What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-05-18 14:06:04 | PATCH Act: A New Bill Designed to Prevent Occurrences Like WannaCrypt (lien direct) | Following the worldwide WannaCrypt ransomware attack that leveraged the EternalBlue exploit developed by and stolen from the NSA, Microsoft's chief legal officer called for governments to stop stockpiling 0-day exploits. His arguments are morally appealing but politically difficult. | Wannacry | |||
| 2017-05-18 12:00:00 | NSA Tools Behind WannaCry Being Used In Even Bigger Attack Campaign (lien direct) | Attackers have been using NSAs EternalBlue and Double Pulsar to distribute AdylKuzz cryptocurrency malware to hundreds of thousands of systems, Proofpoint says. | Wannacry | |||
| 2017-05-18 11:56:07 | How Basic Endpoint Patching Helps Protect Against Ransomware and Other Attacks (lien direct) | Effective defense against large-scale ransomware attacks such as WannaCry starts with basic endpoint protection and patch management. | Wannacry | |||
| 2017-05-18 11:42:12 | What You Need To Know About WannaCry (lien direct) | The ISBuzz Post: This Post What You Need To Know About WannaCry | Wannacry | |||
| 2017-05-18 11:30:00 | WannaCry: Ransomware Catastrophe or Failure? (lien direct) | Using Bitcoin payments as a measure, the WannaCry attack is not nearly as profitable as the headlines suggest. But you should still patch your Windows systems and educate users. | Wannacry | |||
| 2017-05-18 10:14:38 | Researchers discover another ongoing cyberattack using NSA hacking tools (lien direct) | Cybersecurity researchers have identified a second ongoing global cyberattack that has quietly hijacked hundreds of thousands of computers around the world, including many in the United States, for a massive cryptocurrency mining operation.While investigating the WannaCry ransomware attacks, researchers at the cybersecurity firm Proofpoint stumbled upon another “less noisy†form of malware called Adylkuzz that, ... | Wannacry | |||
| 2017-05-18 10:09:52 | Ransomware Attack a Wake-Up Call (lien direct) | The WannaCry ransomware attack that has impacted an estimated 300,000 users in 150 countries is a wake-up call for both government and business, said the global body for ICT professionals. Mike Hinchey, President of IFIP (International Federation for Information Processing), today warned that WannaCry was only the latest in a series of online attacks that ... | Wannacry | ★★★★ | ||
| 2017-05-18 09:00:45 | WannaCryptor: Are governments and financial regulators to blame? (lien direct) | Are governments and financial regulators to blame for WannaCryptor, aka WannaCry, asks Tony Anscombe in this insightful feature. | Wannacry | |||
| 2017-05-18 08:00:46 | Check Point Reveals Global WannaCry Ransomware Infection Map (lien direct) | The ISBuzz Post: This Post Check Point Reveals Global WannaCry Ransomware Infection Map | Wannacry | |||
| 2017-05-18 06:55:07 | My Little CVE Bot, (Thu, May 18th) (lien direct) | The massive spread of the WannaCry ransomware last Friday was another good proof that many organisations still fail to patch their systems. Everybody admits that patching is a boring task. They are many constraints that make this process very difficult to implement and... apply!Thats why any help is welcome to know what to patch and when. This is the key: What to patch? What are the applications/appliancesthat are deployed in your infrastructure? When to patch? When are new vulnerabilities discovered? The classification of vulnerabilities is based on the CVE (or Common Vulnerabilities and Exposures) standard maintained by mitre.org[1]. To explain briefly, when a security researcher or a security firm finds a new vulnerability, a CVE number is assigned to it (CVE-YYYY-NNNNN). The CVE contains all the details of the vulnerability (which application/system is affected, the severity and many more information). As an example, the vulnerability exploited by WannaCry was %%cve:2017-0143%%. Those CVE are stored in open databases and many organisations are using them and provide online services like cvedetails.com[2]. There are plenty of them that offer almost all the same features but they don width:700px" /> Based on cve-search, I can provide details about new CVEs to my customers or any other organisationsjust by querying the database. Indeed, reading the daily flow of CVE is difficult and useless for many people. They have to focus on what affect them. To help them, Im using a quick padding:5px 10px"> email_contact | days_to_check | output_format | product_definition [ | product_definition ] ... The script will parse this config file and search for new CVE for each product definition. Results will be sent via email to the specified address. As I width:700px" /> Of course, the main requirement is to know what you are using on your infrastructure. The information used in the config file describes the products is based on the CPE standard[6] which categorisesapplications, operating systems and hardware devices. This information can be found byNmap. An alternative is touse the following tool on your own network (only!): cve-scan[7]. It scans hosts and searches for vulnerabilities in thecve-search database. My script is available on my GitHubrepository[5]. [1]https://cve.mitre.org [2]http://www.cvedetails.com/ [3]https://github.com/cve-search/cve-search [4]https://hub.docker.com/r/rootshell/cvesearch/ [5]https://github.com/xme/toolbox [6]http://cpe.mitre.org/ [7]https://github.com/NorthernSec/cve-scan Xavier Mertens (@xme) ISC Handler - Freelance Security Consultant PGP Key (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License. | Wannacry | |||
| 2017-05-18 06:08:35 | Smashing Security #21: WannaCry - Who\'s to blame? (lien direct) |  The WannaCry ransomware predictably dominates the discussion in our podcast this week, but that's not the only security story that caught our eye.
Computer security veterans Graham Cluley and Carole Theriault are joined on the podcast this week by special guest Paul Baccas. The WannaCry ransomware predictably dominates the discussion in our podcast this week, but that's not the only security story that caught our eye.
Computer security veterans Graham Cluley and Carole Theriault are joined on the podcast this week by special guest Paul Baccas.
|
Wannacry | ★★★★ | ||
| 2017-05-18 05:00:52 | WannaCry biggest incident to date for National Cyber Security Centre (lien direct) | The WannaCry ransomware attack that started on 12 May 2017 is the biggest single incident that the new UK National Cyber Security Centre (NCSC) has faced | Wannacry | |||
| 2017-05-18 02:12:30 | APT Inc.: Research Finds Ties Between Chinese Security Firm and Advanced Threat Group (lien direct) | In-brief: The hacking group known as APT 3 appears to be a commercial outfit working on behalf of the Chinese Ministry of State Security (MSS), the firm Recorded Future reported on Wednesday. The hacking group known as APT 3 appears to be a commercial outfit working on behalf of the Chinese Ministry of State Security (MSS), the firm Recorded...Read the whole entry... _!fbztxtlnk!_ https://feeds.feedblitz.com/~/324578408/0/thesecurityledger -->» |
Wannacry APT 28 APT 3 | |||
| 2017-05-17 22:29:31 | (Déjà vu) Adylkuzz Crytocurrency Miner Is Not The Next WannaCry (lien direct) | Adylkuzz impact and prevalence is much lower than WannaCry | Wannacry | |||
| 2017-05-17 22:29:31 | (Déjà vu) Adylkuzz Cryptocurrency Miner Is Not The Next WannaCry (lien direct) | Adylkuzz impact and prevalence is much lower than WannaCry | Wannacry | |||
| 2017-05-17 21:08:20 | ESET Ireland\'s Top 8 Tips For Preventing \'WannaCry\' Ransomware Attack (lien direct) | The ISBuzz Post: This Post ESET Ireland's Top 8 Tips For Preventing 'WannaCry' Ransomware Attack | Wannacry | |||
| 2017-05-17 19:28:37 | Patching WannaCrypt: Dispatches from the frontline (lien direct) | The WannaCrypt ransomware exploit is wreaking havoc around the world. This is a first-hand perspective of how one company kept the threat under control. | Wannacry | |||
| 2017-05-17 19:15:57 | WannaCry FAQ - Take-aways and Learnings (lien direct) | WannaCry FAQ: How does WannaCry spread? WannaCry has multiple ways of spreading. Its primary method is to use the Backdoor.Double.Pulsar backdoor exploit tool released last March by the hacker group known as Shadow Brokers, and managed to infect thousands of Microsoft Windows computers in only a few weeks. Because DoublePulsar runs in kernel mode, it grants hackers a high level of control over the compromised computer system. | Wannacry | |||
| 2017-05-17 18:13:00 | How WannaCrypt attacks (lien direct) | WannaCrypt's roots -- the malware behind world's biggest ransomware attack ever -- lie in an old Windows network protocol. | Wannacry | |||
| 2017-05-17 17:19:30 | Next NSA Exploit Payload Could be Much Worse Than WannaCry (lien direct) | Researchers urge Windows admins to apply MS17-010 before the next attack using the EternalBlue NSA exploit deploys a worse payload than WannaCry ransomware. | Wannacry | |||
| 2017-05-17 17:06:55 | WannaCry Ransomware Creators Make Rookie Mistake (lien direct) | WannaCry Ransomware Didn't Utilize Trackable Bitcoin Wallets | Wannacry | |||
| 2017-05-17 16:05:51 | WannaCry : Etat des lieux à J+5 – Commentaire Avast (lien direct) |  Cinq jours après la cyberattaque qui a déjà touché 150 pays dans le monde et fait plus de 250Â 000 victimes, Jakub Kroustek, Threat Lab Team Lead, chez Avast, revient sur les données observées au fil des heures et les questions concrètes qui s'y rapportent. Communiqué de presse – Le vendredi après-midi, plus de 50 000 […] Cinq jours après la cyberattaque qui a déjà touché 150 pays dans le monde et fait plus de 250Â 000 victimes, Jakub Kroustek, Threat Lab Team Lead, chez Avast, revient sur les données observées au fil des heures et les questions concrètes qui s'y rapportent. Communiqué de presse – Le vendredi après-midi, plus de 50 000 […] |
Guideline | Wannacry | ||
| 2017-05-17 14:31:09 | Lessons Learned From the WannaCry Ransomware Attack and Many Others That Preceded It (lien direct) | The best strategy to defend against the WannaCry ransomware attack and similar events is to adopt tools to prevent them from occurring in the first place. | Wannacry | |||
| 2017-05-17 14:30:17 | WannaCry: What It Is And What To Do About It (lien direct) | The ISBuzz Post: This Post WannaCry: What It Is And What To Do About It | Wannacry | |||
| 2017-05-17 14:01:56 | After WannaCry, UIWIX Ransomware and Monero-Mining Malware Follow Suit (lien direct) | WannaCry ransomware's outbreak during the weekend was mitigated by having its kill switch domain registered. It was only a matter of time, however, for other cybercriminals to follow suit. Case in point: the emergence of UIWIX ransomware (detected by Trend Micro as RANSOM_UIWIX.A) and two notable Trojans our sensors detected. Post from: Trendlabs Security Intelligence Blog - by Trend Micro After WannaCry, UIWIX Ransomware and Monero-Mining Malware Follow Suit | Wannacry | |||
| 2017-05-17 13:14:06 | Cryptocurrency-mining malware cashes in on NSA exploit that enabled WannaCry (lien direct) | WannaCry continues to hit headlines, but it's not the first piece of malware to make use of the NSA's EternalBlue exploit |
Wannacry | |||
| 2017-05-17 13:00:11 | Check Point Reveals Global WannaCry Ransomware Infection Map at CPX Europe 2017 (lien direct) | Check Point researchers have been investigating the ransomware campaign in detail since it was first reported. With a new Check Point WannaCry Ransomware Infection Map, the researchers were able to track 34,300 attack attempts in 97 countries. The average pace as of today is one attempt in every three second – indicating a slight decline […] | Wannacry | |||
| 2017-05-17 13:00:00 | Basic Best Practices for Securing LDAP and Active Directory with Red Hat (lien direct) | In the enterprise, it's very popular to manage Windows client PCs through Red Hat servers. This sort of configuration is especially common in healthcare and the financial services industries. Red Hat Enterprise Linux (RHEL) has good software for working with Windows Active Directory. Red Hat Enterprise Linux can also manage clients with multiple platforms, such as Windows, OS X, Android, and other Linux distributions with OpenLDAP, an opensource implementation of the Lightweight Directory Access Protocol (LDAP). Cyber threats are now more common than ever, so it's crucial to be mindful of security when installing and configuring an LDAP application. You should not only be concerned with information security policy compliance; you should go above and beyond compliance whenever possible without restricting necessary functionality. This is a brief guide on how to use LDAP in Red Hat in a secure way. Your network and enterprise computing needs may be very complex, as can the specific security policies, government and industry regulations you must abide by. This piece only covers some fundamental basics. Think of it as a starting point, a 101 guide for a network administrator. The information here applies to Red Hat Enterprise Linux 6 and 7. There are multiple basic ways to configure RHEL servers with Windows Active Directory, depending on how many servers, clients, and domains you have. You also need to know which sorts of functions you need. Do you need file sharing? Do you need to be able to configure user account attributes? Take a whitelisting approach, and only enable the services that you need. These considerations will help you choose which backend you should run in RHEL for Active Directory management. Choosing the appropriate backend for your needs isn't only important for functionality, but also for security. The most frequently implemented backends are Samba implementations which require Winbind. They all support file sharing and login access. idmap_tdb is the default Winbind backend. It's also the simplest to use. It supports both read and write operations. But it must be run from only one RHEL server, and its scalability is limited. idmap_rid can be run from multiple RHEL servers, as can all the backends further down this list. It features algorithmic ID mappings across multiple servers, keeping them consistent across RHEL systems. But it only supports read operations. idmap_ad uses standardized user configuration, and centralized user account management. But it's read-only, and also requires more work for a network administrator as user and group ID attributes must be set within Active Directory. idmap_ldap can keep ID mappings in a non-AD server, such as OpenLDAP. It supports both read and write. Keep in mind that an external LDAP server is required, and it can have a complex configuration because of Samba LDAP mapping limitations. idmap_adex works well with legacy versions of Samba, it's not to be used with recent versions of Samba. It's read-only, and ID mappings are assigned by the administrator. idmap_hash is read-only and has simpler configuration than other Winbind backends that support multiple RHEL servers. Be careful about ID collisions if you choose this backend. idmap_tdb2 supports both read and write operations. Scripting can be used if you perform ID mappings with an external program. But it can only be used with Samba clusters. idmap_nss is read-only and uses pre-existing ID mappings. Keep in mind that it offers no support for trusted domains. Detailed information about choosing a configuration specific to your needs can be found in this guide from Red Hat. Remember that the best practice for security is to choose a configuration that supports all your needs while not enabling services that you'll never use. Remember, take a whitelisting approach. Installing a Kerberos client is optional, but it's a best practice for secure AD | Wannacry | |||
| 2017-05-17 12:00:44 | WannaCryptor wasn\'t the first to use EternalBlue: Miners misused it days after Shadow Brokers leak (lien direct) | The massive campaign that spread the WannaCry ransomware wasn't the only large-scale infection misusing the EternalBlue and DoublePulsar exploits. | Wannacry | |||
| 2017-05-17 08:08:42 | WannaCryptor \'Afterthoughts\'… (lien direct) | …Not that we’re exactly in the post-WannaCryptor era yet. But forgive me if you’ve heard enough of the saga of the ransomware ESET calls Win32/Filecoder.WannaCryptor.D (after just a few days, I certainly have). Craig Williams, of the company Gigabyte IT Solutions on St. Helena, mailed me wondering about my take on the issue.* Here are a […] | Wannacry | |||
| 2017-05-17 08:07:58 | Botnet minier Adylkuzz – Encore plus fort que WannaCry ! (lien direct) |  Tous ceux qui s'étonnaient des faibles gains générés par les cybercriminels à l'origine de WannaCry (estimé à un peu plus de 50 000 dollars), voila que l'on apprend la découverte d'un malware similaire exploitant les mêmes vulnérabilités pour générer massivement des bitcoins. Les gains auraient déjà dépassés le million de dollars ! Tous ceux qui s'étonnaient des faibles gains générés par les cybercriminels à l'origine de WannaCry (estimé à un peu plus de 50 000 dollars), voila que l'on apprend la découverte d'un malware similaire exploitant les mêmes vulnérabilités pour générer massivement des bitcoins. Les gains auraient déjà dépassés le million de dollars ! |
Wannacry | |||
| 2017-05-17 06:50:12 | 3 Security Firms Say WannaCry Ransomware Shares Code with North Korean Malware (lien direct) | While initially, we thought this would be a silly and unsubstantiated discovery, the number of security firms claiming they've identified and confirmed connections between the WannaCry ransomware and malware used by the Lazarus Group has now gone up to three. [...] | Medical | Wannacry APT 38 | ||
| 2017-05-17 06:30:11 | Cryptocurrency-mining malware has been using WannaCry\'s NSA exploit for weeks (lien direct) |  A cryptocurrency-mining malware began exploiting a leaked NSA vulnerability several weeks before WannaCry sank its teeth into it.
David Bisson reports. A cryptocurrency-mining malware began exploiting a leaked NSA vulnerability several weeks before WannaCry sank its teeth into it.
David Bisson reports.
|
Wannacry | |||
| 2017-05-17 06:20:36 | Cyberattaque ransomware mondiale – Les entreprises doivent sécuriser les accès à leurs systèmes critiques (lien direct) |  Les entreprises du monde entier se préparent pour une seconde vague d'attaques de ransomware alors qu'on en est toujours à évaluer les conséquences de l'attaque WannaCry de vendredi. Les entreprises du monde entier se préparent pour une seconde vague d'attaques de ransomware alors qu'on en est toujours à évaluer les conséquences de l'attaque WannaCry de vendredi. |
Wannacry | |||
| 2017-05-17 04:19:00 | DocuSign Data Breach Led to Targeted Email Malware Campaign (lien direct) | While we all were busy in the WannaCry ransomware menace, two separate data breaches have been reported, one in DocuSign, a major provider of electronic signature technology, and another in BELL, Canada's largest telecommunications company.
In a notice on its website on Tuesday, DocuSign confirmed a breach at one of its email systems when investigating the cause of an increase in
|
Wannacry | |||
| 2017-05-17 04:18:36 | Bell Canada Hacked: Data of 1.9 Million Customers Stolen (lien direct) | While we all were busy in the WannaCry ransomware menace, two separate data breaches have been reported, one in DocuSign, a major provider of electronic signature technology, and another in BELL, Canada's largest telecommunications company.
Canadian mobile phone, TV, and internet service provider Bell on Monday confirmed that the company had been hit by an unknown hacker who has managed to
|
Wannacry | |||
| 2017-05-17 03:33:55 | WanaCrypt0r Ransomworm (lien direct) | Written by Sergei Shevchenko and Adrian NishBACKGROUNDSince the release of the ETERNALBLUE exploit by 'The Shadow Brokers' last month security researchers have been watching for a mass attack on global networks. This came on Friday 12th May when it was bundled with ransomware called WanaCrypt0r and let loose. Initial reports of attacks were highlighted by Telefonica in Spain but the malware quickly spread to networks in the UK where the National Health Service (NHS) was impacted, followed by many other networks across the world.The infographic below illustrates the key components of the WanaCrypt0r ransomware. This is described in further detail in subsequent sections of this report along with initial clues on attribution.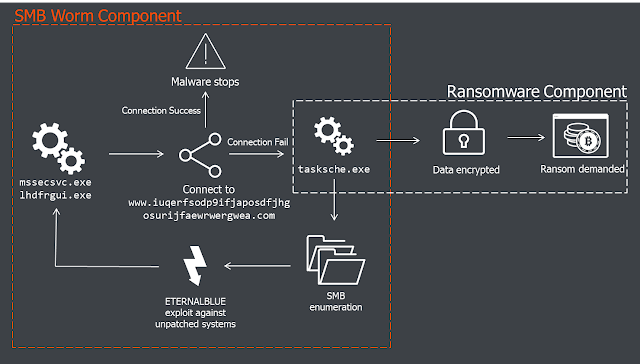 ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs ANALYSIS: Initial VectorThe initial infection vector is still unknown. Reports by some of phishing emails have been dismissed by other researchers as relevant only to a different (unrelated) ransomware campaign, called Jaff.There is also a working theory that initial compromise may have come from SMB shares exposed to the public internet. Results from Shodan show over 1.5 million devices with port 445 open – the attacker could have infected those shares directly.The Dropper/WormThe infection starts from a 3.6Mb executable file named mssecsvc.exe or lhdfrgui.exe. Depending on how it's executed, it can function as a dropper or as a worm.When run, the executable first checks if it can connect to the following URL:http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com The connection is checked with the WinINet functions, shown below: 01 qmemcpy(&szUrl, 02 "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com", 03 57u); 04 h1 = InternetOpenA(0,&nbs |
Guideline Medical | Wannacry APT 38 | ||
| 2017-05-17 02:22:51 | Après WannaCry, voici Adylkuzz, la cyberattaque qui fait de l\'argent sur votre dos (lien direct) | Des chercheurs en sécurité ont découvert l'existence d'une autre attaque de grande ampleur utilisant le même exploit que WannaCry mais de manière plus discrète.  |
Wannacry | |||
| 2017-05-16 23:25:32 | WannaCry: the ransomware worm that didn\'t arrive on a phishing hook (lien direct) | Email doesn't seem to have been the initial vector for WannaCry, which initially took hold in south-east Asia |
Wannacry | |||
| 2017-05-16 21:40:00 | WannaCry\'s \'Kill Switch\' May Have Been a Sandbox-Evasion Tool (lien direct) | Massive ransomware worm attack appears to have come with a poorly planned anti-analysis feature. | Wannacry | |||
| 2017-05-16 20:30:04 | WannaCry – Cyber Attack (lien direct) | The ISBuzz Post: This Post WannaCry – Cyber Attack | Wannacry | |||
| 2017-05-16 17:53:42 | WannaCry, et si ce n\'était que la partie immergée de l\'iceberg ? (lien direct) |  Depuis vendredi dernier, plus de 300 000 ordinateurs dans 150 pays ont été touchés lors de la plus grande opération de cyber-extorsion à ce jour. Renault, Vodafone, FedEx, ministère de l'Intérieur russe, la Deutsche Bahn ou encore les NHS se sont fait pirater dans cette vague de cyberattaques sans précédent. De quoi s’agit-il ? À […] Depuis vendredi dernier, plus de 300 000 ordinateurs dans 150 pays ont été touchés lors de la plus grande opération de cyber-extorsion à ce jour. Renault, Vodafone, FedEx, ministère de l'Intérieur russe, la Deutsche Bahn ou encore les NHS se sont fait pirater dans cette vague de cyberattaques sans précédent. De quoi s’agit-il ? À […] |
FedEx Wannacry | |||
| 2017-05-16 17:05:04 | NSA\'s EternalBlue Exploit Fully Ported to Metasploit (lien direct) | The National Security Agency (NSA)-linked EternalBlue exploit that became well known after being used in a recent global ransomware campaign has been ported to the popular Metasploit penetration testing Framework. | Wannacry | |||
| 2017-05-16 16:48:44 | CRYING IS FUTILE: SandBlast Forensic Analysis of WannaCry (lien direct) | Using the NSA exploit EternalBlue released by the Shadow Brokers, the WannaCry ransomware developers have added their names to malware lore. Given the number of institutions hit and the amount of media generated, it seemed appropriate to show what the ransomware actually does on a system through our SandBlast Agent Forensics product. The WannaCry outbreak […] | Wannacry | |||
| 2017-05-16 15:45:50 | WannaCry Shares Code with Lazarus APT Samples (lien direct) | Experts have confirmed there are similarities between code used by the ransomware WannaCry and the Lazarus APT. | Wannacry APT 38 | |||
| 2017-05-16 15:08:06 | Check-EternalBlue: Is your PC patched against the WannaCryptor worm vulnerability? (lien direct) | In this post, ESET's Cassius Puodzius addresses what we can learn from WannaCryptor ransomware attack, and what we can expect. | Wannacry | |||
| 2017-05-16 14:06:11 | Industry Reactions to WannaCry Ransomware Attacks (lien direct) | The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has infected more than 200,000 devices worldwide. The attacks affected banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants. | Wannacry | |||
| 2017-05-16 13:32:53 | North Korea Possibly Behind WannaCry Ransomware Attacks (lien direct) | An earlier WannaCry ransomware sample shows code similarities with malware used by a North Korea-linked hacking group responsible for multiple financial and destructive attacks, security researchers say. | Wannacry | |||
| 2017-05-16 13:05:28 | People Are Photoshopping WannaCry Ransom Notes on Everything with a Screen (lien direct) | It only took one troll to photoshop one image to get the ball rolling. Now we have all sorts of craziness, ranging from pregnancy tests to the Star Trek Enterprise. [...] | Wannacry | |||
| 2017-05-16 13:00:00 | Innovation for the Sake of Innovation (lien direct) |
“Perfection is finally attained not when there is no longer anything to add, but when there is no longer anything to take away.” - Antoine de Exupery
In today’s world, it feels as if innovation has become the curse of many companies. It forces changes, and wheels being reinvented when not needed, out of fear that lack of innovation will be perceived as stagnation.
In addition, innovation for the sake of innovation can lead to security issues. These issues manifest predominantly in one of two ways:
Scope Creep The first is one of scope creep and the introduction of vulnerabilities through hurried and unplanned changes. For example, adding a new set of fields onto a web application at the last minute often results in an over-worked developer hastily cobbling together code to incorporate functionality. This can lead to inadequate testing and vulnerabilities being introduced.
But not all scope creep is rapid. Sometimes functionality is added slowly over time. What starts off life as a simple workflow ends up being a Frankenstein-esque corporate accounting, inventory, and pricing platform running the entire company.
The fundamental problem is that there is little linking of ideas from a brainstorm with reality. Often times things that are 'nice to have' are just that, only nice to have. There’s no need to invest in a shiny box that will add artificial intelligence to your security team, if you don't already have the basics mapped out.
Because we can The second issue which comes about from ‘innovation for the sake of innovation’ is the introduction of features not out of need, but rather because they are available.
The ever-increasing number of smart-devices are a good example of these. Just because it is possible to connect wirelessly to a kettle, a toaster, or a pillow, it doesn’t necessarily mean that it is a good idea.
In security teams, we often see this manifest in many ways. For example, keeping each and every log generated by every device is a good idea for investigations or to rebuild timelines. But is it really necessary for everything? Why not scope out and only store full logs for critical systems and strip away the noise.
Or why build a fraud detection system when the threat of fraud against your business is low.
 The user experience Anytime there are new features or functionality added, user experience takes a hit. Even ‘good’ updates require users to learn new menu commands, alter their workflow, or simply having to retrain muscle memory to click on a different part of the screen.
But more so, it can disrupt the natural use of a product or technology. For example, an email client should be an email client. When it morphs into an all-singing-all-dancing CRM with context-aware reminders, and bluetooth enabled functionality, one wonders whether the product is actually an email client at all.
Security is not immune to these problems. Whether these be in-house scripts that evolve into a homegrown SOC, or enabling of additional capabilities - it adds unnecessary complexity and confusion.
The impact of such security changes is amplified when they impact the end user. Password reset policies, multi-factor authentication, phishing exercises, etc. all add to the mental workload of the users.
Technology, and by extension security, shouldn’t need to go through innovation for the sake of innovation. While arguments can be made for the progress such innovation brings, the risks often-times outweigh the pros.
Instead, I propose technology be put on an ‘Atkins diet’ of decluttering. While there are many intricacies to decluttering, they can be broken down into two broad steps:
The user experience Anytime there are new features or functionality added, user experience takes a hit. Even ‘good’ updates require users to learn new menu commands, alter their workflow, or simply having to retrain muscle memory to click on a different part of the screen.
But more so, it can disrupt the natural use of a product or technology. For example, an email client should be an email client. When it morphs into an all-singing-all-dancing CRM with context-aware reminders, and bluetooth enabled functionality, one wonders whether the product is actually an email client at all.
Security is not immune to these problems. Whether these be in-house scripts that evolve into a homegrown SOC, or enabling of additional capabilities - it adds unnecessary complexity and confusion.
The impact of such security changes is amplified when they impact the end user. Password reset policies, multi-factor authentication, phishing exercises, etc. all add to the mental workload of the users.
Technology, and by extension security, shouldn’t need to go through innovation for the sake of innovation. While arguments can be made for the progress such innovation brings, the risks often-times outweigh the pros.
Instead, I propose technology be put on an ‘Atkins diet’ of decluttering. While there are many intricacies to decluttering, they can be broken down into two broad steps:
 Simplify When looking at your
Simplify When looking at your |
Guideline | Wannacry |
To see everything:
Our RSS (filtrered)
