What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2020-03-17 08:58:05 | NBlog March 17 - COVID-19 BCM (lien direct) |  From my narrow perspective as a practitioner, manager and consultant in the field, some 20-30 years ago, Business Continuity Planning revolved around IT Disaster Recovery which generally involved (at the time) either powering up an alternative data centre or hiring a few servers on the back of a truck and plugging them in to restore services taken out when the data centre was flooded/burnt. It was almost entirely IT focused, expensive, and could cope with very few disaster scenarios (there still had to be somewhere for the truck to park up and plug in, while the backups to be restored had to have survived miraculously, plus of course the rest of the organization - including the alternative data centre plus the people and associated essential services).From that primitive origin, BCP started to get better organised, with scenario planning and tabletop exercises, and actual 'management' instead of just 'planning' - leading to Business Continuity Management. The scenarios expanded, and before long organisations realised that they couldn't reasonably plan and prepare playbooks for every possible situation, every single risk. Also, the process linkages with incident management grew stronger, including the shortcuts necessary to escalate serious incidents, authorise and initiate significant responses quickly etc. Oh and warm-site and hot-site concepts appeared, along with Recovery Time Objective, Recovery Point Objective and a few other basic metrics. Then, about 10 to 15 years ago, resilience popped out of the ether as a supplement for IT DR and other recovery approaches, the idea being to do whatever it takes to maintain essential services supporting essential business processes. Even today, some organisations struggle with this concept, and yet "high availability" systems and networks, dual-live/distributed systems, load-sharing, multi-sourced supplies, customer diversity etc. are reasonably straightforward and generally-accepted concepts. I guess they have trouble joining the dots - particularly in the area of workforce resilience, and the cultural aspects of "We WILL get through this: now, what can I do to help? Here, hold my beer ..." During the past 10 years or so, true contingency approaches have appeared, in some organizations at least, partly in rec From my narrow perspective as a practitioner, manager and consultant in the field, some 20-30 years ago, Business Continuity Planning revolved around IT Disaster Recovery which generally involved (at the time) either powering up an alternative data centre or hiring a few servers on the back of a truck and plugging them in to restore services taken out when the data centre was flooded/burnt. It was almost entirely IT focused, expensive, and could cope with very few disaster scenarios (there still had to be somewhere for the truck to park up and plug in, while the backups to be restored had to have survived miraculously, plus of course the rest of the organization - including the alternative data centre plus the people and associated essential services).From that primitive origin, BCP started to get better organised, with scenario planning and tabletop exercises, and actual 'management' instead of just 'planning' - leading to Business Continuity Management. The scenarios expanded, and before long organisations realised that they couldn't reasonably plan and prepare playbooks for every possible situation, every single risk. Also, the process linkages with incident management grew stronger, including the shortcuts necessary to escalate serious incidents, authorise and initiate significant responses quickly etc. Oh and warm-site and hot-site concepts appeared, along with Recovery Time Objective, Recovery Point Objective and a few other basic metrics. Then, about 10 to 15 years ago, resilience popped out of the ether as a supplement for IT DR and other recovery approaches, the idea being to do whatever it takes to maintain essential services supporting essential business processes. Even today, some organisations struggle with this concept, and yet "high availability" systems and networks, dual-live/distributed systems, load-sharing, multi-sourced supplies, customer diversity etc. are reasonably straightforward and generally-accepted concepts. I guess they have trouble joining the dots - particularly in the area of workforce resilience, and the cultural aspects of "We WILL get through this: now, what can I do to help? Here, hold my beer ..." During the past 10 years or so, true contingency approaches have appeared, in some organizations at least, partly in rec |
Guideline | |||
| 2020-02-29 16:46:00 | NBlog March - InfoSec 101 module released (lien direct) |  Whereas usually our awareness and training modules focus in some depth on one of the 70 information security topics in our portfolio, Information Security 101 is a broad but shallow module. It is intended to bring workers quickly up to speed on the basics of information risk and security during security induction courses, for periodic refresher training, or when launching an awareness program.As soon as a new worker arrives, they start absorbing and being assimilated into the corporate culture, picking up 'the way we do things here'. Sensible organizations run orientation sessions to welcome newcomers and kick-start the cultural integration. Whereas usually our awareness and training modules focus in some depth on one of the 70 information security topics in our portfolio, Information Security 101 is a broad but shallow module. It is intended to bring workers quickly up to speed on the basics of information risk and security during security induction courses, for periodic refresher training, or when launching an awareness program.As soon as a new worker arrives, they start absorbing and being assimilated into the corporate culture, picking up 'the way we do things here'. Sensible organizations run orientation sessions to welcome newcomers and kick-start the cultural integration.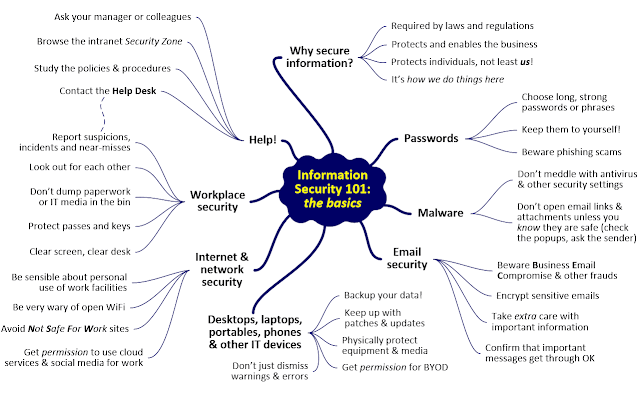 InfoSec 101 covers common information risks (e.g. malware) and information security controls (e.g.& antivirus). The materials are deliberately succinct, outlining key aspects without delving into the details. We're not trying to tell workers everything about information risk and security all at once but to set them off on the right foot, engaging them as integral and valuable parts of the organisation's Information Security Management System. It's a gentle introduction, more splash in the paddling pool than high dive at the deep end!First impressions matter, so the module helps Information Security, HR or training professionals deliver interesting and engaging awareness sessions accompanied by impressive, top-quality supporting materials. Establishing personal contacts throughout the organization gradually expands the Information Security team across the enterprise - more 'eyes and ears' out there. This alone would be well worth the investment!As well as induction or orientation purposes, InfoSec InfoSec 101 covers common information risks (e.g. malware) and information security controls (e.g.& antivirus). The materials are deliberately succinct, outlining key aspects without delving into the details. We're not trying to tell workers everything about information risk and security all at once but to set them off on the right foot, engaging them as integral and valuable parts of the organisation's Information Security Management System. It's a gentle introduction, more splash in the paddling pool than high dive at the deep end!First impressions matter, so the module helps Information Security, HR or training professionals deliver interesting and engaging awareness sessions accompanied by impressive, top-quality supporting materials. Establishing personal contacts throughout the organization gradually expands the Information Security team across the enterprise - more 'eyes and ears' out there. This alone would be well worth the investment!As well as induction or orientation purposes, InfoSec |
Guideline | |||
| 2020-02-19 18:03:26 | NBlog Feb 19 - Brahms and Liszt (lien direct) |  Fueled by a lot of Brahms and a wee tot of rum, half an hour's idle brainstorming on the purpose and objectives for information security awareness generated the following little Liszt:Rites, ritualsRite of passageRitual slaughterReligionsBelief systems Cult, visionary leader, positional power, faithSheep, lemmingsWolves, packs, threats, skillsGroup-think, conformityCompliance, rules, constraints, in the boxIndividuality, creativity, nonconformity, freedom, out of the boxHippies, communes, cliquesHallucinogensNoncomplianceCultural norms, expectationsCounter-cultural, bucking trendsConventions, habits, preferencesAutomatic behaviours, instinctsSocialising infosecSocial pressure, influence, shared valuesSocial acceptabilitySocial structures, hierarchies, linksNetworks and relationshipsFamilies, organizations, departments, teams, groups, cliquesNationsInteractions Fueled by a lot of Brahms and a wee tot of rum, half an hour's idle brainstorming on the purpose and objectives for information security awareness generated the following little Liszt:Rites, ritualsRite of passageRitual slaughterReligionsBelief systems Cult, visionary leader, positional power, faithSheep, lemmingsWolves, packs, threats, skillsGroup-think, conformityCompliance, rules, constraints, in the boxIndividuality, creativity, nonconformity, freedom, out of the boxHippies, communes, cliquesHallucinogensNoncomplianceCultural norms, expectationsCounter-cultural, bucking trendsConventions, habits, preferencesAutomatic behaviours, instinctsSocialising infosecSocial pressure, influence, shared valuesSocial acceptabilitySocial structures, hierarchies, linksNetworks and relationshipsFamilies, organizations, departments, teams, groups, cliquesNationsInteractions |
Guideline | |||
| 2020-01-30 11:02:19 | NBlog Jan 30 - simplicity itself (lien direct) |  "Simplicity is the default unless there's a good business reason to do something else. What is typically lacking are the business reasons ..."That comment on CISSPforum set me pondering during this morning's caffeine fix. We've been chatting about some training webinar sessions recently promoted by (ISC)2. Some say they over-simplify information security to the point of trivialising and perhaps misleading people.If you follow NBlog, you'll know that this month I have been slaving away on an awareness module covering malware, a topic we've covered many times before - particularly the avoidance or prevention of infections but this year a customer asked us for something on publicly disclosing incidents in progress, a disarmingly simple request that turned into a fascinating foray into the post-malware-infection incident management and resolution phase for a change. I've been exploring and writing about what does, could or should happen after malware 'hits' - from that dramatic moment the ransomware demands appear on everyone's screens, for example. What follows is quite an intricate and frantic dance, in fact, involving management, IT and other staff, customers, suppliers and partners, regulators/authorities, journalists and the news + social media etc. plus the Incident Management Team, infosec and business continuity pros trying to keep everything on track, the legal team figuring out who to sue, the compliance pros wondering how not to get sued, and various hired-hands helping with forensics, disinfection and finding then retrospectively plugging whatever holes were initially exploited by the malware. All the while, the menacing hackers and cybercrims are wielding big coshes in the shape of threats to make the disruption permanent and terminal, and/or to disclose whatever juicy tidbits of corporate and personal info they've previously stolen (the CEO's emails, or browser history perhaps?). And all the while the systems, data, business processes/activities, websites and apps are being maintained, recovered or restored. Brands and relationships are under pressure, along with all the dancers. It's an intensely stressful time for them, I'm sure. The approach we've taken is to explore the timeline of an actual incident, in real time as it happens (as it happens), building a case study around the ongoing Travelex ransomware incident: the sequence forms a convenient thread to lead people through the story, thinking about what's going on at each stage and imagining how it would be if a similar incident happened 'here'. I've drawn up a simplified Travelex incident timeline in the same style as the one I drew for the Sony Pictures Entertainment fiasco 5 years back, pointing out some of the key events plus the phases of the overall process. The new Travelex version ('in press'!) is simpler "Simplicity is the default unless there's a good business reason to do something else. What is typically lacking are the business reasons ..."That comment on CISSPforum set me pondering during this morning's caffeine fix. We've been chatting about some training webinar sessions recently promoted by (ISC)2. Some say they over-simplify information security to the point of trivialising and perhaps misleading people.If you follow NBlog, you'll know that this month I have been slaving away on an awareness module covering malware, a topic we've covered many times before - particularly the avoidance or prevention of infections but this year a customer asked us for something on publicly disclosing incidents in progress, a disarmingly simple request that turned into a fascinating foray into the post-malware-infection incident management and resolution phase for a change. I've been exploring and writing about what does, could or should happen after malware 'hits' - from that dramatic moment the ransomware demands appear on everyone's screens, for example. What follows is quite an intricate and frantic dance, in fact, involving management, IT and other staff, customers, suppliers and partners, regulators/authorities, journalists and the news + social media etc. plus the Incident Management Team, infosec and business continuity pros trying to keep everything on track, the legal team figuring out who to sue, the compliance pros wondering how not to get sued, and various hired-hands helping with forensics, disinfection and finding then retrospectively plugging whatever holes were initially exploited by the malware. All the while, the menacing hackers and cybercrims are wielding big coshes in the shape of threats to make the disruption permanent and terminal, and/or to disclose whatever juicy tidbits of corporate and personal info they've previously stolen (the CEO's emails, or browser history perhaps?). And all the while the systems, data, business processes/activities, websites and apps are being maintained, recovered or restored. Brands and relationships are under pressure, along with all the dancers. It's an intensely stressful time for them, I'm sure. The approach we've taken is to explore the timeline of an actual incident, in real time as it happens (as it happens), building a case study around the ongoing Travelex ransomware incident: the sequence forms a convenient thread to lead people through the story, thinking about what's going on at each stage and imagining how it would be if a similar incident happened 'here'. I've drawn up a simplified Travelex incident timeline in the same style as the one I drew for the Sony Pictures Entertainment fiasco 5 years back, pointing out some of the key events plus the phases of the overall process. The new Travelex version ('in press'!) is simpler |
Ransomware Malware Guideline | |||
| 2020-01-29 05:23:20 | NBlog Jan 25 - data privacy day (lien direct) |  On Tuesday, data privacy day, privacy will be top of the agenda.Well, OK, not top exactly, not even very high if I'm honest.And apart from mine, I'm not sure whose agenda I'm talking about.Evidently it's about "data privacy", not other kinds of privacy, oh no.If I'm coming across just a little cynically, then evidently I need to try harder.I bumped into data privacy day while searching for something privacy related - I forget exactly what, now. Otherwise, it would surely have passed me by, and maybe you too, dear blog reader.Anyway, data privacy day appears to date back to Jan 28th 1981 when Convention 108 was signed in conventional Europe. "The Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data" was among the first, if not the very first, data protection regulation, predating today's privacy laws and regs.In 2006, the Council of Europe launched Data Privacy Day as an annual event on January 28th.Data privacy day was later taken up by some American organizations. On Tuesday, data privacy day, privacy will be top of the agenda.Well, OK, not top exactly, not even very high if I'm honest.And apart from mine, I'm not sure whose agenda I'm talking about.Evidently it's about "data privacy", not other kinds of privacy, oh no.If I'm coming across just a little cynically, then evidently I need to try harder.I bumped into data privacy day while searching for something privacy related - I forget exactly what, now. Otherwise, it would surely have passed me by, and maybe you too, dear blog reader.Anyway, data privacy day appears to date back to Jan 28th 1981 when Convention 108 was signed in conventional Europe. "The Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data" was among the first, if not the very first, data protection regulation, predating today's privacy laws and regs.In 2006, the Council of Europe launched Data Privacy Day as an annual event on January 28th.Data privacy day was later taken up by some American organizations. |
Guideline | |||
| 2020-01-27 16:54:17 | NBlog Jan 27 - MD/CISO\'s question time (lien direct) |  Seems I'm not the only ravenous shark circling the Travelex ransomware incident.Over at the Institute of Chartered Accountants in England and Wales website, Kirstin Gillon points out there are learning opportunities for senior management in this "horror story".Specifically, Kirstin suggests posing six awkward questions of those responsible for managing incidents and risks of this nature ... Seems I'm not the only ravenous shark circling the Travelex ransomware incident.Over at the Institute of Chartered Accountants in England and Wales website, Kirstin Gillon points out there are learning opportunities for senior management in this "horror story".Specifically, Kirstin suggests posing six awkward questions of those responsible for managing incidents and risks of this nature ... Rhetorical questions of this nature are not a bad way to get management thinking and talking about the important issues arising - a valuable activity in its own right although it falls some way short of taking decisions leading to appropriate action. Admittedly, there's an art to framing and posing such questions. Kirstin's questions are along the right lines, a good starting point at least.Faced with such questions, some Boards and management teams will immediately 'get it', initiating further work to explore the issues, evaluate the risks and controls more deeply, and if appropriate propose corrective actions to a Rhetorical questions of this nature are not a bad way to get management thinking and talking about the important issues arising - a valuable activity in its own right although it falls some way short of taking decisions leading to appropriate action. Admittedly, there's an art to framing and posing such questions. Kirstin's questions are along the right lines, a good starting point at least.Faced with such questions, some Boards and management teams will immediately 'get it', initiating further work to explore the issues, evaluate the risks and controls more deeply, and if appropriate propose corrective actions to a |
Ransomware Malware Guideline | |||
| 2020-01-24 08:37:48 | NBlog Jan 24 - information, data, knowledge And All That (lien direct) |  On the ISO27k Forum lately we've been discussing something that comes up repeatedly, a zombie topic you could say since the discussion is never really settled to everyone's complete satisfaction. There's always more to say.The discussion concerns the disarmingly simple phrase "information asset", used in some but no longer defined in any of the ISO27k standards. Among other things, we've discussed whether people/workers can be classed as information assets, hence information risks associated with people potentially fall within scope of an ISO27k ISMS.Yesterday, Mat said:"Knowledge is generally broken down into three different types - explicit, implicit, and tacit. When we are talking about classing employees as an asset or simply treating the information that they know as an asset, I think maybe this can be broken down further using these different knowledge types. Explicit knowledge is knowledge that is easily transferable, can be recorded and stored. Things like standard work instructions, guides, procedures, policies. Due to the nature of this information, it seems obvious to class the information itself as the asset here - you can mitigate the risk of information loss simply by recording the information. Implicit knowledge is the practical application of explicit knowledge. This can include knowing your way around a particular security product, or a particular piece of equipment. This type of knowledge is difficult to record, however, things like best practices are the best attempt although it's difficult to include the entire background knowledge of the best practice. Due to this, loss of this information is difficult to completely mitigate, and hence, I think the employee here could be classed as the information asset. The best mitigation is to keep the employee. Tacit knowledge is the practical application of implicit knowledge. Examples of this are knowing not only a particu On the ISO27k Forum lately we've been discussing something that comes up repeatedly, a zombie topic you could say since the discussion is never really settled to everyone's complete satisfaction. There's always more to say.The discussion concerns the disarmingly simple phrase "information asset", used in some but no longer defined in any of the ISO27k standards. Among other things, we've discussed whether people/workers can be classed as information assets, hence information risks associated with people potentially fall within scope of an ISO27k ISMS.Yesterday, Mat said:"Knowledge is generally broken down into three different types - explicit, implicit, and tacit. When we are talking about classing employees as an asset or simply treating the information that they know as an asset, I think maybe this can be broken down further using these different knowledge types. Explicit knowledge is knowledge that is easily transferable, can be recorded and stored. Things like standard work instructions, guides, procedures, policies. Due to the nature of this information, it seems obvious to class the information itself as the asset here - you can mitigate the risk of information loss simply by recording the information. Implicit knowledge is the practical application of explicit knowledge. This can include knowing your way around a particular security product, or a particular piece of equipment. This type of knowledge is difficult to record, however, things like best practices are the best attempt although it's difficult to include the entire background knowledge of the best practice. Due to this, loss of this information is difficult to completely mitigate, and hence, I think the employee here could be classed as the information asset. The best mitigation is to keep the employee. Tacit knowledge is the practical application of implicit knowledge. Examples of this are knowing not only a particu |
Guideline | |||
| 2020-01-22 09:00:00 | NBlog Jan 22 - further lessons from Travelex (lien direct) |  At the bottom of a Travelex update on their incident, I spotted this yesterday:Customer PrecautionsBased on the public attention this incident has received, individuals may try to take advantage of it and attempt some common e-mail or telephone scams. Increased awareness and vigilance are key to detecting and preventing this type of activity. As a precaution, if you receive a call from someone claiming to be from Travelex that you are not expecting or you are unsure about the identity of a caller, you should end the call and call back on 0345 872 7627. If you have any questions or believe you have received a suspicious e-mail or telephone call, please do not hesitate to contact us. Although I am not personally aware of any such 'e-mail or telephone scams', Travelex would know better than me - and anyway even if there have been no scams as yet, the warning makes sense: there is indeed a known risk of scammers exploiting major, well-publicised incidents such as this. We've seen it before, such as fake charity scams taking advantage of the public reaction to natural disasters such as the New Orleans floods, and - who knows - maybe the Australian bushfires.At the same time, this infosec geek is idly wondering whether the Travelex warning message and web page are legitimate. It is conceivable that the cyber-criminals and hackers behind the ransomware incident may still have control of the Travelex domains, webservers and/or websites, perhaps all their corporate comms including the Travelex Twitter feeds and maybe even the switchboard behind that 0345 number. I'm waffling on about corporate identity theft, flowing on from the original incident.I appreciate the scenario I'm postulating seems unlikely but bear with me and my professional paranoia for a moment. Let's explore the hypot At the bottom of a Travelex update on their incident, I spotted this yesterday:Customer PrecautionsBased on the public attention this incident has received, individuals may try to take advantage of it and attempt some common e-mail or telephone scams. Increased awareness and vigilance are key to detecting and preventing this type of activity. As a precaution, if you receive a call from someone claiming to be from Travelex that you are not expecting or you are unsure about the identity of a caller, you should end the call and call back on 0345 872 7627. If you have any questions or believe you have received a suspicious e-mail or telephone call, please do not hesitate to contact us. Although I am not personally aware of any such 'e-mail or telephone scams', Travelex would know better than me - and anyway even if there have been no scams as yet, the warning makes sense: there is indeed a known risk of scammers exploiting major, well-publicised incidents such as this. We've seen it before, such as fake charity scams taking advantage of the public reaction to natural disasters such as the New Orleans floods, and - who knows - maybe the Australian bushfires.At the same time, this infosec geek is idly wondering whether the Travelex warning message and web page are legitimate. It is conceivable that the cyber-criminals and hackers behind the ransomware incident may still have control of the Travelex domains, webservers and/or websites, perhaps all their corporate comms including the Travelex Twitter feeds and maybe even the switchboard behind that 0345 number. I'm waffling on about corporate identity theft, flowing on from the original incident.I appreciate the scenario I'm postulating seems unlikely but bear with me and my professional paranoia for a moment. Let's explore the hypot |
Ransomware Malware Patching Guideline | APT 15 | ||
| 2020-01-18 09:00:04 | NBlog Jan 18 - business discontinuity (lien direct) |  As if following a cunning plan (by sheer conicidence, in fact) and leading directly on from my last two bloggings about business continuity exercises, Belgian manufacturing company Picanol suffered a ransomware infection this week, disabling its IT and halting production of high-tech weaving machines at its facilities in Ypres, Romania and China.Fortunately, Picanol's corporate website is still up and running thanks to Webhosting.be, hence management was able to publish this matter-of-fact press release about the incident: As if following a cunning plan (by sheer conicidence, in fact) and leading directly on from my last two bloggings about business continuity exercises, Belgian manufacturing company Picanol suffered a ransomware infection this week, disabling its IT and halting production of high-tech weaving machines at its facilities in Ypres, Romania and China.Fortunately, Picanol's corporate website is still up and running thanks to Webhosting.be, hence management was able to publish this matter-of-fact press release about the incident: Unsurprisingly, just a few short days after it struck, technical details about the "massive ransomware attack" are sparse at this point. The commercial effects, though, are deemed serious enough for trading in its shares to have been suspended on the Brussels bourse. There's already plenty of information here for a case study in February's awareness module. Through a brief scenario and a few rhetorical questions, we'll prompt workers to consider the implications both for Picanol and for their own organizations. If a similar malware incident occurred here, knocking out IT and production for at lea Unsurprisingly, just a few short days after it struck, technical details about the "massive ransomware attack" are sparse at this point. The commercial effects, though, are deemed serious enough for trading in its shares to have been suspended on the Brussels bourse. There's already plenty of information here for a case study in February's awareness module. Through a brief scenario and a few rhetorical questions, we'll prompt workers to consider the implications both for Picanol and for their own organizations. If a similar malware incident occurred here, knocking out IT and production for at lea |
Ransomware Malware Studies Guideline | |||
| 2020-01-06 19:24:42 | NBlog Jan 6 - post-malware-incident notification & other stuff (lien direct) |  A couple of days ago here on NBlog I wrote: "One screamingly-obvious lesson from the rash of ransomware incidents is that we need to anticipate malware infections when the preventive controls fail, which means strengthening the security protecting our business-critical systems and being ready to recover IT services and data efficiently following incidents." That's not all.Anticipating that, despite all we do to prevent them, malware infections are still likely to occur implies the need for several post-event controls. These are the kinds of controls I have in mind:Reliable, efficient, effective, top-quality incident response and management processes - in particular, speed is almost always of the essence in malware incidents, and the responses need to be well-practiced - not just the run-of-the-mill routine infections but the more extreme/serious "outbreaks";Decisive action is required, with strong leadership, clear roles and responsibilities, and of course strong awareness and training both for the response team and for the wider organization;Clarity around priorities for action e.g. halt the spread, assess the damage, find the source/cause, recover;Technological controls, of course, such as network segmentation (part of network architectural design), traffic filtering and (reliable!) isolation of segments pending their being given the all-clear;Clarity around priorities for reporting including rapid escalation and ongoing progress updates, in parallel with the other activities;Forensics, where appropriate, feasible and helpful (e.g. which preventive controls failed, why, and what if anything can be done to strengthen them); A couple of days ago here on NBlog I wrote: "One screamingly-obvious lesson from the rash of ransomware incidents is that we need to anticipate malware infections when the preventive controls fail, which means strengthening the security protecting our business-critical systems and being ready to recover IT services and data efficiently following incidents." That's not all.Anticipating that, despite all we do to prevent them, malware infections are still likely to occur implies the need for several post-event controls. These are the kinds of controls I have in mind:Reliable, efficient, effective, top-quality incident response and management processes - in particular, speed is almost always of the essence in malware incidents, and the responses need to be well-practiced - not just the run-of-the-mill routine infections but the more extreme/serious "outbreaks";Decisive action is required, with strong leadership, clear roles and responsibilities, and of course strong awareness and training both for the response team and for the wider organization;Clarity around priorities for action e.g. halt the spread, assess the damage, find the source/cause, recover;Technological controls, of course, such as network segmentation (part of network architectural design), traffic filtering and (reliable!) isolation of segments pending their being given the all-clear;Clarity around priorities for reporting including rapid escalation and ongoing progress updates, in parallel with the other activities;Forensics, where appropriate, feasible and helpful (e.g. which preventive controls failed, why, and what if anything can be done to strengthen them); |
Ransomware Malware Guideline | |||
| 2019-12-27 18:30:47 | NBlog Dec 27 - Pakistan supports ISO27k (lien direct) |  Through the Pakistan Software Export Board of the Ministry of IT & Telecom, the Pakistan government is subsidising 80% of the cost of consultants and auditors to advise and certify Pakistani IT companies against ISO 20000 (ITIL) and ISO/IEC 27001 (information security). With over 5,000 companies in Pakistan offering Business Process Outsourcing and IT services, this represent a substantial investment, reflecting the government's intention to raise standards in the industry. Good on them! If only other governments would follow their lead. Through the Pakistan Software Export Board of the Ministry of IT & Telecom, the Pakistan government is subsidising 80% of the cost of consultants and auditors to advise and certify Pakistani IT companies against ISO 20000 (ITIL) and ISO/IEC 27001 (information security). With over 5,000 companies in Pakistan offering Business Process Outsourcing and IT services, this represent a substantial investment, reflecting the government's intention to raise standards in the industry. Good on them! If only other governments would follow their lead. |
Guideline | |||
| 2019-12-13 13:57:03 | NBlog Dec 10 - a brutal lesson in risk management (lien direct) | Yesterday's volcanic eruption on White Island is headline news around the globe, a tragedy that sadly resulted in several deaths, currently estimated at 13. Also, yesterday in NZ there were roughly 90 other deaths (as there are every day), roughly two thirds of which were caused by cardiovascular diseases or cancer: So, yesterday, the proportion of deaths in NZ caused by "Natural disasters" spiked from 0% to 13%. Today, it is likely to fall back to 0%. "Natural disasters" will have caused roughly 0.04% of the ~33,500 deaths in NZ during 2019 ... but judging by the news media coverage today, you'd have thought NZ was a disaster zone, a lethal place - which indeed it is for ~33,500 of us every year. Very very few, though, expire under a hail of molten rock and cloud of noxious fumes, viewable in glorious Technicolor on social media.Those 13 tourists who perished yesterday chose to see NZ's most active volcano up close, real close. You may be thinking "Ah but if they'd known it would erupt, they wouldn't have gone" ... but they did know it was a possibility: for at least some of the 13, that was the very reason they went. It's euphemistically called "adventure tourism". The possibility of death or serious injury is, perversely, part of the attraction, the thrill of it. Recent warnings from geologists about the increased threat of eruption on White Island would, I'm sure, have been carefully considered by the tourist companies involved, plus I guess they may have noticed changes in the amount of steam and sulfur lingering in the air. Tourists are explicitly warned about the dangers and instructed on the safety aspects. I gather one of the dead was a local, an employee of the tourist company. Aside perhaps from the geologists, it's hard to think of anyone more aware of the risk.Having weighed-up the risks and rewards, the 13 enjoyed an amazing spectacle, doing the equivalent of 'clicking the go-away button' to dismiss computer security warnings despite facing, in their case, the ultimate impact. While I suspect their final moments would have been literally petrifying, hopefully the extra-special buzz leading up to it made it worthwhile. At that point, h So, yesterday, the proportion of deaths in NZ caused by "Natural disasters" spiked from 0% to 13%. Today, it is likely to fall back to 0%. "Natural disasters" will have caused roughly 0.04% of the ~33,500 deaths in NZ during 2019 ... but judging by the news media coverage today, you'd have thought NZ was a disaster zone, a lethal place - which indeed it is for ~33,500 of us every year. Very very few, though, expire under a hail of molten rock and cloud of noxious fumes, viewable in glorious Technicolor on social media.Those 13 tourists who perished yesterday chose to see NZ's most active volcano up close, real close. You may be thinking "Ah but if they'd known it would erupt, they wouldn't have gone" ... but they did know it was a possibility: for at least some of the 13, that was the very reason they went. It's euphemistically called "adventure tourism". The possibility of death or serious injury is, perversely, part of the attraction, the thrill of it. Recent warnings from geologists about the increased threat of eruption on White Island would, I'm sure, have been carefully considered by the tourist companies involved, plus I guess they may have noticed changes in the amount of steam and sulfur lingering in the air. Tourists are explicitly warned about the dangers and instructed on the safety aspects. I gather one of the dead was a local, an employee of the tourist company. Aside perhaps from the geologists, it's hard to think of anyone more aware of the risk.Having weighed-up the risks and rewards, the 13 enjoyed an amazing spectacle, doing the equivalent of 'clicking the go-away button' to dismiss computer security warnings despite facing, in their case, the ultimate impact. While I suspect their final moments would have been literally petrifying, hopefully the extra-special buzz leading up to it made it worthwhile. At that point, h |
Threat Guideline | |||
| 2019-12-11 08:00:00 | NBlog Dec 11 - risk treatments (lien direct) |  Yesterday I wrote about what the White Island eruption teaches us about risk management, in particular the way we decide how to deal with or "treat" identified risks. ISO/IEC 27005 describes 4 risk treatment options:Avoid the risk by deliberately not getting ourselves into risky situations - not getting too close to a known active volcano for example;Modify the risk: typically we mitigate (reduce) the risk through the use of controls intended to reduce the threats or vulnerabilities and hence the probability, or to reduce the impacts;Retain the risk: this is the default - more on this below;Share the risk: previously known as "risk transfer", this involves getting the assistance of third parties to deal with our risks, through insurance for instance, or liability clauses in contracts, or consultants' advice.Risk management standards and advisories usually state or imply that these 'options' are exclusive, in other words alternatives from which we should choose just one treatment per risk. ISO/IEC 27005 says "Controls to reduce, retain, avoid, or share the risks should be selected". In fact, they are nonexclusive options since they all involve an element of risk retention. The sentence should perhaps read "Controls to reduce, retain, avoid, and share the risks should be selected".*Risk retention is inevitable because of the very nature of risk. We can never be totally certain of risk, up to the point that the probability reaches 1 when an incident occurs (which, arguably, means it is no longer a risk but a certainty!). We might have misunderstood it, or made mistakes in our analysis. Our risk treatments might not work out as expected, perhaps even failing spectacularly when we least expect it, or conversely working so well that the risk never eventuates. Our insurers and partners might reneg Yesterday I wrote about what the White Island eruption teaches us about risk management, in particular the way we decide how to deal with or "treat" identified risks. ISO/IEC 27005 describes 4 risk treatment options:Avoid the risk by deliberately not getting ourselves into risky situations - not getting too close to a known active volcano for example;Modify the risk: typically we mitigate (reduce) the risk through the use of controls intended to reduce the threats or vulnerabilities and hence the probability, or to reduce the impacts;Retain the risk: this is the default - more on this below;Share the risk: previously known as "risk transfer", this involves getting the assistance of third parties to deal with our risks, through insurance for instance, or liability clauses in contracts, or consultants' advice.Risk management standards and advisories usually state or imply that these 'options' are exclusive, in other words alternatives from which we should choose just one treatment per risk. ISO/IEC 27005 says "Controls to reduce, retain, avoid, or share the risks should be selected". In fact, they are nonexclusive options since they all involve an element of risk retention. The sentence should perhaps read "Controls to reduce, retain, avoid, and share the risks should be selected".*Risk retention is inevitable because of the very nature of risk. We can never be totally certain of risk, up to the point that the probability reaches 1 when an incident occurs (which, arguably, means it is no longer a risk but a certainty!). We might have misunderstood it, or made mistakes in our analysis. Our risk treatments might not work out as expected, perhaps even failing spectacularly when we least expect it, or conversely working so well that the risk never eventuates. Our insurers and partners might reneg |
Guideline | |||
| 2019-12-03 17:12:11 | NBlog Dec 3 - infosec driving principles (lien direct) | In an interview for CIO Dive, Maersk's recently-appointed CISO Andy Powell discussed aligning the organization with these five 'key operating principles': "The first is trust. The client has got to trust us with their data, to trust us to look at their business. So we've got to build trust through the cybersecurity solutions that we put in place. That is absolutely fundamental. So client trust, client buy-in has been fundamental to what we tried to drive as a key message. The second is resilience. Because you've got to have resilient systems because clients won't give you business if you're not resilient ... The third really is around the fact that security is everybody's responsibility. And we push that message really hard across the company … be clear about what you need to do and we train people accordingly. ...The fourth one really is accountability of security and I have pushed accountability for cyber risk to the business. ... And the final piece, and this has been one of the big call outs of my team to everybody, is that security is a benefit, not a burden. The reason I say that is people's perception is that security will slow things down, will get in the way ... the reality is that if you involve security early enough, you can build solutions that actually attract additional clients."Fair enough Andy. I wouldn't particularly quarrel with any of them, but as to whether they would feature in my personal top-five I'm not so sure. Here are five others they'd be competing against, with shipping-related illustrations just for fun:Governance involves structuring, positioning, setting things up and guiding the organization in the right overall direction - determining then plotting the optimal route to the ship's ultimate destination, loading up with the right tools, people and provisions. Corporate governance necessarily involves putting things in place for both protecting and exploiting information, a vital and valuable yet vulnerable business asset;Information is subject to risks that can and probably should be managed proactively, just as a ship's captain doesn't merely accept the inclement weather and various other hazards but, where appropriate, actively mitigates or avoids them, dynamically reacting and adjusting course as things change;Flexibility and responsiveness, along with resilience and ro "The first is trust. The client has got to trust us with their data, to trust us to look at their business. So we've got to build trust through the cybersecurity solutions that we put in place. That is absolutely fundamental. So client trust, client buy-in has been fundamental to what we tried to drive as a key message. The second is resilience. Because you've got to have resilient systems because clients won't give you business if you're not resilient ... The third really is around the fact that security is everybody's responsibility. And we push that message really hard across the company … be clear about what you need to do and we train people accordingly. ...The fourth one really is accountability of security and I have pushed accountability for cyber risk to the business. ... And the final piece, and this has been one of the big call outs of my team to everybody, is that security is a benefit, not a burden. The reason I say that is people's perception is that security will slow things down, will get in the way ... the reality is that if you involve security early enough, you can build solutions that actually attract additional clients."Fair enough Andy. I wouldn't particularly quarrel with any of them, but as to whether they would feature in my personal top-five I'm not so sure. Here are five others they'd be competing against, with shipping-related illustrations just for fun:Governance involves structuring, positioning, setting things up and guiding the organization in the right overall direction - determining then plotting the optimal route to the ship's ultimate destination, loading up with the right tools, people and provisions. Corporate governance necessarily involves putting things in place for both protecting and exploiting information, a vital and valuable yet vulnerable business asset;Information is subject to risks that can and probably should be managed proactively, just as a ship's captain doesn't merely accept the inclement weather and various other hazards but, where appropriate, actively mitigates or avoids them, dynamically reacting and adjusting course as things change;Flexibility and responsiveness, along with resilience and ro |
Tool Guideline | NotPetya | ||
| 2019-11-26 17:57:12 | NBlog Nov 26 - 7 ways to improve security awareness & training (lien direct) |  Although 7 Ways to Improve Employee Development Programs by Keith Ferrazzi in the Harvard Business Review is not specifically about information security awareness and training, it's straightforward to apply it in that context. The 7 ways in bold below are quoted from Keith's paper, followed by my take.1. Ignite managers' passion to coach their employees. I quite like this one: the idea is to incentivize managers to coach the workforce. As far as I'm concerned, this is an inherent part of management and leadership, something that can be enabled and encouraged in a general manner not just through explicit (e.g. financial) incentives. For me, this starts right at the very top: a proactive CEO, MD and executive/leadership team is in an ideal position to set this ball rolling on down the cascade - or not. If the top table is ambiguous or even negative about this, guess what happens! So, right there is an obvious strategy worth pursuing: start at, or at the very least, include those at the very top of the organization ... which means taking their perspectives and addressing their current information needs, preferred learning styles and so forth (more below: directors and execs are - allegedly - as human as the rest of us!).2. Deal with the short-shelf life of learning and development needs. 'Short shelf-life' is a nice way to put it. In the field of information risk and security, the emergence of novel threats that exploit previously unrecognized vulnerabilities causing substantial business impacts, is a key and recurrent challenge. I totally agree with the need to make security awareness an ongoing, ideally continuous activity, drip-feeding workers with current, pertinent information and guidance all year long rather than attempting to dump everything on them in a once-in-a-blue-moon event, session or course. Apart from anything else, keeping the awareness materials and activities topical makes them more interesting than stale old irrelevant and distracting junk that is 'so last year' (at best!).3. Teach employees to own their career development. An interesting suggestion, this, especially for the more involved infosec topics normally taught through intensive training courses rather than general spare-time awareness activities. I'm not sure off-hand how this suggestion would work in practice, but it occurs to me that periodic employee appraisals and team meetings provide ample opportunities to offer training and encourage workers to take up whatever suits their career and personal development aspirations. Although 7 Ways to Improve Employee Development Programs by Keith Ferrazzi in the Harvard Business Review is not specifically about information security awareness and training, it's straightforward to apply it in that context. The 7 ways in bold below are quoted from Keith's paper, followed by my take.1. Ignite managers' passion to coach their employees. I quite like this one: the idea is to incentivize managers to coach the workforce. As far as I'm concerned, this is an inherent part of management and leadership, something that can be enabled and encouraged in a general manner not just through explicit (e.g. financial) incentives. For me, this starts right at the very top: a proactive CEO, MD and executive/leadership team is in an ideal position to set this ball rolling on down the cascade - or not. If the top table is ambiguous or even negative about this, guess what happens! So, right there is an obvious strategy worth pursuing: start at, or at the very least, include those at the very top of the organization ... which means taking their perspectives and addressing their current information needs, preferred learning styles and so forth (more below: directors and execs are - allegedly - as human as the rest of us!).2. Deal with the short-shelf life of learning and development needs. 'Short shelf-life' is a nice way to put it. In the field of information risk and security, the emergence of novel threats that exploit previously unrecognized vulnerabilities causing substantial business impacts, is a key and recurrent challenge. I totally agree with the need to make security awareness an ongoing, ideally continuous activity, drip-feeding workers with current, pertinent information and guidance all year long rather than attempting to dump everything on them in a once-in-a-blue-moon event, session or course. Apart from anything else, keeping the awareness materials and activities topical makes them more interesting than stale old irrelevant and distracting junk that is 'so last year' (at best!).3. Teach employees to own their career development. An interesting suggestion, this, especially for the more involved infosec topics normally taught through intensive training courses rather than general spare-time awareness activities. I'm not sure off-hand how this suggestion would work in practice, but it occurs to me that periodic employee appraisals and team meetings provide ample opportunities to offer training and encourage workers to take up whatever suits their career and personal development aspirations. |
Guideline | |||
| 2019-11-07 10:31:27 | NBlog Nov 6 - insight into ISO27k editing (lien direct) | Today I find myself poring through ISO/IEC 27000:2018 looking for quotable snippets to use on our awareness posters in January. Although there's plenty of good content, I can't help but notice a few rough edges, such as this:“Conducting a methodical assessment of the risks associated with the organization's information assets involves analysing threats to information assets, vulnerabilities to and the likelihood of a threat materializing to information assets, and the potential impact of any information security incident on information assets. The expenditure on relevant controls is expected to be proportionate to the perceived business impact of the risk materializing.” [part of clause 4.5.2]. First off, here and elsewhere the '27000 text uses the term “information asset” which is no longer defined in the standard since the committee couldn't reach consensus on that. Readers are left to figure out the meaning for themselves, with the possibility of differing interpretations that may affect the sense in places. The term is, or probably should be, deprecated. Secondly, the first sentence is long and confusing – badly constructed and (perhaps) grammatically incorrect. “Vulnerabilities to” is incomplete: vulnerabilities to what? Shouldn't that be “vulnerabilities in” anyway? Threats get mentioned twice for no obvious reason, overemphasizing that aspect. “Likelihood” is a vague and problematic word with no precise equivalent in some languages - it too should probably be deprecated. The final clause as worded could be interpreted to mean that the process is only concerned with potential impacts on information assets, whereas incidents can cause direct and/or indirect/consequential impacts on systems, organizations, business relationships, compliance status, reputations and brands, commercial prospects, profits, individuals, partners, society at large and so forth, not all of which are information assets (as commonly interpreted, anyway!). Thirdly, do “the organization's information assets” include personal information? Some might argue that personal information belongs to the person concerned – the data subject – not the organiza Secondly, the first sentence is long and confusing – badly constructed and (perhaps) grammatically incorrect. “Vulnerabilities to” is incomplete: vulnerabilities to what? Shouldn't that be “vulnerabilities in” anyway? Threats get mentioned twice for no obvious reason, overemphasizing that aspect. “Likelihood” is a vague and problematic word with no precise equivalent in some languages - it too should probably be deprecated. The final clause as worded could be interpreted to mean that the process is only concerned with potential impacts on information assets, whereas incidents can cause direct and/or indirect/consequential impacts on systems, organizations, business relationships, compliance status, reputations and brands, commercial prospects, profits, individuals, partners, society at large and so forth, not all of which are information assets (as commonly interpreted, anyway!). Thirdly, do “the organization's information assets” include personal information? Some might argue that personal information belongs to the person concerned – the data subject – not the organiza |
Threat Guideline | |||
| 2018-03-20 10:30:42 | NBlog March 20 - a critique of CIS netsec metrics (lien direct) |  Perusing a CIS paper on metrics for their newly-updated recommended network security controls (version 7), several things strike me all at once, a veritable rash of issues.Before reading on, please at least take a quick squint at the CIS paper. See what you see. Think what you think. You'll get more out of this blog piece if you've done your homework first. You may well disagree with me, and we can talk about that. That way, I'll get more out of this blog piece too![Pause while you browse the CIS paper on metrics][Further pause while you get your thoughts in order] Perusing a CIS paper on metrics for their newly-updated recommended network security controls (version 7), several things strike me all at once, a veritable rash of issues.Before reading on, please at least take a quick squint at the CIS paper. See what you see. Think what you think. You'll get more out of this blog piece if you've done your homework first. You may well disagree with me, and we can talk about that. That way, I'll get more out of this blog piece too![Pause while you browse the CIS paper on metrics][Further pause while you get your thoughts in order] |
Guideline | |||
| 2018-03-15 07:43:59 | NBlog March 15 - scheduling audits (lien direct) |  One type of assurance is audit, hence auditing and IT auditing in particular is very much in-scope for our next security awareness module.By coincidence, yesterday on the ISO27k Forum, the topic of 'security audit schedules' came up.An audit schedule is a schedule of audits, in simple terms a diary sheet listing the audits you are planning to do. The usual way to prepare an audit schedule is risk-based and resource-constrained. Here's an outline (!) of the planning process to set you thinking, with a sprinkling of Hinson tips:Figure out all the things that might be worth auditing within your scope (the 'audit universe') and list them out. Brainstorm (individually and if you can with a small group of brainstormers), look at the ISMS scope, look for problem areas and concerns, look at incident records and findings from previous audits, reviews and other things. Mind map if that helps ... then write them all down into a linear list.Assess the associated information risks, at a high level, to rank the rough list of potential audits by risk - riskiest areas at the top (roughly at first -'high/medium/low' risk categories would probably do - not least because until the audit work commences, it's hard to know what the risks really are). Guess how much time and effort each audit would take (roughly at first -'big/medium/small categories would probably do - again, this will change in practice but you have to start your journey of discovery with a first step).In conjunction with other colleagues, meddle around with the wording and purposes of the potential audits, taking account of the business value (e.g. particular audits on the list that would be fantastic 'must-do' audits vs audits that would be extraordinarily difficult or pointless with little prospect of achieving real change). If it helps, split up audits that are too big to handle, and combine or blend-in tiddlers that are hardly worth running separately. Make notes on any fixed constraints (e.g. parts of the business cycle when audits would be needed, or would be problematic; and dependencies such as pre/prep-work audits to be followed by in-depth audits to explore problem areas found earlier, plus audits that are linked to IT system/service implementations, mergers, compliance deadlines etc.). One type of assurance is audit, hence auditing and IT auditing in particular is very much in-scope for our next security awareness module.By coincidence, yesterday on the ISO27k Forum, the topic of 'security audit schedules' came up.An audit schedule is a schedule of audits, in simple terms a diary sheet listing the audits you are planning to do. The usual way to prepare an audit schedule is risk-based and resource-constrained. Here's an outline (!) of the planning process to set you thinking, with a sprinkling of Hinson tips:Figure out all the things that might be worth auditing within your scope (the 'audit universe') and list them out. Brainstorm (individually and if you can with a small group of brainstormers), look at the ISMS scope, look for problem areas and concerns, look at incident records and findings from previous audits, reviews and other things. Mind map if that helps ... then write them all down into a linear list.Assess the associated information risks, at a high level, to rank the rough list of potential audits by risk - riskiest areas at the top (roughly at first -'high/medium/low' risk categories would probably do - not least because until the audit work commences, it's hard to know what the risks really are). Guess how much time and effort each audit would take (roughly at first -'big/medium/small categories would probably do - again, this will change in practice but you have to start your journey of discovery with a first step).In conjunction with other colleagues, meddle around with the wording and purposes of the potential audits, taking account of the business value (e.g. particular audits on the list that would be fantastic 'must-do' audits vs audits that would be extraordinarily difficult or pointless with little prospect of achieving real change). If it helps, split up audits that are too big to handle, and combine or blend-in tiddlers that are hardly worth running separately. Make notes on any fixed constraints (e.g. parts of the business cycle when audits would be needed, or would be problematic; and dependencies such as pre/prep-work audits to be followed by in-depth audits to explore problem areas found earlier, plus audits that are linked to IT system/service implementations, mergers, compliance deadlines etc.). |
Guideline | |||
| 2018-03-09 13:00:43 | NBlog March 9 - word cloud creativity (lien direct) |  Yesterday I wrote about mind mapping. The tick image above is another creative technique we use to both explore and express the awareness topic.To generate a word cloud, we start by compiling a list of words relating in some way to the area. Two key sources of inspiration are: The background research we've been doing over the past couple of months - lots of Googling, reading and contemplating; and Our extensive information risk and security glossary, a working document of 300-odd pages, systematically reviewed and updated every month and included in the NoticeBored awareness modules. Two specific terms in that word cloud amuse me: "Man-sure" and "Lady-sure" hint about the different ways people think about things. When a lay person (man or woman!) says "I'm sure", they may be quite uncertain in fact. They are usually expressing a subjective opinion, an interpretation or belief with little substance, no objective, factual evidence. It can easily be wrong and misleading. When a male or female expert or scientist, on the other hand, says "I'm sure", their opinion typically stems from experience, and carries more weight. It is less likely to be wrong, and hence provides greater assurance. This relates to integrity, a core part of information security. It's not literally about sex.Aside from integrity and assurance, we have defined more than 2,000 terms-of-art in the glossary, with key words in the definitions hyperlinked to the corresponding glossary entries. I use it like a thesaurus, following a train of thought that meanders through the document, sometimes spinning off at a tangent but always triggering fresh ideas. Updating the glossary is painstaking yet creative at the same time.Getting back to the word cloud, we squeeze extra value from the list of words by generating puzzles for the modules. Our word-searches are grids of letters that spell out the words in various directions. Finding the words 'hidden' in the grid is an interesting, fun challenge in itself, and also a learning process since the words all relate to the chosen topic.There are other aspects to the word cloud graphic:All the words are relevant to the topic, to some extent; Yesterday I wrote about mind mapping. The tick image above is another creative technique we use to both explore and express the awareness topic.To generate a word cloud, we start by compiling a list of words relating in some way to the area. Two key sources of inspiration are: The background research we've been doing over the past couple of months - lots of Googling, reading and contemplating; and Our extensive information risk and security glossary, a working document of 300-odd pages, systematically reviewed and updated every month and included in the NoticeBored awareness modules. Two specific terms in that word cloud amuse me: "Man-sure" and "Lady-sure" hint about the different ways people think about things. When a lay person (man or woman!) says "I'm sure", they may be quite uncertain in fact. They are usually expressing a subjective opinion, an interpretation or belief with little substance, no objective, factual evidence. It can easily be wrong and misleading. When a male or female expert or scientist, on the other hand, says "I'm sure", their opinion typically stems from experience, and carries more weight. It is less likely to be wrong, and hence provides greater assurance. This relates to integrity, a core part of information security. It's not literally about sex.Aside from integrity and assurance, we have defined more than 2,000 terms-of-art in the glossary, with key words in the definitions hyperlinked to the corresponding glossary entries. I use it like a thesaurus, following a train of thought that meanders through the document, sometimes spinning off at a tangent but always triggering fresh ideas. Updating the glossary is painstaking yet creative at the same time.Getting back to the word cloud, we squeeze extra value from the list of words by generating puzzles for the modules. Our word-searches are grids of letters that spell out the words in various directions. Finding the words 'hidden' in the grid is an interesting, fun challenge in itself, and also a learning process since the words all relate to the chosen topic.There are other aspects to the word cloud graphic:All the words are relevant to the topic, to some extent; |
Guideline | |||
| 2018-02-17 12:25:47 | NBlog February 17 - The I part of CIA (lien direct) |  Integrity is a universal requirement, especially if you interpret the term widely to include aspects such as:Completeness of information;Accuracy of information;Veracity, authenticity and assurance levels in general e.g. testing and measuring to determine how complete and accurate a data set is, or is not (an important control, often neglected);Timeliness (or currency or 'up-to-date-ness') of information (with the implication of controls to handle identifying and dealing appropriately with outdated info – a control missing from ISO/IEC 27001 Annex A, I think);Database integrity plus aspects such as contextual appropriateness plus internal and external consistency (and, again, a raft of associated controls at all levels of the system, not just Codd's rules within the DBMS);Honesty, justified credibility, trust, trustworthiness, 'true grit', resilience, dependability and so forth, particularly in the humans and systems performing critical activities (another wide-ranging issue with several related controls);Responsibility and accountability, including custodianship, delegation, expectations, obligations, commitments and all that …… leading into ethics, professional standards of good conduct, 'rules', compliance and more.The full breadth of meanings and the implications of “integrity” are the key rea Integrity is a universal requirement, especially if you interpret the term widely to include aspects such as:Completeness of information;Accuracy of information;Veracity, authenticity and assurance levels in general e.g. testing and measuring to determine how complete and accurate a data set is, or is not (an important control, often neglected);Timeliness (or currency or 'up-to-date-ness') of information (with the implication of controls to handle identifying and dealing appropriately with outdated info – a control missing from ISO/IEC 27001 Annex A, I think);Database integrity plus aspects such as contextual appropriateness plus internal and external consistency (and, again, a raft of associated controls at all levels of the system, not just Codd's rules within the DBMS);Honesty, justified credibility, trust, trustworthiness, 'true grit', resilience, dependability and so forth, particularly in the humans and systems performing critical activities (another wide-ranging issue with several related controls);Responsibility and accountability, including custodianship, delegation, expectations, obligations, commitments and all that …… leading into ethics, professional standards of good conduct, 'rules', compliance and more.The full breadth of meanings and the implications of “integrity” are the key rea |
Guideline | |||
| 2018-01-11 16:06:05 | NBlog January 11 - awareness styles (lien direct) |  Over the past couple of months, I've written and published a suite of 'Hinson tips' on another passion of mine: amateur radio. The tips concern a cutting-edge development in digital communications, and how to get the most out of the associated software. I've had a lot of feedback on the tips, reflecting global interest in the new software and, I guess, the need for more guidance on how to use it. The reason I'm bringing it up here is that my writing style appears to have influenced the nature of the feedback I'm getting from, and my relationship with, the readers. I honestly wasn't expecting that.There was already a reasonably comprehensive help file for the program, well-written but in a fairly formal and dry technical style typical of technical manuals (not those ineptly translated from Chinese via Double Dutch!). A constant refrain is that people don't read the help file, just as we don't RTFM (Read The Flamin' Manual!). I suspect part of the reason is that 'fairly formal and dry technical style': despite amateur radio being a technical hobby, many hams are not technically-minded. Some simply enjoy using the radio to talk to people, and why not? It takes all sorts. Digital communications adds another layer of complexity through information theory and mathematics underpinning the protocols we use, and IT is a world of pain for some. To be frank, although I have a passing interest and some knowledge, I'm way out of my depth in some of those areas ... which means I empathise with those who are equally uncomfortable.There is also an active online support forum, populated by a mix of experts, somewhat experienced users and complete novices. Unfortunately, the forum is suffering a little from the recent influx of people, some of whom are very passionate (which can easily come across as opinionated, strong-willed and direct). Being a global community, a lot of hams don't understand English very well (if at all!), hence the language can be a problem for them, as well as the sometimes hostile reception anyone gets on asking a 'dumb question'. Even attempting to explain things patiently in response to a genuine question or discuss ways to respond to an issue can lead to complaints that there are 'too many messages' and we are 'going off-topic', reflecting general frustration and perhaps a lack of understanding and/or focus.So, I deliberately chose to write the tips in an accessible, readable, informal style, drawing on, interpreting and re-writing material from the help file and the forum, Over the past couple of months, I've written and published a suite of 'Hinson tips' on another passion of mine: amateur radio. The tips concern a cutting-edge development in digital communications, and how to get the most out of the associated software. I've had a lot of feedback on the tips, reflecting global interest in the new software and, I guess, the need for more guidance on how to use it. The reason I'm bringing it up here is that my writing style appears to have influenced the nature of the feedback I'm getting from, and my relationship with, the readers. I honestly wasn't expecting that.There was already a reasonably comprehensive help file for the program, well-written but in a fairly formal and dry technical style typical of technical manuals (not those ineptly translated from Chinese via Double Dutch!). A constant refrain is that people don't read the help file, just as we don't RTFM (Read The Flamin' Manual!). I suspect part of the reason is that 'fairly formal and dry technical style': despite amateur radio being a technical hobby, many hams are not technically-minded. Some simply enjoy using the radio to talk to people, and why not? It takes all sorts. Digital communications adds another layer of complexity through information theory and mathematics underpinning the protocols we use, and IT is a world of pain for some. To be frank, although I have a passing interest and some knowledge, I'm way out of my depth in some of those areas ... which means I empathise with those who are equally uncomfortable.There is also an active online support forum, populated by a mix of experts, somewhat experienced users and complete novices. Unfortunately, the forum is suffering a little from the recent influx of people, some of whom are very passionate (which can easily come across as opinionated, strong-willed and direct). Being a global community, a lot of hams don't understand English very well (if at all!), hence the language can be a problem for them, as well as the sometimes hostile reception anyone gets on asking a 'dumb question'. Even attempting to explain things patiently in response to a genuine question or discuss ways to respond to an issue can lead to complaints that there are 'too many messages' and we are 'going off-topic', reflecting general frustration and perhaps a lack of understanding and/or focus.So, I deliberately chose to write the tips in an accessible, readable, informal style, drawing on, interpreting and re-writing material from the help file and the forum, |
Guideline | |||
| 2018-01-04 11:14:03 | NBlog January 4 - IoT and BYOD security awareness module released (lien direct) |  The Internet of Things and Bring Your Own Device typically involve the use of small, portable, wireless networked computer systems, big on convenience and utility but small on security. Striking the right balance between those and other factors is tricky, especially if people don't understand or willfully ignore the issues – hence education through security awareness on this topic makes a lot of sense.From the average employee's perspective, BYOD is simply a matter of working on their favorite IT devices rather than being lumbered with the clunky corporate stuff provided by most organizations. In practice, there are substantial implications for information risk and security e.g.:Ownership and control of the BYOD device is distinct from ownership and control of the corporate data and IT services;The lines between business use and personal life, and data, are blurred;The organization and workers may have differing, perhaps even conflicting expectations and requirements concerning security and privacy (particularly the workers' private and personal information on their devices);Granting access to the corporate network, systems, applications and data by assorted devices, most of which are portable and often physically remote, markedly changes the organization's cyber-risk profile compared to everything being contained on the facilities and wired LANs;Increasing technical diversity and complexity leads to concerns over supportability, management, monitoring etc., and security of course. Complexity is the information security manager's kryptonite.IoT is more than just allowing assorted things to be connected to The Internet of Things and Bring Your Own Device typically involve the use of small, portable, wireless networked computer systems, big on convenience and utility but small on security. Striking the right balance between those and other factors is tricky, especially if people don't understand or willfully ignore the issues – hence education through security awareness on this topic makes a lot of sense.From the average employee's perspective, BYOD is simply a matter of working on their favorite IT devices rather than being lumbered with the clunky corporate stuff provided by most organizations. In practice, there are substantial implications for information risk and security e.g.:Ownership and control of the BYOD device is distinct from ownership and control of the corporate data and IT services;The lines between business use and personal life, and data, are blurred;The organization and workers may have differing, perhaps even conflicting expectations and requirements concerning security and privacy (particularly the workers' private and personal information on their devices);Granting access to the corporate network, systems, applications and data by assorted devices, most of which are portable and often physically remote, markedly changes the organization's cyber-risk profile compared to everything being contained on the facilities and wired LANs;Increasing technical diversity and complexity leads to concerns over supportability, management, monitoring etc., and security of course. Complexity is the information security manager's kryptonite.IoT is more than just allowing assorted things to be connected to |
Guideline | |||
| 2017-12-21 15:49:45 | NBlog December 21 - auditor independence [LONG] (lien direct) |  Over on the ISO27k Forum, we've been discussing one of my favourite topics: auditing, or more precisely the question of auditor independence. How independent should an auditor be? What does that even mean, in this context? SPOILER ALERT: there's rather more to it than reporting lines.My experienced IT auditor friend Anton posted some relevant definitions from ISACA, including this little gem:"Independence of mind: the state of mind that permits the expression of a conclusion without being affected by influences that compromise professional judgement, thereby allowing an individual to act with integrity and exercise objectivity and professional scepticism."While I agree this is an extremely important factor, I have a slightly different interpretation. 'Independence of mind', to me, is the auditor's mental capacity to examine a situation free of the prejudice or bias that naturally afflicts people who have been in or dealing with or managing or indeed suffering from the situation, plus all that led up to it, and all the stuff around it (the context), including all the 'constraints' or 'reasons' or 'issues' that make it 'a situation' at all. It's more about the auditor making a back-to-basics theoretical assessment, thinking through all the complexities and (hopefully!) teasing out the real underlying reasons for whatever has happened, is happening, and needs to happen next. The ability to report stuff (ISACA's "expression of a conclusion") is only part of it: figuring out how the situation ought to be in theory, then looking at it in practice, gathering objective, factual evidence, doing the analysis, probing further and focusing on the stuff that matters most (the 'root causes'), are at least as important audit activities as reporting.Here's a little exercise to demonstrate why independence matters: next time you drive or are driven on a familiar route, make an extra special effort to spot and look carefully at EVERY road sign and potential hazard along the way. Concentrate on the task (as well as driving safely, please!). Say out loud ever Over on the ISO27k Forum, we've been discussing one of my favourite topics: auditing, or more precisely the question of auditor independence. How independent should an auditor be? What does that even mean, in this context? SPOILER ALERT: there's rather more to it than reporting lines.My experienced IT auditor friend Anton posted some relevant definitions from ISACA, including this little gem:"Independence of mind: the state of mind that permits the expression of a conclusion without being affected by influences that compromise professional judgement, thereby allowing an individual to act with integrity and exercise objectivity and professional scepticism."While I agree this is an extremely important factor, I have a slightly different interpretation. 'Independence of mind', to me, is the auditor's mental capacity to examine a situation free of the prejudice or bias that naturally afflicts people who have been in or dealing with or managing or indeed suffering from the situation, plus all that led up to it, and all the stuff around it (the context), including all the 'constraints' or 'reasons' or 'issues' that make it 'a situation' at all. It's more about the auditor making a back-to-basics theoretical assessment, thinking through all the complexities and (hopefully!) teasing out the real underlying reasons for whatever has happened, is happening, and needs to happen next. The ability to report stuff (ISACA's "expression of a conclusion") is only part of it: figuring out how the situation ought to be in theory, then looking at it in practice, gathering objective, factual evidence, doing the analysis, probing further and focusing on the stuff that matters most (the 'root causes'), are at least as important audit activities as reporting.Here's a little exercise to demonstrate why independence matters: next time you drive or are driven on a familiar route, make an extra special effort to spot and look carefully at EVERY road sign and potential hazard along the way. Concentrate on the task (as well as driving safely, please!). Say out loud ever |
Guideline | |||
| 2017-12-08 10:10:13 | NBlog December 8 - cybersecurity awareness story-telling (lien direct) | Conceptual diagrams ('mind maps') are extremely useful for awareness purposes. This one, for instance, only has about 50 words but expresses a lot more than could be said with ~50 words of conventional prose: Despite it being more than 7 years since I drew that diagram in Visio, it immediately makes sense. It tells a story. Working clockwise from 1 o'clock, it steps through the main wireless networking technologies that were common in 2010, picking out some of the key information security concerns for each of them. It's not hard to guess what I was thinking about.The arrows draw the reader's eye in the specified direction along each path linking together related items. Larger font, bold text and the red highlight the main elements, leading towards and emphasizing "New risks" especially. Sure enough today we have to contend with a raft of personal, local, mesh, community and wide area networks, in addition to the those shown. When the diagram was prepared, we didn't know exactly what was coming but predicted that new wireless networking technologies would present new risks. That's hardly ground-breaking insight, although pointing out that risks arise from the combination of threats, vulnerabilities and impacts hinted at the likelihood of changes in all three areas, a deliberate ploy to get the audience wondering about what might be coming, and hopefully thinking and planning ahead.It's time, now, to update the diagram and adapt it to reflect the current situation for inclusion in January's awareness module. The process of updating the diagram is as valuable as the product - researching and thinking about what has changed, how things have changed, what's new in this spa Despite it being more than 7 years since I drew that diagram in Visio, it immediately makes sense. It tells a story. Working clockwise from 1 o'clock, it steps through the main wireless networking technologies that were common in 2010, picking out some of the key information security concerns for each of them. It's not hard to guess what I was thinking about.The arrows draw the reader's eye in the specified direction along each path linking together related items. Larger font, bold text and the red highlight the main elements, leading towards and emphasizing "New risks" especially. Sure enough today we have to contend with a raft of personal, local, mesh, community and wide area networks, in addition to the those shown. When the diagram was prepared, we didn't know exactly what was coming but predicted that new wireless networking technologies would present new risks. That's hardly ground-breaking insight, although pointing out that risks arise from the combination of threats, vulnerabilities and impacts hinted at the likelihood of changes in all three areas, a deliberate ploy to get the audience wondering about what might be coming, and hopefully thinking and planning ahead.It's time, now, to update the diagram and adapt it to reflect the current situation for inclusion in January's awareness module. The process of updating the diagram is as valuable as the product - researching and thinking about what has changed, how things have changed, what's new in this spa |
Guideline | |||
| 2017-12-07 11:16:01 | NBlog December 7 - Santa\'s slaves bearing gifts (lien direct) |  Today we went on a tiki-tour of the forest in search of a few pine saplings of just the right size, shape and density to serve as Christmas trees. Naturally, the best ones were in the brambles or on the side of a near vertical slope but, hey, that's all part of the fun.I guess 'Web-enabled remotely-controllable LED Christmas tree lights' are The Thing this year. Ooh the sheer luxury of being able to program an amazing light show from your mobile phone!So what are the information risks in that scenario? Let's run through a conventional risk analysis.THREATSElves meddling with the light show, causing frustration and puzzlement.Pixies making the lights flash at a specific frequency known to trigger epileptic attacks.Naughty pixies intent on infecting mobile phones with malware, taking control of them and stealing information, via the light show app.Hackers using yet-another-insecure-Thing as an entry point into assorted home ... and corporate networks (because, yes, BYOD doubtless extends to someone bringing in Web-enabled lights to brighten up the office Christmas tree this year).VULNERABILITIESIrresistibly sexy new high-technology stuff. Resistance is futile. Christmas is coming. Santa is king.Inherently insecure Things (probably ... with probability levels approaching one). Blind-spots towards information risk and security associated with Things, especially cheap little Things in all the shops. Who gives a stuff about cybersecurity for web-enabled Christmas tree lights? Before you read this blog, did it even occur to you as an issue? Are you still dubious about it? Read on!Does anyone bother security-testing them, or laying down rules about bringing them into the home Today we went on a tiki-tour of the forest in search of a few pine saplings of just the right size, shape and density to serve as Christmas trees. Naturally, the best ones were in the brambles or on the side of a near vertical slope but, hey, that's all part of the fun.I guess 'Web-enabled remotely-controllable LED Christmas tree lights' are The Thing this year. Ooh the sheer luxury of being able to program an amazing light show from your mobile phone!So what are the information risks in that scenario? Let's run through a conventional risk analysis.THREATSElves meddling with the light show, causing frustration and puzzlement.Pixies making the lights flash at a specific frequency known to trigger epileptic attacks.Naughty pixies intent on infecting mobile phones with malware, taking control of them and stealing information, via the light show app.Hackers using yet-another-insecure-Thing as an entry point into assorted home ... and corporate networks (because, yes, BYOD doubtless extends to someone bringing in Web-enabled lights to brighten up the office Christmas tree this year).VULNERABILITIESIrresistibly sexy new high-technology stuff. Resistance is futile. Christmas is coming. Santa is king.Inherently insecure Things (probably ... with probability levels approaching one). Blind-spots towards information risk and security associated with Things, especially cheap little Things in all the shops. Who gives a stuff about cybersecurity for web-enabled Christmas tree lights? Before you read this blog, did it even occur to you as an issue? Are you still dubious about it? Read on!Does anyone bother security-testing them, or laying down rules about bringing them into the home |
Guideline | |||
| 2017-12-05 08:24:37 | NBlog December 5 - lurid headline (lien direct) | Social-Engineer.com's newsletter is a useful source of information about social engineering methods. The latest issue outlines some of the tricks used by phishers to lure their victims initially."It is not breaking news that phishing is the leading cause of data breaches in the modern world. It is safe to ask why that is the case though, given how much of this email gets caught up in our spam filters and perimeter defenses. One trick sophisticated attackers use is triggering emotional responses from targets using simple and seemingly innocuous messaging to generate any response at all. Some messaging does not initially employ attachments or links, but instead tries to elicit an actual reply from the target. Once the attackers establish a communication channel and a certain level of trust, either a payload of the attacker's choosing can then be sent or the message itself can entice the target to act."That same technique is used by advertisers over the web in the form of lurid or intriguing headlines and images, carefully crafted to get us to click the links and so dive into a rabbit warren of further items and junk, all the while being inundated with ads. You may even see the lures here or hereabouts (courtesy of Google). Once you've seen enough of them, you'll recognize the style and spot the trigger words - bizarre, trick, insane, weird, THIS and so on, essentially meaning CLICK HERE, NOW!They are curiously attractive, almost irresistible, even though we've groped around in the rabbit warrens before and suspect or know what we're letting ourselves in for. But why is that? 'Curiously' is the key: it's our natural curiosity that leads us in. It's what led you to read this sentence. Ending the previous paragraph with a rhetorical question was my deliberate choice. Like magpies or trout chasing something shiny, I got you. You fell for it. I manipulated you. Sorry.There are loads more examples along similar lines - random survey statistics for instance ("87% of X prone to Y") and emotive subjects ("Doctors warn Z causes cancer"). We have the newspapers to thank for the very term 'headline', not just the tabloid/gutter press ("Elvis buried on Mars") but the broadsheets and more up-market magazines and journals, even scientific papers. The vast majority of stuff we read has titles and headings, large and bold in style, both literally and figuratively. Postings on this blog all have short titles and a brief summary/description, and some of the more detailed pieces have subheadings providing structure and shortcuts for readers who lack the time or inclination to read every word ... which hints at another issue, information overload. Today's Web is so vast that we're all sipping from the fire hose.And that | Guideline | APT 15 | ||
| 2017-11-28 22:34:29 | ISO27k internal audits for small organizations (lien direct) |  Figuring out how to organize, resource and conduct internal audits of an ISO/IEC 27001 Information Security Management System can be awkward for small organizations.Independence is the overriding factor in auditing of all forms. For internal auditing, it's not just a question of who the auditors report to and their freedom to 'say what needs to be said' (important though that is), but more fundamentally their mindset, experience and attitude. They need to see things with fresh eyes, pointing out and where necessary challenging management to deal with deep-seated long-term 'cultural' issues that are part of the fabric in any established organization. That's hard if they are part of the day-to-day running of the organization, fully immersed in the culture and (for managers in small organizations especially) partly responsible for the culture being the way it is. We all have our biases and blind spots, our habits and routines: a truly independent view hopefully does not - at least, not entirely the same one!ISO/IEC 27001 recommends both management reviews and internal audits. The people you have mentioned may well be technically qualified to do both but (especially without appropriate experience/training, management support and the independent, critical perspective I've mentioned) they may not do so well at auditing as, say, consultants. The decision is a business issue for you and your management: do the benefits of having a truly independent and competent audit outweigh the additional cost? Or do you think your own people would do it well enough at lower cost?As the customer, you get to specify exactly what you want the consultants to bid for. A very tightly scoped and focused internal audit for a relatively small and simple ISMS might only take a day or two of consulting time, keeping the costs down. On the other hand, they will be able to dig deeper and put more effort into the reporting and achieving improvements if you allow them more time for the job – again, a management decision, worth discussing with potential consultants.One strategy you might consider is to rotate the internal audit responsibility among your own people, having different individuals perform successive audits. That way, although they are not totally independent, they do at least have the chance to bring different perspectives to areas that they would not normally get involved in. It would help to have a solid, standardized audit process though, so each of the auditors is performing and reporting the audit work in a similar way … and to get you started and set that up, you might like to engage a consultant for the first audit, designing and documenting the audit process, providing checklist and reporting templates etc., Figuring out how to organize, resource and conduct internal audits of an ISO/IEC 27001 Information Security Management System can be awkward for small organizations.Independence is the overriding factor in auditing of all forms. For internal auditing, it's not just a question of who the auditors report to and their freedom to 'say what needs to be said' (important though that is), but more fundamentally their mindset, experience and attitude. They need to see things with fresh eyes, pointing out and where necessary challenging management to deal with deep-seated long-term 'cultural' issues that are part of the fabric in any established organization. That's hard if they are part of the day-to-day running of the organization, fully immersed in the culture and (for managers in small organizations especially) partly responsible for the culture being the way it is. We all have our biases and blind spots, our habits and routines: a truly independent view hopefully does not - at least, not entirely the same one!ISO/IEC 27001 recommends both management reviews and internal audits. The people you have mentioned may well be technically qualified to do both but (especially without appropriate experience/training, management support and the independent, critical perspective I've mentioned) they may not do so well at auditing as, say, consultants. The decision is a business issue for you and your management: do the benefits of having a truly independent and competent audit outweigh the additional cost? Or do you think your own people would do it well enough at lower cost?As the customer, you get to specify exactly what you want the consultants to bid for. A very tightly scoped and focused internal audit for a relatively small and simple ISMS might only take a day or two of consulting time, keeping the costs down. On the other hand, they will be able to dig deeper and put more effort into the reporting and achieving improvements if you allow them more time for the job – again, a management decision, worth discussing with potential consultants.One strategy you might consider is to rotate the internal audit responsibility among your own people, having different individuals perform successive audits. That way, although they are not totally independent, they do at least have the chance to bring different perspectives to areas that they would not normally get involved in. It would help to have a solid, standardized audit process though, so each of the auditors is performing and reporting the audit work in a similar way … and to get you started and set that up, you might like to engage a consultant for the first audit, designing and documenting the audit process, providing checklist and reporting templates etc., |
Guideline | |||
| 2017-11-20 18:14:49 | NBlog November 20 - an A to Z catalog of social engineering (lien direct) |  A productive couple of days' graft has seen what was envisaged to be a fairly short and high-level general staff awareness briefing on social engineering morph gradually into an A-to-Z list of scams, con-tricks and frauds.It has grown to about 9 pages in the process. That may sound like a tome, over-the-top for awareness purposes ... and maybe it is, but the scams are described in an informal style in just a few lines each, making it readable and easily digestible. The A-to-Z format leads the reader naturally through a logical sequence, perhaps skim-reading in places and hopefully stopping to think in others.For slow/struggling readers, there are visual cues and images to catch their eyes but let's be honest: this briefing is not for them. They would benefit more from seminars, case studies, chatting with their colleagues and getting involved in other interactive activities (which we also support through our other awareness content). The NoticeBored mind maps and posters, for instance, express things visually with few words.Taking a step back from the A-Z list, the sheer variety and creativity of scams is fascinating, and I'm not just saying that because I wrote it! That's a key security awareness lesson in itself. Social engineering is hard to pin down to a few simple characteristics, in a way that workers can be expected to recognize easily. Some social engineering methods, such as ordinary phishing, are readily explained and fairly obvious but even then there are more obscure variants (such as whaling and spear phishing) that take the technique and threat level up a gear. It's not feasible for an awareness program to explain all forms of social engineering in depth, literally impossible in fact. It's something that an intensive work or college course might attempt, perhaps, for fraud specialists who will be fully immersed in the topic, but that's fraud training, not security awareness. We can't bank on workers taking time out from their day-jobs to sit in a room, paying full attention to their lecturers and scribbling notes for hour after hour. There probably aren't 'lecturers' in practice: most of this stuff is delivered online today, pushed out impersonally through the corporate intranet and learning management systems.Our aim is to grab workers' A productive couple of days' graft has seen what was envisaged to be a fairly short and high-level general staff awareness briefing on social engineering morph gradually into an A-to-Z list of scams, con-tricks and frauds.It has grown to about 9 pages in the process. That may sound like a tome, over-the-top for awareness purposes ... and maybe it is, but the scams are described in an informal style in just a few lines each, making it readable and easily digestible. The A-to-Z format leads the reader naturally through a logical sequence, perhaps skim-reading in places and hopefully stopping to think in others.For slow/struggling readers, there are visual cues and images to catch their eyes but let's be honest: this briefing is not for them. They would benefit more from seminars, case studies, chatting with their colleagues and getting involved in other interactive activities (which we also support through our other awareness content). The NoticeBored mind maps and posters, for instance, express things visually with few words.Taking a step back from the A-Z list, the sheer variety and creativity of scams is fascinating, and I'm not just saying that because I wrote it! That's a key security awareness lesson in itself. Social engineering is hard to pin down to a few simple characteristics, in a way that workers can be expected to recognize easily. Some social engineering methods, such as ordinary phishing, are readily explained and fairly obvious but even then there are more obscure variants (such as whaling and spear phishing) that take the technique and threat level up a gear. It's not feasible for an awareness program to explain all forms of social engineering in depth, literally impossible in fact. It's something that an intensive work or college course might attempt, perhaps, for fraud specialists who will be fully immersed in the topic, but that's fraud training, not security awareness. We can't bank on workers taking time out from their day-jobs to sit in a room, paying full attention to their lecturers and scribbling notes for hour after hour. There probably aren't 'lecturers' in practice: most of this stuff is delivered online today, pushed out impersonally through the corporate intranet and learning management systems.Our aim is to grab workers' |
Guideline | |||
| 2017-11-10 16:37:41 | NBlog November 10 - one step at a time (lien direct) |  This colorful image popped onto my screen as I searched our stash of security awareness content for social engineering-related graphics. It's a simple but striking visual expression of the concept that security awareness is not the ultimate goal, but an important step on the way towards achieving a positive outcome for the organization. A major part of the art of raising awareness in any area is actively engaging with people in such a way that they think and behave differently as a result of the awareness activities. For some people, providing cold, hard, factual information may be all it takes, which even the most basic awareness programs aim to do. That's not enough for the majority though: most of us need things to be explained to us in terms that resonate and motivate us to respond in some fashion. In physical terms, we need to overcome inertia. In biology, we need to break bad habits to form better ones.Social engineering is a particular challenge for awareness since scammers, fraudsters and other social engineers actively exploit our lack of awareness or (if that fails) subvert the very security mechanisms we put in place. "Your password has expired: pick a new one now to avoid losing access to your account!" is a classic example used by many a phisher. It hinges on tricking victims into accepting the premise (password expired) at face value and taking the easy option, clicking a link that leads them to the phisher's lair while thinking they are going to a legitimate password-change function. Our raising awareness of the need to choose strong passwords may be counterproductive if employees unwittingly associate phishing messages with user authentication and security!Part of our awareness approach in December's NoticeBored materials on social engineering will be to hook-in to our natural tendency to notice something amiss, something strange and different. Humans are strong at spotting patterns at a subconscious level. For instance, did you even notice the gradation from red to green on the ladder image? That was a deliberate choice in designing the image, a fairly crude and obvious example ... once it has been pointed out anyway! See if you can spot the other, more subtle visual cues (and by all means email me to see what you missed!). This colorful image popped onto my screen as I searched our stash of security awareness content for social engineering-related graphics. It's a simple but striking visual expression of the concept that security awareness is not the ultimate goal, but an important step on the way towards achieving a positive outcome for the organization. A major part of the art of raising awareness in any area is actively engaging with people in such a way that they think and behave differently as a result of the awareness activities. For some people, providing cold, hard, factual information may be all it takes, which even the most basic awareness programs aim to do. That's not enough for the majority though: most of us need things to be explained to us in terms that resonate and motivate us to respond in some fashion. In physical terms, we need to overcome inertia. In biology, we need to break bad habits to form better ones.Social engineering is a particular challenge for awareness since scammers, fraudsters and other social engineers actively exploit our lack of awareness or (if that fails) subvert the very security mechanisms we put in place. "Your password has expired: pick a new one now to avoid losing access to your account!" is a classic example used by many a phisher. It hinges on tricking victims into accepting the premise (password expired) at face value and taking the easy option, clicking a link that leads them to the phisher's lair while thinking they are going to a legitimate password-change function. Our raising awareness of the need to choose strong passwords may be counterproductive if employees unwittingly associate phishing messages with user authentication and security!Part of our awareness approach in December's NoticeBored materials on social engineering will be to hook-in to our natural tendency to notice something amiss, something strange and different. Humans are strong at spotting patterns at a subconscious level. For instance, did you even notice the gradation from red to green on the ladder image? That was a deliberate choice in designing the image, a fairly crude and obvious example ... once it has been pointed out anyway! See if you can spot the other, more subtle visual cues (and by all means email me to see what you missed!). |
Guideline | |||
| 2017-11-03 09:35:50 | NBlog November 3 - audit sampling (LONG) (lien direct) | [This piece was stimulated by a question on the ISO27k Forum about ISO27k certification auditors checking information security controls, and a response about compliance audit requirements. It's a backgrounder, an essay or a rant if you like. Feel free to skip it, or wait until you have a spare 10 mins, a strong coffee and the urge to read and think on!]“Sampling†is an important concept in both auditing and science. Sampling (i.e. selecting a sample of a set or population for review) is necessary because under most circumstances it is practically impossible to assess every single member – in fact it is often uncertain how many items belong to the set, where they are, what state they are in etc. There is often lots of uncertainty.For example, imagine an auditor needs to check an organization's “information security policies†in connection with an internal audit or certification/compliance audit.  Some organizations make that quite easy by having a policy library or manual or database, typically a single place on the intranet where all the official corporate policies exist and are maintained and controlled as a suite. In a large/diverse organization there may be hundreds of policies, thousands if you include procedures and guidelines and work instructions and forms and so forth. Some of them may be tagged or organized under an “information security†heading, so the auditor can simply work down that list … but almost straight away he/she will run into the issue that information security is part of information risk is part of risk, and information security management is part of risk management is part of management, hence there should be lots of cross-references to other kinds of policy. A “privacy policyâ€, for instance, may well refer to policies on identification and authentication, access control, encryption etc. (within the information security domain) plus other policies in areas such as accountability, compliance, awareness and training, incident management etc. which may or may not fall outside the information security domain depending on how it is defined, plus applicable privacy-related laws and regulations, plus contracts and agreements (e.g.nondisclosure agreements) … hence the auditor could potentially end up attempting to audit the entire corporate policy suite and beyond! In practice, that's not going to happen. Some organizations make that quite easy by having a policy library or manual or database, typically a single place on the intranet where all the official corporate policies exist and are maintained and controlled as a suite. In a large/diverse organization there may be hundreds of policies, thousands if you include procedures and guidelines and work instructions and forms and so forth. Some of them may be tagged or organized under an “information security†heading, so the auditor can simply work down that list … but almost straight away he/she will run into the issue that information security is part of information risk is part of risk, and information security management is part of risk management is part of management, hence there should be lots of cross-references to other kinds of policy. A “privacy policyâ€, for instance, may well refer to policies on identification and authentication, access control, encryption etc. (within the information security domain) plus other policies in areas such as accountability, compliance, awareness and training, incident management etc. which may or may not fall outside the information security domain depending on how it is defined, plus applicable privacy-related laws and regulations, plus contracts and agreements (e.g.nondisclosure agreements) … hence the auditor could potentially end up attempting to audit the entire corporate policy suite and beyond! In practice, that's not going to happen. |
Guideline | |||
| 2017-10-27 15:57:11 | NBlog October 27 - Equifax cultural issues (lien direct) |   Motherboard reveals a catalog of issues and failings within Equifax that seem likely to have contributed to, or patently failed to prevent, May's breach of sensitive personal information on over 145 million Americans, almost half the population.Although we'll be using the Equifax breach to illustrate November's awareness materials on privacy, we could equally have used them in this month's module on security culture since, according to BoingBoing:"Motherboard's Lorenzo Franceschi-Bicchierai spoke to several Equifax sources who described a culture of IT negligence and neglect, in which security audits and warnings were routinely disregarded, and where IT staff were unable to believe that their employers were so cavalier with the sensitive data the company had amassed."'A culture of IT negligence and neglect' is almost the opposite of a security culture, more of a toxic culture you could say. Workers who simply don't give a stuff about information security or privacy are hardly likely to lift a finger if someone reports issues to them, especially if (as seems likely) senior managers are complicit, perhaps even the source of the toxin. Their lack of support, leadership, prioritization and resourcing for the activities necessary to identify and address information risks makes it hard for professionals, staff members and even management Motherboard reveals a catalog of issues and failings within Equifax that seem likely to have contributed to, or patently failed to prevent, May's breach of sensitive personal information on over 145 million Americans, almost half the population.Although we'll be using the Equifax breach to illustrate November's awareness materials on privacy, we could equally have used them in this month's module on security culture since, according to BoingBoing:"Motherboard's Lorenzo Franceschi-Bicchierai spoke to several Equifax sources who described a culture of IT negligence and neglect, in which security audits and warnings were routinely disregarded, and where IT staff were unable to believe that their employers were so cavalier with the sensitive data the company had amassed."'A culture of IT negligence and neglect' is almost the opposite of a security culture, more of a toxic culture you could say. Workers who simply don't give a stuff about information security or privacy are hardly likely to lift a finger if someone reports issues to them, especially if (as seems likely) senior managers are complicit, perhaps even the source of the toxin. Their lack of support, leadership, prioritization and resourcing for the activities necessary to identify and address information risks makes it hard for professionals, staff members and even management |
Guideline | Equifax | ||
| 2017-10-02 10:51:19 | NBlog October 2 - a 2-phase approach to bolster the security culture (lien direct) |  We've just updated the NoticeBored website to describe the new awareness module on security culture and delivered the latest batch of security awareness materials to subscribers. Culture is a nebulous, hand-waving concept, hard to pin down and yet an important, far-reaching factor in any organization. The new module (the 63rd topic in our bulging security awareness portfolio) is essentially a recruitment drive, aimed at persuading workers to join and become integral parts of the Information Security function. The basic idea is straightforward in theory but in practice it is a challenge to get people to sit up and take notice, then to change their attitudes and behaviors. During September, we developed a two-phased approach:Strong leadership is critically important which means first convincing management (all the way up to the exec team and Board) that they are the lynch-pins. In setting the tone at the top, the way managers treat information risk, security, privacy, compliance and related issues has a marked effect on the entire organization. Their leverage is enormous, with the potential to enable or undermine the entire approach, as illustrated by the Enron, Sony and Equifax incidents.With management support in the bag, the next task is to persuade workers in general to participate actively in the organization's information security arrangements. Aside from directly appealing to staff on a personal level, we enlist the help of professionals and specialists since they too are a powerful influence on the organization - including management. October's awareness materials follow hot on the heels of the revised Information Security 101 module delivered in September. That set the scene, positioning information security as an essential part of modern business. Future modules will expand on different aspects, each one reinforcing the fundamentals ... which is part of the process of enhancing the security cu We've just updated the NoticeBored website to describe the new awareness module on security culture and delivered the latest batch of security awareness materials to subscribers. Culture is a nebulous, hand-waving concept, hard to pin down and yet an important, far-reaching factor in any organization. The new module (the 63rd topic in our bulging security awareness portfolio) is essentially a recruitment drive, aimed at persuading workers to join and become integral parts of the Information Security function. The basic idea is straightforward in theory but in practice it is a challenge to get people to sit up and take notice, then to change their attitudes and behaviors. During September, we developed a two-phased approach:Strong leadership is critically important which means first convincing management (all the way up to the exec team and Board) that they are the lynch-pins. In setting the tone at the top, the way managers treat information risk, security, privacy, compliance and related issues has a marked effect on the entire organization. Their leverage is enormous, with the potential to enable or undermine the entire approach, as illustrated by the Enron, Sony and Equifax incidents.With management support in the bag, the next task is to persuade workers in general to participate actively in the organization's information security arrangements. Aside from directly appealing to staff on a personal level, we enlist the help of professionals and specialists since they too are a powerful influence on the organization - including management. October's awareness materials follow hot on the heels of the revised Information Security 101 module delivered in September. That set the scene, positioning information security as an essential part of modern business. Future modules will expand on different aspects, each one reinforcing the fundamentals ... which is part of the process of enhancing the security cu |
Guideline | Equifax | ||
| 2017-09-25 15:51:23 | NBlog September 24 - five-step bulletproofing? (lien direct) | In the course of searching for case study materials and quotations to illustrate October's awareness materials, I came across 5 ways to create a bulletproof security culture by Brian Stafford. Brian's 5 ways are, roughly: Get Back to Basics - address human behaviors including errors. Fair enough. The NoticeBored InfoSec 101 awareness module we updated last month is precisely for a back-to-basics approach, including fundamental concepts, attitudes and behaviors.Reinvent the Org Chart - have the CISO report to the CEO. Brian doesn't explain why but it's pretty obvious, especially if you accept that the organization's culture is like a cloak that covers everyone, and strong leadership is the primary way of influencing it. The reporting relationship is only part of the issue though: proper governance is a bigger consideration, for example aligning the management of information risks and assets with that for other kinds of risk and asset. Also security metrics - a gaping hole in the governance of most organizations.Invest in Education - "Any company that seeks to have a strong security culture must not only offer robust trainings to all employees-including the c-suite-but also encourage professional development opportunities tailored to their unique focus areas." Awareness, training and education go hand-in-hand: they are complementary.Incentivize & Reward Wanted Behavior e.g. by career advancement options. Again, the InfoSec 101 module proposes a structured gold-silver-bronze approach to rewards and incentives, and I've discussed the idea here on the blog several times. Compliance reinforcement through rewards and encouragement is far more positive and motivational than the negative compliance enforcement approach through pressure, penalties and grief. Penalties may still be necessary but as a last resort than the default option.Apply the Right Technology - hmm, an important consideration, for sure, although I'm not sure what this has to do with security culture. I guess I would say that technical controls need to work in concert with non-tech controls, and the selection, operation, use and management of all kinds of control is itself largely a human activity. The fact that Brian included this as one of his 5 ways betrays the widespread bias towards technology and cybersecurity. I'd go so far as to call it myopic. Personally, and despite Personally, and despite |
Guideline | |||
| 2017-09-22 08:59:43 | NBlog September 22 - cultured security (lien direct) |  Aside from concerning the attitudes and values shared within groups, or its use in microbiology (!), there's another meaning of 'culture' relating to being suave and sophisticated. In the information risk and security context, it's about both being and appearing professional, exuding competence and quality - and that can be quite important if you consider the alternative. Given the choice, would you be happy interacting and doing business with an organization that is, or appears to be, uncultured - crude, slapdash, unreliable etc.? Or would you be somewhat reluctant to trust them?There are some obvious examples in the news headlines most weeks: any organization that suffers a major privacy breach, hack, ransomware or other incident comes across as a victim and arguably perhaps culpable for the situation. It's hardly a glowing endorsement of their information risk, security, privacy and compliance arrangements! Contrast their position against the majority of organizations, particularly the banks that exude trustworthiness. Corporate cultures, brands and reputations are bound strongly together.The two meanings of 'culture' are linked in the sense that the overall impression an organization portrays is the combination of many individual factors or elements. Through marketing, advertising and promotions, public relations, social media etc., management naturally strives to present a polished, impressive, business-like, trustworthy external corporate image, but has limited control over all the day-to-day goings on. Myriad interactions between workers and the outside world are largely independent, driven by the individuals, individually, and by the corporate culture as a whole.Management may try to control the latter, espousing 'corporate values' through motivational speeches and posters, but in most organizations it's like herding cats or plaiting fog. Much like managing change, managing the corporate culture is a tough challenge in practice. Realistically, the best management can hope for is to influence things in the right direction, perhaps rounding-off the sharpest corners and presenting a more consistently positive front. Aside from concerning the attitudes and values shared within groups, or its use in microbiology (!), there's another meaning of 'culture' relating to being suave and sophisticated. In the information risk and security context, it's about both being and appearing professional, exuding competence and quality - and that can be quite important if you consider the alternative. Given the choice, would you be happy interacting and doing business with an organization that is, or appears to be, uncultured - crude, slapdash, unreliable etc.? Or would you be somewhat reluctant to trust them?There are some obvious examples in the news headlines most weeks: any organization that suffers a major privacy breach, hack, ransomware or other incident comes across as a victim and arguably perhaps culpable for the situation. It's hardly a glowing endorsement of their information risk, security, privacy and compliance arrangements! Contrast their position against the majority of organizations, particularly the banks that exude trustworthiness. Corporate cultures, brands and reputations are bound strongly together.The two meanings of 'culture' are linked in the sense that the overall impression an organization portrays is the combination of many individual factors or elements. Through marketing, advertising and promotions, public relations, social media etc., management naturally strives to present a polished, impressive, business-like, trustworthy external corporate image, but has limited control over all the day-to-day goings on. Myriad interactions between workers and the outside world are largely independent, driven by the individuals, individually, and by the corporate culture as a whole.Management may try to control the latter, espousing 'corporate values' through motivational speeches and posters, but in most organizations it's like herding cats or plaiting fog. Much like managing change, managing the corporate culture is a tough challenge in practice. Realistically, the best management can hope for is to influence things in the right direction, perhaps rounding-off the sharpest corners and presenting a more consistently positive front. |
Guideline | |||
| 2017-09-20 08:27:57 | NBlog September 20 - Phishing awareness & cultural change (lien direct) |  This plopped into my inbox last evening at about 8pm, when both ANZ customers and the ANZ fraud and security pros are mostly off-guard, relaxing at home. It's clearly a phishing attack, obvious for all sorts of reasons (e.g. the spelling and grammatical errors, the spurious justification and call to action, the non-ANZ hyperlink, oh and the fact that I don't have an ANZ account!) - obvious to me, anyway, and I hope obvious to ANZ customers, assuming they are sufficiently security-aware to spot the clues.I guess the phishers are either hoping to trick victims into disclosing their ANZ credentials directly, or persuade them to reveal enough that they can trick the bank into accepting a change of the mobile phone number presumably being used for two-factor authentication, or for password resets.Right now (8 am, 12 hours after the attack) I can't see this particular attack mentioned explicitly on the ANZ site, although there is some basic guidance on "hoax messages" with a few other phishing examples. The warnings and advice are not exactly prominent, however, so you need to go digging to find the information, which means you need to be alert and concerned enough in the first place, which implies a level of awareness - a classic chicken-and-egg situation. I presume ANZ has other security awareness materials, advisories and reminders for customers. If not, perhaps we can help!Aside from the authentication and fraud angle, I'm interested in the cultural aspects. Down here in NZ, people generally seem to be quite honest and trusting: it's a charming feature of the friendly and welcoming Pacific culture that pervades our lives. Given its size and history, things may be different in Australia - I don't know. But I do know that phishing and other forms of fraud are problematic in NZ. The Pacific culture is changing, becoming more careful as a result of these and other scams, but very slowly. Increasing distrust and cynicism seems likely to knock the corners off the charm that I mentioned, with adverse implications for tourism and commerce - in other words cultural changes can create as well as solve problems. The same issue applies within organizations: pushing security awareness will lead (eventually, if sustained) to changes in the corporate culture, only some of which are beneficial. It's possible to be too security-conscious, too risk-averse, to the point that it interferes with business. October's awareness seminar and briefings for management will discuss a strategic approach ai This plopped into my inbox last evening at about 8pm, when both ANZ customers and the ANZ fraud and security pros are mostly off-guard, relaxing at home. It's clearly a phishing attack, obvious for all sorts of reasons (e.g. the spelling and grammatical errors, the spurious justification and call to action, the non-ANZ hyperlink, oh and the fact that I don't have an ANZ account!) - obvious to me, anyway, and I hope obvious to ANZ customers, assuming they are sufficiently security-aware to spot the clues.I guess the phishers are either hoping to trick victims into disclosing their ANZ credentials directly, or persuade them to reveal enough that they can trick the bank into accepting a change of the mobile phone number presumably being used for two-factor authentication, or for password resets.Right now (8 am, 12 hours after the attack) I can't see this particular attack mentioned explicitly on the ANZ site, although there is some basic guidance on "hoax messages" with a few other phishing examples. The warnings and advice are not exactly prominent, however, so you need to go digging to find the information, which means you need to be alert and concerned enough in the first place, which implies a level of awareness - a classic chicken-and-egg situation. I presume ANZ has other security awareness materials, advisories and reminders for customers. If not, perhaps we can help!Aside from the authentication and fraud angle, I'm interested in the cultural aspects. Down here in NZ, people generally seem to be quite honest and trusting: it's a charming feature of the friendly and welcoming Pacific culture that pervades our lives. Given its size and history, things may be different in Australia - I don't know. But I do know that phishing and other forms of fraud are problematic in NZ. The Pacific culture is changing, becoming more careful as a result of these and other scams, but very slowly. Increasing distrust and cynicism seems likely to knock the corners off the charm that I mentioned, with adverse implications for tourism and commerce - in other words cultural changes can create as well as solve problems. The same issue applies within organizations: pushing security awareness will lead (eventually, if sustained) to changes in the corporate culture, only some of which are beneficial. It's possible to be too security-conscious, too risk-averse, to the point that it interferes with business. October's awareness seminar and briefings for management will discuss a strategic approach ai |
Guideline | |||
| 2017-09-08 18:35:37 | NBlog September 8 - security certification (lien direct) |  Aside from the elevator pitch, another short awareness item in our newly-revised Information Security 101 module is a course completion certificate, simply acknowledging that someone has been through the induction or orientation course.I say 'simply' but as usual with NoticeBored, there's more to it.For a start, some of us (especially those who consider ourselves 'professionals') just love our certificates: our qualifications and the letters before/after our names mean something to us and hopefully other people. This is a personal thing with cultural relevance, and it's context-dependent (my 30-year-old PhD in microbial genetics has next to nothing to do with my present role!). My even older cycling proficiency certificate is meaningless now, barely a memory, but at the time I was proud of my achievement. Receiving it boosted my self-esteem, as valuable a benefit as being able to demonstrate my prowess on two wheels. I'm tempted to use Cprof on my business cards just to see if anyone reads them!On the other hand, a certificate indicating a pass mark in some assessment or test can be misleading. The driving test, for example, is a fairly low hurdle in terms of all the situations that a driver may have to deal with over the remainder of their driving career. There is clearly a risk that a newly-certified and licensed driver might be over-confident as a result of passing the test and going solo, a time when accidents are more likely hence some countries encourage a subsequent period of driving with special P-plates (meaning probationary, or passed or potential or ...) in the hope that others will give new drivers more space. In risk terms, there are risk-reduction benefits in letting new drivers continue to hone their new-found skills, offsetting the increased risk of incidents.In the same way with the InfoSec 101 course completion certificate, we're glad to acknowledge the personal achievement and boost people's self-esteem (yay - something positive associated with information risk and security!), although there is a risk they might believe themselves more competent in this area that they truly are. On balance, we'd rather deal with that issue, in part through the ongoing security awareness activities that delve deeper into areas covered quite superficially in the 101 module, across a br Aside from the elevator pitch, another short awareness item in our newly-revised Information Security 101 module is a course completion certificate, simply acknowledging that someone has been through the induction or orientation course.I say 'simply' but as usual with NoticeBored, there's more to it.For a start, some of us (especially those who consider ourselves 'professionals') just love our certificates: our qualifications and the letters before/after our names mean something to us and hopefully other people. This is a personal thing with cultural relevance, and it's context-dependent (my 30-year-old PhD in microbial genetics has next to nothing to do with my present role!). My even older cycling proficiency certificate is meaningless now, barely a memory, but at the time I was proud of my achievement. Receiving it boosted my self-esteem, as valuable a benefit as being able to demonstrate my prowess on two wheels. I'm tempted to use Cprof on my business cards just to see if anyone reads them!On the other hand, a certificate indicating a pass mark in some assessment or test can be misleading. The driving test, for example, is a fairly low hurdle in terms of all the situations that a driver may have to deal with over the remainder of their driving career. There is clearly a risk that a newly-certified and licensed driver might be over-confident as a result of passing the test and going solo, a time when accidents are more likely hence some countries encourage a subsequent period of driving with special P-plates (meaning probationary, or passed or potential or ...) in the hope that others will give new drivers more space. In risk terms, there are risk-reduction benefits in letting new drivers continue to hone their new-found skills, offsetting the increased risk of incidents.In the same way with the InfoSec 101 course completion certificate, we're glad to acknowledge the personal achievement and boost people's self-esteem (yay - something positive associated with information risk and security!), although there is a risk they might believe themselves more competent in this area that they truly are. On balance, we'd rather deal with that issue, in part through the ongoing security awareness activities that delve deeper into areas covered quite superficially in the 101 module, across a br |
Guideline | |||
| 2017-09-04 15:31:24 | NBlog September 4 - InfoSec 101 elevator pitch, final part (lien direct) | Moving on from our discussion of the first two paragraphs of this month's elevator pitch paper in part 1 and part 2, here's the closing paragraph:As a manager, you play a vital governance, leadership and oversight rôle. Please make the effort to engage with and support the security awareness program, discuss information risk and security with your colleagues, and help us strengthen the corporate security culture. In classical marketing terms, it's the call-to-action for people who have been lured and hooked. Having presented our case, what do we actually want them to do? Compared to the preceding two, the third paragraph is quite long. While we could easily have dropped the first sentence, it serves a purpose. It shows deference to the management audience, acknowledging their influential and powerful status, gently reminding them that they are expected to direct and oversee things. Essentially (in not so many word), it says "Pay attention! This is an obligation, one of your duties as a manager."The final sentence, including those three words in bold, was especially tricky to write for the InfoSec 101 module. What is it, exactly, that we expect senior managers to do in relation to this very broad introductory-level topic? Think about that question for a moment. There are many possible answers e.g.:Show leadershipDemonstrate commitmentSupport the Information Security Management System (in an ISO27k organization)Get actively involved in information risk and security management activities, such as risk assessment and risk treatment decisionsRaise the profile and priority of information risk and security mattersProvide adequate resources to do this stuff properly for once (!)Encourage or enforce compliance In classical marketing terms, it's the call-to-action for people who have been lured and hooked. Having presented our case, what do we actually want them to do? Compared to the preceding two, the third paragraph is quite long. While we could easily have dropped the first sentence, it serves a purpose. It shows deference to the management audience, acknowledging their influential and powerful status, gently reminding them that they are expected to direct and oversee things. Essentially (in not so many word), it says "Pay attention! This is an obligation, one of your duties as a manager."The final sentence, including those three words in bold, was especially tricky to write for the InfoSec 101 module. What is it, exactly, that we expect senior managers to do in relation to this very broad introductory-level topic? Think about that question for a moment. There are many possible answers e.g.:Show leadershipDemonstrate commitmentSupport the Information Security Management System (in an ISO27k organization)Get actively involved in information risk and security management activities, such as risk assessment and risk treatment decisionsRaise the profile and priority of information risk and security mattersProvide adequate resources to do this stuff properly for once (!)Encourage or enforce compliance |
Guideline | |||
| 2017-08-25 14:13:47 | NBlog August 25 - awareness boosters (lien direct) |  The Information Security 101 awareness module update is going well. We might even finish slightly ahead of the deadline, provided I can resist the temptation to keep polishing and adding to the content!One of the deliverables is a 'menu' of rewards for workers who uphold the information risk and security practises, controls and behaviors we wish to encourage. The rewards are divided into bronze, silver and gold categories.Bronze rewards are generally free or cheap, and yet welcome - a nice way to thank workers for simply participating in awareness seminars, case study/workshop session or quiz maybe. Here are just a few examples:A phone call, personal thank-you note and/or emailLetter of participation or commendation to be placed in the employee's personnel file (whatever that means!)Relaxed dress code for the recipient – for a defined period such as a day or a week Generic certificate acknowledging a level of competence (e.g. on completion of security induction training - there's a template in the module)Note and/or photo on hall-of-fame, newsletter and/or the Security Zone (Information Security's intranet website - again there's a generic website design specification in the module)Plain (dull bronze) pin badge or sticker with awareness program logoPlain (dull bronze) staff pass lanyard with awareness program logo and stock message (such as how to contact the Help Desk or Site Security)Moving up a level, silver awards are more valuable and attractive, requiring a little more money and effort:[if !supportLists]-->Polo/tee-shirt printed with corporate and/or awareness program logo and a relevant quotation or catch-phrase The Information Security 101 awareness module update is going well. We might even finish slightly ahead of the deadline, provided I can resist the temptation to keep polishing and adding to the content!One of the deliverables is a 'menu' of rewards for workers who uphold the information risk and security practises, controls and behaviors we wish to encourage. The rewards are divided into bronze, silver and gold categories.Bronze rewards are generally free or cheap, and yet welcome - a nice way to thank workers for simply participating in awareness seminars, case study/workshop session or quiz maybe. Here are just a few examples:A phone call, personal thank-you note and/or emailLetter of participation or commendation to be placed in the employee's personnel file (whatever that means!)Relaxed dress code for the recipient – for a defined period such as a day or a week Generic certificate acknowledging a level of competence (e.g. on completion of security induction training - there's a template in the module)Note and/or photo on hall-of-fame, newsletter and/or the Security Zone (Information Security's intranet website - again there's a generic website design specification in the module)Plain (dull bronze) pin badge or sticker with awareness program logoPlain (dull bronze) staff pass lanyard with awareness program logo and stock message (such as how to contact the Help Desk or Site Security)Moving up a level, silver awards are more valuable and attractive, requiring a little more money and effort:[if !supportLists]-->Polo/tee-shirt printed with corporate and/or awareness program logo and a relevant quotation or catch-phrase |
Guideline | |||
| 2017-08-22 15:51:29 | NBlog August 22 - what to ask in a gap assessment (lien direct) |  A relatively simple and naive question on the ISO27k Forum this morning set me thinking. "RP" asked:"Does anybody have a generic [set of] high level questions for business departments other than IT, that can be asked during gap assessment?"As is so often the way with newcomers to the Forum, RP evidently hasn't caught up with past Forum threads (e.g. we recently chatted about various forms of gap analysis, and the markedly different ways that people [including dentists!] use and interpret the term), paid scant attention to forum etiquette (e.g. he/she didn't tell us his/her name), and provided little to no context in which to address the question (e.g. what size and kind of organization is it? What industry/sector? Does it have a functional, certified and mature ISO27k ISMS already, is it working towards one, or is RP just idly thinking about it over coffee?).Despite that, a couple of us responded as best we could, making assumptions about the context, the meaning and purpose of the 'gap assessment', and RP's situation. I suggesting posing questions along these lines:"What kinds of information do you use? Tell me more. Which is the most important information for your business activities, and why? What would happen if it was lost, damaged, out of date, inaccurate, incomplete, misleading, fraudulent, or disclosed e.g. on the Web?Roughly how much of the information you handle is classified? How much is SECRET/TOP-SECRET? [You'd probably need to be security cleared, and have management support, to get a meaningful answer to that!]What information do you generate? What happens to it? Where does it go? Who uses it, and for what? Would it matter to them if it stopped coming, or was late, or inaccurate, or incomplete, or was disclosed on the Web?When was the last time you examined your information risks? What was the result? Show me! What changed as a result?When was the last time you completed a business impact analysis and business continuity p A relatively simple and naive question on the ISO27k Forum this morning set me thinking. "RP" asked:"Does anybody have a generic [set of] high level questions for business departments other than IT, that can be asked during gap assessment?"As is so often the way with newcomers to the Forum, RP evidently hasn't caught up with past Forum threads (e.g. we recently chatted about various forms of gap analysis, and the markedly different ways that people [including dentists!] use and interpret the term), paid scant attention to forum etiquette (e.g. he/she didn't tell us his/her name), and provided little to no context in which to address the question (e.g. what size and kind of organization is it? What industry/sector? Does it have a functional, certified and mature ISO27k ISMS already, is it working towards one, or is RP just idly thinking about it over coffee?).Despite that, a couple of us responded as best we could, making assumptions about the context, the meaning and purpose of the 'gap assessment', and RP's situation. I suggesting posing questions along these lines:"What kinds of information do you use? Tell me more. Which is the most important information for your business activities, and why? What would happen if it was lost, damaged, out of date, inaccurate, incomplete, misleading, fraudulent, or disclosed e.g. on the Web?Roughly how much of the information you handle is classified? How much is SECRET/TOP-SECRET? [You'd probably need to be security cleared, and have management support, to get a meaningful answer to that!]What information do you generate? What happens to it? Where does it go? Who uses it, and for what? Would it matter to them if it stopped coming, or was late, or inaccurate, or incomplete, or was disclosed on the Web?When was the last time you examined your information risks? What was the result? Show me! What changed as a result?When was the last time you completed a business impact analysis and business continuity p |
Guideline |
To see everything:
Our RSS (filtrered)
