simply a minority of one. At one time it had been a sign of madness to believe that the earth goes round the sun; today, to believe that the past is inalterable. He might be ALONE in holding that belief, and if alone, then a lunatic. But the thought of being a lunatic did not greatly trouble him: the horror was that he might also be wrong.I'm definitely a lunatic, alone in my beliefs. I sure hope I'm not wrong. Update: Other lunatics document their struggles with Minitrue: When I was investigating the TJX breach, there were NYT articles citing unnamed sources that were made up & then outlets would publish citing the NYT. The TJX lawyers would require us to disprove the articles. Each time we would. It was maddening fighting lies for 8 months.— Nicholas J. Percoco (@c7five) March 1, 2021 |
Ransomware | NotPetya Wannacry APT 32 | ||
| 2021-02-17 21:12:56 | U.S. Indicts North Korean Hackers in Theft of $200 Million (lien direct) | The U.S. Justice Department today unsealed indictments against three men accused of working with the North Korean regime to carry out some of the most damaging cybercrime attacks over the past decade, including the 2014 hack of Sony Pictures, the global WannaCry ransomware contagion of 2017, and the theft of roughly $200 million and attempted theft of more than $1.2 billion from banks and other victims worldwide. | Ransomware Hack | Wannacry Wannacry | ||
| 2021-01-26 14:06:51 | Increase in Ransomware Attacks on Healthcare Industry (lien direct) | In 2017 the NHS fell victim to the WannaCry ransomware attack, causing severe disruption and causing the UK’s health service £92m. On top of that, 19,000 patient appointments were cancelled. The attack was launched with malicious code placed in commonly used software. As a result, health systems prompted a renewed focus on cyber defences. Especially, […] | Ransomware | Wannacry Wannacry | ||
| 2021-01-07 12:42:02 | L\'importance des mises à jour en matière de cybersécurité (lien direct) | Qu'on se le dise, les systèmes qui ne sont pas régulièrement mis à jour sont fortement exposés aux cyberattaques. Dans ce contexte, le ransomware WannaCry fait figure d'illustration parfaite de la vulnérabilité des postes. The post L'importance des mises à jour en matière de cybersécurité first appeared on UnderNews. | Ransomware | Wannacry Wannacry | ||
| 2020-10-28 16:00:20 | WannaCry: How the Widespread Ransomware Changed Cybersecurity (lien direct) | If I had polled cybersecurity experts on their way to work on May 12, 2017, most of them would have said they knew a major cybersecurity event loomed. Yet, on that day no one expected that they were walking into the perfect storm — in the form of WannaCry ransomware, the most damaging cyberattack to […] | Ransomware | Wannacry | ||
| 2020-07-28 13:38:33 | Kaspersky: North Korean hackers are behind the VHD ransomware (lien direct) | North Korean hackers return to actively deploying ransomware after the huge WannaCry debacle. | Ransomware | Wannacry | ||
| 2020-06-30 16:27:31 | Ransomware: Weapons of Mass Disruption (lien direct) |
 May 12th 2020 marked the 3 year anniversary of the WannaCry ransomware attack. Estimated to have affected hundreds of thousands of endpoints across 150 countries all around the world, the total damages as a result of the WannaCry attack have reached up to 4 billion USD, according to some accounts.
May 12th 2020 marked the 3 year anniversary of the WannaCry ransomware attack. Estimated to have affected hundreds of thousands of endpoints across 150 countries all around the world, the total damages as a result of the WannaCry attack have reached up to 4 billion USD, according to some accounts. |
Ransomware | Wannacry | ||
| 2020-06-24 13:01:51 | 3 ans après, le spectre de NotPetya est toujours présent (lien direct) | Le nom de NotPetya est familier à toute personne intéressée par le sujet de la cybersécurité. NotPetya est désormais connue comme la 3èmecyberattaque mondiale, survenue en 2017, après les non moins célèbres Wannacry et Adylkuzz. Apparue le 27 juin 2017, NotPetya a été défini comme un ransomware - puisque demandant le paiement d'une rançon – mais d'un genre un peu nouveau puisqu'il agissait d'un malware destructeur de données – wiper - se propageant comme un ver informatique. NotPetya était surtout basé, comme (...) - Points de Vue | Ransomware Malware | NotPetya Wannacry | ★★★ | |
| 2020-05-13 09:49:35 | “Anti-Ransomware Day” declared by Interpol (lien direct) | International crime-fighting organization INTERPOL has teamed up with cybersecurity firm Kaspersky to declare WannaCry’s third anniversary ‘Anti-Ransomware Day.’ bWannaCry, notorious as the largest ransomware epidemic in history, reached its peak on May 12, 2017. Recent research by Kaspersky confirms that three years on, WannaCry retains the dubious honor of being among the most prevalent ransomware […] | Ransomware | Wannacry | ||
| 2020-05-13 02:35:07 | U.S Defence Warns of 3 New Malware Used by North Korean Hackers (lien direct) | Yesterday, on the 3rd anniversary of the infamous global WannaCry ransomware outbreak for which North Korea was blamed, the U.S. government released information about three new malware strains used by state-sponsored North Korean hackers.
Called COPPERHEDGE, TAINTEDSCRIBE, and PEBBLEDASH, the malware variants are capable of remote reconnaissance and exfiltration of sensitive information from |
Ransomware Malware | Wannacry | ||
| 2020-05-12 12:30:02 | WannaCryptor remains a global threat three years on (lien direct) | WannaCryptor is still alive and kicking, so much so that it sits atop the list of the most commonly detected ransomware families | Ransomware Threat | Wannacry | ||
| 2020-02-24 23:30:00 | Ransomware contre la machine: comment les adversaires apprennent à perturber la production industrielle en le ciblant et en OT Ransomware Against the Machine: How Adversaries are Learning to Disrupt Industrial Production by Targeting IT and OT (lien direct) |
Depuis au moins 2017, il y a eu une augmentation significative des divulgations publiques des incidents de ransomwares ayant un impact sur la production industrielle et les organisations d'infrastructures critiques.Des familles de ransomwares bien connues comme Wannacry,Lockergoga, Megacortex, Ryuk, Maze, et maintenant Snakehose (alias Snake / Ekans), ont des victimes de coûts dans une variété de verticales de l'industrie plusieurs millions de dollarsen rançon et en coûts de garantie.Ces incidents ont également entraîné des perturbations et des retards importants sur les processus physiques qui permettent aux organisations de produire et de fournir des biens et services.
tandis que beaucoup
Since at least 2017, there has been a significant increase in public disclosures of ransomware incidents impacting industrial production and critical infrastructure organizations. Well-known ransomware families like WannaCry, LockerGoga, MegaCortex, Ryuk, Maze, and now SNAKEHOSE (a.k.a. Snake / Ekans), have cost victims across a variety of industry verticals many millions of dollars in ransom and collateral costs. These incidents have also resulted in significant disruptions and delays to the physical processes that enable organizations to produce and deliver goods and services. While lots |
Ransomware Industrial | Wannacry | ★★★ | |
| 2020-01-30 13:54:30 | The NHS has only suffered six ransomware attacks since the WannaCry worm, investigation reveals (lien direct) | An investigation claims that the UK's National Health Service, which was hit hard by the notorious WannaCry worm in 2017, has seen a marked fall in ransomware attacks since. Read more in my article on the Tripwire State of Security blog. | Ransomware | Wannacry | ||
| 2019-11-21 20:46:20 | Experts Comments On The News: French Hospital Hit By Ransomware Attack (lien direct) | You may have already spotted, but a ransomware attack has hit a French hospital crippling 6,000 computers; reminiscent of WannaCry, which hit the NHS in 2017. To prevent the infection spreading, the IT team opted to close down the systems and operate in 'degraded mode'. It is predicted it will take much of this week to … The ISBuzz Post: This Post Experts Comments On The News: French Hospital Hit By Ransomware Attack | Ransomware | Wannacry | ||
| 2019-11-05 13:04:14 | Spanish companies hit by ransomware (lien direct) | Two major Spanish companies have been hit by ransomware today. Both infections occurred on the same day, sparking memories of the WannaCry outbreak. Spain was one of the first countries alongside the UK, where the WannaCry ransomware infections were spotted for the first time back on May 12, 2017. Affected at the time were Spanish newspaper […] | Ransomware | Wannacry | ★★★ | |
| 2019-11-04 17:53:28 | Ransomware hits Spanish companies, sparking WannaCry panic (lien direct) | Two victims reported so far: IT consultancy firm Everis and leading radio network Cadena SER. | Ransomware Guideline | Wannacry | ||
| 2019-09-27 09:33:26 | Emsisoft released a new free decryption tool for the Avest ransomware (lien direct) | Emsisoft security firm has released a new free decryption tool for the Avest ransomware, a few days after the release of WannaCryFake decryptor. Emsisoft security firm has released a new free decryption tool for the Avest ransomware, a few days ago the researchers also released a free decryptor for the WannaCryFake ransomware. The Avest ransomware […] | Ransomware Tool | Wannacry | ||
| 2019-09-26 07:01:34 | Emsisoft releases a free decryptor for the WannaCryFake ransomware (lien direct) | Researchers at Emsisoft security firm have released a new free decryption tool for the WannaCryFake ransomware. Good news for the vicitms of the WannaCryFake ransomware, researchers at Emsisoft have released a FREE decryption tool that will allow decrypting their data. WannaCryFake is a piece of ransomware that uses AES-256 to encrypt a victim's files. The […] | Ransomware Tool | Wannacry |
To see everything:
Our RSS (filtrered)
